App Dev Managers Syed Mehdi, Sanjeev Gogna, Charles Ofori, and Rob Smith come together to spotlight powerful new offerings with Microsoft’s Security Risk Detection services.
As part of our focus in Microsoft Developer Support, helping customers build and deploy applications faster with less risk by leveraging the Cloud and DevOps practices, we have found that integrating application security practices and tools into the software development process is critical for customers to successfully release a modern, cloud ready application. With that in mind, we are updating our offerings portfolio with new application security engagements along with releases to existing engagements that span Assessment, Education, Remediation, and Implementation. One of the practice areas and associated tooling where we see customers asking for assistance is around security testing automation and integrating that with their DevOps practices. We’ll touch on some more of these offerings in future posts, but to start with security testing, we are excited to share the updated release of Microsoft Security Risk Detection (MSRD)!
MSRD is a self-service, AI-powered Dynamic Application Security Testing service that optimizes your web development cycle to identify and remediate bugs and security risks as they’re introduced into the codebase – not after they are already in production.
In today’s challenging environment where we hear about a breach every day, you need to have more powerful tools that adapt with time and help you remediate bugs and reduce security risk during development and testing instead of when you are releasing to production. This cloud-based service is powered by the same technology that Microsoft has been using for years to test our own applications, websites, and services. MSRD allows you to easily scan Windows, Linux, and Web applications & services for security vulnerabilities.
Since our last blog on MSRD in May 2017, there have been new features added along with updates to existing features:
- New: Web Vulnerability Scanning
- New: Subscription-based pricing
- New: DevOps integration for Fuzzing
- Updated: Self-Service Portal
Web Vulnerability Scanning
Web vulnerability scanning is a form of Dynamic Application Security Testing (DAST) that assesses whether a web application or service is vulnerable to attack. MSRD Web Scanning covers most of the OWASP Top 10, plus dozens of other security, privacy, and reliability issues that can adversely impact the confidentiality, integrity, or availability of your web properties. MSRD was built to identify security vulnerabilities and other issues in traditional websites, as well as newer architectures like single-page applications, back-end REST APIs, and microservices, etc. MSRD Web Scanning is platform agnostic. It provides coverage for everything from Ruby on Rails and PHP on Linux to ASP.NET on Windows to Angular and React in the browser.
When coupled with other security best practices like threat modeling and static analysis, web vulnerability scanning can increase confidence that your applications and data are resilient to attack. Following these security best practices implies that a hypothetical attacker would need to invest more time and resources to identify weaknesses or vulnerabilities in your code – there won’t be any easy, low-hanging fruit – thus decreasing their return on investment and encouraging them to look elsewhere.
Web scanning is easy to set up. All that is required is access to the target site from our cloud-based scanning engines and the credentials necessary to access it. We support both public and private URLs (via VPN connectivity).
Web scanning configuration in the Self-Service Portal:
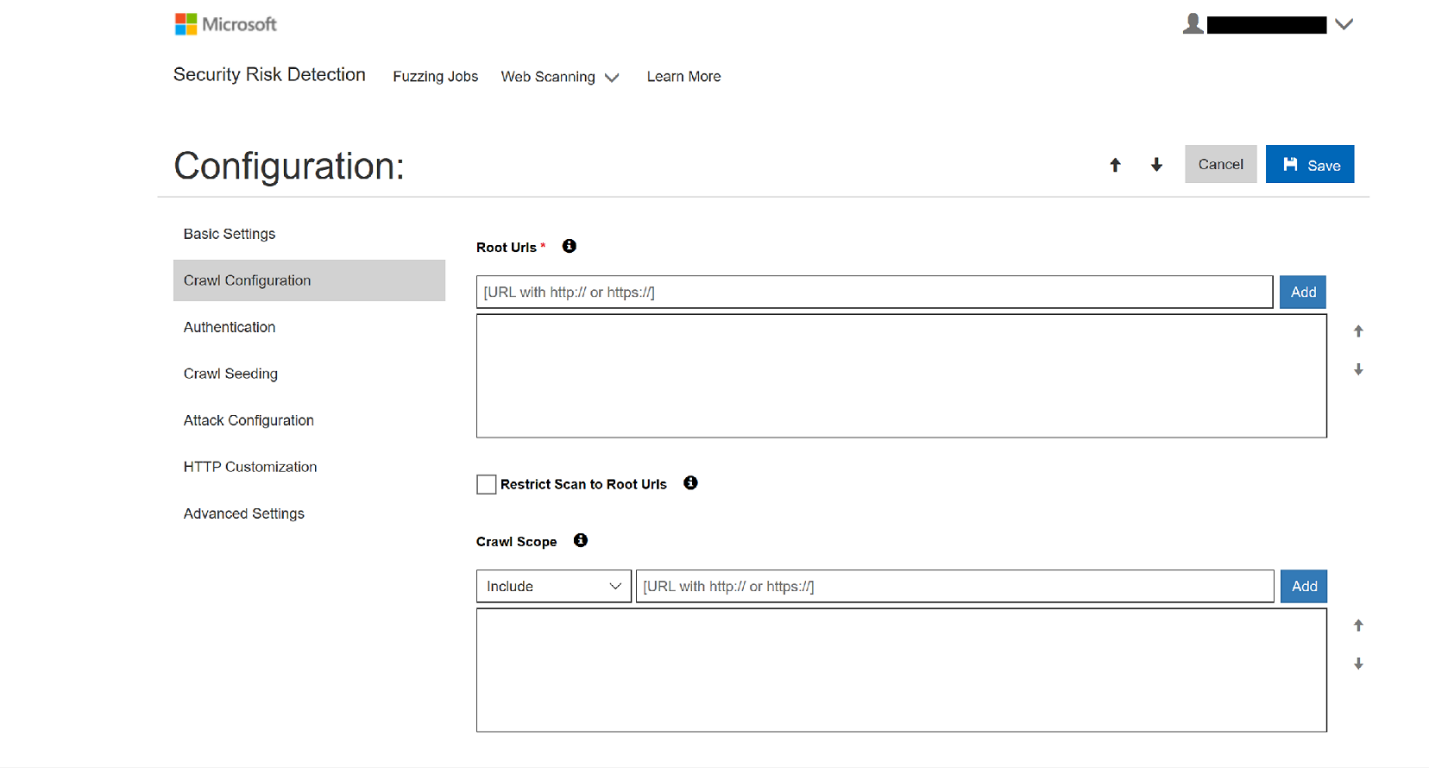
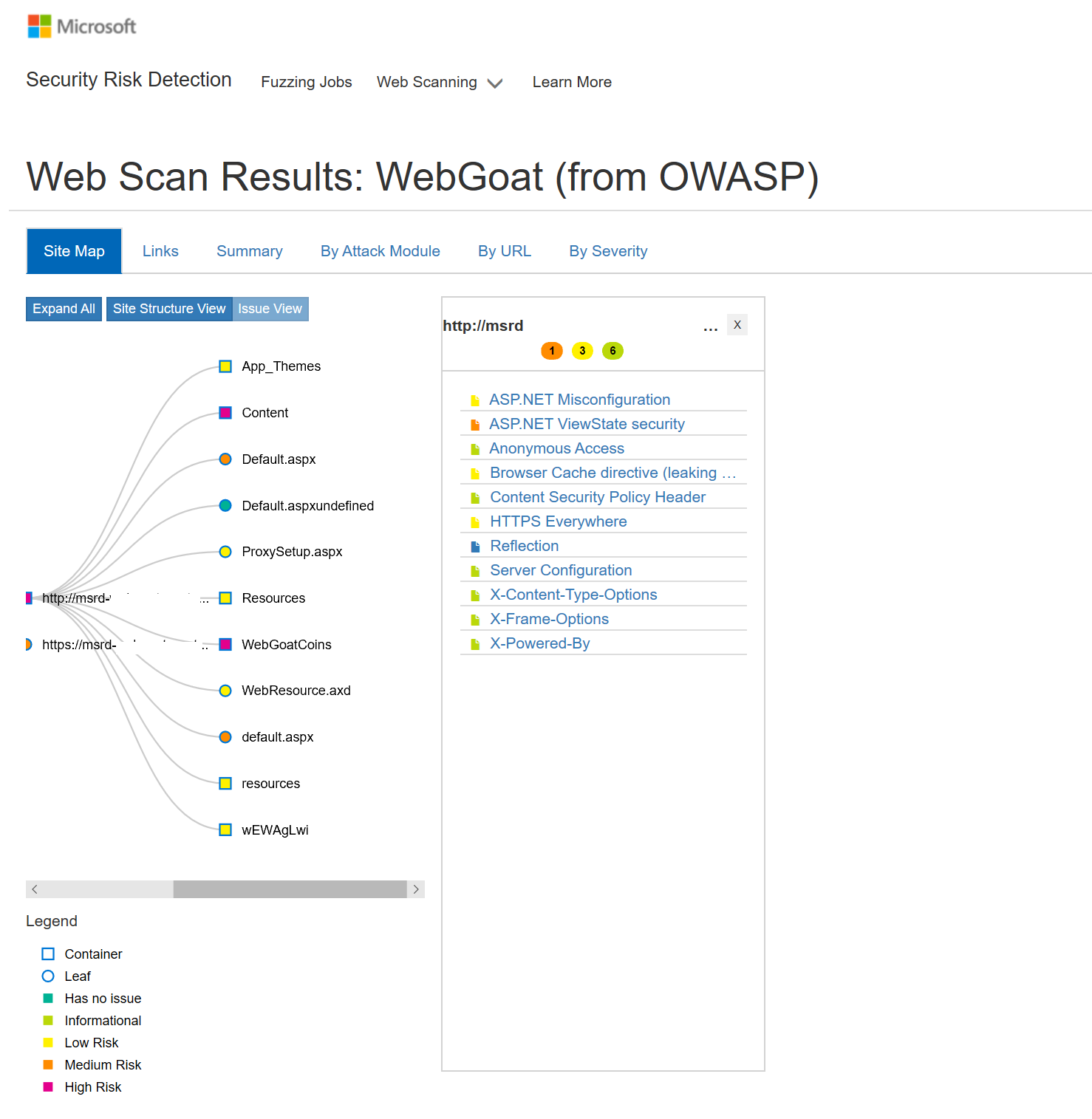
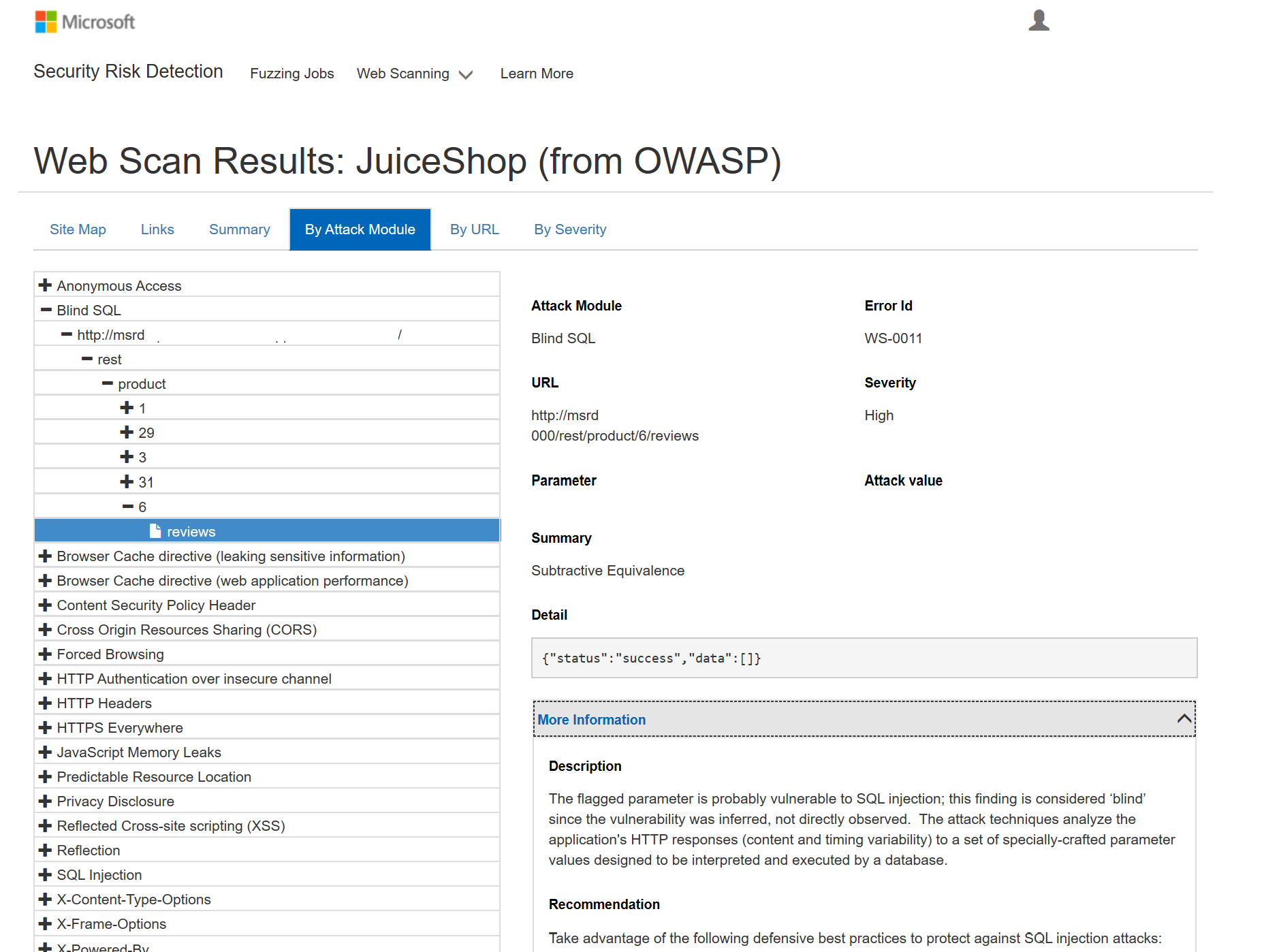
Example of Web Vulnerability Scan results in the Site Structure View, available in the Self-service Portal:
New Pricing Model
- If you are a Premier or Unified Support customer, you can now purchase MSRD as a subscription, rather than pay by the job. This can be an additional purchase or use existing pre-paid proactive support (contact your ADM for additional details).
- The new subscriptions are based on concurrency – 1, 2 or 3 concurrent scans. This means you just pay for how many scans you would be running at the same time. And you can mix and match to get the desired concurrency including accounting for potential seasonal variability.
- Unlimited Seats – You do not pay by the user nor the domain name so any developer or security engineer in the company can run the scans from the self-service portal or your CI/CD pipelines (see more details below).
- This subscription allows you to run both Fuzzing and Web Scanning. So, if you determine a web app needs to be scanned for web vulnerabilities while a service needs its parsing logic fuzzed, you can scan both apps.
Free Trial Available!
- Your ADM can coordinate a free trial where you can try out web vulnerability scanning and fuzz testing for 2 weeks. We help you run the scan(s) and see the results.
Self Service Portal
With this release, Web Vulnerability Scanning has been added to the Self-service Portal. Customers can now, on their own, configure and run scans and view the results for both types of security testing. Microsoft will assist the customer with on-boarding to the service. And, through Developer Support, Microsoft can assist customers with review and remediation based on the results.
Here is a screenshot showing creating a new Fuzzing job in the Self-service portal.
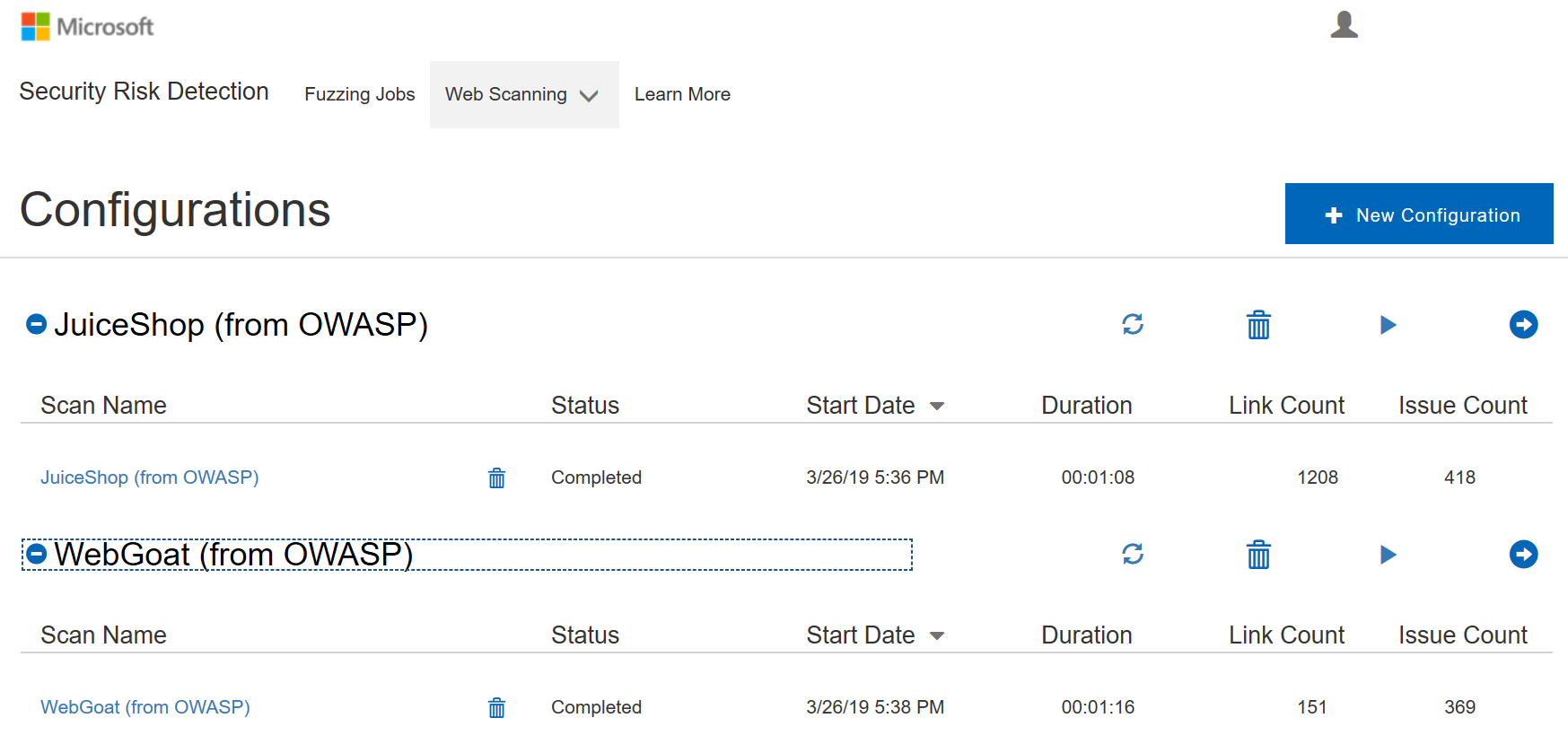
Here is screenshot showing two web app configurations for web scanning in the Self-service portal.
Web scanning interface provides a simple view of the site map of the target of the web scan, with results aggregated in multiple ways for easy consumption, including by Attack Module, By URL or By Severity.
DevOps Integration for Fuzzing
DevOps Extension
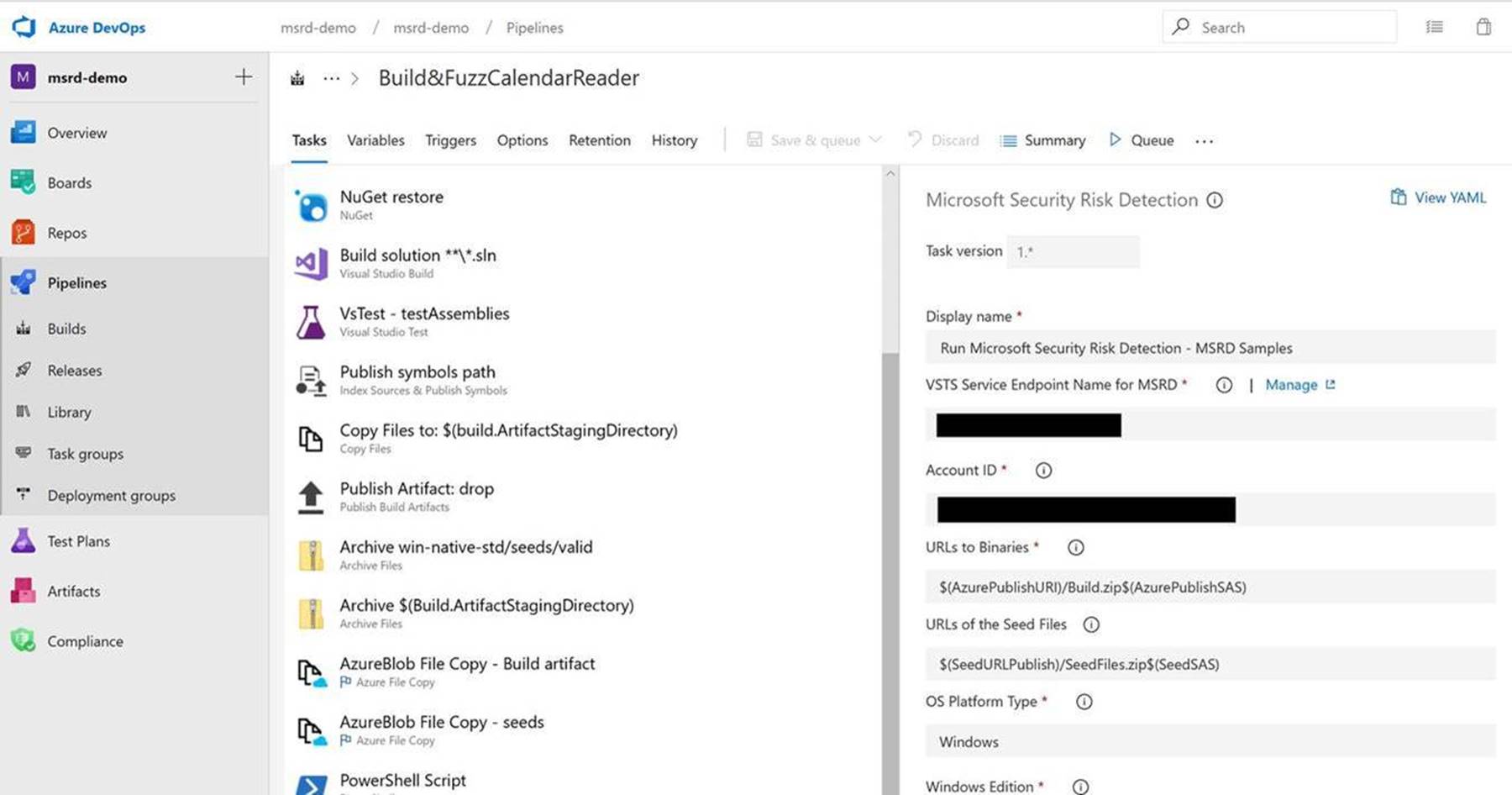
Microsoft Security Code Analysis Extension is a collection of tasks for Azure DevOps Services, that allow developers to configure and run secure development tools in Build pipelines. A task for Security Risk Detection Fuzzing is now integrated into the extension enabling developers, who are adopting DevSecOps and Security Development Lifecycle Practices for DAST, to automate fuzz testing. While this extension is currently in preview, you will have access to it as part of your MSRD subscription to enable you to fuzz your application from you Azure DevOps Build pipeline.
MSRD task shown configured in Azure DevOps Build Pipeline:
Webhooks
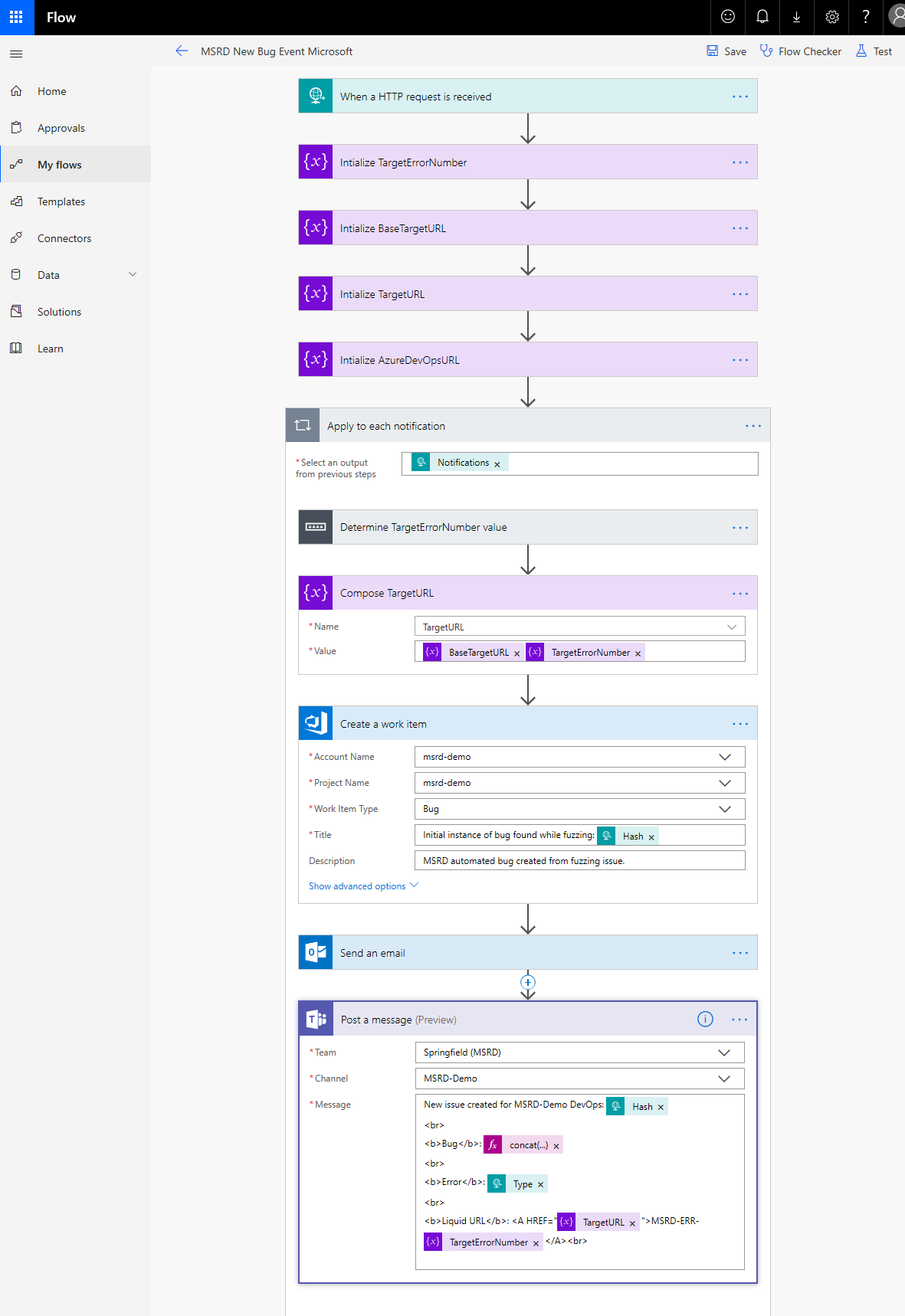
Webhooks allow you to have MSRD (Fuzzing currently) scanning events sent to a URL of your choice. This enables integration scenarios for various DevOps and bug tracking solutions including home grown ones. For example, you can push a bug to Azure DevOps or send an email to notify or developers or even message them on Teams. You can leverage Microsoft cloud services such as Azure Logic Apps and Microsoft Flow to help with this integration workflow. With Flow, you can even build that receiving service without developing any code using its connectors for Slack and Jira. This provides reliable interaction with dozens of development and support platforms, including Azure DevOps, GitHub, Slack, Jenkins, and Jira.
Sample New MSRD bug Flow workflow showing creating a work item in Azure DevOps, sending an email and posting a message in Teams:
DevOps Integration for Web Scanning
Currently, the DevOps integrations are not available for the Web Vulnerability Scanning. A future release will provide the integration and automation options for DevOps platforms such as Azure DevOps and Jenkins.
Final Thoughts
All our customers, from small businesses to large enterprises, are committed to securing the products and services they acquire, build, or deploy– whether they’re just starting to adopt security practices, or have a mature security processes in place. Any customer, no matter the size or maturity, will ship statistically safer software by following Microsoft’s Security Development Lifecycle, and MSRD was designed to meet its dynamic analysis practice.
To learn more about MSRD in action, please visit our Success Stories. And, check out this story of how a security company used MSRD Fuzzing to find a 0 Day vulnerability and responsibly report it.

0 comments