This is the seventh in a ten-part blog series where we’ll demonstrate principles of the Cybersecurity Maturity Model Certification aligned with Microsoft Azure. Subsequent blogs in the series will delve into security assessment & risk management, system & communications protection and system & information integrity. In this seventh blog of the series we will explore how to leverage Microsoft Azure for recovery & risk management.
Please note that the information cutoff date for this post is October 2020, and that as of the date of this writing, CMMC developments and guidance are in progress. Additionally, as of the date of this writing, the CMMC Accreditation Body has not certified any the third-party assessors and guidance on the formal assessment process is still under development. As a result, the information herein, including our CMMC related offerings, may be enhanced in the future to align with future guidance from the DoD and CMMC Accreditation Body. Microsoft is closely tracking developments related to the CMMC.
Here are all the blogs in our CMMC series:
- Access Control Maturity
- Audit & Accountability Maturity
- Asset & Configuration Management Maturity
- Identification & Authentication Maturity
- Incident Response Maturity
- Maintenance & Media Protection Maturity
- Recovery & Risk Management Maturity
- Security Assessment & Situational Awareness Maturity
- System & Communications Protection Maturity
- System & Information Integrity Maturity
What is Cybersecurity Maturity Model Certification (CMMC)?
 The Defense Industrial Base (DIB) is charged with implementing Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012. DFARS requires organizations supporting the Department of Defense (DoD) to implement NIST SP 800-171 and FedRAMP Moderate Impact level controls. DoD has mandated CMMC with periodic assessments in order to strengthen cybersecurity across the DIB. CMMC builds upon DFARS 7012 by verifying an organization’s readiness to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) such as International Traffic in Arms Regulation (ITAR) and Export Administration Regulations (EAR) export-controlled data.
The Defense Industrial Base (DIB) is charged with implementing Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012. DFARS requires organizations supporting the Department of Defense (DoD) to implement NIST SP 800-171 and FedRAMP Moderate Impact level controls. DoD has mandated CMMC with periodic assessments in order to strengthen cybersecurity across the DIB. CMMC builds upon DFARS 7012 by verifying an organization’s readiness to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) such as International Traffic in Arms Regulation (ITAR) and Export Administration Regulations (EAR) export-controlled data.
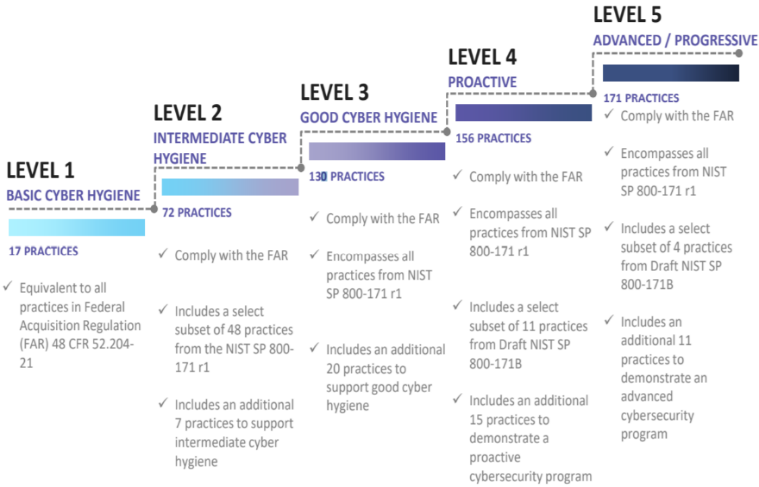
CMMC extends beyond the parent organization into sub-contractors, partners, and suppliers. The framework is intended to enforce critical thinking approaches for comprehensive security. The CMMC framework specifies 5 levels of maturity measurement from Maturity Level 1 (Basic Cyber Hygiene) to Maturity Level 5 (Proactive & Advanced Cyber Practice). The Certification levels will be determined through audits from independent, third-party assessment organizations (C3PAO).
What preparation is required for CMMC alignment to risk & recovery management?
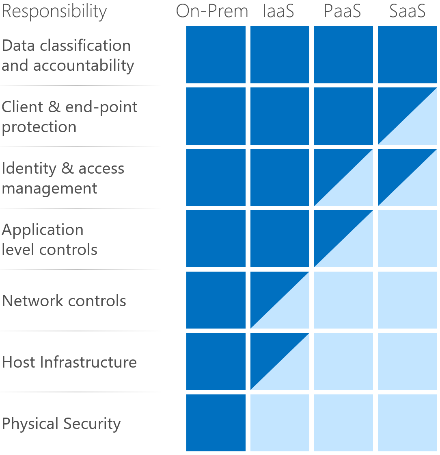
It’s important to understand that compliance is a shared responsibility between the customer and the Cloud Services Provider (CSP). The graphic on the left demonstrates the CSP responsibility in respective cloud models (On-Prem, IaaS, PaaS, SaaS) with dark blue aligning with customer responsibility and light blue aligning with CSP responsibility. For example, CMMC requirements such as Physical Protection (PE) for limiting physical access (C028) is managed by the CSP. Establishment of respective policies and procedures are the customer’s responsibility. It’s important to note that this blog series is aligned with setting the foundation of controls for CMMC Maturity Levels 1 & 2. Once C3PAOs are identified by the CMMC Accreditation Body, customers are advised to work with their respective C3PAO for guidance on comprehensive alignment of controls, audit and certification.
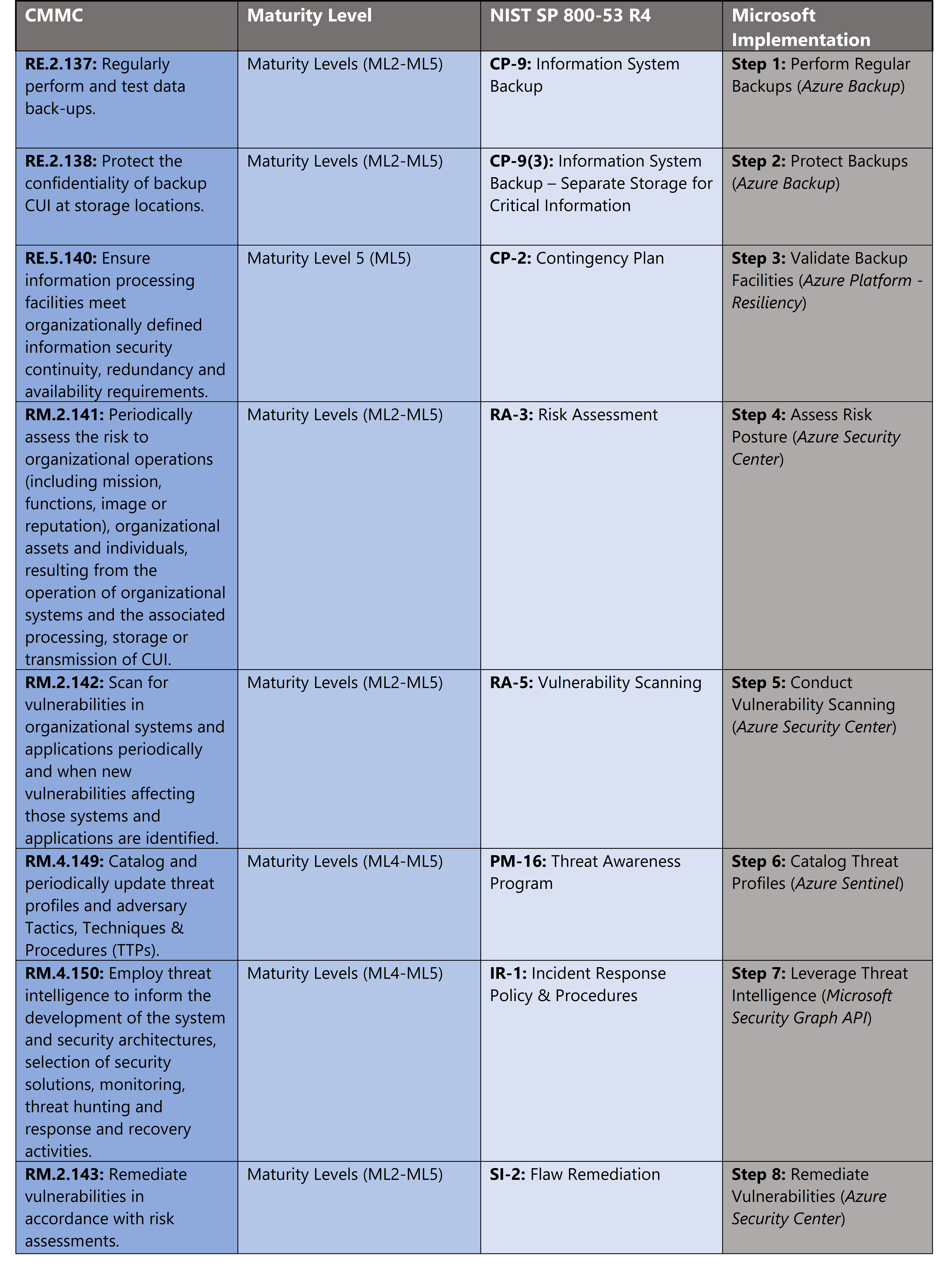
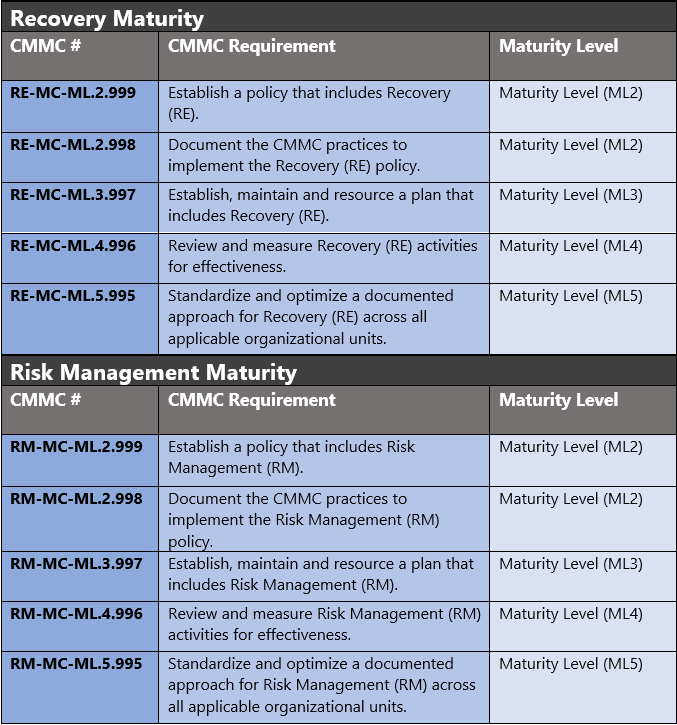
The administrative controls for the CMMC Recovery Maturity (RE-MC) and Risk Management Maturity (RM-MC) are listed here. These controls fall within the customer’s responsibility. This starts with establishing polices to include recovery & risk management (ML2) and progresses to a documented approach across all applicable organizational units (ML5). These controls should be formally created, documented in the System Security Plan (SSP) and implemented within the organization.
Microsoft Azure Security Controls Aligned to CMMC: Recovery & Risk Management
Azure Security Controls Aligned to CMMC: Recovery & Risk Management
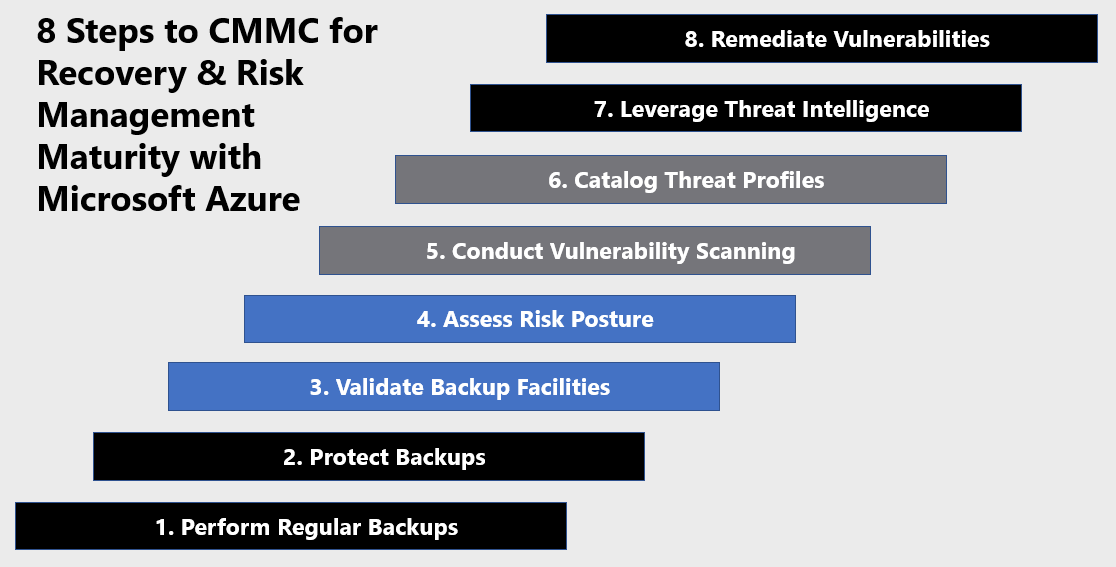
Microsoft Azure Government has developed an 8-step process to facilitate recovery & risk management with the security principles within CMMC, NIST SP 800-53 R4 and NIST SP 800-171 standards. Note this process is a starting point, as CMMC requires alignment of people, processes, policy and technology so refer to organizational requirements and respective standards for implementation. Azure has several offerings to facilitate recovery & risk management including Azure Backup, Azure Security Center, Azure Sentinel and the Microsoft Graph Security API.
- Azure Backup facilitates backups for Azure Virtual Machines, SQL workloads, and on-premises VMware machines without additional infrastructure. Encrypt data and keep it for extended periods, even after legitimate deletion, through multifactor authentication.
- Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud – whether they’re in Azure or not – as well as on premises.
- Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
- Microsoft Graph Security API simplifies integration with Microsoft and third-party security solutions. Using one endpoint, one software development kit (SDK), one schema, and one authentication mechanism, customers and partners can easily build integrated security applications, workflows and analytics.
8 Steps to CMMC for Recovery & Risk Management with Microsoft Azure
1) Perform Regular Backups
Regular backups ensure continuity and availability in the event of a disaster. The Azure Backup service provides simple, secure, and cost-effective solutions to back up your data and recover it from the Microsoft Azure cloud. Azure Backup provides redundancy for on-premises systems/files, Azure VMs, Azure File shares and various databases.
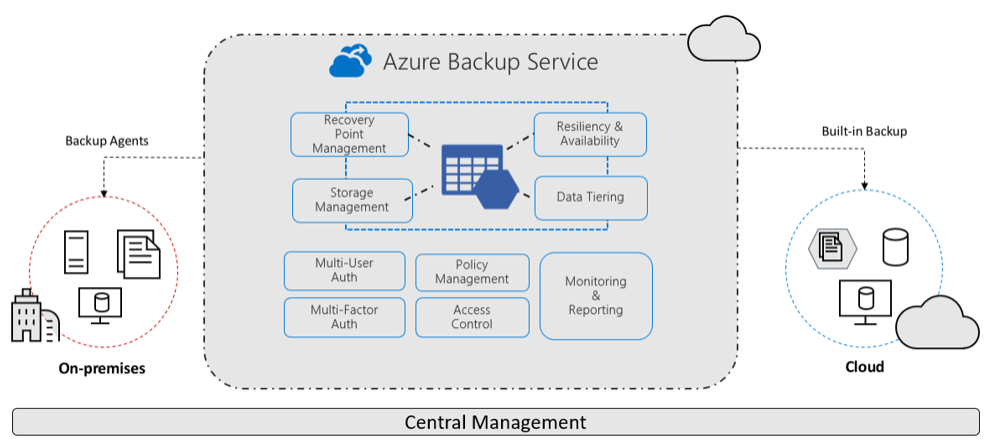
Azure Backup provides several benefits which are listed below. For more information, see What is the Azure Backup service?
- Offload on-premises backup: Azure Backup offers a simple solution for backing up your on-premises resources to the cloud. Get short and long-term backup without the need to deploy complex on-premises backup solutions.
- Back up Azure IaaS VMs: Azure Backup provides independent and isolated backups to guard against accidental destruction of original data. Backups are stored in a Recovery Services vault with built-in management of recovery points. Configuration and scalability are simple, backups are optimized, and you can easily restore as needed.
- Scale easily: Azure Backup uses the underlying power and unlimited scale of the Azure cloud to deliver high availability with no maintenance or monitoring overhead.
- Get unlimited data transfer: Azure Backup doesn’t limit the amount of inbound or outbound data you transfer, or charge for the data that is transferred.
- Keep data secure: Azure Backup provides solutions for securing data in transit and at rest.
- Centralized monitoring and management: Azure Backup provides built-in monitoring and alerting capabilities in a Recovery Services vault. These capabilities are available without any additional management infrastructure. You can also increase the scale of your monitoring and reporting by using Azure Monitor.
- Get app-consistent backups: An application-consistent backup means a recovery point has all required data to restore the backup copy. Azure Backup provides application-consistent backups, which ensure additional fixes aren’t required to restore the data. Restoring application-consistent data reduces the restoration time, allowing you to quickly return to a running state.
- Retain short and long-term data: You can use Recovery Services vaults for short-term and long-term data retention.
- Automatic storage management: Hybrid environments often require heterogeneous storage – some on-premises and some in the cloud. With Azure Backup, there’s no cost for using on-premises storage devices. Azure Backup automatically allocates and manages backup storage and it uses a pay-as-you-use model.
- Multiple storage options: Azure Backup offers two types of replication to keep your storage/data highly available.
- Locally redundant storage (LRS) replicates your data three times (it creates three copies of your data) in a storage scale unit in a datacenter. All copies of the data exist within the same region. LRS is a low-cost option for protecting your data from local hardware failures.
- Geo-redundant storage (GRS) is the default and recommended replication option. GRS replicates your data to a secondary region (hundreds of miles away from the primary location of the source data). GRS costs more than LRS, but GRS provides a higher level of durability for your data, even if there’s a regional outage.
2) Protect Backups
There are several methods to protecting backups including access management, redundancy and encryption. Azure Role-Based Access Control (RBAC) enables fine-grained access management for Azure. Using RBAC, you can segregate duties within your team and grant only the amount of access to users that they need to perform their jobs. Azure Backup provides three built-in roles to control backup management operations. For more information, see Use Role-Based Access Control to manage Azure Backup recovery points.
- Backup Contributor: This role has all permissions to create and manage backup except deleting Recovery Services vault and giving access to others. Imagine this role as admin of backup management who can do every backup management operation.
- Backup Operator: This role has permissions to everything a contributor does except removing backup and managing backup policies. This role is equivalent to contributor except it can’t perform destructive operations such as stop backup with delete data or remove registration of on-premises resources.
- Backup Reader: This role has permissions to view all backup management operations. Imagine this role to be a monitoring person.
Concerns about security issues, like malware, ransomware, and intrusion, are increasing. These security issues can be costly, in terms of both money and data. To guard against such attacks, Azure Backup now provides security features to help protect backup data even after deletion.
One such feature is soft delete. With soft delete, even if a malicious actor deletes the backup of a VM (or backup data is accidentally deleted), the backup data is retained for 14 additional days, allowing the recovery of that backup item with no data loss. The additional 14 days retention of backup data in the “soft delete” state don’t incur any cost to the customer. Azure also encrypts all the backed-up data at rest using Storage Service Encryption to further secure your data. For more information, see Security features to help protect cloud workloads that use Azure Backup.
All your backed-up data is automatically encrypted when stored in the cloud using Azure Storage encryption, which helps you meet your security and compliance commitments. This data at rest is encrypted using 256-bit AES encryption, one of the strongest block ciphers available, and is FIPS 140-2 compliant. In addition to encryption at rest, all your backup data in transit is transferred over HTTPS. It always remains on the Azure backbone network. For more information, see Azure Storage encryption for data at rest.
3) Validate Backup Facilities
Azure backups are distributed through Azure data centers which adhere to strict standards of confidentiality, integrity and availability. Azure is composed of a globally distributed datacenter infrastructure, supporting thousands of online services and spanning more than 100 highly secure facilities worldwide. The infrastructure is designed to bring applications closer to users around the world, preserving data residency, and offering comprehensive compliance and resiliency options for customers. Azure has 52 regions worldwide and is available in 140 countries/regions.
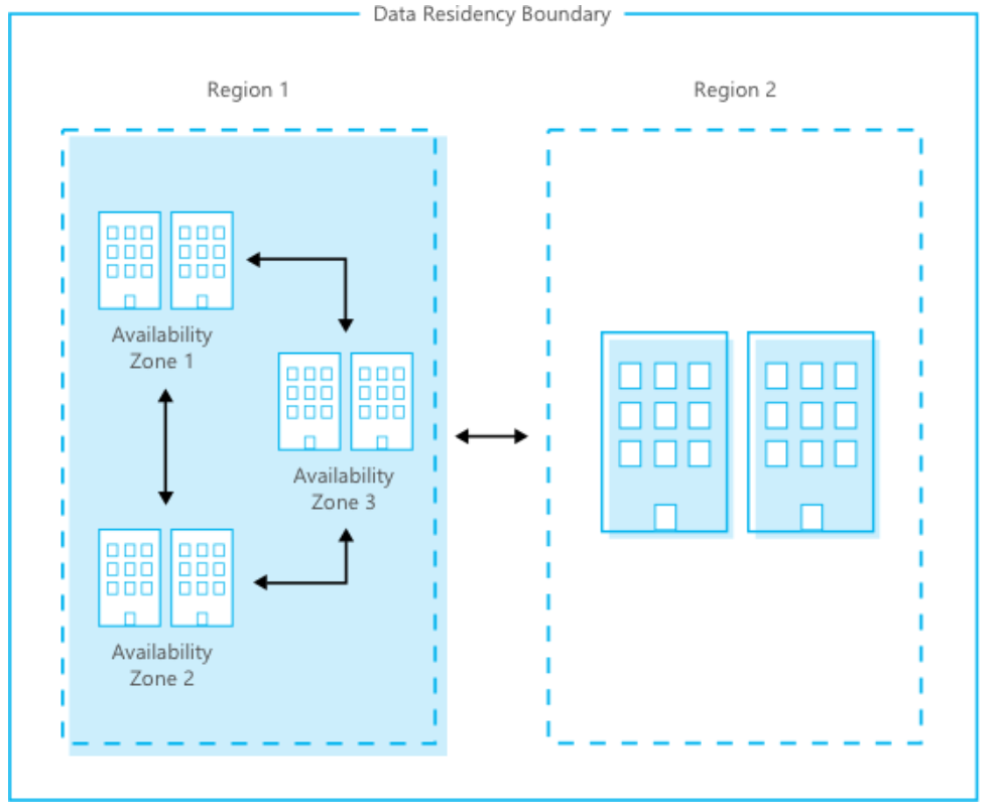
The Microsoft Cloud Infrastructure and Operations team designs, builds, operates, and improves the security of the cloud infrastructure. This team ensures that the Azure infrastructure is delivering high availability and reliability, high efficiency, and smart scalability. The team provides a more secure, private, and trusted cloud.
Uninterruptible power supplies and vast banks of batteries ensure that electricity remains continuous if a short-term power disruption occurs. Emergency generators provide backup power for extended outages and planned maintenance. If a natural disaster occurs, the datacenter can use onsite fuel reserves.
High-speed and robust fiber optic networks connect datacenters with other major hubs and internet users. Compute nodes host workloads closer to users to reduce latency, provide geo-redundancy, and increase overall service resiliency. A team of engineers works around the clock to ensure services are persistently available.
Microsoft ensures high availability through advanced monitoring and incident response, service support, and backup failover capability. Geographically distributed Microsoft operations centers operate 24/7/365. The Azure network is one of the largest in the world. The fiber optic and content distribution network connect datacenters and edge nodes to ensure high performance and reliability.
- Disaster Recovery: Azure keeps your data durable in two locations. You can choose the location of the backup site. In both locations, Azure constantly maintains three healthy replicas of your data.
- Database Availability: Azure ensures that a database is internet accessible through an internet gateway with sustained database availability. Monitoring assesses the health and state of the active databases at five-minute time intervals.
- Storage Availability: Azure delivers storage through a highly scalable and durable storage service, which provides connectivity endpoints. This means that an application can access the storage service directly. The storage service processes incoming storage requests efficiently, with transactional integrity. For more information, see Azure infrastructure availability.
4) Assess Risk Posture
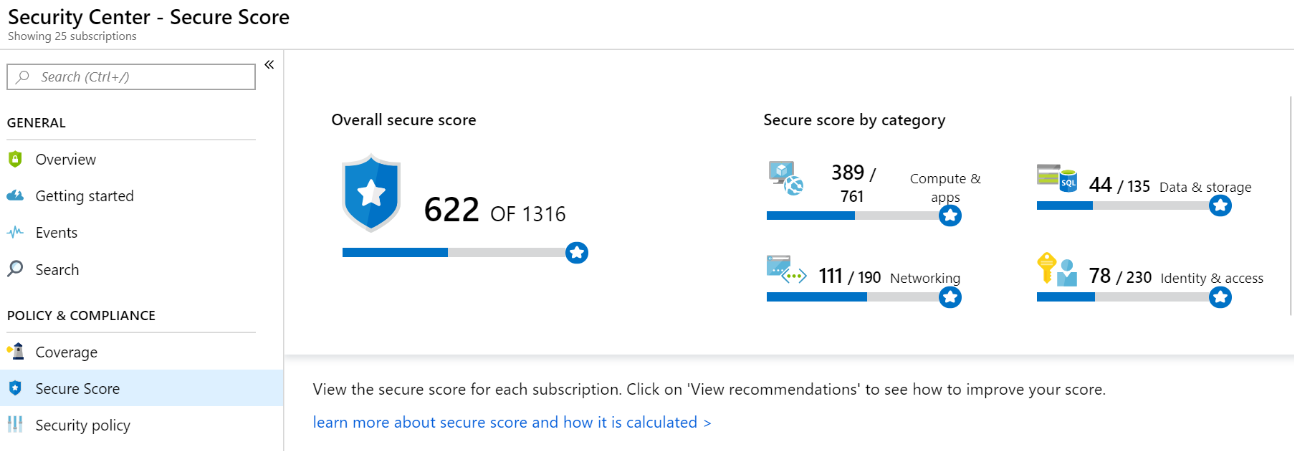
Azure Security Center provides the Secure Score calculation to provide a readily consumable assessment of your risk posture. Security Center mimics the work of a security analyst, reviewing your security recommendations and applying advanced algorithms to determine how crucial each recommendation is. Azure Security center constantly reviews your active recommendations and calculates your Secure Score based on them, the score of a recommendation is derived from its severity and security best practices that will affect your workload security the most. Security Center also provides you with an Overall Secure Score.
Overall Secure Score is an accumulation of all your recommendation scores. You can view your overall Secure Score across your subscriptions or management groups, depending on what you select. The score will vary based on subscription selected and the active recommendations on these subscriptions. To check which recommendations impact your Secure Score most, you can view the top three most impactful recommendations in the Security Center dashboard or you can sort the recommendations in the recommendations list blade using the Secure Score impact column. View your overall Secure Score via the steps below. For more information, see Improve your secure score in Azure Security Center.
- In the Azure dashboard, click Security Center and then click Secure Score.
- At the top you can see Secure Score highlights:
- The Overall Secure Score represents the score per policies, per selected subscription
- Secure Score by category shows you which resources need the most attention
- Top recommendations by Secure Score impact provides you with a list of the recommendations that will improve your Secure Score the most if you implement them.

5) Conduct Vulnerability Scanning
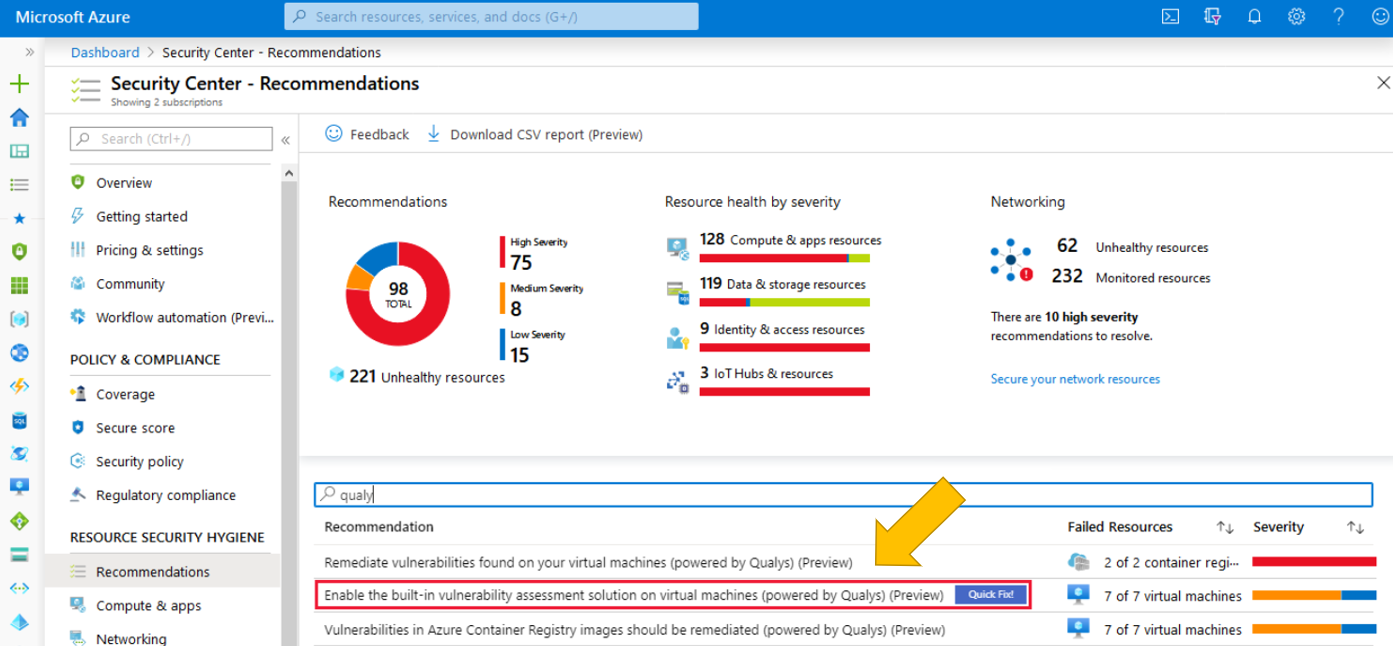
Azure Security Center includes a built-in vulnerability scanner powered by Qualys. There is also capability for direct integration with the vulnerability scanner of your choice via the Azure Security Marketplace. Qualys’s scanner is the leading tool for real-time identification of vulnerabilities in your Azure Virtual Machines. It’s only available to users on the standard pricing tier. You don’t need a Qualys license or even a Qualys account – everything’s handled seamlessly inside Security Center. Deploy the Qualys built-in vulnerability scanner with the steps below. For more information, see Integrated vulnerability scanner for virtual machines (Standard tier only).
- Open Azure Security Center and go to the Recommendations page.

- Select the recommendation named “Enable the built-in vulnerability assessment solution on virtual machines (powered by Qualys)”. Your VMs will appear in one or more of the following groups:
- Healthy resources: the vulnerability scanner extension has been deployed to these VMs.
- Unhealthy resources: the vulnerability scanner extension can be deployed to these VMs.
- Not applicable resources: these VMs can’t have the vulnerability scanner extension deployed.
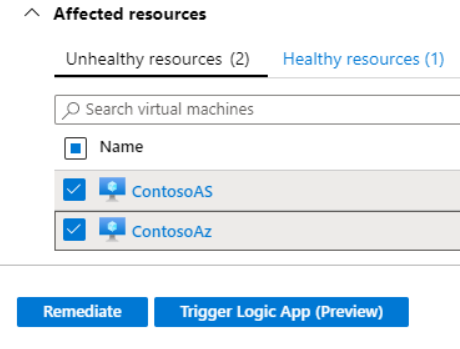
- From the Unhealthy resources tab, select the VMs on which you want to deploy the Qualys scanner and click Remediate. The scanner extension will be installed on all the selected VMs. Scanning begins automatically as soon as the extension is successfully deployed. Scans will then run at four-hour intervals.

6) Catalog Threat Profiles
We’ve highlighted how to enable Azure Sentinel and how to get started with threat hunting in previous blogs in this series. Azure Sentinel provides hunting capabilities to align cyber defenders to threat tactics and facilitate building threat profiles. These profiles allow cyber defenders to target the phase of the attack lifecycle. Azure Sentinel hunting is aligned to the MITRE ATT&CK™ (adversarial tactics, techniques, and common knowledge) framework. These adversary tactics and techniques are grouped within a matrix and include the following categories listed below. For more information, see Threat hunting: Part 1—Why your SOC needs a proactive hunting team.
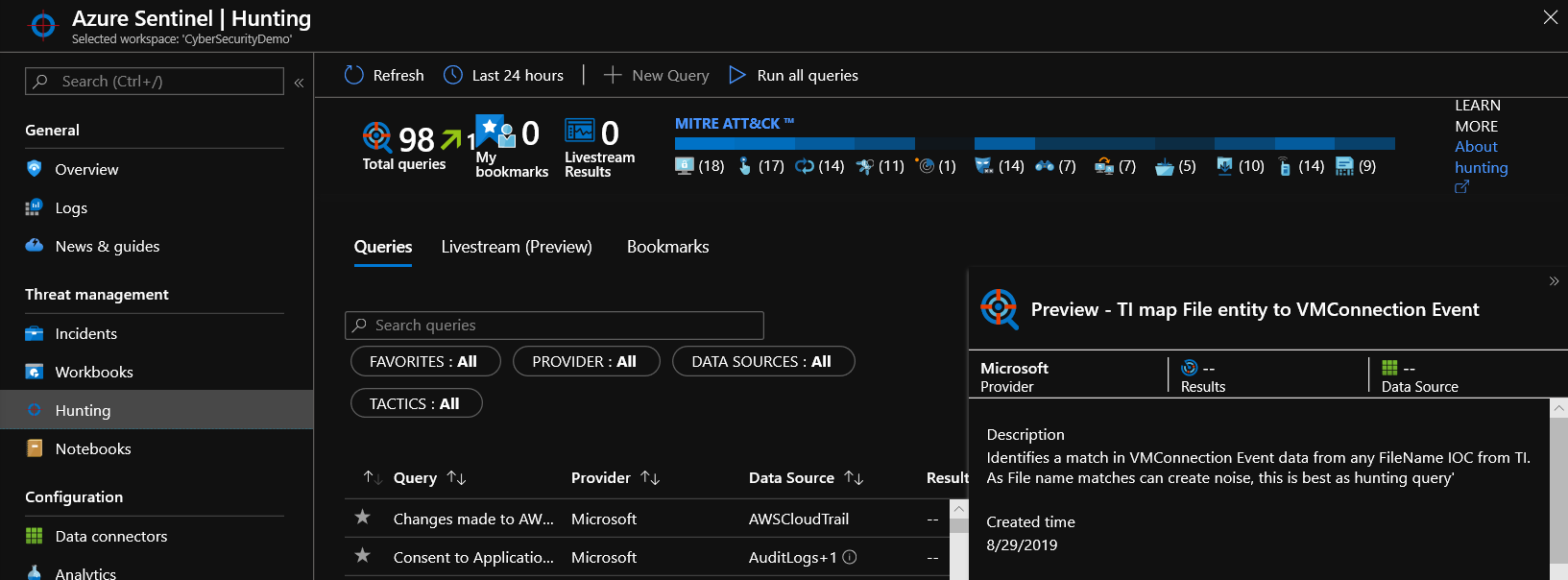
- Initial access: Techniques used by the adversary to obtain a foothold within a network, such as targeted spear-phishing, exploiting vulnerabilities or configuration weaknesses in public-facing systems.
- Execution: Techniques that result in an adversary running their code on a target system. For example, an attacker may run a PowerShell script to download additional attacker tools and/or scan other systems.
- Persistence: Techniques that allow an adversary to maintain access to a target system, even following reboots and credential changes. An example of a persistence technique would be an attacker creating a scheduled task that runs their code at a specific time or on reboot.
- Privilege escalation: Techniques leveraged by an adversary to gain higher-level privileges on a system, such as local administrator or root.
- Defense evasion: Techniques used by attackers to avoid detection. Evasion techniques include hiding malicious code within trusted processes and folders, encrypting or obfuscating adversary code, or disabling security software.
- Credential access: Techniques deployed on systems and networks to steal usernames and credentials for re-use.
- Discovery: Techniques used by adversaries to obtain information about systems and networks that they are looking to exploit or use for their tactical advantage.
- Lateral movement: Techniques that allow an attacker to move from one system to another within a network. Common techniques include “Pass-the-Hash” methods of authenticating users and the abuse of the remote desktop protocol.
- Collection: Techniques used by an adversary to gather and consolidate the information they were targeting as part of their objectives.
- Command and control: Techniques leveraged by an attacker to communicate with a system under their control. One example is that an attacker may communicate with a system over an uncommon or high-numbered port to evade detection by security appliances or proxies.
- Exfiltration: Techniques used to move data from the compromised network to a system or network fully under control of the attacker.
- Impact: Techniques used by an attacker to impact the availability of systems, networks, and data. Methods in this category would include denial of service attacks and disk- or data-wiping software.
7) Leverage Threat Intelligence
Millions of unique threat indicators are generated every day by Microsoft and its partners and shared across Microsoft products and services. That provides an unparalleled view into the evolving threat landscape and enables rapid innovation to detect and respond to threats. The Microsoft Intelligent Security Graph uses advanced analytics to link a massive amount of threat intelligence and security data from Microsoft and partners to combat cyberthreats. Insights from the Intelligent Security Graph power real-time threat protection in Microsoft products and services. Also, many organizations utilize threat intelligence platform (TIP) solutions to aggregate threat indicator feeds from a variety of sources. If your organization utilizes an integrated TIP solution the platforms data connector allows you leverage your TIP to import threat indicators into Azure Sentinel. The Threat Intelligence Platforms data connector works with the Microsoft Graph Security tiIndicators API to bring threat indicators into Azure. For more information, see Bring your threat intelligence to Azure Sentinel.
8) Remediate Vulnerabilities
Risk assessment highlights respective vulnerabilities. The severity of risk and it’s assessed impact on your organization sets a priority list for remediation. Azure Security Center Secure Score highlights vulnerability and rank orders by severity to facilitate remediation. Each recommendation includes detailed remediation steps and respective documentation. Remediating vulnerabilities at scale can be a challenge. What if 1,000 of your virtual machines require a port closed on their host-based firewalls?
In order to simplify remediation of security misconfigurations and to be able to quickly improve your secure score, we are introducing a new capability that allows you to remediate a recommendation on a bulk of resources in a single click. This operation will allow you to select the resources you want to apply the remediation to and launch a remediation action that will configure the setting on your behalf. Single click remediation is available today for preview customers as part of the Security Center recommendations blade. You can look for the 1-click fix label next to the recommendation and click on the recommendation:
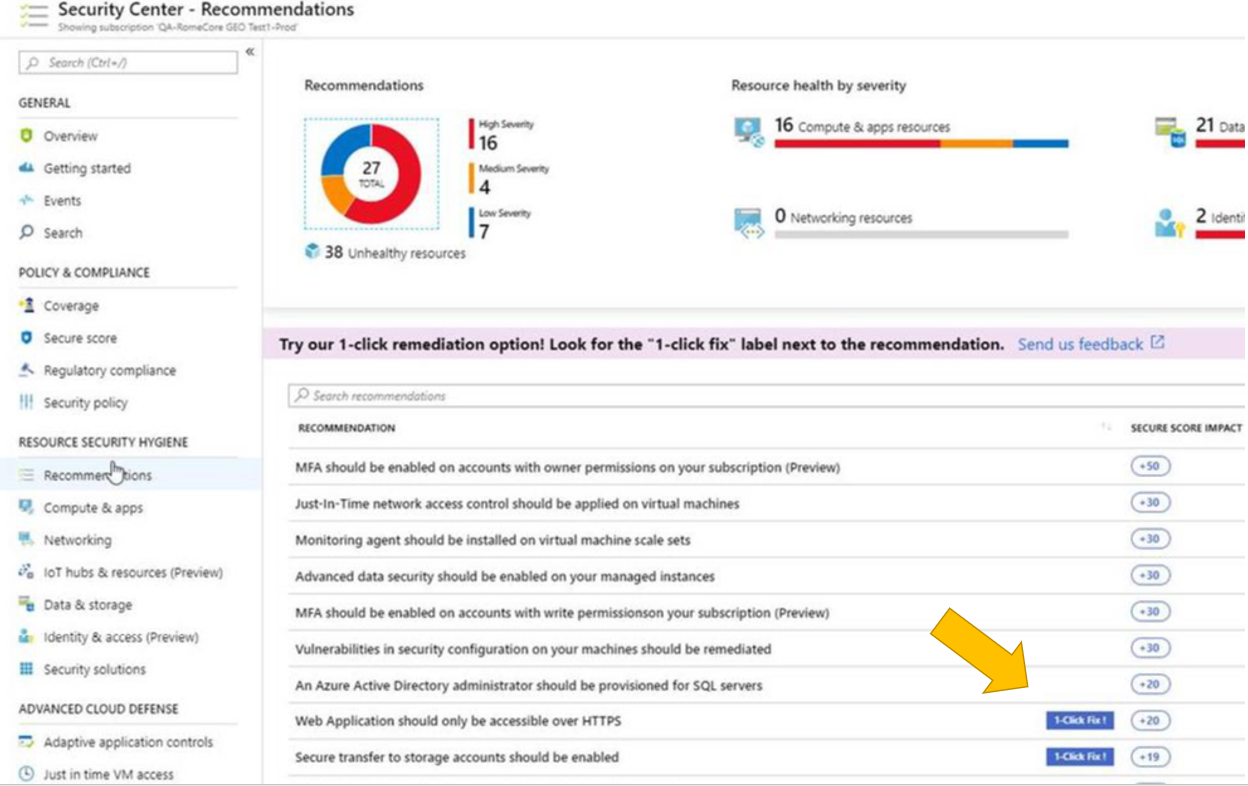
Single click remediation is part of the Azure Security Center free tier. Single-click remediations include policies to fix common vulnerabilities listed below. For more information, see Azure Security Center single click remediation.
- Web Apps, Function Apps, and API Apps should only be accessible over HTTPS
- Remote debugging should be turned off for Function Apps, Web Apps, and API Apps
- CORS should not allow every resource to access your Function Apps, Web Apps, or API Apps
- Secure transfer to storage accounts should be enabled
- Transparent data encryption for Azure SQL Database should be enabled
- Monitoring agent should be installed on your virtual machines
- Diagnostic logs in Azure Key Vault and Azure Service Bus should be enabled
- Diagnostic logs in Service Bus should be enabled
- Vulnerability assessment should be enabled on your SQL servers
- Advanced data security should be enabled on your SQL servers
- Vulnerability assessment should be enabled on your SQL managed instances
- Advanced data security should be enabled on your SQL managed instances
Learn more about CMMC with Microsoft
Here are some of the best resource to learn more about CMMC in the cloud with Microsoft:
- Accelerating CMMC compliance for Microsoft cloud (in depth review)
- CMMC-AB Standards with Regan Edens – National Conversation
- Defense Federal Acquisition Regulation Supplement (DFARS)
- International Traffic in Arms Regulations (ITAR)
- Federal Risk and Authorization Management Program (FedRAMP)
- US Export Administration Regulations (EAR)
- NIST SP 800-171 Compliance
- Overview of the NIST SP 800-53 R4 blueprint sample
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.

Maybe I missed it, but where is the Azure mappings for Maturity Level 1 (there are two controls from this domain in it). Also, I see that the Azure mappings for System & Information Integrity Domain were supposed to be live 5/28/2020 – it is mid July and still not posted. The rule change take effect in October, and entities are trying to prepare. Would be great to finish these mappings for ML1 & ML3.
Thanks!
Cary
Cary,
Thanks for your question and for following our blog series. All 10 blogs in the series are published on Azure Government Devblogs and below is a link: https://devblogs.microsoft.com/azuregov/cmmc-with-microsoft-azure-system-information-integrity-10-of-10/ Recovery (RE) and Risk Management (RM) do not have controls listed for ML1, as controls for these domains start at ML2. Feel free to refer to DoD respective guidance per the link below: https://www.acq.osd.mil/cmmc/draft.html