Microsoft Security Risk Detection
In this post, Application Development Managers, Mike Batongbacal and Syed Medhi, introduce the Microsoft Security Risk Detection service formerly known as Project Springfield.
Software Security is a Business Imperative
In today’s world, the threat of security breaches in computer networks and business software is an all too real possibility. More than ever before, businesses are seeing application security as a business imperative. They have implemented strategies and processes to prevent and uncover potential security vulnerabilities and enable their applications to be more resilient to cyber-attacks.
To help in this effort, Microsoft is providing one of the one of the most sophisticated tools it has for rooting out these potential security vulnerabilities in software. At Microsoft Build 2017, Sr. Researcher, David Molnar, debuted the Microsoft Security Risk Detection service, formerly known as Project Springfield. The service is built on Azure and makes use of a software testing technique called Fuzz Testing or Fuzzing.
Fuzz Testing
Fuzz testing is used to root out code that is susceptible to security attacks in software. The technique employs inputting massive amounts of random and unexpected data, called fuzz, to the system. The service then looks for instances in which these unforeseen actions cause the software to crash, signaling a security vulnerability.
The Security Risk Detection service also adds an artificial intelligence layer in order to make more sophisticated decisions about what might trigger a crash and signal a security concern. Every time the service runs, it collects data in order to focus on areas of code that are most critical, making it more likely to find vulnerabilities that other fuzzing tools might miss.
How Does Security Risk Detection Work?
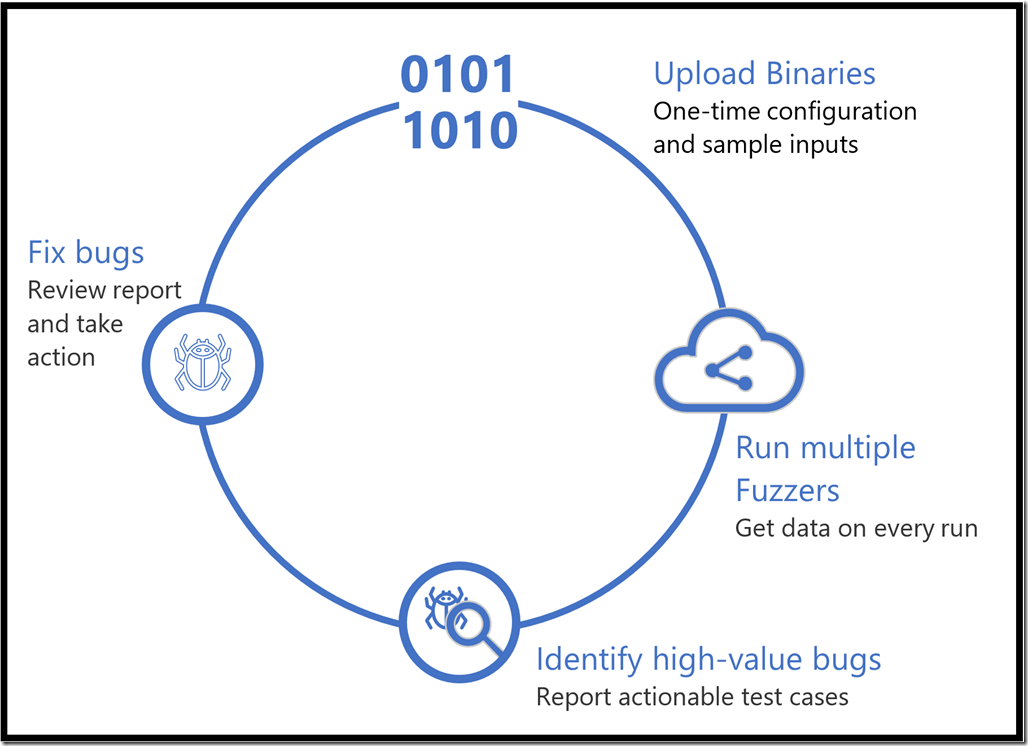
Security Risk Detection can be employed as a step in your Secure Development Lifecycle to verify the resilience of your software application. The service currently supports Windows applications and is in the process of adding Linux applications as well. The service follows an iterative approach with the following steps:
- Upload Binaries – The customer logs into a secure web portal. Security Risk Detection provides a Virtual Machine (VM) for the customer to install the binaries of the software to be tested, along with a “test driver” program that runs the scenario to be tested, and a set of sample input files called “seed files” to use as a starting point for fuzzing.
- Run Multiple Fuzzers – Security Risk Detection will continuously fuzz test using multiple methods, including Microsoft whitebox fuzzing technology.
- Identify High Value Bugs – Security Risk Detection reports security vulnerabilities in real time on the secure web portal. Customers can download actionable test cases to reproduce the issue.
- Fix Bugs – The customer can then prioritize and fix bugs. You can iterate and re-test as needed to ensure the effectiveness of the fix.
Next Steps
To learn more and sign up to use the Microsoft Security Risk Detection service, click on the following link: https://www.microsoft.com/en-us/security-risk-detection/
David Molnar’s presentation at Microsoft Build 2017 can be viewed by following this link: https://channel9.msdn.com/Events/Build/2017/B8077
Premier Support for Developers provides strategic technology guidance, critical support coverage, and a range of essential services to help teams optimize development lifecycles and improve software quality. Contact your Application Development Manager (ADM) or email us to learn more about what we can do for you.

 Light
Light Dark
Dark
0 comments