In Visual Studio 2019 version 16.1 Preview 3 we have integrated AddressSanitizer (ASan) into Visual Studio for Linux projects. ASan is a runtime memory error detector for C/C++ that catches the following errors:
- Use after free (dangling pointer reference)
- Heap buffer overflow
- Stack buffer overflow
- Use after return
- Use after scope
- Initialization order bugs
You can enable ASan for MSBuild-based Linux projects and CMake projects that target a remote Linux system or WSL (Windows Subsystem for Linux). If you are just getting started with cross-platform development, I recommend following this walk-through to get started with Visual Studio’s native support for WSL.
ASan detects errors that are encountered during program execution and stops execution on the first detected error. When you run a program that has ASan enabled under the debugger, you will see the following error message (detailing the type of error and location) at the line where the error occurred:
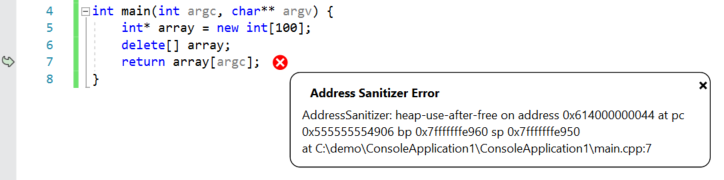
You can also view the full ASan output (including where the corrupted memory was allocated/deallocated) in the Debug pane of the output window.
Getting started with ASan in Visual Studio
In order to use ASan in Visual Studio, you need to install the debug symbols for ASan (libasan-dbg) on your remote Linux machine or WSL installation. The version of libasan-dbg that you load depends on the version of GCC you have installed on your Linux machine:
| ASan version | GCC version |
| libasan0 | gcc-4.8 |
| libasan2 | gcc-5 |
| libasan3 | gcc-6 |
| libasan4 | gcc-7 |
| libasan5 | gcc-8 |
You can determine the version of GCC you have on your Linux machine or WSL installation with the following command:
gcc –version
You can also view the version of libasan-dbg you will need by looking at the Debug pane of the output window. The version of ASan that is loaded corresponds to the version of libasan-dbg you will need on your Linux machine. You can search for the following line (ctrl + F) in the Debug pane of the output window:
Loaded ‘/usr/lib/x86_64-linux-gnu/libasan.so.4’. Symbols loaded.
In this example, my Linux machine (Ubuntu 18.04) is using libasan4.
You can install the ASan debug bits on Linux distros that use apt with the following command (this command installs version 4):
sudo apt-get install libasan4-dbg
If you have enabled ASan in Visual Studio, then we will prompt you to install the debug symbols for ASan at the top of the Debug pane of the output window.
Enable ASan for MSBuild-based Linux projects
You can enable ASan for MSBuild-based Linux projects in the project’s Property Pages. Right-click on the project in the Solution Explorer and select “Properties” to open the project’s Property Pages, then navigate to Configuration Properties > C/C++ > Sanitizers. ASan is enabled via compiler and linker flags and requires recompilation in order to work.
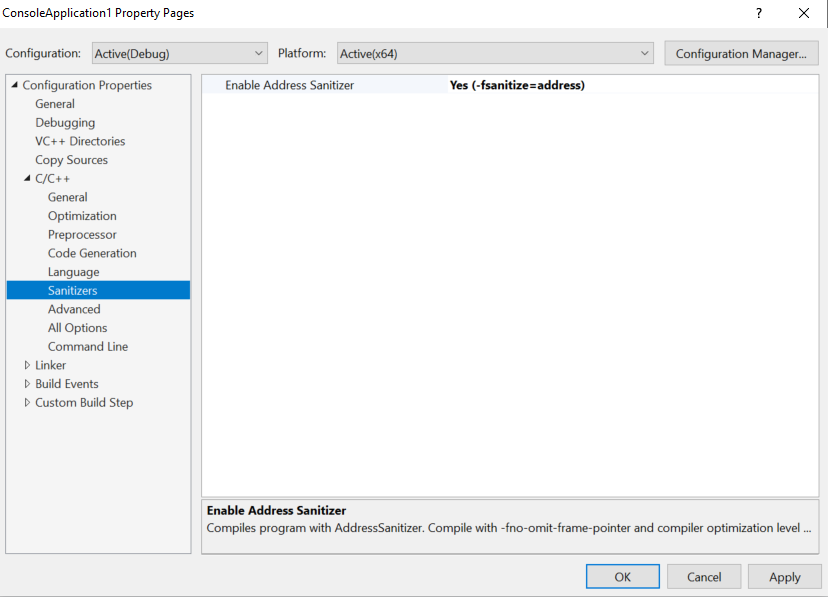
Note: Starting in Visual Studio 2019 version 16.4, AddressSanitizer for Linux projects is enabled via Configuration Properties > C/C++ > Enable Address Sanitizer.
You can also pass optional ASan runtime flags by navigating to Configuration Properties > Debugging > AddressSanitizer Runtime Flags.
Enable ASan for Visual Studio CMake projects
You can enable ASan for CMake configurations targeting a remote Linux machine or WSL in the CMake Settings Editor. In the “General” section of the editor you will see the following two properties to enable ASan and pass optional runtime flags: 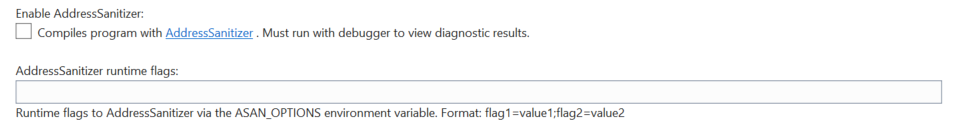
Again, ASan is enabled via compiler and linker flags and requires recompilation in order to work.
Give us your feedback!
If you have feedback on ASan for the Linux Workload or anything regarding our Linux support in Visual Studio, we would love to hear from you. We can be reached via the comments below or via email (visualcpp@microsoft.com). If you encounter other problems with Visual Studio or MSVC or have a suggestion, you can use the Report a Problem tool in Visual Studio or head over to Visual Studio Developer Community. You can also find us on Twitter (@VisualC) and (@erikasweet_).

Is this still supposed to work?
Just setup a Linux Console Application project using these instructions, and allowed “Enable Address Sanitizer” following this article. I’m trying to build a simple program against an Ubuntu 18 WSL machine, and get the error:
1>C:\Program Files (x86)\Microsoft Visual Studio\2019\Preview\MSBuild\Microsoft\VC\v160\Microsoft.CppBuild.targets(444,5): error MSB8058: -fsanitize=address (Enable Address Sanitizer) not supported by platform ‘x64’.
I’m using the latest VS2019 Preview 2
Hi,
Does VS code currently have this functionality?
I am trying to enable Address Sanitizer with WSL. First I understand that x64 is not supported. So I select x86 and I prompted to Connect to Linux. Why? Is this because WSL only works in x64? If I do need to provide a connection what is it for the WSL? If I disable the Sanitizer and enable X64 all works. Summary: Is Address Sanitizer, x64, WSL supported? Aside: In general WSL/VS2019 is good but just far too many different configurations and not all are possible which makes it difficult to use.
Hey Graham, thanks for the feedback. Are you using a CMake project or MSBuild-based project?
x64 + AddressSanitizer + WSL should be a supported scenario. The x64/x86 distinction you are referring to is specific to AddressSanitizer for Windows with MSVC. Can you please open a bug on Developer Community so we can investigate the issue?
And thanks for the feedback on the configurations. This is helpful as we work to improve VS2019.
Hi, Your article really helped me, but i have 1 problem.
When i add “detect_leaks=1” in “AddressSanitizer Runtime Flags”
I get libsan.so.pdb not loadedAlthough it is installed on my WSL.
How can i fix it?
Hi Valentin, sorry for the late reply. Unfortunately LeakSanitizer doesn’t work under ptrace (strace, gdb, etc.). Visual Studio’s ASan integration for Linux projects is integrated with the debugger (which leverages gdb) so LeakSanitizer is not integrated with Visual Studio as this time.
Erika,For me the ASan is ignored. At least I don't see any effect.I have a WSL (Ubuntu, presumably 18.04, default installed yesterday). I have MS VS Enterprise 2019 Preview, 16.3.0, Preview 2.0 (installed yesterday).I successfully built the "Hello CMake" example from "C++ with Visual Studio 2019 and Windows Subsystem for Linux (WSL)" and the example works fine both in WSL console and on native Ubuntu Linux 19.04.
# I have the following `libasan` packages installed in WSL:$ dpkg -l *asan*Desired=Unknown/Install/Remove/Purge/Hold| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)||/ Name Version Architecture Description+++-========================-=================-=================-=====================================================ii libasan4:amd64 7.4.0-1ubuntu1~18 amd64 AddressSanitizer -- a fast memory error detectorii libasan4-dbg:amd64 7.4.0-1ubuntu1~18...