Summary: Ed Wilson, Microsoft Scripting Guy, talks about filtering event log events with the Get-WinEvent cmdlet.
 Hey, Scripting Guy! I try to use the Get-WinEvent cmdlet to search event logs, but it is pretty hard to do. Also, I don’t see the nice switches that I had with Get-EventLog, so I don’t see why I should use the other cmdlet and have to pipe everything to Select-Object or Where-Object.
Hey, Scripting Guy! I try to use the Get-WinEvent cmdlet to search event logs, but it is pretty hard to do. Also, I don’t see the nice switches that I had with Get-EventLog, so I don’t see why I should use the other cmdlet and have to pipe everything to Select-Object or Where-Object.
—EG
 Hello EG,
Hello EG,
Microsoft Scripting Guy, Ed Wilson, is here. One of the things that you need to realize is that with Windows PowerShell, one should always filter to the left of the pipeline. This is the prime directive when it comes to working with large amounts of data. Event logs can be huge and contain massive amounts of data. They can consume huge amounts of bandwidth when they are delivered across the network or other places. Like the alligator that the Scripting Wife and I saw while we were hiking the other day, this can be a hidden trap with serious outcomes if the network admin is not paying attention.
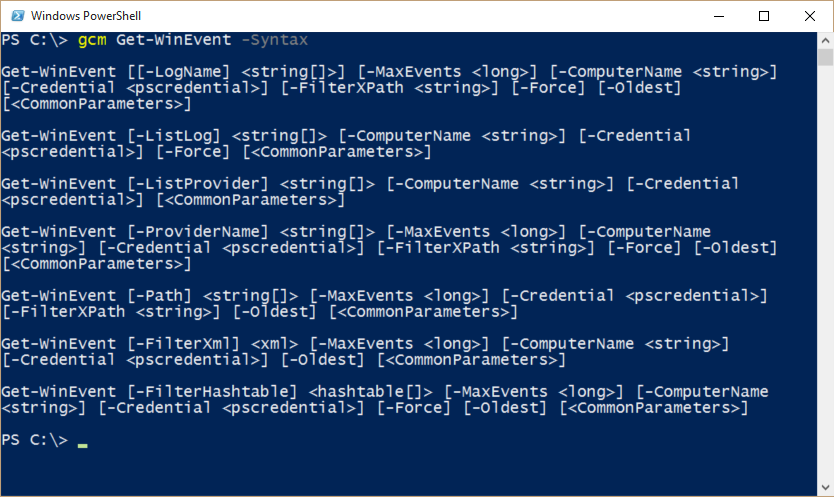
Seven parameter sets
The Get-WinEvent cmdlet has a number of parameter sets. In fact, it has seven parameter sets. For the sake of the IT pro who needs to filter data from event logs, there are exactly three parameter sets. The parameter sets are shown here:
Here are the three filter parameters:
PS C:\> ((gcm Get-WinEvent | select -expand parametersets).parameters).where({$_.name
-match '^filter'}) | select name -Unique
Name
—-
FilterXPath
FilterXml
FilterHashtable
Of the three filter parameters, the easiest for me to use is FilterHashTable. The FilterHashTable parameter accepts…wait for it…you will never guess this one…
…a hash table.
That is right, the FilterHashTable parameter accepts a hash table as the input parameter.
Note If you need a refresher about hash tables, see Learn the Basics of PowerShell Hash Tables.
Here is the most important thing you need to understand when using the FilterHashTable parameter:
Everything goes into the hash table.
The syntax is shown here:
Get-WinEvent [-FilterHashtable] <hashtable[]> [-MaxEvents <long>] [-ComputerName
<string>] [-Credential <pscredential>] [-Force] [-Oldest] [<CommonParameters>]
I said everything—well obviously, not everything. But things used for filtering the events, such as the event log name, the ID, and stuff like that go into the hash table. Here is a table of things you can use when creating a filter hash table:
|
Key name |
Value data type |
Accepts wildcard characters? |
|
LogName |
<String[]> |
Yes |
|
ProviderName |
<String[]> |
Yes |
|
Path |
<String[]> |
No |
|
Keywords |
<Long[]> |
No |
|
ID |
<Int32[]> |
No |
|
Level |
<Int32[]> |
No |
|
StartTime |
<DateTime> |
No |
|
EndTime |
<DataTime> |
No |
|
UserID |
<SID> |
No |
|
Data |
<String[]> |
No |
|
* |
<String[]> |
No |
The filter hash table takes the following form:
- At sign
- Opening Curly bracket
- Keyname
- Equals
- Value
- Closing Curly bracket
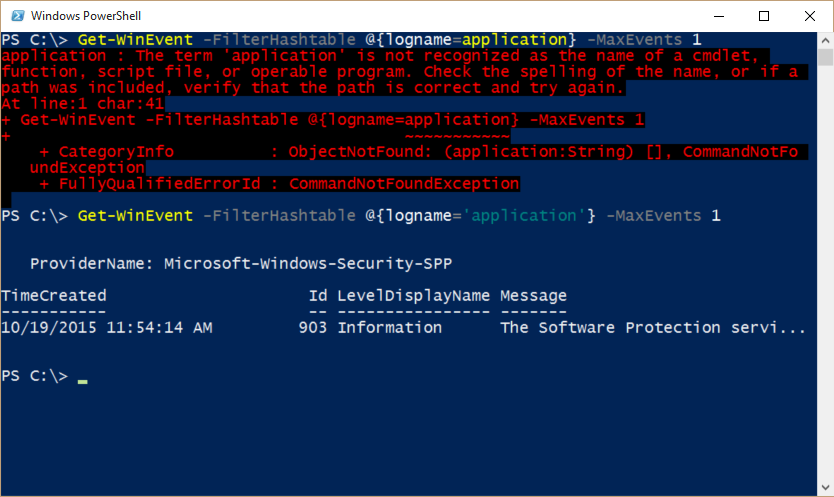
Here is a simple example that returns all the events from the application log:
Get-WinEvent -FilterHashtable @{logname='application'}
Although PowerShell is often very good at converting input to the required data type (dynamic type system), the filter hash table must have the string values placed in single or double quotation marks. For example, if I don't put my value for the LogName keyword in quotation marks, the following error message appears:
Note When testing a filter hash table for the Get-WinEvent cmdlet, it is a good idea to limit the amount of data returned to just a few records. This is where MaxEvents is a useful parameter.
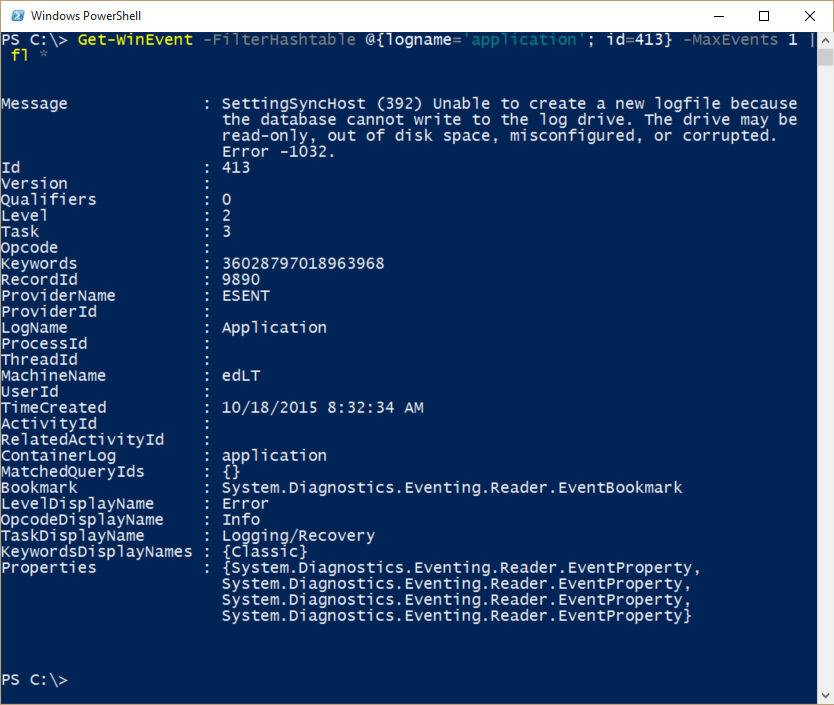
To add another key name/value combination to FilterHashTable, separate the key name=value pair with a semicolon. This is shown here, where I search the Application log for event ID 413.
Get-WinEvent -FilterHashtable @{logname='application'; id=413}
I can get an idea about the properties and values of an event log record by selecting a single event and piping the output to the Format-List cmdlet (fl is an alias). I then select all of the properties by using the asterisk ( * ) wildcard character. This is shown here:
By looking at the leven parameter, and knowing that my entry is an error record, I can surmise that I can filter specifically on events that have the ID of 413 and are error records. Again, I use a semicolon to separate my key name=value pair. Here is my revised query:
Get-WinEvent -FilterHashtable @{logname='application'; id=413; level=2}
The output is shown here:
PS C:\> Get-WinEvent -FilterHashtable @{logname='application'; id=413; level=2} -MaxEvents 1
ProviderName: ESENT
TimeCreated Id LevelDisplayName Message
———– — —————- ——-
10/18/2015 8:32:34 AM 413 Error SettingSyncHost (392) Unable …
PS C:\>
EG, that is how you can use Windows PowerShell to read the event logs. Join me tomorrow when I will talk about more cool stuff.
I invite you to follow me on Twitter and Facebook. If you have any questions, send email to me at scripter@microsoft.com, or post your questions on the Official Scripting Guys Forum. See you tomorrow. Until then, peace.
Ed Wilson, Microsoft Scripting Guy


0 comments