

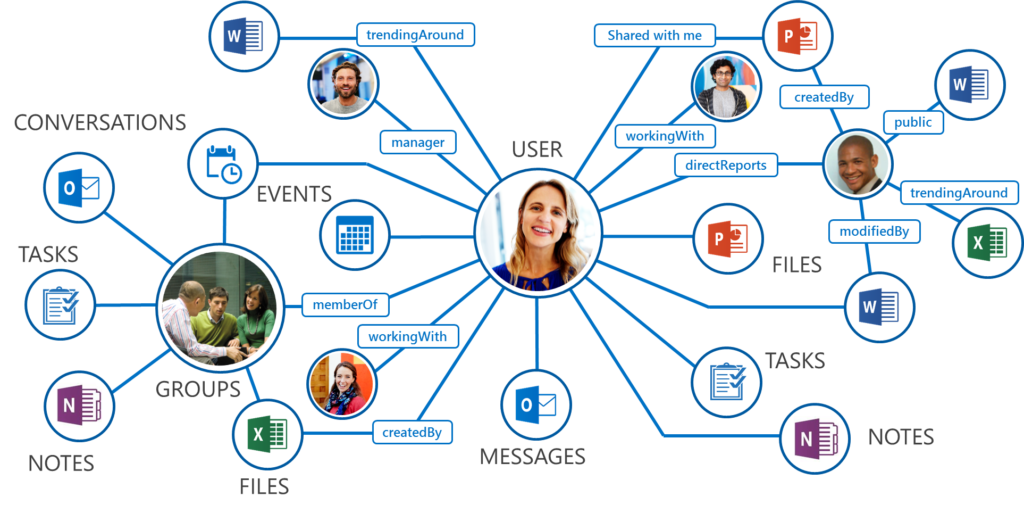
Microsoft Graph or the Azure AD Graph

New Azure AD Identity Protection APIs now in preview in Microsoft Graph

30DaysMSGraph – Day 20 – Use case: Device Code flow to authenticate users

30DaysMSGraph – Day 12 – Authentication and authorization scenarios


 Light
Light Dark
Dark