Developer Support
Advocacy and Innovation
Latest posts

The Journey Begins – DevOps starts with culture!
At this point we were five plus years into a local transformation that was underappreciated and overlooked by the global IT organization. The frustration was high and the hope was waning. For me this became my motivation to start a journey to understand why some organization can adopt DevOps strategies successfully and other struggle.

Tribal Knowledge – The Anti-DevOps Culture
By removing or reducing tribal knowledge from projects and teams, organizations set themselves up for success in an ever-changing landscape (exponentially changing). In other words, you can add to your DevOps culture (or create one) simply by subtracting the bad habits and behaviors.

AI and the Art of What’s Possible
Application Development Manager Rich Maines explores the art of the possible with AI in the context of Microsoft services and the ethical principles that we believe should drive the development of AI.
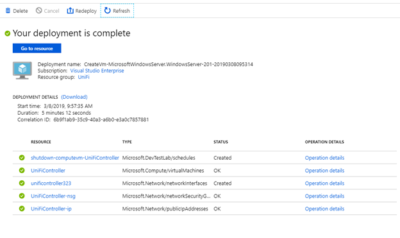
Setting up a cloud server to run UniFi Controller
In this post, we'll explore how to setup an Azure virtual machine to act as a UniFi controller in the cloud, enabling 24x7 guest access without the overhead of running a physical machine continuously in your home.

Getting started with Docker for Windows
In this walkthrough, our App Dev Managers show how to install, configure and containerize a simple webapp to help you get up and running with Docker.

Easily create a low-cost WordPress blog on Azure
These directions apply if you want to create a personal blog which is hosted on someone else's domain, and that won’t get a lot of traffic, and you want to do this cheaply.

Choosing the OAuth2 grant flow
Premier Dev Consultant Marius Rochon explores OAuth2 questions you need to ask and how the answers lead to the selection of the grant. The OAuth2 specifications define six different grant types (https://tools.ietf.org/html/rfc6749 and https://tools.ietf.org/html/draft-ietf-oauth-device-flow-15). Each provides the most optimal (from the security point of view) way of obtaining access or (for OIDC) id_tokens given the circumstances of the client application. This blog summarizes the questions that the implementer of the OAuth2 client application needs to ask and how the answers lead to the selection of the a...
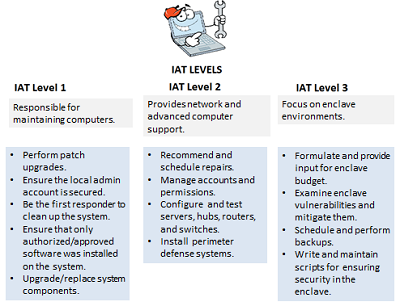
Understanding ‘Why’ you should take CompTIA’s Security+ Exam for DoD Programs
It is extremely difficult to find individuals with Security+ accreditation. Achieving this accreditation not only helps you but also helps defense contracting companies and the DoD community to fill in those national security related positions with those specialized needs.

Is the latest technology the key to your team’s success, or is there something else?
We experienced many different emotions with what seemed like a daunting task. What made it less daunting, the facilitators reminded us, was that we are not alone - we are team - so, leverage each other.
