Dev Consultant Andrew Charbonneau shares some tips for adding security checks to your CI/CD pipelines.
When working with customers that are just starting their journey of converting to CI/CD pipelines within Azure DevOps, the initial focus is making sure their current manual build and release processes are automated. How do we take our current workflow, translate that into a series of automated jobs and tasks, and have the output mirror the existing process? This is a reasonable first step and often leads to the next round of questions. Can our pipeline do more? How do we build security steps into the process?
The answer may be even easier than everyone thought! The following are a few extensions and tasks that can be added to your pipelines. They all help build in security for your applications and are well received by most customers. Disclaimer – not all of these tasks/extensions are created by Microsoft.
White Source & White Source Bolt
WhiteSource is a platform that scans your code base for the use of any open source components. It then provides a report of any known vulnerabilities for each component, as well as the severity of each vulnerability. You just point the task to your repository and WhiteSource handles the rest. WhiteSource Bolt is the free version, and will run the scan mentioned; the paid/licensed version goes beyond that to provide additional functionality, including more robust reporting, real-time alerts, and even auto generated pull requests. An example of the report that shows alongside your build summary:
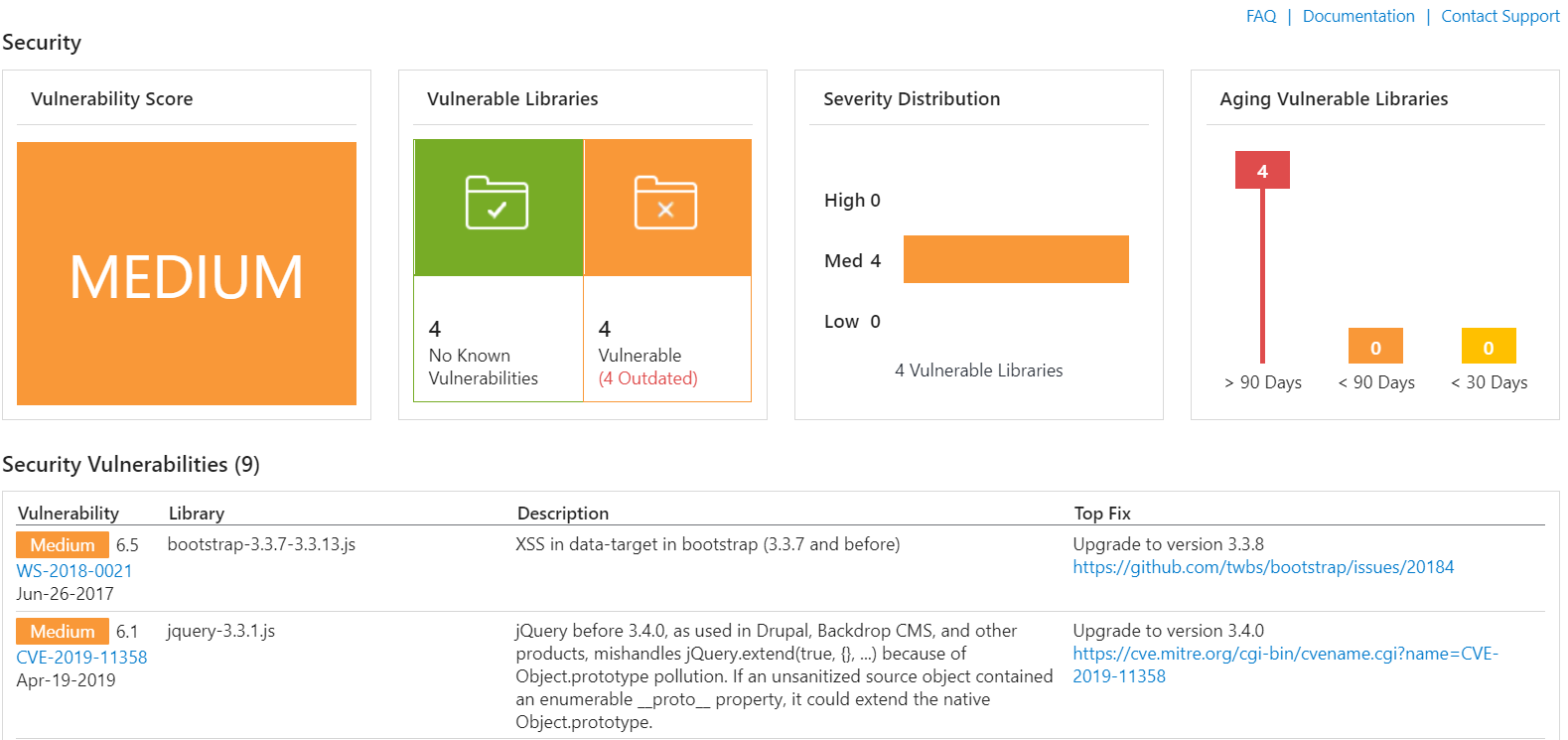
CredScan
CredScan is a task, which is part of the larger Microsoft Security Code Analysis Extension. CredScan runs within your build process, and will scan your code repo, like the last extension, but this time identifying any credentials that have been stored within the source code or any configuration files. The analysis tool will detect default passwords, connection strings and certificates with private keys – all things that significantly diminish the security of your application, and can be exploited by malicious parties. A report is then created that can be published with the rest of your build artifacts.
SonarQube
Many of you may already be familiar with SonarQube, but unaware that it can be implemented directly within your pipelines. For anyone unfamiliar with SonarQube, it is a platform that scans your code to find security vulnerabilities, code smells, and bugs; and then will create a report that can be reviewed with the pertinent information. SonarQube supports more than 20 different programming languages, but some do require a license to be purchased.
These 3 extensions can quickly help you build security into your build process, but by no means are the only tools that help provide some defense measures. I encourage everyone to think of additional ways of adding security to your CI/CD process, and seek out many of the other extensions in the marketplace that specialize in security. For an added challenge you can even try to setup these tasks to run in parallel or run as their own individual pipelines as part of your master branch build validations.

0 comments