This is the fourth in a ten-part blog series where we’ll demonstrate principles of the Cybersecurity Maturity Model Certification aligned with Microsoft Azure. Subsequent blogs in the series will delve into incident response, maintenance & media protection, recovery & risk management, security assessment & risk management, system & communications protection and system & information integrity. In this fourth blog of the series we will explore how to leverage Microsoft Azure for identification & authentication maturity.
Please note that the information cutoff date for this post is October 2020, and that as of the date of this writing, CMMC developments and guidance are in progress. Additionally, as of the date of this writing, the CMMC Accreditation Body has not certified any the third-party assessors and guidance on the formal assessment process is still under development. As a result, the information herein, including our CMMC related offerings, may be enhanced in the future to align with future guidance from the DoD and CMMC Accreditation Body. Microsoft is closely tracking developments related to the CMMC.
Stay tuned for the published and upcoming CMMC blogs in the series:
- Access Control Maturity – live
- Audit & Accountability Maturity – live
- Asset & Configuration Management Maturity – live
- Identification & Authentication Maturity – this blog
- Incident Response Maturity – live
- Maintenance & Media Protection Maturity – live
- Recovery & Risk Management Maturity – live
- Security Assessment & Situational Awareness Maturity – live
- System & Communications Protection Maturity – live
- System & Information Integrity Maturity (5/28)
What is Cybersecurity Maturity Model Certification (CMMC)?
The Defense Industrial Base (DIB) is charged with implementing Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012. DFARS requires organizations supporting the Department of Defense (DoD) to implement NIST SP 800-171 and FedRAMP Moderate Impact level controls. DoD has mandated CMMC with periodic assessments in order to strengthen cybersecurity across the DIB. CMMC builds upon DFARS 7012 by verifying an organization’s readiness to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) such as International Traffic in Arms Regulation (ITAR) and Export Administration Regulations (EAR) export-controlled data.
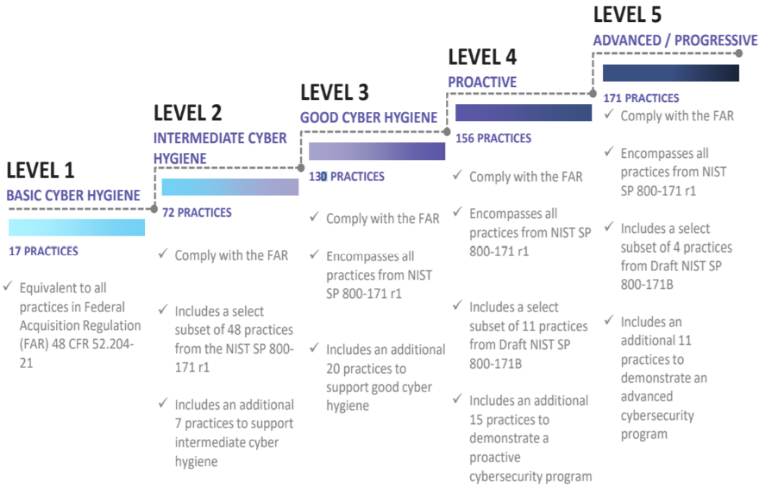
CMMC extends beyond the parent organization into sub-contractors, partners, and suppliers. The framework is intended to enforce critical thinking approaches for comprehensive security. The CMMC framework specifies 5 levels of maturity measurement from Maturity Level 1 (Basic Cyber Hygiene) to Maturity Level 5 (Proactive & Advanced Cyber Practice). The Certification levels will be determined through audits from independent, third-party assessment organizations (C3PAO).
What preparation is required for CMMC alignment to identification & authentication management?

It’s important to understand that compliance is a shared responsibility between the customer and the Cloud Services Provider (CSP). The graphic on the left demonstrates the CSP responsibility in respective cloud models (On-Prem, IaaS, PaaS, SaaS) with dark blue aligning with customer responsibility and light blue aligning with CSP responsibility. For example, CMMC requirements such as Physical Protection (PE) for limiting physical access (C028) is managed by the CSP. Establishment of respective policies and procedures are the customer’s responsibility. It’s important to note that this blog series is aligned with setting the foundation of controls for CMMC Maturity Levels 1 & 2. Once C3PAOs are identified by the CMMC Accreditation Body, customers are advised to work with their respective C3PAO for guidance on comprehensive alignment of controls, audit and certification.
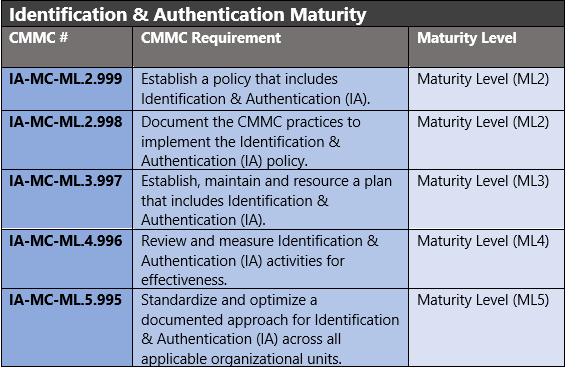
The administrative controls for the CMMC Identification & Authentication Maturity Capability (IA-MC) are listed here. These controls fall within the customer’s responsibility. This starts with establishing polices to include identification & authentication (ML2) and progresses to a documented approach across all applicable organizational units (ML5). These controls should be formally created, documented in the System Security Plan (SSP) and implemented within the organization.
Microsoft Azure Security Controls Aligned to CMMC: Identification & Authentication
Azure Security Controls Aligned to CMMC: Identification & Authentication Maturity
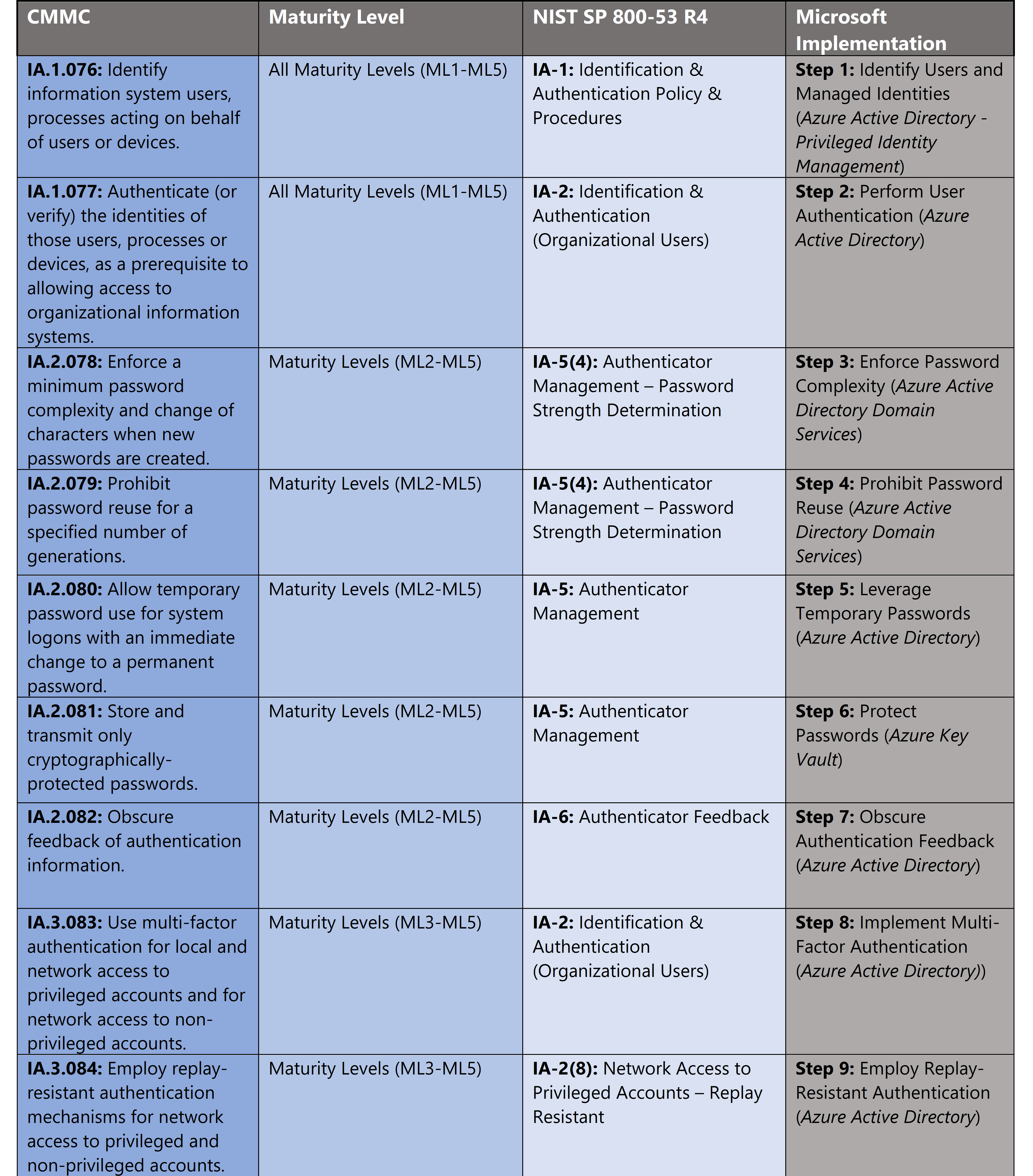
Microsoft Azure Government has developed a 9-step process to facilitate identification & authentication maturity with the security principles within CMMC, NIST SP 800-53 R4 and NIST SP 800-171 standards. Note this process is a starting point, as CMMC requires alignment of people, processes, policy and technology so refer to organizational requirements and respective standards for implementation. Azure has several offerings to facilitate identification & authentication including Azure Active Directory, Azure AD Privileged Identity Management, Azure Active Directory Domain Services, Azure Policy and Key Vault.
- Azure Active Directory is an identity and access management-as-a-service (IDaaS) solution that combines single-on capabilities to any cloud and on-premises application with advanced protection.
- Azure AD Privileged Identity Management is a service that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services like Office 365 or Microsoft Intune.
- Azure Active Directory Domain Services gives you enterprise-grade scale and reliability. It’s a highly available service hosted in globally distributed datacenters.
- Azure Policy helps you manage and prevent IT issues with policy definitions that enforce rules and effects for your resources.
- Key Vault is a service to centralize storage of secrets allowing you to control their distribution. Key Vault greatly reduces the chances that secrets may be accidentally leaked.
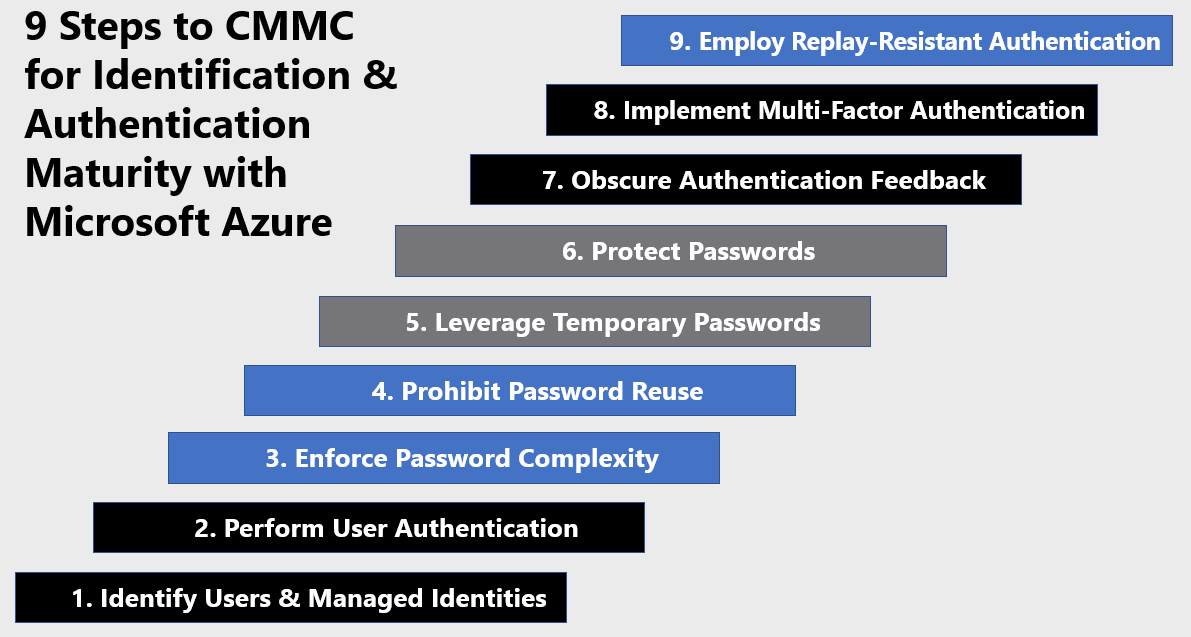
9 Steps to CMMC for Identity & Authentication Maturity with Microsoft Azure
1) Identify Users & Managed Identities
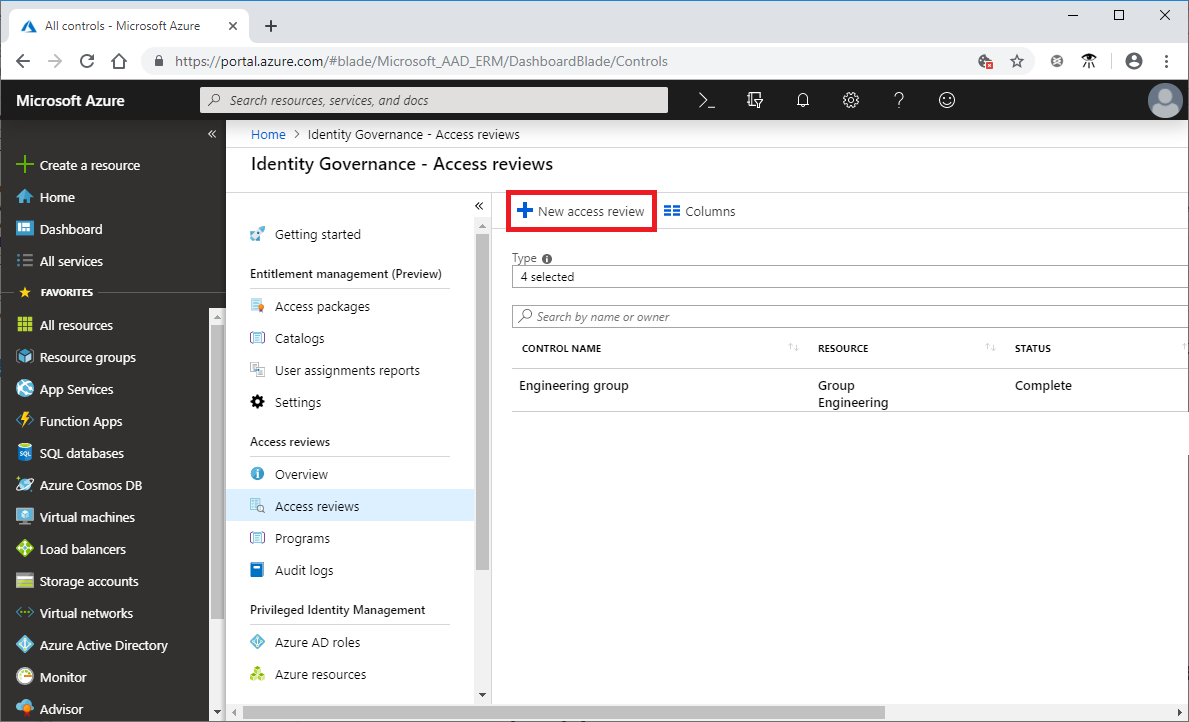
Evaluating user credentials is a challenging and continuous function requiring administrators to determine the appropriate user accounts, credentials and access methods. Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User’s access can be reviewed on a regular basis to make sure only the right people have continued access. Access reviews automate the process of controlling user and administrative rights and are accomplished via the steps below:
- Sign in to the Azure portal and open the Identity Governance page.
- In the left menu, click Access reviews.

- Click New access review to create a new access review.
- Name the access review and provide a description for the reviewers.
- Select the start date. The end date defaults to 30 days out.
- To make the access review recurring, change the Frequency setting from One time to Weekly, Monthly, Quarterly or Annually.
- In the Users section, specify the users that the access review applies to.
- In the Groups section, select one or more groups that you would like to review membership of.
- In the Reviewers section, select either one or multiple people to review all the users in scope.
- Set Upon completion settings to specify what happens (No change, Remove access, Approve access or Take recommendations) after a review completes then click Start.
This process initiates the access review. For more information, see Create an access review of groups and applications in Azure AD access reviews.
2) Perform User Authentication
Deploying Azure Active Directory (AAD) requires administrators to enable baseline security features to create a more secure and easy to use foundation in Azure AD before importing or creating user accounts. This process includes designating global administrators, using non global-admin roles where possible, enabling privileged identity management and designing identity polices. For more information, see the Azure Active Directory feature deployment guide.
Azure Active Directory provides administrators the flexibility to apply granular user authentication per their requirements. As an administrator, choosing authentication methods for Azure Multi-Factor Authentication and self-service password reset (SSPR) it is recommended that you require users to register multiple authentication methods. When an authentication method is not available for a user, they can choose to authenticate with another method. Authentication methods include password, security questions, email address, Microsoft Authenticator app, OATH Hardware token, SMS, Voice call, and App passwords. For more information, see Authentication methods.
Microsoft uses Azure Active Directory (AD) Privileged Identity Management (PIM) to manage elevated access for users who have privileged roles for Azure services. PIM manages privileged identities for on premises and Azure services to process requests for elevated access and help mitigate risks that elevated access can introduce. With Azure AD PIM, administrators can implement just-in-time access for privileged roles in Azure and view audit logs. Before Azure AD PIM, privileged roles in Azure were always elevated. The elevated access workflow provides a review, approval, just-in-time (JIT) time-bound access and detailed reporting for monitoring and the workflow is detailed in the diagram below.
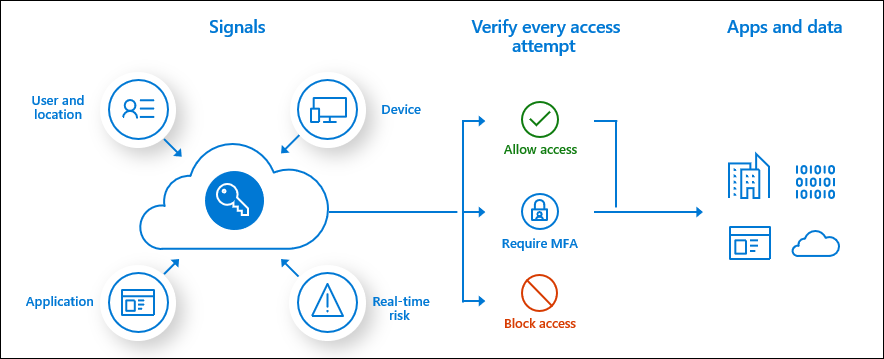
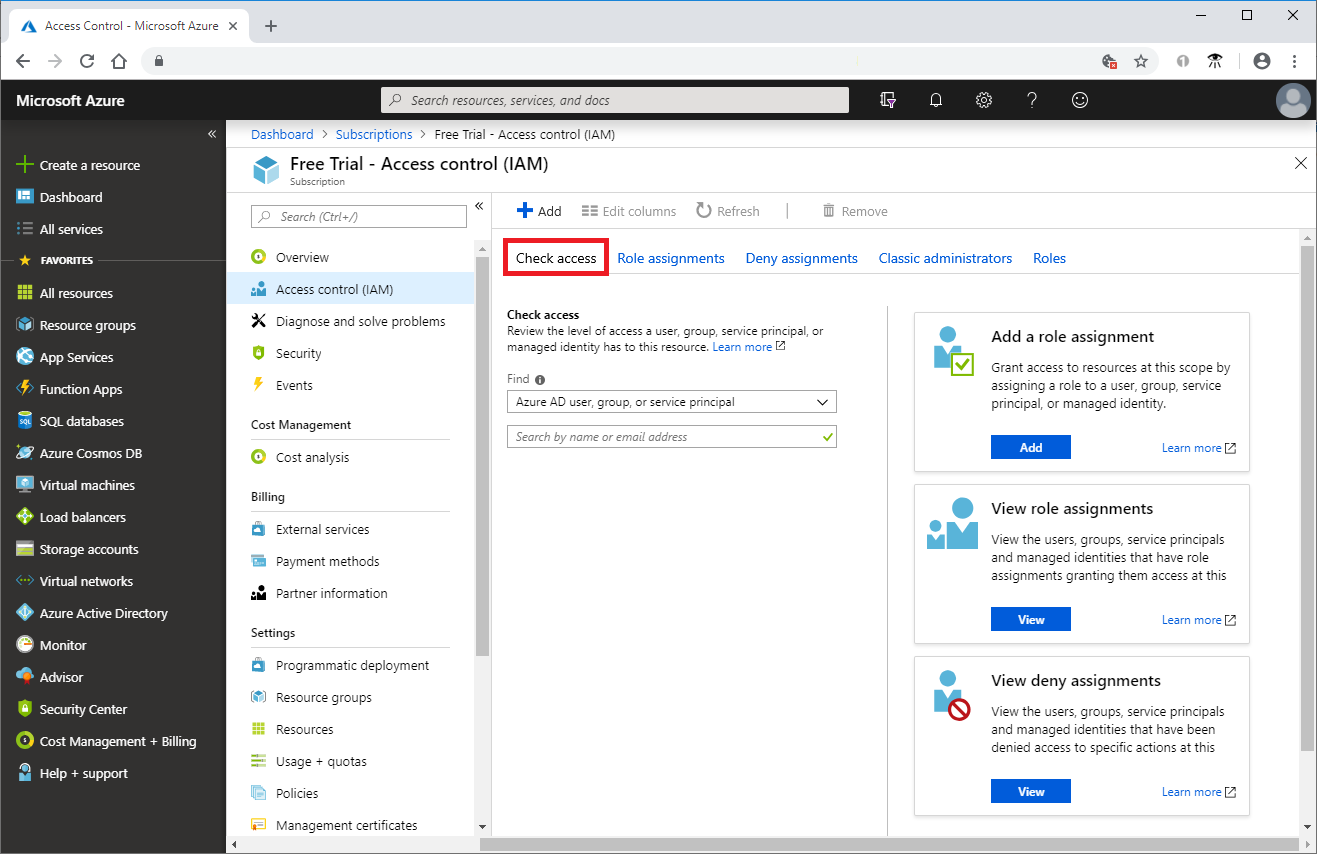
You can use the Access control (IAM) blade in role-based access control (RBAC) to view the access a user or another security principal has to Azure resources. However, sometimes you just need to quickly view the access for a single user or another security principal. The easiest way to do this is to use the Check access feature in the Azure portal. Determining user access to resources is accomplished via the steps below:
- In the Azure portal, click All services and then Subscriptions
- Click your subscription.
- Click Access control (IAM).
- Click the Check access tab.

- In the Find list, select the type of security principal you want to check access for.
- In the search box, enter a string to search the directory for display names, email addresses, or object identifiers.
- Click the security principal to open the assignments pane.
For more information, see Quickstart: View the access a user has to Azure resources.
3) Enforce Password Complexity
Enforcing password complexity is a critical requirement for protecting identification and authentication. A weak password such as “mydog123” would be relatively simple for an attacker to guess via leveraging brute force attacks with password dictionaries. The more complex the password (uppercase, lowercase, number, special characters, 8+ characters), the more compute power and time an attacker would need to crack it.
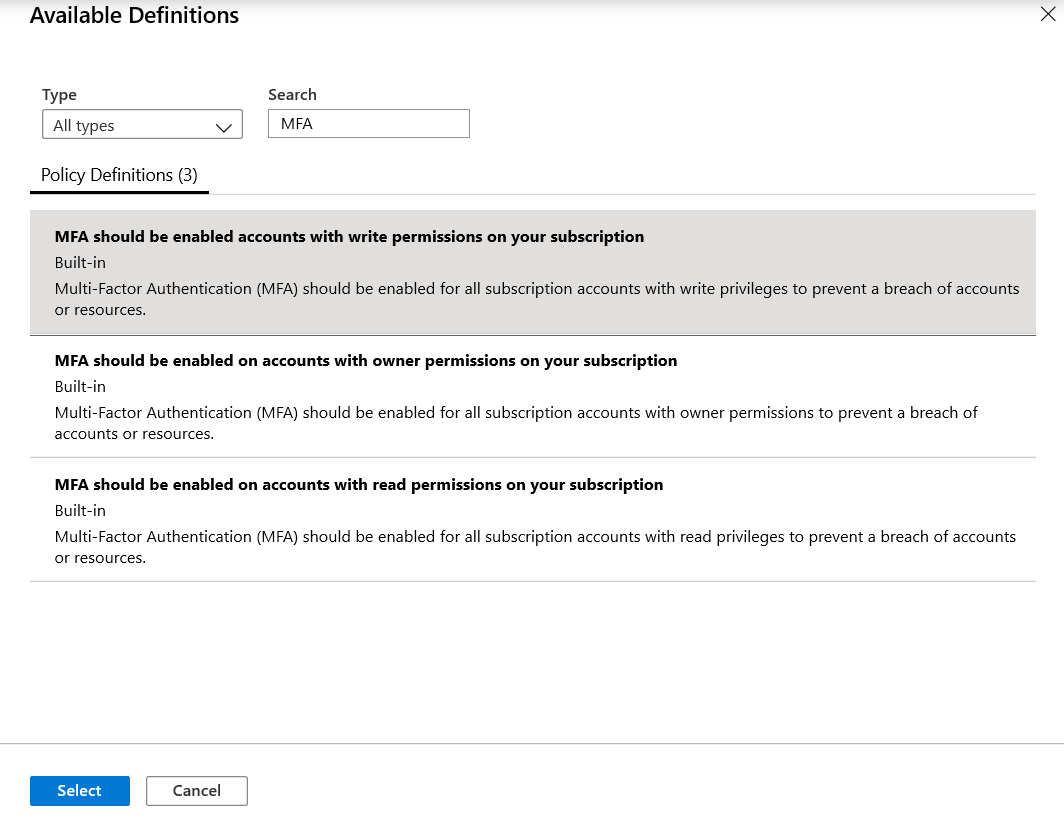
Azure Active Directory Domain Services also provides capabilities to set custom authentication policies for your requirements. For more information see Password and account lockout policies on managed domains. Azure Policy provides capabilities to audit your virtual machines to ensure password complexity is enforced via the policies below.
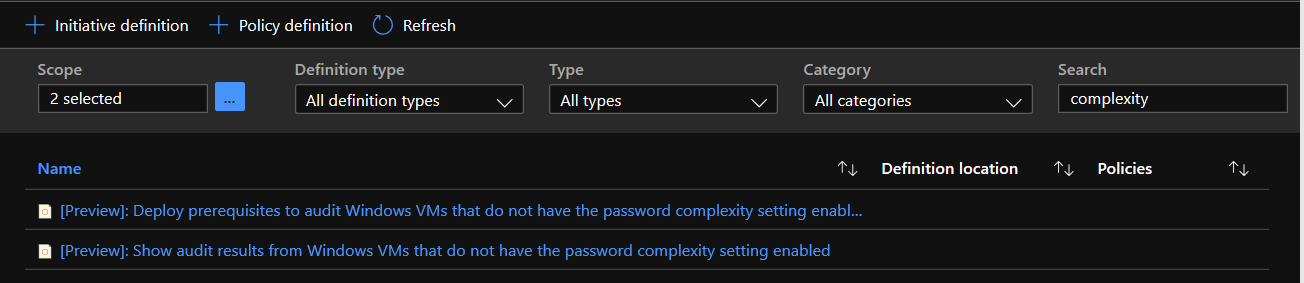
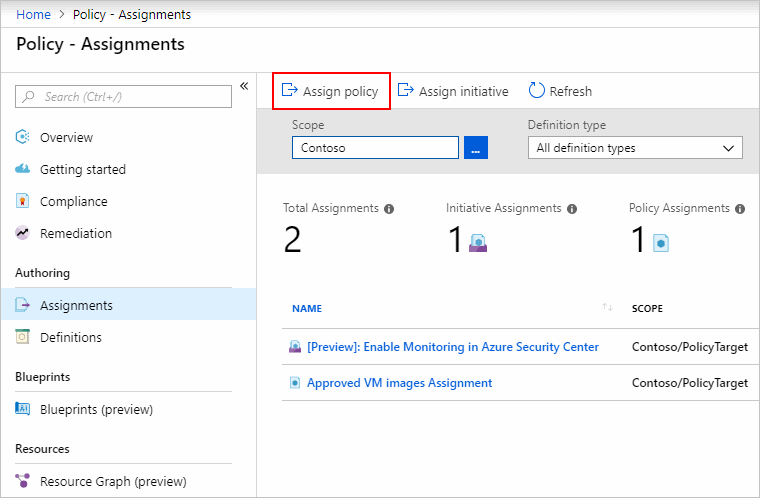
Configure an Azure Policy via the steps below. For more information see Tutorial: Create and manage policies to enforce compliance.
- In the Policy portal, select Assignments
- Select Assign Policy from the top of the Policy – Assignments page.

- On the Assign Policy page, select the Scope by clicking the ellipsis and selecting either a management group or subscription.
- Select the Policy definition ellipsis, search for the desired policy definition and click Select.

- Set an Assignment name, Description, and set Policy Enforcement to Enabled.
- Click Assign.
4) Prohibit Password Reuse
Prohibiting password reuse prevents attackers from using old passwords to access resources. This limits the window for an attacker to steal and leverage credentials. Azure Policy allows you to audit virtual machines for password re-use weaknesses via the policies below.
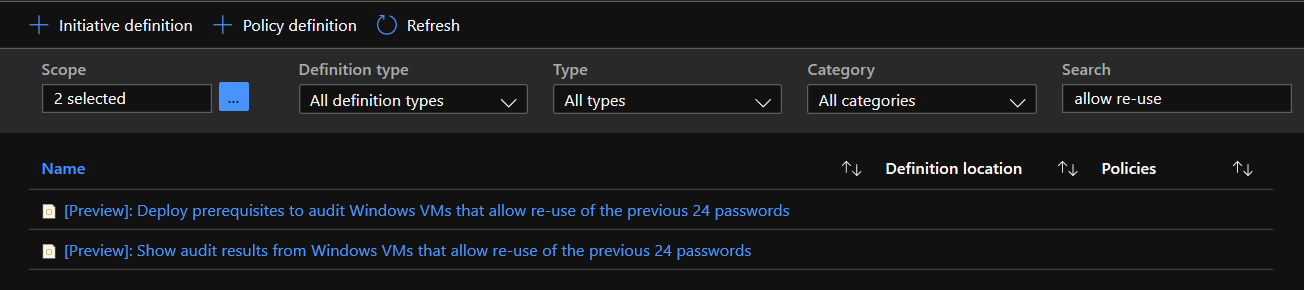
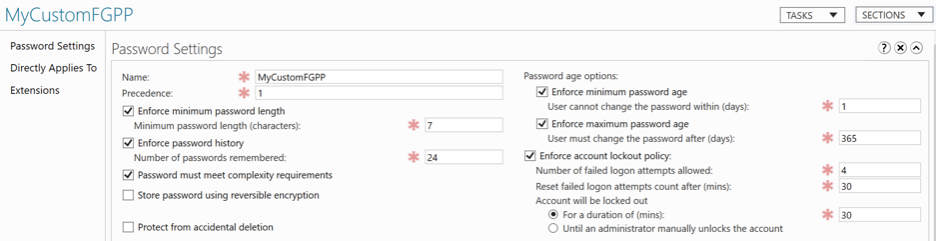
With Azure Active Directory Domain Services (Azure AD DS), you can define fine-grained password policies that control account lockout settings or minimum password length and complexity. A default fine grained password policy is created and applied to all users in an Azure AD DS managed domain. To provide granular control and meet specific business or compliance needs, additional policies can be created and applied to specific groups of users. Azure AD DS default password settings have a password’s maximum age (lifetime) set to 90 days. You can amend this timeline and set the threshold for unique passwords. The password history enforcement limits password reuse. Enforcing a password history to 99 with a minimum password age of 45 days would prevent a user from reusing the same password for 12+ years. Create a custom password policy in Azure AD DS via the steps below. For more information, see Create a custom password policy.
- To create a custom password policy in an Azure AD DS managed domain, you must be signed into a user account that’s a member of the AAD DC Administrators group.
- Access Active Directory Administrative Center from a domain joined management VM.
- From the Start screen, select Administrative Tools. A list of available management tools is shown that were installed in the tutorial to create a management VM.
- To create and manage OUs, select Active Directory Administrative Center from the list of administrative tools.
- In the left pane, choose your Azure AD DS managed domain, such as aaddscontoso.com.
- Open the System container, then the Password Settings Container.
- In the Tasks panel on the right, select New > Password Settings.
- In the Create Password Settings dialog, enter a name for the policy, such as MyCustomFGPP.

- Navigate to Directly Applies to and select Add.
- Configure target users, groups, locations and click OK to apply the policy.
5) Leverage Temporary Passwords
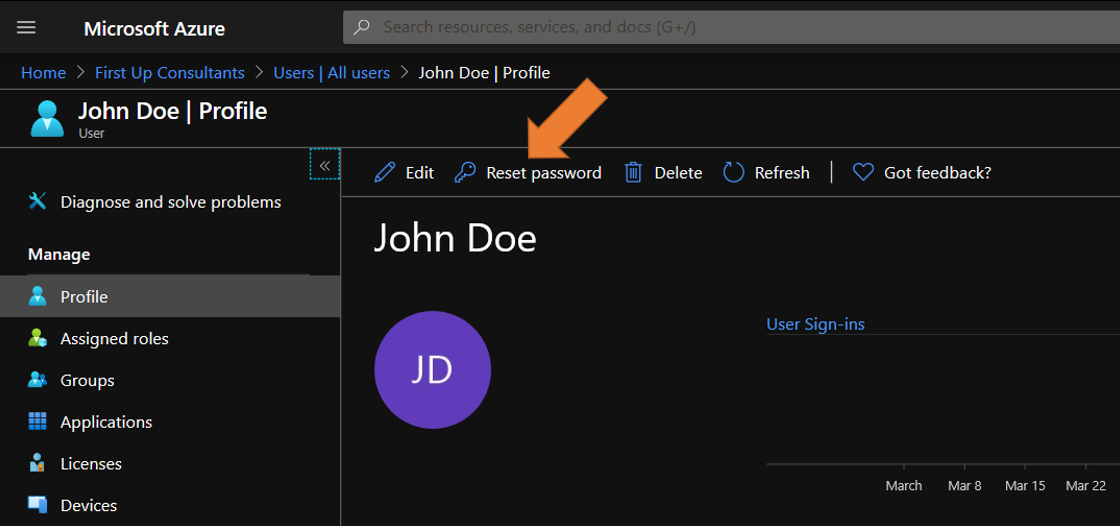
Temporary passwords are an important part of password reissue. If an administrator assigns a user’s permanent password, they will then have access to the account. If the permanent password was provided to the user insecurely an attacker might be able to intercept it. Temporary passwords mitigate this challenge. When an administrator resets a user’s password or when a user requests a self-service password reset, a temporary one-time password (OTP) is issued. This password allowed a user to sign-in only once to reset their password. You can reset a user’s password in Azure Active Directory and issue a temporary password via the steps below. For more information, see Reset a user’s password using Azure Active Directory.
- Sign into the Azure portal as a user administrator, or password administrator.
- Select Azure Active Directory, select Users, search for and select the user that needs the reset, and then select Reset Password.
- In the Reset password page, select Reset password. When using Azure Active Directory, a temporary password is auto generated for the user.

- Copy the temporary password and securely transmit to the user. The user will be required to change the password during the next sign-in process.
6) Protect Passwords
Azure Key Vault is a versatile platform for securing shared secrets. This provides password protection for secrets, passwords, keys and certificates while simplifying administration. There are flexible models for Microsoft generated keys, hardware security modules (HSMs) and bring your own key (BYOK) deployments. Azure Key Vault helps solve the following challenges:
- Secrets Management – Azure Key Vault can be used to Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets
- Key Management – Azure Key Vault can also be used as a Key Management solution. Azure Key Vault makes it easy to create and control the encryption keys used to encrypt your data.
- Certificate Management – Azure Key Vault is also a service that lets you easily provision, manage, and deploy public and private Transport Layer Security/Secure Sockets Layer (TLS/SSL) certificates for use with Azure and your internal connected resources.
- Store secrets backed by Hardware Security Modules – The secrets and keys can be protected either by software or FIPS 140-2 Level 2 validated HSMs
Create an Azure Key Vault via the steps below. For more information, see Quickstart: Set and retrieve a secret from Azure Key Vault using the Azure portal.
7) Obscure Authentication Feedback
Obscuring authentication feedback is an important control for information systems. This requirement is geared towards mitigating shoulder-surfing. If my password is displayed while I’m signing into an information system, someone might be able to look over my shoulder to steal my password. By default, Azure Active Directory obscures all passwords by default and below is an example. In this example, John Doe has typed his password, but the characters are masked for security. John would only be able to view his typed password for verification by scrolling to the far right of the bar and selecting the hidden eye icon. Selecting anything else, even a right click will automatically move the password back to masked characters. For more information, see Azure Active Directory fundamentals documentation.

8) Implement Multi-Factor Authentication
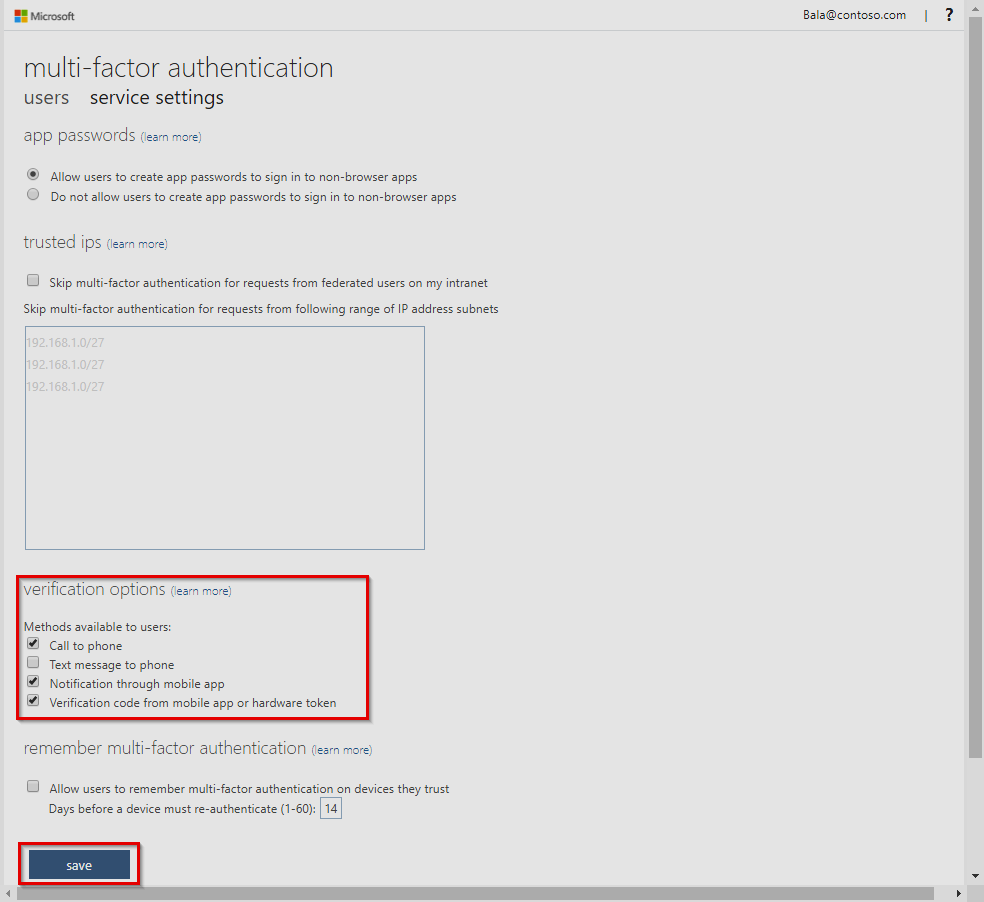
Implementing Multi-Factor Authentication is arguably one of the strongest controls to protect identity and access management in the cloud. This ensures the user making the authentication request is who they say they are, because the user must input an additional token which is generated on another device they own. The secondary factors used in MFA policies are much more difficult to spoof because they are time-sensitive and generally tied to hardware which an attacker is less likely to get their hands on. Configuring MFA requires either User administrator or Global administrator rights. The process is accomplished via the steps below:
- Browse to Azure Active Directory, Users, Multi-Factor Authentication.
- In the new tab that opens browse to service settings.
- Under verification options, check all boxes for methods available to users.

- Click on Save.
- Close the service settings tab.
The user authentication method has been changed to MFA. For more information, see Planning a cloud-based Azure Multi-Factor Authentication deployment.
9) Employ Replay-Resistant Authentication
Azure Active Directory provides configurations to enforce replay-resistant authentication. This prevents attackers from sniffing authentication attempts and replaying the password for unauthorized authentication. The TokenReplayCache is used to prevent the replay of Active Directory Authentication Library (ADAL) authentication tokens. The TokenReplayCache property allows application developers to define a token replay cache, a store that can be used for saving tokens for the purpose of verifying that no token can be used more than once.
This is a measure against a common attack, the aptly called token replay attack: an attacker intercepting the token sent at sign-in might try to send it to the app again (“replay” it) for establishing a new session. E.g., In OIDC code-grant flow, after successful user authentication, a request to “/signin-oidc” endpoint of the relying party is made with “id_token”, “code” and “state” parameters.
The relying party validates this request and establishes a new session. If an adversary captures this request and replays it, he/she can establish a successful session and spoof the user. The presence of the nonce in OpenID Connect can limit but not fully eliminate the circumstances in which the attack can be successfully enacted. To protect their applications, developers can provide an implementation of ITokenReplayCache and assign an instance to TokenReplayCache. For more information, see Security Frame: Authentication | Mitigations.
Learn more about CMMC with Microsoft
Here are some of the best resource to learn more about CMMC in the cloud with Microsoft:
- Accelerating CMMC compliance for Microsoft cloud (in depth review)
- CMMC-AB Standards with Regan Edens – National Conversation
- Defense Federal Acquisition Regulation Supplement (DFARS)
- International Traffic in Arms Regulations (ITAR)
- Federal Risk and Authorization Management Program (FedRAMP)
- US Export Administration Regulations (EAR)
- NIST SP 800-171 Compliance
- Overview of the NIST SP 800-53 R4 blueprint sample
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.

0 comments