You’ve probably heard some version of the story about a developer who mistakenly checked in his AWS S3 key to Github. He pulled the key within 5 minutes but still racked up a multi-thousand dollar bill from bots that crawl open source sites looking for secrets. As developers we all understand and care about keeping dev and production secrets safe but managing those secrets on your own or especially in a team can be cumbersome. We are pleased to announce several new features that together will make detecting secrets in code and working with secrets stored securely on Azure easier than it’s ever been before.
- App Services Authentication Extension for Visual Studio 2017 version 15.5 or later
- Managed Service Identity (MSI) support in Azure App Services
- ASP.NET Key Vault and User Secret Configuration builders Builder | .NET 4.7.1
- Credential Scanner (CredScan) Code Analyzer Preview
Safeguarding Secrets while building for Azure
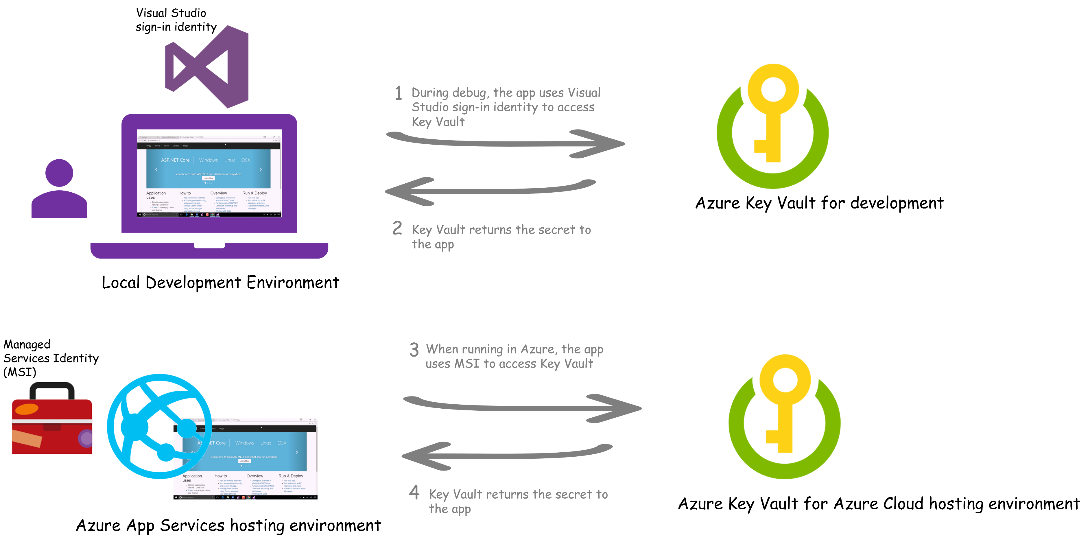
Most of us know it’s a best practice to keep secret settings like connection strings, domain passwords, or other credentials as a runtime configuration and outside the source code. Azure Key Vault provides a security location to safeguard keys and other secrets used by cloud apps. Azure App services recently added support for Managed Service identity which means apps running on App Service can easily get authorized to access a Key Vault and other AAD-protected resources so you no longer need to store secrets visibility in environment variables.
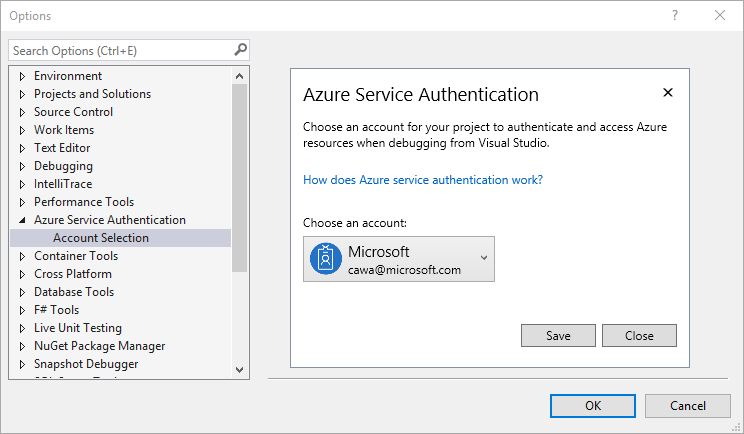
If you do this though, getting your local dev environment setup with the right secrets can be a pain, especially if you work in a team. We hear many developers distribute secrets for shared dev services through email or just check them into source code. So we created the App Authentication Extension to make it easy to develop apps locally while keeping your secrets in Key Vault. With the extension installed, your locally running app uses the identity signed into Visual Studio to get secrets you are authorized to access directly from Key Vault. This works great in a team environment where you might have security group for the dev team with access to a dev environment Key Vault.
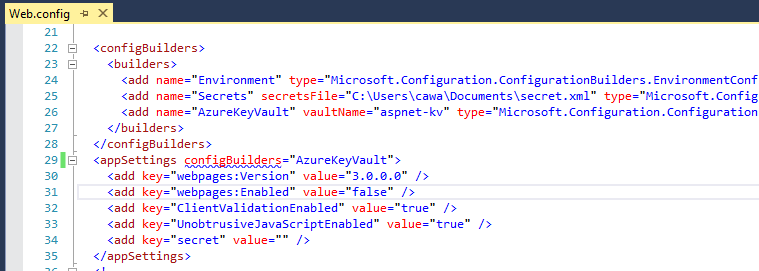
In ASP.NET applications the ASP.NET Key Vault and User Secret configuration builders with .NET 4.7.1 is a NuGet package that allows secret app settings to be saved in secure configuration stores instead of in web.config as plaintext, without changing application source code. In ASP.NET Core applications there is a small code change, to load Key Vault as a configuration provider and once you do this you are set. This change isn’t done yet, but we’re hoping to eliminate it soon.
Here are a couple of walkthroughs that show you how everything works:
- ASP.NET: app-service-msi-keyvault-dotnet
- ASP.NET Core: aspnetcore-msi-keyvault
Credential Scanner (CredScan) Code Analyzer Preview
We also wanted to make it easier for devs to find secrets in their code to encourage moving secrets to more secure locations like User Secrets or Azure Key Vault. The Credential Scan Code Analyzer is a very early preview that can detect Storage access keys, SAS tokens, API management keys, Cosmos DB access keys, AAD Service principal keys, connection strings for SQL, Azure SQL, Service Bus, Azure Logic apps, BizTalk server, and various other credential types. As you edit your code the analyzer scans your code and immediately warns you about secrets it finds in any open documents with warnings in the error list and in the Build and Code Analysis at Commit time. It’s something we’ve been developing, utilizing, and improving within Microsoft for some time now.
The Credential Scan Code Analyzer is a preview and ships in the experimental DevLabs extension, Continuous Delivery Tools for Visual Studio. This is because we know this is an important area that goes beyond open documents and can stretch all the way into your CI environment. Rather than waiting, we released an experimental version now because we think it’s useful and we want your feedback on how you would use this in your environment.
Please install these extensions and give the walkthroughs a try to let us know what you think.
 |
Catherine Wang, Program Manager, Azure Developer Experience Team @cawa_cathyCatherine is a Program Manager for Azure Developer Experience team in Microsoft. I worked on Azure security tooling, Azure diagnostics, Storage Explorer, Service Fabric and Docker tools. Interested in making development experience simple, smooth and productive. |

0 comments