Insider Threat Monitoring for Zero Trust with Microsoft Azure (5 of 6)
This is the fifth in a six-part blog series where we will demonstrate the application of Zero Trust concepts for securing federal information systems with Microsoft Azure. In this fifth blog of the series we will explore how to leverage Microsoft Azure for insider threats in Zero Trust models. The last blog in the series will include monitoring supply chain risk management.
This blog series is coauthored by TJ Banasik, CISSP-ISSEP, ISSAP, ISSMP, Sr. Program Manager, Azure Global Customer Engineering, Mark McIntyre, CISSP, Senior Director, Enterprise Cybersecurity Group and Adam Dimopoulos, Azure Global Customer Engineering.
What is an insider threat?
The Microsoft Zero Trust vision paper outlines three principles of Zero Trust- Verify Explicitly, Least Privilege Access and Assume Breach. Zero Trust assumes breach and verifies each request as though it originates from an uncontrolled network. Access requests are inspected for anomalies prior to granting access and user access is limited to least privilege required to perform respective job functions. The NIST SP 800-207 draft for Zero Trust Architecture identifies several threats associated with a Zero Trust architecture including subversion of the ZTA decision process, denial of service and insider threats. The standard describes insider threat detection, as “Trust Algorithms can detect access patterns that are out of normal behavior and deny the compromised account (or insider threat) access to resources.”[i] An insider threat is a user or entity that leverages authorized access to knowingly or unknowingly cause harm to an organization. Insider threats range from an unwitting user accidentally clicking a phishing link to a malicious actor stealing sensitive information.
Defining Zero Trust governance based on federal frameworks
Governance definition is a critical precursor to any Zero Trust initiative. For this blog we’ve leveraged TIC 3.0 Zero Trust principles and aligned with respective NIST SP 800-207 and NIST CSF controls. Our fifth focus point is insider threat monitoring and these standards have a wealth of information aligned to this principle. The diagram below highlights the key takeaways and requirements from the standards.
- Trusted Internet Connections (TIC) is a federal cybersecurity initiative to enhance network and perimeter security across the United States federal government. The TIC initiative is a collaborative effort between the Office of Management and Budget (OMB), the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA), and the General Services Administration (GSA).[ii] The TIC 3.0: Volume 3 Security Capabilities Handbook provides various security controls, applications and best practice for risk management in federal information systems.
- NIST Cybersecurity Framework. The National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework to address risks highlighted in the Cybersecurity Enhancement Act of 2014 with a goal to identify “a prioritized, flexible, repeatable, performance-based, and cost effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks.”[iii] The Framework for Improving Critical Infrastructure Cybersecurity outlines these principles.
- NIST SP 800-207. The National Institute of Standards and Technology (NIST) has recently released NIST SP 800-207 for Zero Trust Architectures which is in draft for comment. This document provides a framework for designing a zero-trust architecture (ZTA) network strategy[iv].
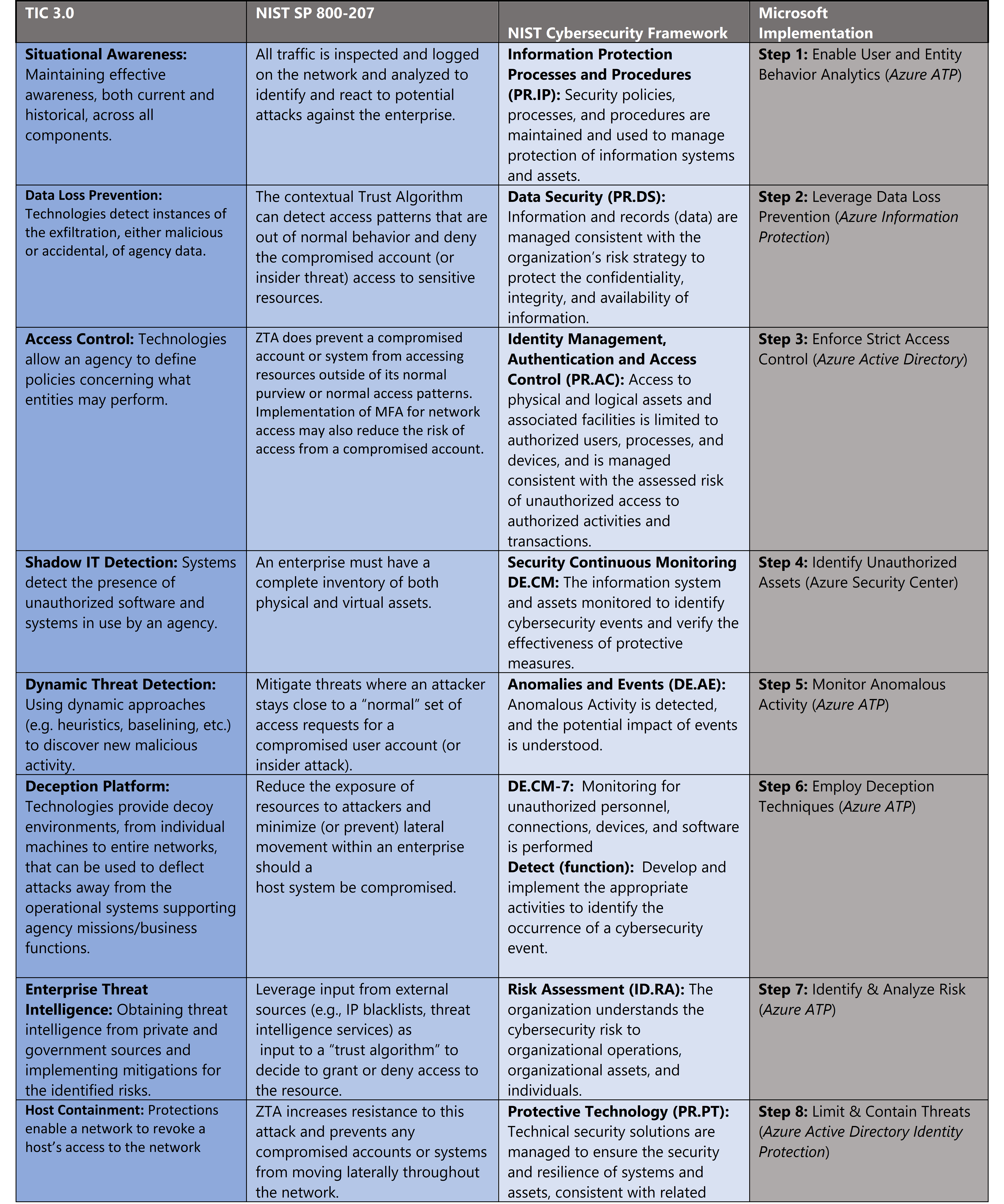
Insider threat monitoring for Zero Trust with Microsoft Azure
Microsoft Azure Government has developed an 8-step process to facilitate insider threat monitoring for federal information systems in Microsoft Azure which is aligned with the security monitoring principles within the TIC 3.0, NIST CSF, and NIST SP 800-207 standards. Note this process is a starting point, as insider threat programs require alignment of people, processes, policy and technology so refer to organizational requirements and respective standards for implementation. Azure has several offerings to facilitate insider threat monitoring including Azure Advanced Threat Protection, Azure Active Directory Identity Protection, Azure Information Protection, and Azure Security Center.
- Azure Advanced Threat Protection is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. *Note offerings, features, and availability may vary between government clouds, for more information see Azure Advanced Threat Protection Security Government service description.
- Azure Active Directory Identity Protection is a tool that allows organizations to automate detection and remediation of identity-based risks, investigate risks using data in the portal and export risk detection data to third-party utilities for further analysis.
- Azure Information Protection is a cloud-based solution that helps an organization to classify and optionally, protect its documents and emails by applying labels. Labels can be applied automatically by administrators who define rules and conditions, manually by users, or a combination where users are given recommendations. *Note offerings, features, and availability may vary between government clouds, for more information see Azure Information Protection Premium Government Service Description.
- Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers and provides advanced threat protection across your hybrid workloads in the cloud – whether they’re in Azure or not – as well as on premises.
8 steps to insider threat monitoring for Zero Trust with Microsoft Azure
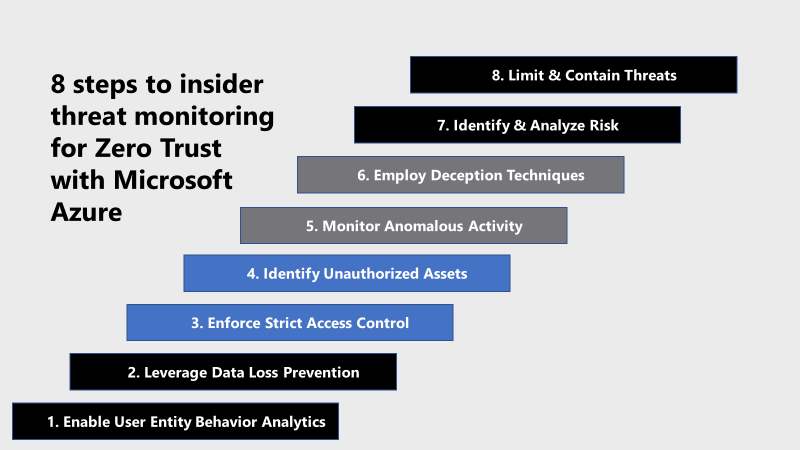
1) Enable User and Entity Behavior Analytics
Azure ATP monitors and analyzes user activities and information across your network, such as permissions and group membership, creating a behavioral baseline for each user. Azure ATP then identifies anomalies with adaptive built-in intelligence, giving you insights into suspicious activities and events, revealing the advanced threats, compromised users, and insider threats facing your organization. Azure ATP’s proprietary sensors monitor organizational domain controllers, providing a comprehensive view for all user activities from every device. Azure ATP also enables SecOps analysts and security professionals struggling to detect advanced attacks in hybrid environments to:
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Enabling Azure ATP requires the following high-level steps:
- Create your ATP instance
- Connect to Active Directory
- Download the Azure ATP sensor package
- Install the ATP sensor
To get started with creating an Azure ATP instance use the following steps. Note that GCC High customers must use the Azure ATP GCC High portal.
- Click Create instance.
- Your Azure ATP instance is automatically named with the Azure AD initial domain name and created in the data center located closest to your Azure AD.
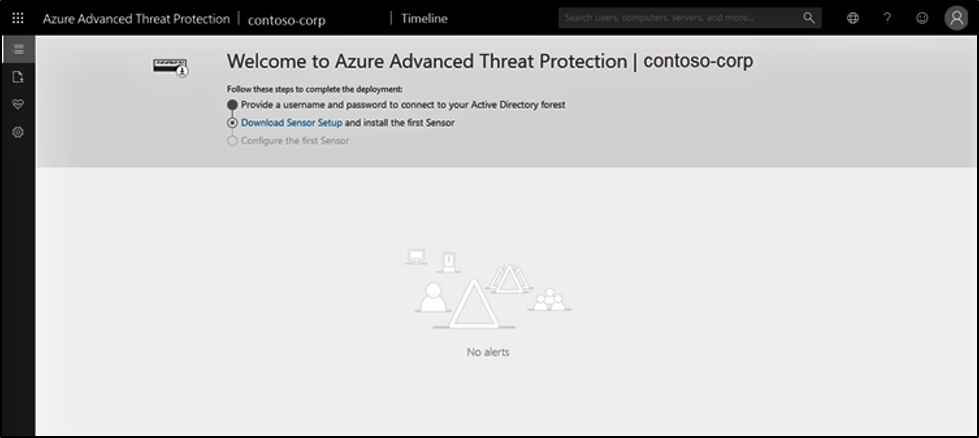
- Click Configuration, Manage role groups, and use the Azure AD Admin Center link to manage your role groups.
- Complete the process by following the deployment guide for Azure AD connection and the Azure ATP Sensor Download/Installation.
For more information, see What is Azure Advanced Threat Protection? and Quickstart: Create your Azure ATP instance.
2) Leverage Data Loss Prevention
Monitoring for insider threats in zero trust models requires data classification. Classification facilitates more detailed monitoring, access control and security. Azure Information Protection (sometimes referred to as AIP) is a cloud-based solution that helps an organization to classify and optionally, protect its documents and emails by applying labels. Labels can be applied automatically by administrators who define rules and conditions, manually by users, or a combination where users are given recommendations.
The following picture shows an example of Azure Information Protection in action on a user’s computer. The administrator has configured a label with rules that detect sensitive data. When a user saves a Word document that contains a credit card number, a custom tooltip that recommends the label that the administrator has configured. This label classifies the document and protects it.
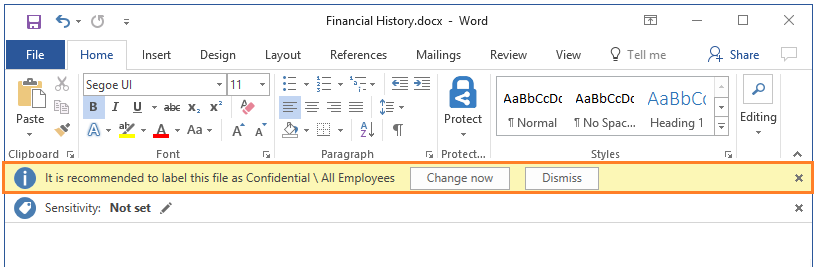
After your content is classified (and optionally protected), you can then track and control how it is used. You can analyze data flows to gain insight into your business, detect risky behaviors and take corrective measures, track access to documents, prevent data leakage or misuse, and so on. For more information on getting started with Azure Information Protection, see Quickstart: Get started with Azure Information Protection in the Azure portal.
3) Enforce Strict Access Control
Strict access control is a central tenant to Zero Trust models. Access management for cloud resources is critical for any organization that uses the cloud. Access control makes it more challenging for an insider threat to move laterally within the environment and creates additional tripwires for insider threat detection. Role-based access control (RBAC) helps manage who has access to Azure resources, what they can do with those resources, and what areas they have access to. Designating groups or individual roles responsible for specific functions in Azure helps avoid confusion that can lead to human and automation errors that create security risks. Restricting access based on the need to know and least privilege security principles is imperative for organizations that want to enforce security policies for data access. For more information, see Azure Identity Management and access control security best practices.
4) Identify Unauthorized Assets
Identification of unauthorized assets and software is another potential indicator of insider threat activity. Unauthorized assets can perform as anchor points for exfiltration while unauthorized software can facilitate exploitation and elevating access. Microsoft provides numerous offerings for combating Shadow IT. Microsoft Defender Advanced Threat Protection (MDATP) provides capabilities to inventory software on endpoints. Microsoft Cloud App Security can identify unauthorized assets across multiple cloud capabilities. Security Center helps you identify Shadow IT subscriptions. By looking at subscriptions labeled not covered in your dashboard, you can know immediately when there are newly created subscriptions and make sure they are covered by your policies, and protected by Azure Security Center. The advanced monitoring capabilities in Security Center also let you track and manage compliance and governance over time. The overall compliance provides you with a measure of how much your subscriptions are compliant with policies associated with your workload. Non-compliant assets are a possible indication of unauthorized assets in the cloud environment. For more information, see What is Azure Security Center?
5) Monitor Anomalous Activity
Anomalous activity is an indicator of possible insider threat activity. Security teams can leverage user baseline activity, set deviation tolerances and alert on anomalies outside respective risk tolerances. Azure ATP monitors and analyzes user activities and information across your network, such as permissions and group membership, creating a behavioral baseline for each user. Azure ATP then identifies anomalies with adaptive built-in intelligence, giving you insights into suspicious activities and events, revealing the advanced threats, compromised users, and insider threats facing your organization. Azure ATP’s proprietary sensors monitor organizational domain controllers, providing a comprehensive view for all user activities from every device. Azure ATP alerts are reviewed on the Security Alerts Timeline. Each security alert provides the following information:
- Entities involved, including users, computers, servers, domain controllers, and resources.
- Times and time frame of the suspicious activities which initiated the security alert.
- Severity of the alert: High, Medium, or Low.
- Status: Open, closed, or suppressed.
- Security alert category:
- Reconnaissance
- Compromised credential
- Lateral movement
- Domain dominance
- Exfiltration
- Ability to:
- Share the security alert with other people in your organization via email.
- Download the security alert in Excel format.
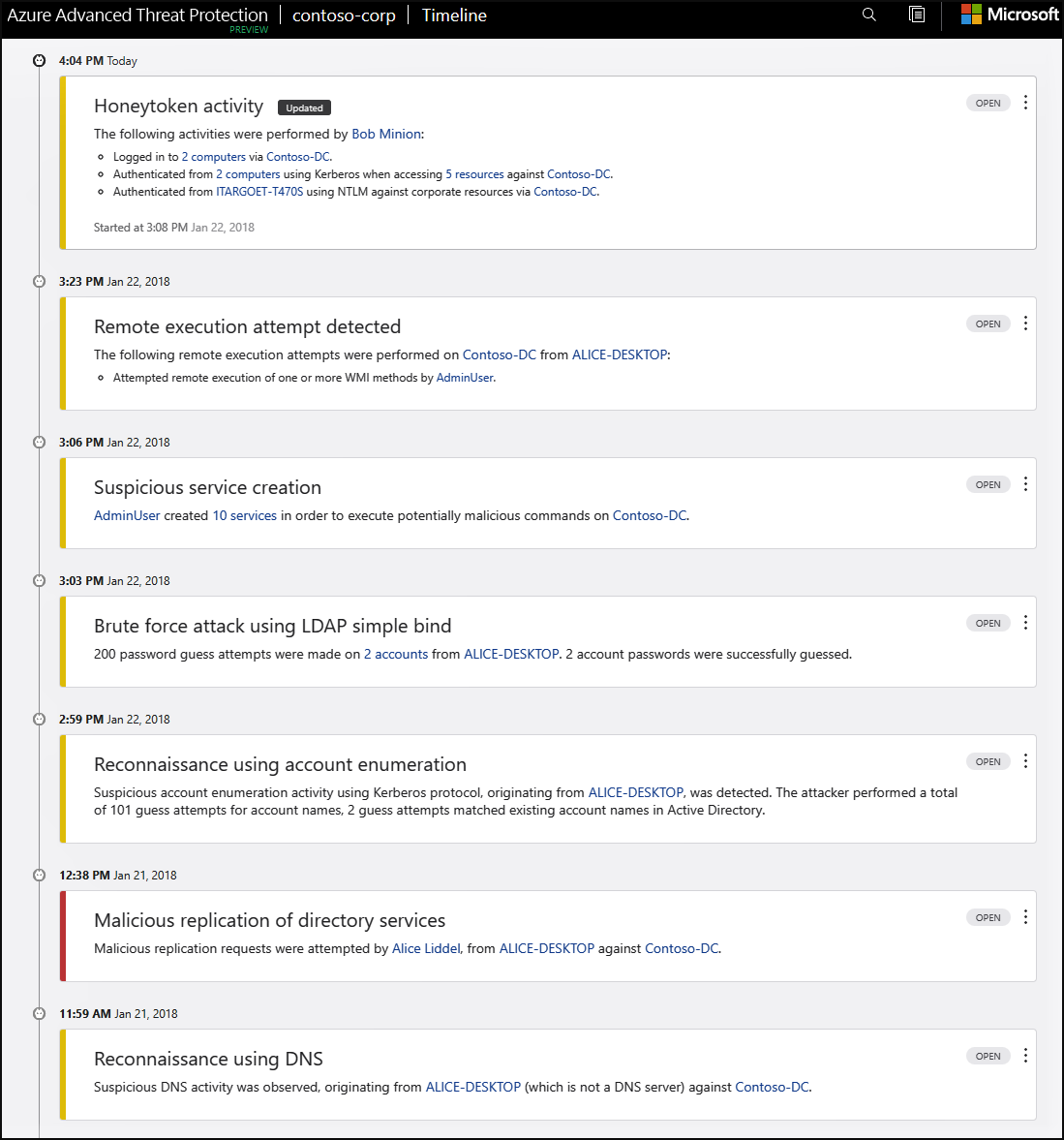
For more information, see Working with Security Alerts.
6) Employ Deception Techniques
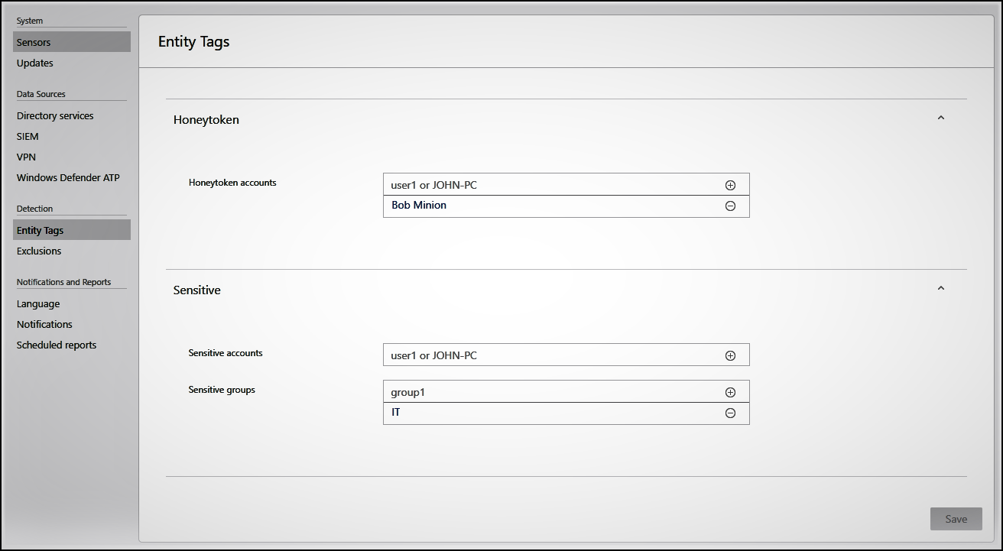
Zero Trust is based in an “assume breach mindset”. While there are several methods to detecting insider threats, evaluating true vs. false positive events in security monitoring is a challenging affair. What if there was a way to bring the insider threat to us? Deception techniques involve deflecting attacks away from critical assets and towards more attractive targets. These techniques include leveraging honeypots and honeynet tokens. A honeypot is an intentionally vulnerable asset hosting data of interest to an attacker or insider threat. This could include open file shares, passwords, insecure services and seemingly sensitive data. This technique allows cyber defenders to place a tripwire for insider threat detection as it is unlikely legitimate users would access these resources. Honeytoken accounts are a similar technique with decoy accounts set up to identify and track malicious activity that involves these accounts. Honeytoken accounts should be left unused, while having an attractive name to lure attackers (for example, SQL-Admin). Any activity from them might indicate malicious behavior. Security teams can host honeypot assets such as virtual machines, files and assets within the network and alert on access via integration with a SIEM solution such as Azure Sentinel. Honeypot assets can also host readily exposed honeytoken account credentials for a second layer of access monitoring. Azure ATP provides the capability to configure monitoring for honeytoken accounts. Leverage Azure ATP for honeynet account monitoring via the steps below:
- From the Azure ATP portal, click the settings icon and select Configuration.
- Under Detection, click Entity tags.
- Under Honeytoken accounts, enter the Honeytoken account name and click the + sign. The Honeytoken accounts field is searchable and automatically displays entities in your network. Click Save.
- Click Exclusions. Enter a user account or IP address to be excluded from the detection, for each type of threat.
- Click the plus The Add entity (user or computer) field is searchable and will autofill with entities in your network. Click Save
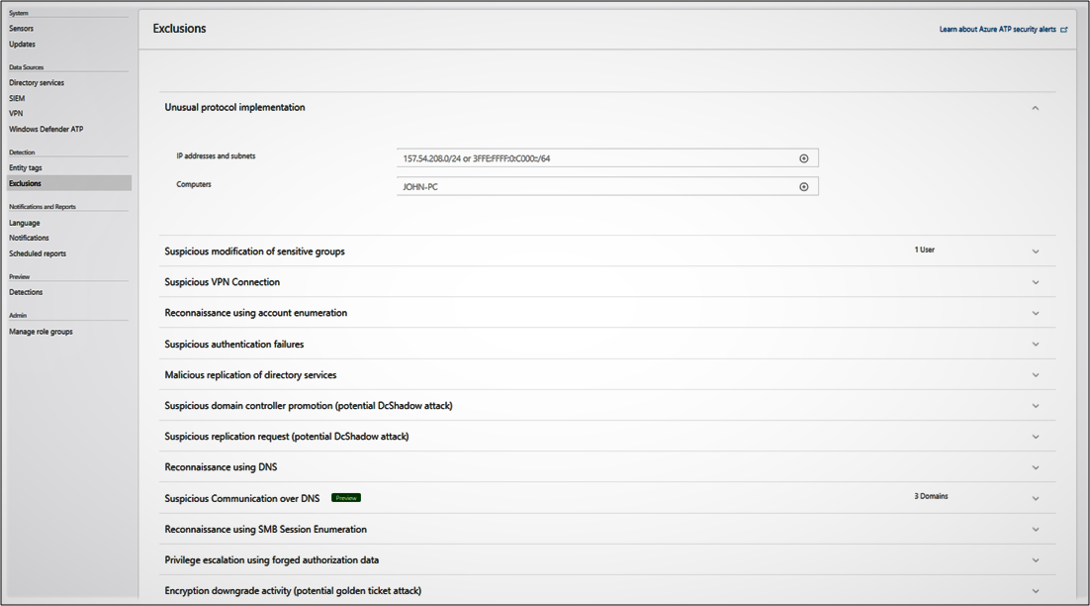
Check the attack timeline to view security alerts generated from detected activities and search for users or computers and view their profiles. For more information, see Configure detection exclusions and honeytoken accounts.
7) Identify & Analyze Risk
Azure ATP alert evidence and lateral movement paths provide clear indications when users have performed suspicious activities or indications exist that their account has been compromised. Investigation suggestions help determine the risk to your organization, decide how to remediate, and determine the best way to prevent similar future attacks. Azure ATP allows security teams to gather information about the user, investigate activities that the user performed, investigate resources the user accessed and investigate lateral movement paths. Azure ATP facilitates investigation steps for suspicious users to determine the following information which is critical for identifying and analyzing user risk to the organization:
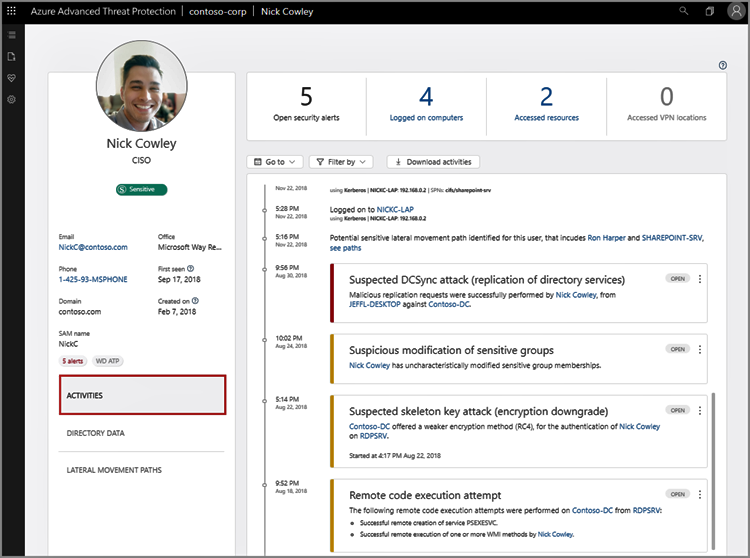
- Who is the user?
- Is the user a sensitive user (such as admin, or on a watchlist, etc.)?
- What is their role within the organization?
- Are they significant in the organizational tree?
- Suspicious activities to investigate:
- Does the user have other opened alerts in Azure ATP, or in other security tools such as Windows Defender-ATP, Azure Security Center and/or Microsoft CAS?
- Did the user have failed logons?
- Which resources did the user access?
- Did the user access high value resources?
- Was the user supposed to access the resources they accessed?
- Which computers did the user log in to?
- Was the user supposed to log in to those computers?
- Is there a lateral movement path (LMP) between the user and a sensitive user?
For more information, see Tutorial: Investigate a user.
8) Limit & Contain Threats
Identification of an insider threat may require remediation actions such as limiting access and containing the threat. Microsoft provides numerous resources for supporting this type of incident response. Microsoft Defender Advanced Threat Protection (MDATP) provides capabilities to contain the endpoint machine. Microsoft Cloud App Security can identify and restrict access across multiple cloud capabilities. Azure Firewall and Network Security Groups provide capabilities to block or limit access on the network. Azure Active Directory provides capabilities to temporarily or permanently restrict user access from the network. Azure Active Directory Identity Protection provides an automated capability for limiting threats in support of Zero Trust models. Identity Protection analyzes signals from each sign-in, both real-time and offline, and calculates a risk score. Administrators can decide based on this risk score signal to enforce organizational requirements. Administrators can choose to block access, allow access, or allow access but require multi-factor authentication. Configure and enable risk policies via the steps below:
- Navigate to the Azure portal.
- Browse to Azure Active Directory > Security > Identity Protection > Overview.
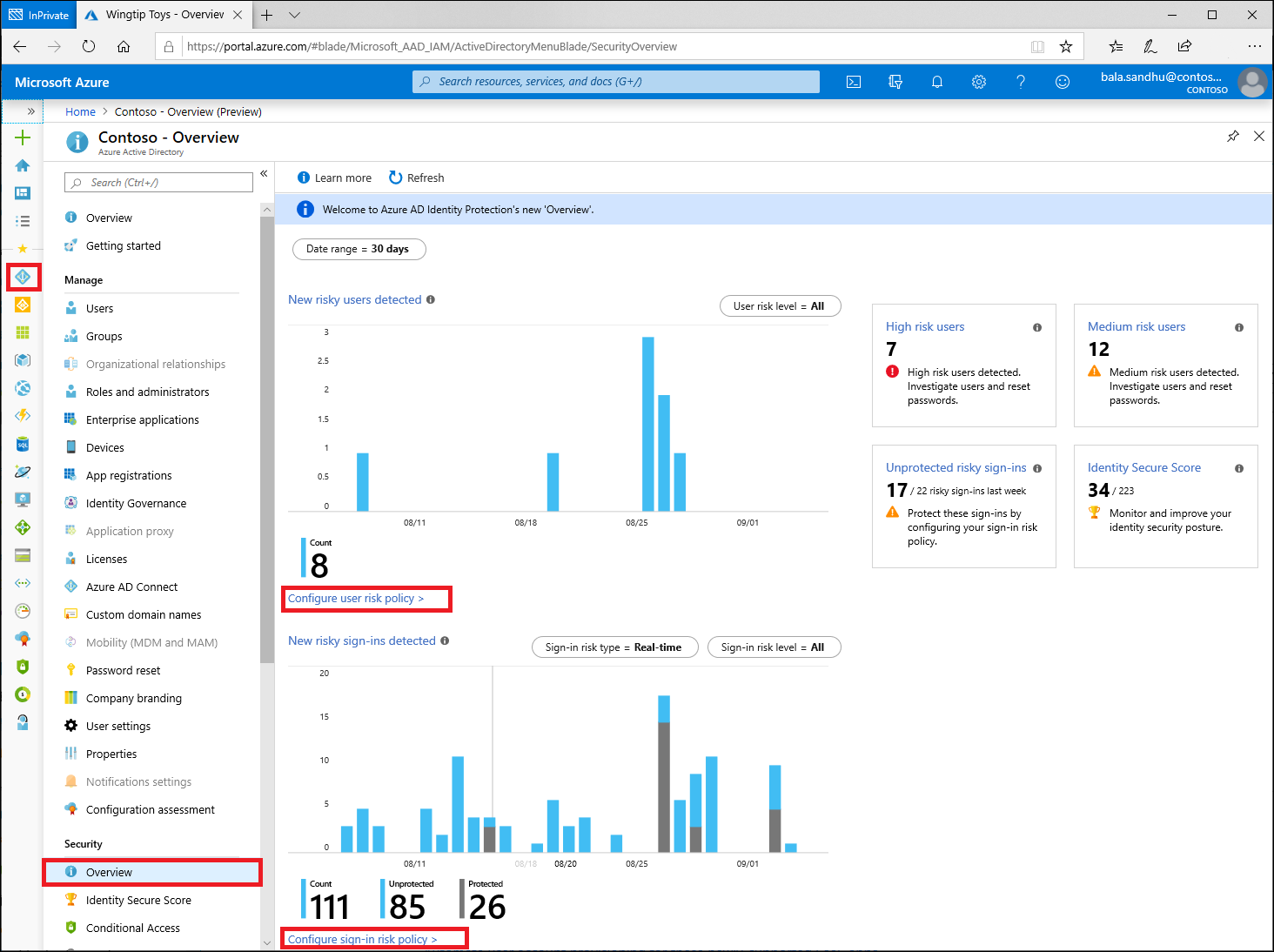
- Select Configure user risk policy.
- Under Assignments
- Users – Choose All users or Select individuals and groups if limiting your rollout.
- Conditions – User risk Microsoft’s recommendation is to set this option to High.
- Under Controls
- Access – Microsoft’s recommendation is to Allow access and Require password change.
- Enforce Policy – On
- Save – This action will return you to the Overview
- Under Assignments
- Select Configure sign-in risk policy.
- Under Assignments
- Users – Choose All users or Select individuals and groups if limiting your rollout.
- Conditions – Sign-in risk Microsoft’s recommendation is to set this option to Medium and above.
- Under Controls
- Access – Microsoft’s recommendation is to Allow access and Require multi-factor authentication.
- Enforce Policy – On
- Save
- Under Assignments
For more information, see Identity Protection policies and How To: Configure and enable risk policies.
Learn more about Zero Trust with Microsoft
Here are some of the best resource to learn more about Zero Trust in the cloud with Microsoft:
- Reach the Optimal State in your Zero Trust Journey
- The Zero Trust Maturity Model
- Zero Trust: A New Era of Security
- Implementing a Zero Trust Security Model at Microsoft
- Zero Trust Strategy: What Good Looks Like
- Securing Mobile: Designing SaaS Service Implementations to Meet Federal TIC Policy
Be sure to check out the other topics we have covered in this series:
- Implementing Zero Trust with Microsoft Azure: Identity and Access Management
- Protecting Cloud Workloads for Zero Trust with Azure Security Center
- Monitoring Cloud Security for Zero Trust with Azure Sentinel
- Enforcing Policy for Zero Trust with Azure Policy
- Supply Chain Risk Management for Zero Trust with Microsoft Azure
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.
[i] National Institute of Standards and Technology. (2019, September 1). Draft NIST Special Publication 800-207: Zero Trust Architecture. Retrieved January 25, 2020, from https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207-draft.pdf
[ii] Cybersecurity and Infrastructure Security Agency. (2019, December 1). Trusted Internet Connections 3.0: Volume 3 Security Capabilities Handbook. Retrieved January 22, 2020, from https://www.cisa.gov/sites/default/files/publications/Draft%20TIC%203.0%20Vol.%203%20Security%20Capabilities%20Handbook.pdf
[iii] National Institute of Standards and Technology. (2018, April 16). Framework for Improving Critical Infrastructure Cybersecurity. Retrieved January 22, 2020, from https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf

 Light
Light Dark
Dark
0 comments