


Importing an OpenAPI API into Azure API Management Service
How to Post a File to an Azure Function in 3 Minutes

Setting up for Azure B2C development

Reducing SNAT Port consumption in Azure App Services

Claims encryption for B2C tokens

Generate a Service Bus SAS Token and Manage Token renewal using Azure Runbooks
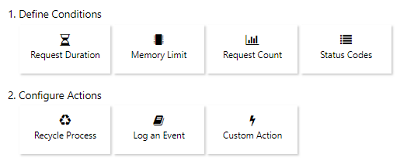
Collect and Automate Diagnostic Actions with Azure App Services

Taste of Premier: Azure Security Center


 Light
Light Dark
Dark