This is the eighth in a ten-part blog series where we’ll demonstrate principles of the Cybersecurity Maturity Model Certification aligned with Microsoft Azure. Subsequent blogs in the series will delve into system & communications protection and system & information integrity. In this eighth blog of the series we will explore how to leverage Microsoft Azure for security assessment & situational awareness.
Please note that the information cutoff date for this post is October 2020, and that as of the date of this writing, CMMC developments and guidance are in progress. Additionally, as of the date of this writing, the CMMC Accreditation Body has not certified any the third-party assessors and guidance on the formal assessment process is still under development. As a result, the information herein, including our CMMC related offerings, may be enhanced in the future to align with future guidance from the DoD and CMMC Accreditation Body. Microsoft is closely tracking developments related to the CMMC.
Stay tuned for the upcoming CMMC blogs in the series:
- Access Control Maturity – live
- Audit & Accountability Maturity – live
- Asset & Configuration Management Maturity – live
- Identification & Authentication Maturity – live
- Incident Response Maturity – live
- Maintenance & Media Protection Maturity – live
- Recovery & Risk Management Maturity – live
- Security Assessment & Situational Awareness Maturity – this blog
- System & Communications Protection Maturity – live
- System & Information Integrity Maturity (5/28)
What is Cybersecurity Maturity Model Certification (CMMC)?
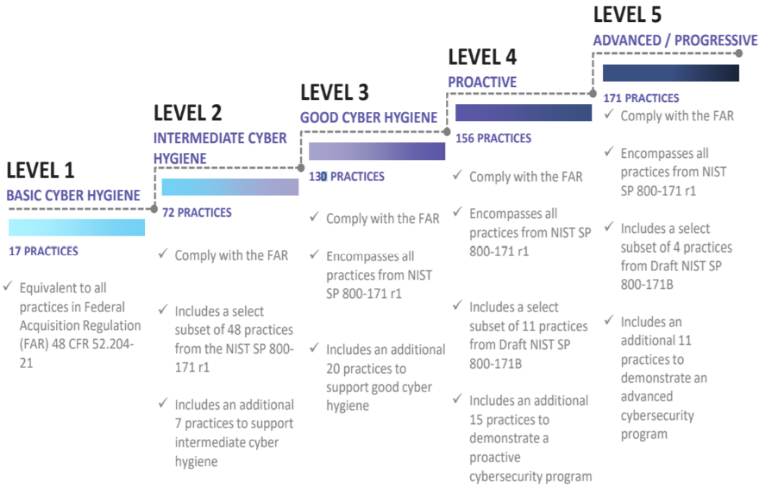
The Defense Industrial Base (DIB) is charged with implementing Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012. DFARS requires organizations supporting the Department of Defense (DoD) to implement NIST SP 800-171 and FedRAMP Moderate Impact level controls. DoD has mandated CMMC with periodic assessments in order to strengthen cybersecurity across the DIB. CMMC builds upon DFARS 7012 by verifying an organization’s readiness to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) such as International Traffic in Arms Regulation (ITAR) and Export Administration Regulations (EAR) export-controlled data.
CMMC extends beyond the parent organization into sub-contractors, partners, and suppliers. The framework is intended to enforce critical thinking approaches for comprehensive security. The CMMC framework specifies 5 levels of maturity measurement from Maturity Level 1 (Basic Cyber Hygiene) to Maturity Level 5 (Proactive & Advanced Cyber Practice). The Certification levels will be determined through audits from independent, third-party assessment organizations (C3PAO).
What preparation is required for CMMC alignment to security assessment & situational awareness?

It’s important to understand that compliance is a shared responsibility between the customer and the Cloud Services Provider (CSP). The graphic on the left demonstrates the CSP responsibility in respective cloud models (On-Prem, IaaS, PaaS, SaaS) with dark blue aligning with customer responsibility and light blue aligning with CSP responsibility. For example, CMMC requirements such as Physical Protection (PE) for limiting physical access (C028) is managed by the CSP. Establishment of respective policies and procedures are the customer’s responsibility. It’s important to note that this blog series is aligned with setting the foundation of controls for CMMC Maturity Levels 1 & 2. Once C3PAOs are identified by the CMMC Accreditation Body, customers are advised to work with their respective C3PAO for guidance on comprehensive alignment of controls, audit and certification.
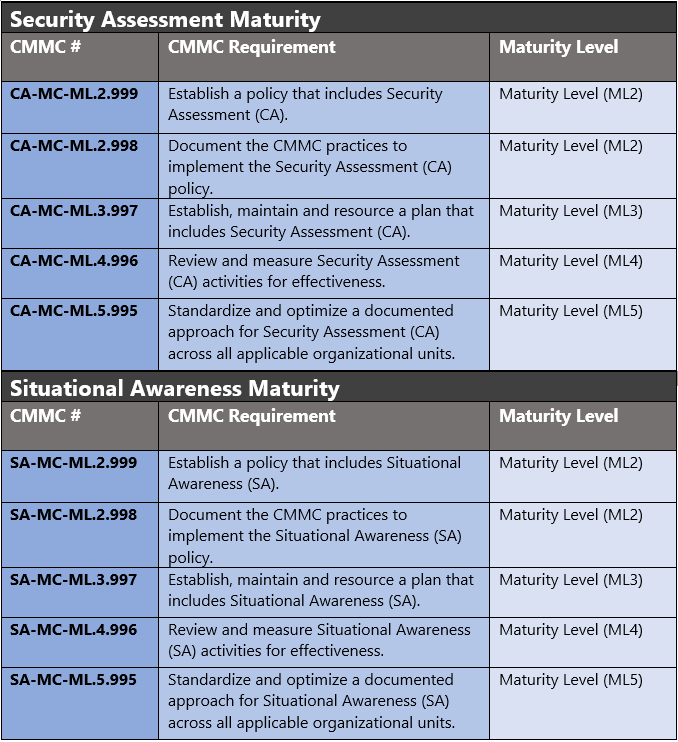
The administrative controls for the CMMC Security Assessment (CA-MC) and Situational Awareness Maturity (SA-MC) are listed here. These controls fall within the customer’s responsibility. This starts with establishing polices to include security assessment & situational awareness (ML2) and progresses to a documented approach across all applicable organizational units (ML5). These controls should be formally created, documented in the System Security Plan (SSP) and implemented within the organization.
Microsoft Azure Security Controls Aligned to CMMC: Security Assessment & Security Awareness
Azure Security Controls Aligned to CMMC: Security Assessment & Situational Awareness
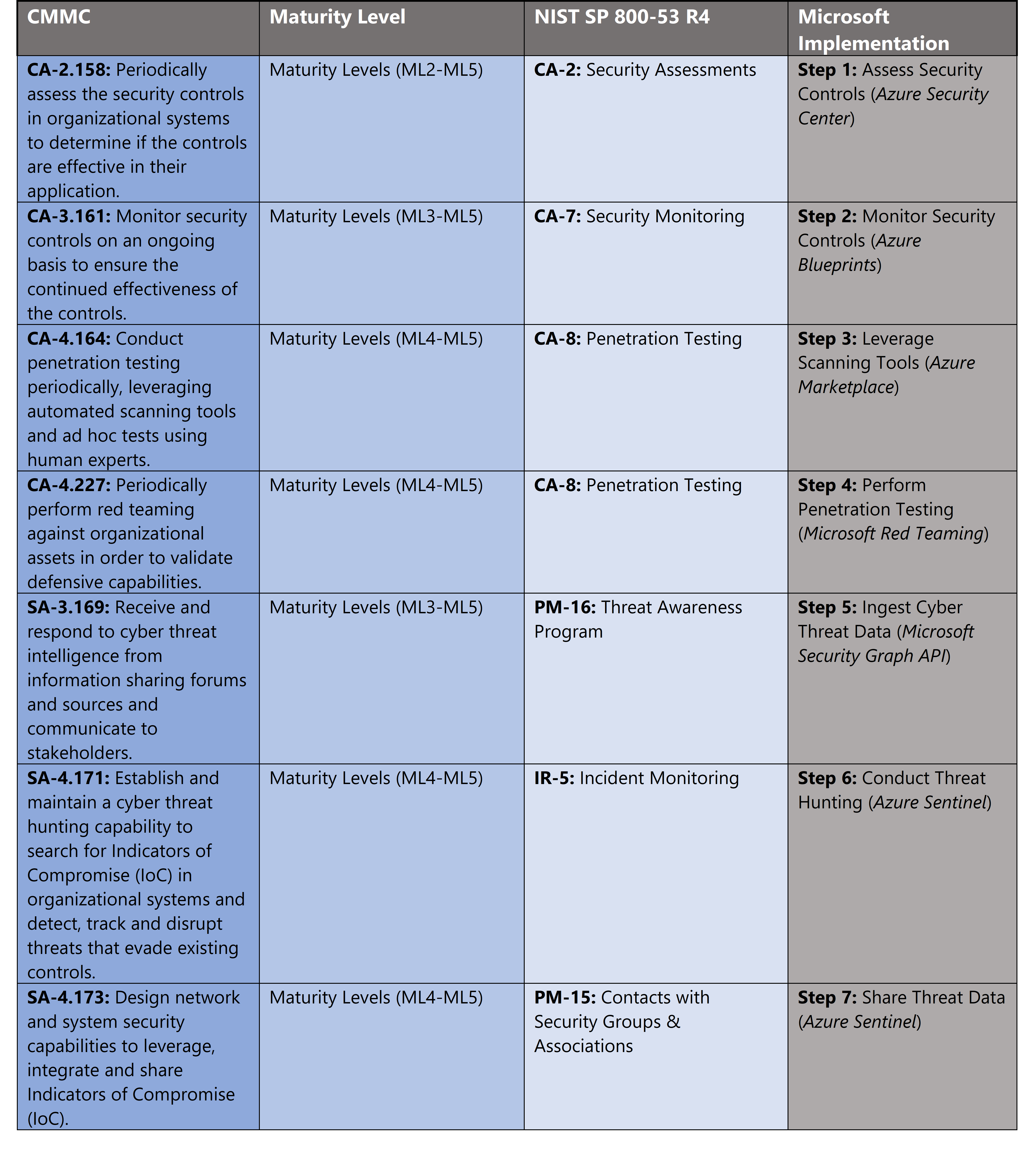
Microsoft Azure Government has developed a 7-step process to facilitate security assessment & situational awareness with the security principles within CMMC, NIST SP 800-53 R4 and NIST SP 800-171 standards. Note this process is a starting point, as CMMC requires alignment of people, processes, policy and technology so refer to organizational requirements and respective standards for implementation. Azure has several offerings to facilitate security assessment & situational awareness including Azure Security Center, Azure Sentinel, Azure Blueprints and the Microsoft Graph Security API.
- Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud – whether they’re in Azure or not – as well as on premises.
- Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
- Azure Blueprints enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization’s standards, patterns, and requirements.
- Microsoft Graph Security API simplifies integration with Microsoft and third-party security solutions. Using one endpoint, one software development kit (SDK), one schema, and one authentication mechanism, customers and partners can easily build integrated security applications, workflows and analytics.
7 Steps to CMMC for Security Assessment & Situational Awareness with Microsoft Azure
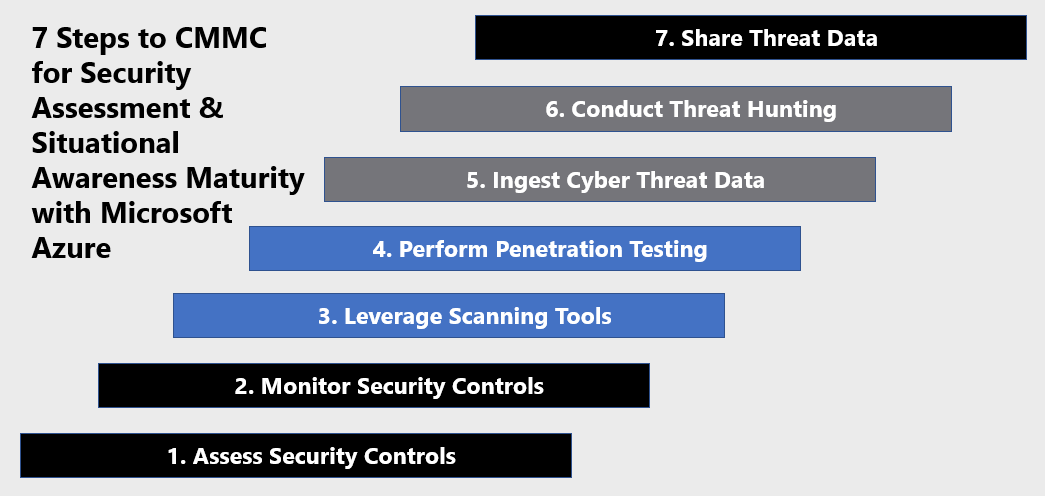
1) Assess Security Controls
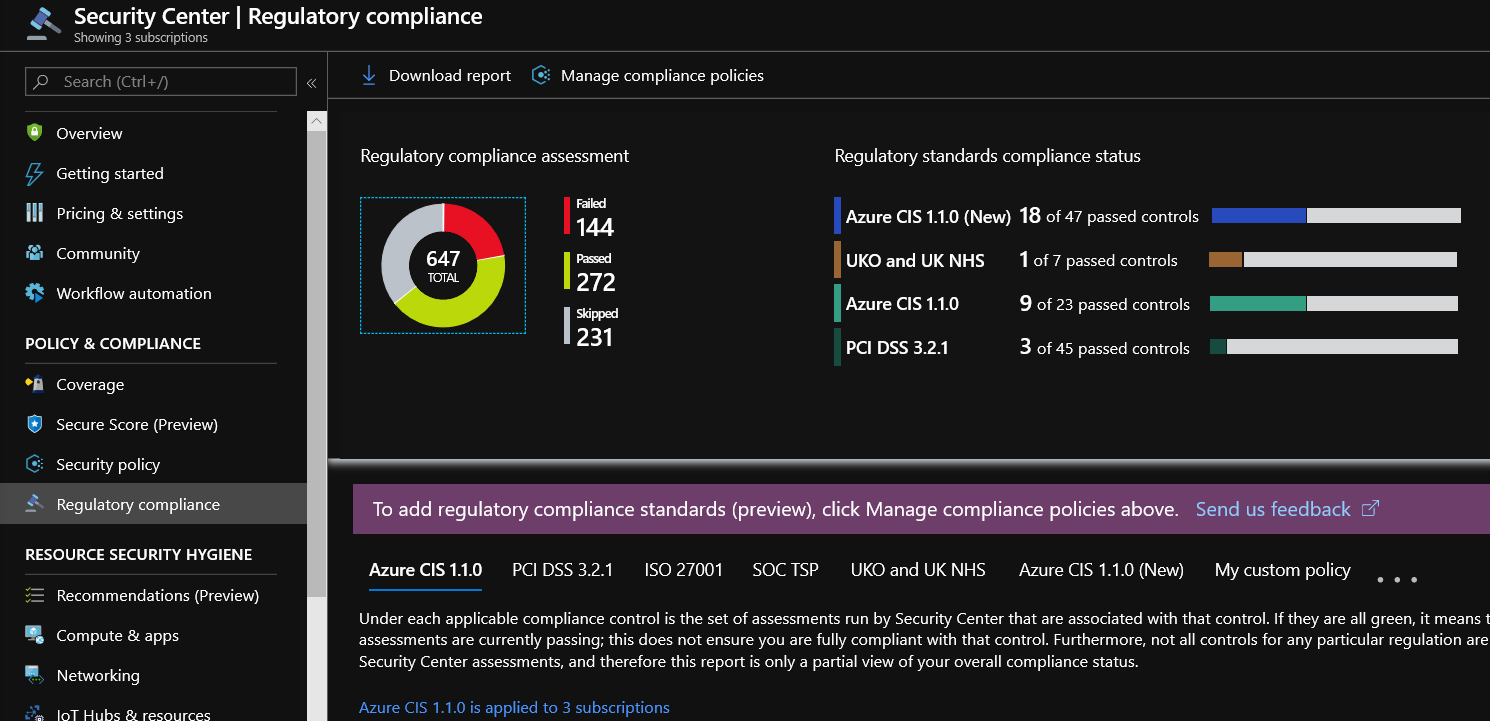
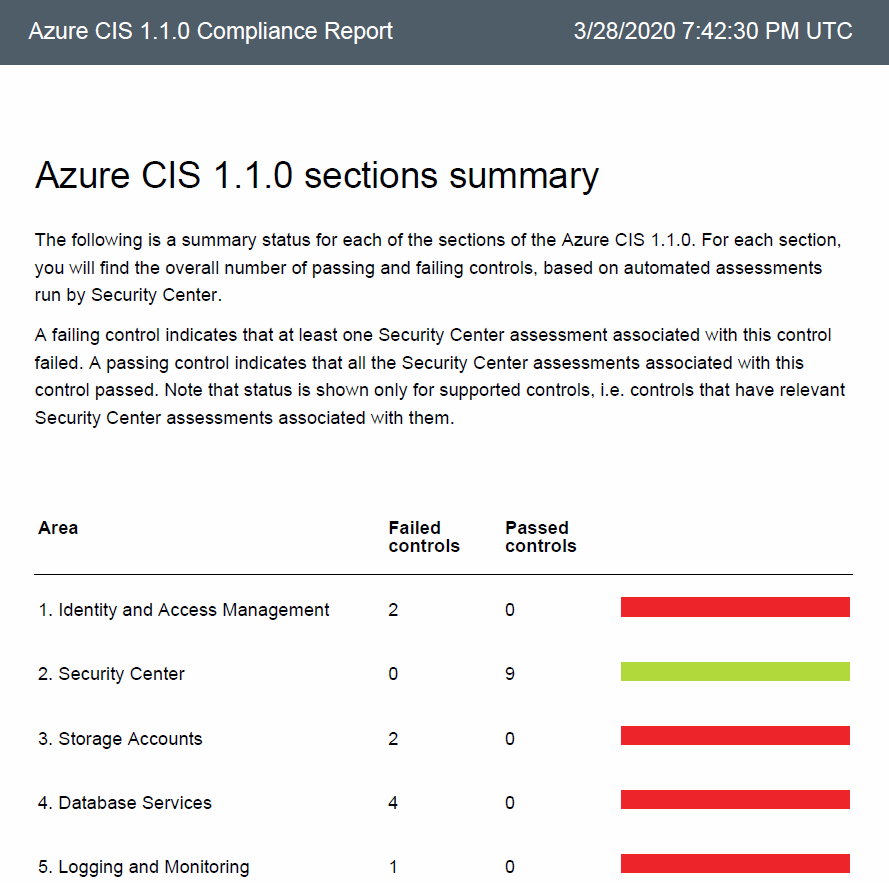
Azure Security Center helps streamline the process for meeting regulatory compliance requirements, using the regulatory compliance dashboard. In the dashboard, Security Center provides insights into your compliance posture based on continuous assessments of your Azure environment. Security Center analyzes risk factors in your hybrid cloud environment according to security best practices. These assessments are mapped to compliance controls from a supported set of standards. In the Regulatory compliance dashboard, you can see the status of all the assessments within your environment in the context of a particular standard or regulation. As you act on the recommendations and reduce risk factors in your environment, your compliance posture improves. Leverage Azure Security Center to assess your regulatory compliance via the steps below. For more information, see Tutorial: Improve your regulatory compliance.
- Navigate to Security Center.
- Select Regulatory compliance.
- Assess Security Control alignment to respective compliance standards. Note you can customize this dashboard by selecting Manage Compliance Policies.

- Select Download Report and specify the desired framework to generate a detailed PDF report.

2) Monitor Security Controls
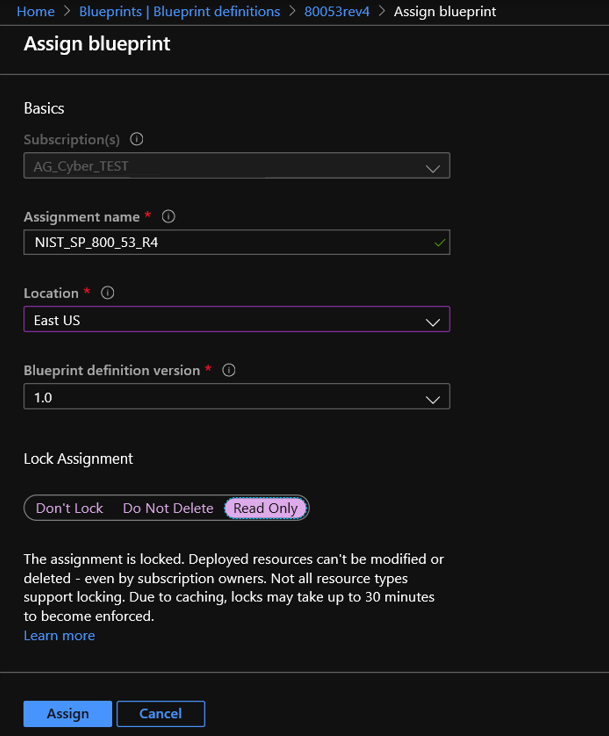
Azure Blueprints provides an avenue to apply security controls, policies and resources. Just as a blueprint allows an engineer or an architect to sketch a project’s design parameters, Azure Blueprints enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization’s standards, patterns, and requirements. Azure Blueprints makes it possible for development teams to rapidly build and stand up new environments with trust they’re building within organizational compliance with a set of built-in components — such as networking — to speed up development and delivery. Azure Blueprints can actively apply controls with the deployifnotexists option or can be leveraged for monitoring controls passively with the auditifnotexists option. Assign an Azure Blueprint via the steps below. For more information, see Tutorial: Protect new resources with Azure Blueprints resource locks.
- Select All services in the left pane. Search for and select Blueprints.
- Select the Blueprint definitions page on the left.
- Select Assign blueprint at the top of the blueprint definition page.
- Provide the parameter values for the blueprint assignment:
- Subscriptions: Select target subscription
- Assignment name: Assign a Blueprint name. This is pre-populated if you use a default Blueprint template.
- Location: Select a region in which to create the managed identity. Azure Blueprint uses this managed identity to deploy all artifacts in the assigned blueprint.
- Blueprint definition version: Select the published version 1.0 of the blueprint definition.
- Lock Assignment: Select the Read Only blueprint lock mode.
- Managed Identity: Use default option for System Assigned.
- Artifact Parameters: Assign respective parameters (resource names, types, locations).

- Select Assign.
3) Leverage Scanning Tools
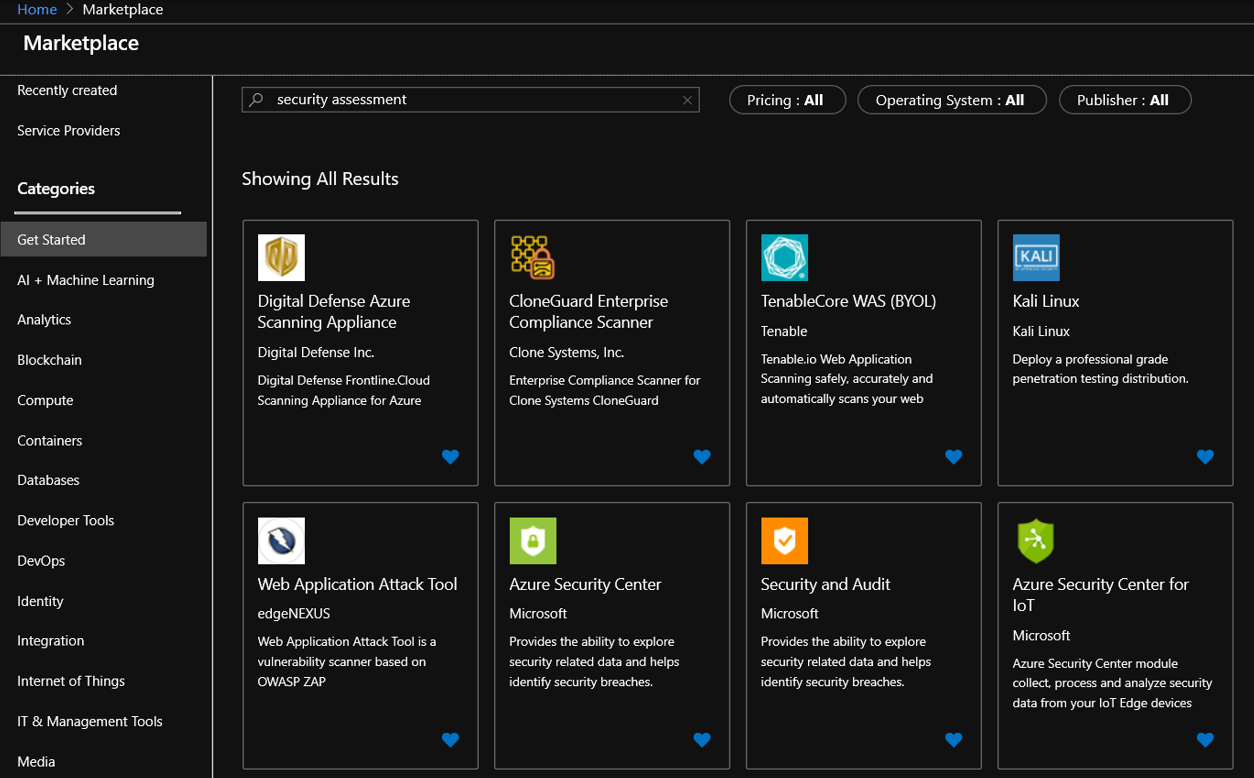
Conducting penetration testing is a valuable tool to assessing your security posture. Penetration testing is proactive security control to test for vulnerabilities before a they’re discovered by real world threats. Penetration testing falls within the customer’s organizational requirements and may be conducted by internal security teams or via partnership with a third party. The Azure Marketplace provides numerous offerings for security assessment tools. These solutions are both first and third party including flexible models for free/open source, trial, Pay As You Go (PAYG), Enterprise Agreements (EA) and Bring Your Own License (BYOL). Search the Azure Marketplace for security assessment tools via the steps below. For more information, see Azure Marketplace.
- Sign into the Azure Portal.
- Search for and select Marketplace.
- Select Security from the categories on the left.

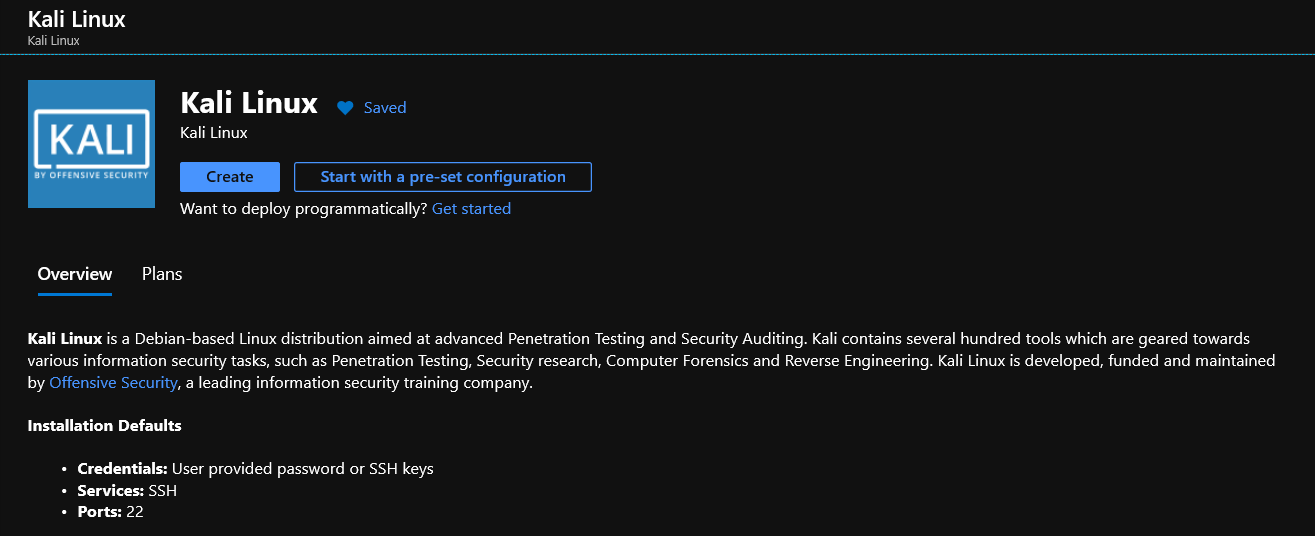
- Select a security assessment tool such as Kali Linux and select Create.

4) Perform Penetration Testing
Organizations can better prepare for the impact of current and future threats by simulating real-world attacks and exercising Tactics, Techniques and Procedures (TTPs) that determined and persistent adversaries use during breaches. Rather than simply seeking to keep security incidents from occurring, it is critical to assume that a security incident can and will occur. The information gained from Red Teaming and live site penetration testing exercises helps to significantly strengthen defenses, improve response strategies, train defenders, and drive greater effectiveness of the entire security program.
Conducting penetration testing generally falls within the customer’s responsibility of the Cloud Services Provider (CSP) responsibility model. Its important for customers to review and adhere to Microsoft’s Penetration Testing Rules of Engagement prior to testing. Care must be taken to limit all penetration tests to your assets and avoid unintended consequences to other customers around you. For more information see, Microsoft’s Penetration Testing Rules of Engagement.
Microsoft also conducts internal red-team exercises against the Microsoft managed cloud infrastructure, services and applications. Red Teaming is above and beyond compliance accreditations or other industry requirements and provides Microsoft, and our customers, with the additional assurance that Microsoft enterprise cloud services are continuously performing security monitoring, testing, and updates to reflect the constantly changing threats that both customers and Microsoft face. For more information, see Microsoft Enterprise Cloud Red Teaming.
5) Ingest Cyber Threat Data
Azure Sentinel lets you import the threat indicators your organization is using, which can enhance your security analysts’ ability to detect and prioritize known threats. Several features from Azure Sentinel then become available or are enhanced:
- Analytics includes a set of scheduled rule templates you can enable to generate alerts and incidents based on matches of log events from your threat indicators.
- Workbooks provide summarized information about the threat indicators imported into Azure Sentinel and any alerts generated from analytics rules that match your threat indicators.
- Hunting queries allow security investigators to use threat indicators within the context of common hunting scenarios.
- Notebooks can use threat indicators when you investigate anomalies and hunt for malicious behaviors.
You can stream threat indicators to Azure Sentinel by using one of the integrated threat intelligence platform (TIP) products listed in the next section, connecting to TAXII servers, or by using direct integration with the Microsoft Graph Security tiIndicators API:
- MISP Open Source Threat Intelligence Platform
- Palo Alto Networks MineMeld
- ThreatConnect Platform
Connect Azure Sentinel to your threat intelligence platform via the following steps. For more information, see Connect data from threat intelligence providers.
- Register an application in Azure Active Directory to get an application ID, application secret, and Azure Active Directory tenant ID. You need these values for when you configure your integrated TIP product or app that uses direct integration with Microsoft Graph Security tiIndicators API.
- Configure API permissions for the registered application: Add the Microsoft Graph Application permission ThreatIndicators.ReadWrite.OwnedBy to your registered application.
- Ask your Azure Active Directory tenant administrator to grant admin consent to the registered application for your organization. From the Azure portal: Azure Active Directory > App registrations > <app name> > View API Permissions > Grant admin consent for <tenant name>.
- Configure your TIP product or app that uses direct integration with Microsoft Graph Security tiIndicators API to send indicators to Azure Sentinel by specifying the following:
- The values for the registered application’s ID, secret, and tenant ID.
- For the target product, specify Azure Sentinel.
- For the action, specify alert.
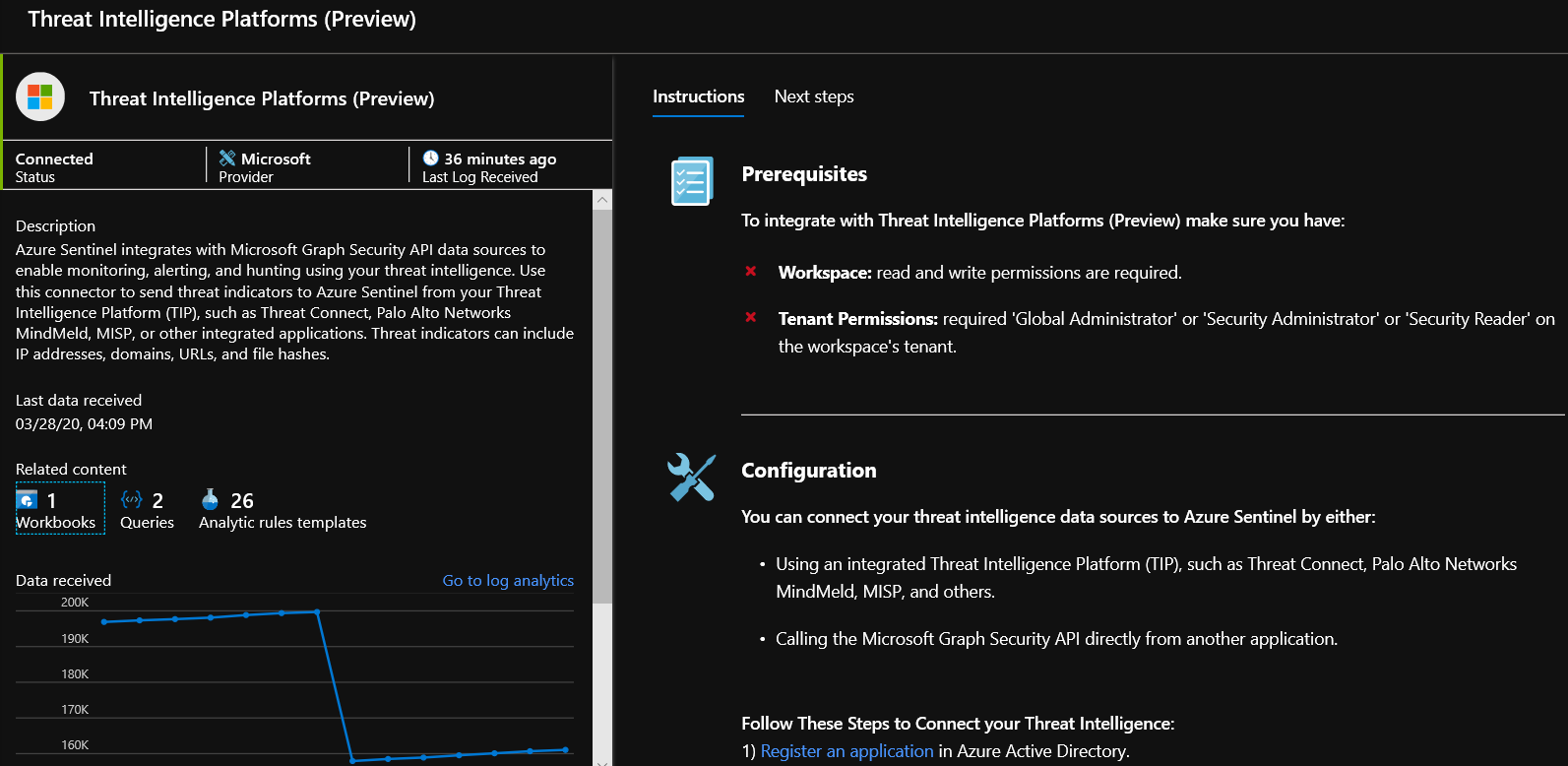
- In the Azure portal, navigate to Azure Sentinel > Data connectors and then select the Threat Intelligence Platforms (Preview) connector.

- Select Open connector page, and then Connect.
- To view the threat indicators imported into Azure Sentinel, navigate to Azure Sentinel – Logs > SecurityInsights and then expand ThreatIntelligenceIndicator.
6) Conduct Threat Hunting
We’ve covered threat hunting with Azure Sentinel in previous blogs in the series. There are dozens of built-in hunting queries in the Azure Sentinel Hunting blade and you can customize new ones per your requirements. There is also a community forum on GitHub with several repositories of useful queries. Below is a quick-start for running an exfiltration activity hunting with Azure Sentinel. For more information, see Azure Sentinel Hunting Queries.
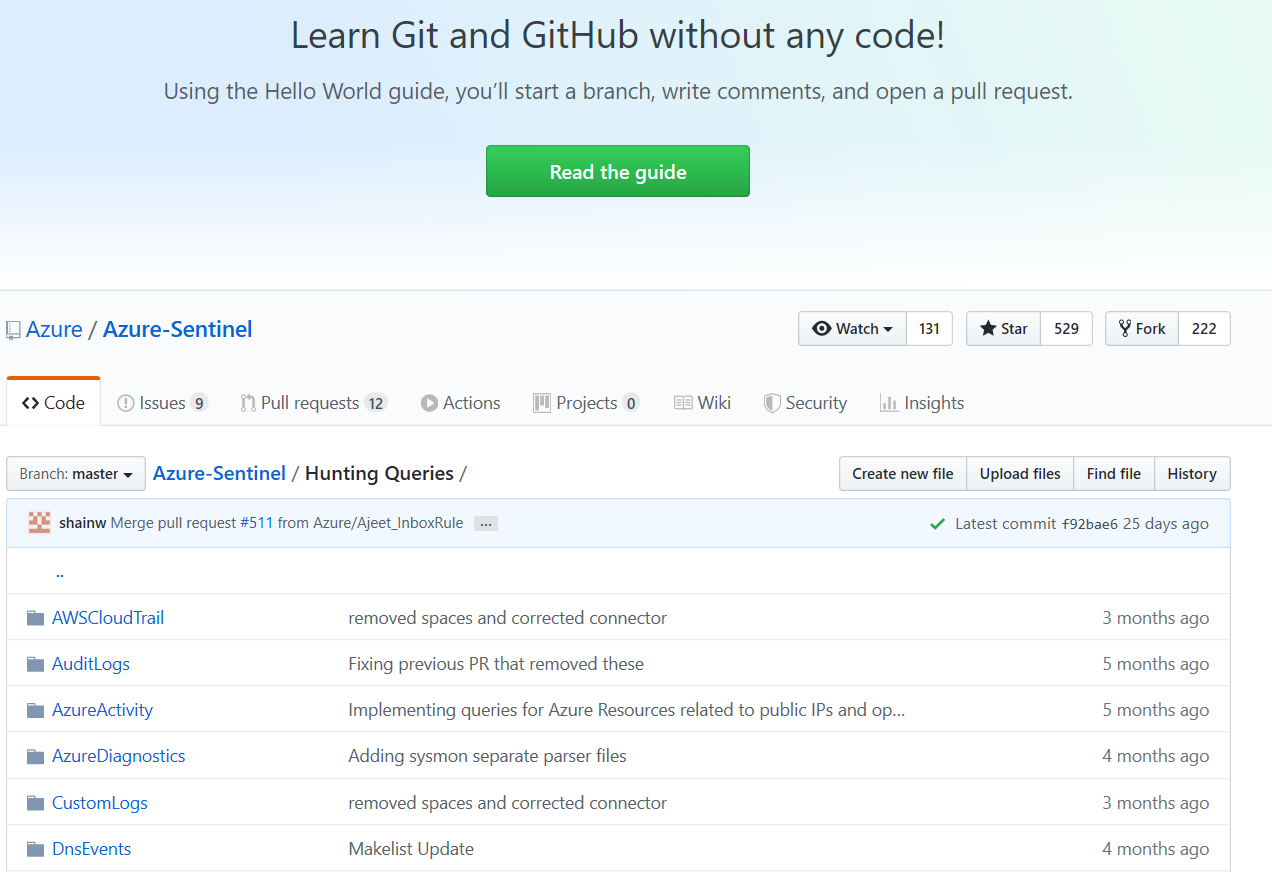
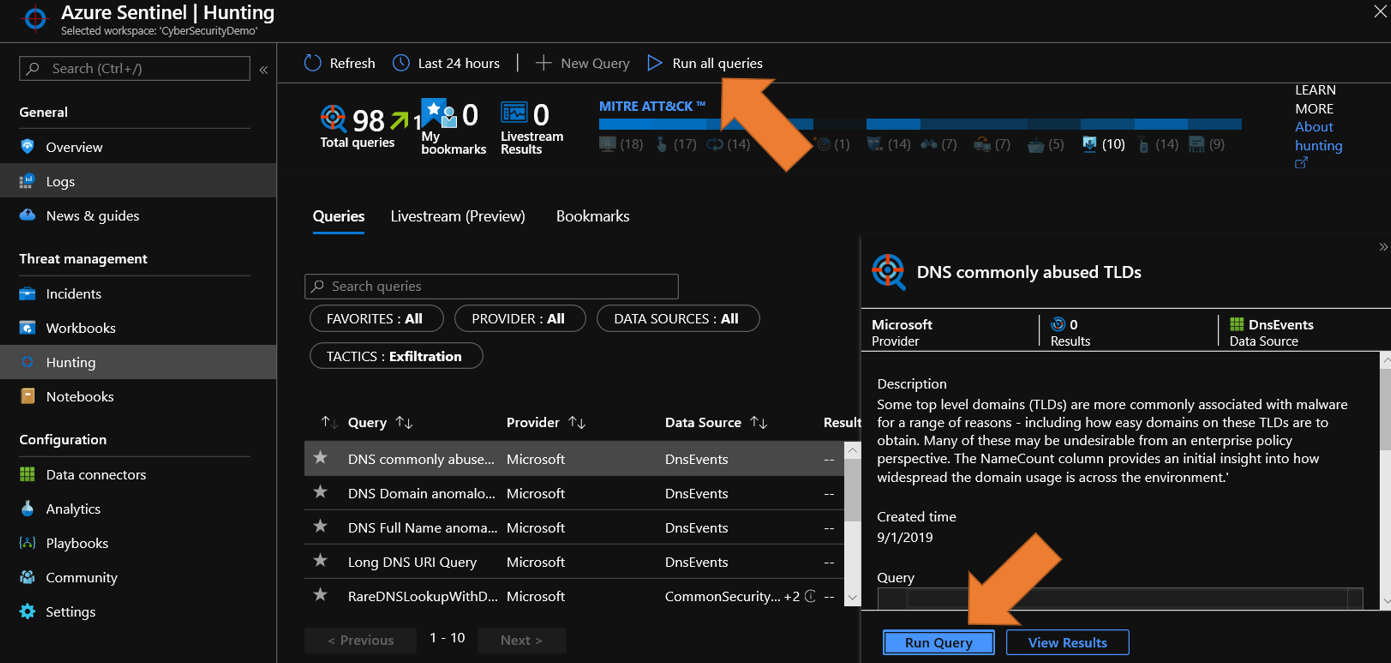
- Sign into the Azure Portal. Select the subscription in which Azure Sentinel will be created.
- Search for and select Azure Sentinel.
- Select target Azure Sentinel workspace.
- Select Hunting under Threat Management.
- Filter Tactics to Exfiltration.
- Select Run Query on a query of choice or select Run all queries to view events of interest.

7) Share Threat Data
Sharing threat data is another sign of a mature security organization. Newly formed organizations will often subscribe to external open source feeds for threat intelligence ingestion. As security organizations mature, threat intelligence teams are often formed to best leverage threat intelligence data. Threat intelligence teams will often consume multiple threat intelligence feeds from free, internal and external feeds. Threat intelligence teams often collaborate with external parties to bolster intelligence collection and sharing. Trust circles are formed between partners in similar industries for secure sharing and collaboration. For example, if you’re a bank security team it would make sense to collaborate with other banks in your industry to share indications of compromise (IOCs) because it’s likely the same tactics are being observed by both organizations.
An organizational threat intelligence team is one of the many indicators of a mature security organization. Threat intelligence groups are generally aligned with proactively hunting threats, hardening the organization against known threats and collaborating with external threat intelligence partners. Azure users can leverage the Azure Sentinel Community to bolster threat intelligence teams and threat data sharing. You can access the Azure Sentinel Community on Github via the configuration blade of Azure Sentinel. The Azure Sentinel Community is a user group collaborating with templates, workbooks, analytics, hunting and automation best practice. For more information, see Azure Sentinel Community.
Learn more about CMMC with Microsoft
Here are some of the best resource to learn more about CMMC in the cloud with Microsoft:
- Accelerating CMMC compliance for Microsoft cloud (in depth review)
- CMMC-AB Standards with Regan Edens – National Conversation
- Defense Federal Acquisition Regulation Supplement (DFARS)
- International Traffic in Arms Regulations (ITAR)
- Federal Risk and Authorization Management Program (FedRAMP)
- US Export Administration Regulations (EAR)
- NIST SP 800-171 Compliance
- Overview of the NIST SP 800-53 R4 blueprint sample
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.

0 comments