Summary: Microsoft Scripting Guy, Ed Wilson, teaches how to configure remote security settings for Windows PowerShell.
![]() Hey, Scripting Guy! I am a Help Desk Support Manager, and I have written a series of scripts that I want to allow the help desk support people to use. These scripts collect basic information, and output to a file that is then emailed to Tier 2 support when necessary. I have found this to be an effective way to streamline our help desk operation. The problem is that I do not want to make our Tier 1 support people Administrators on the remote machines.
Hey, Scripting Guy! I am a Help Desk Support Manager, and I have written a series of scripts that I want to allow the help desk support people to use. These scripts collect basic information, and output to a file that is then emailed to Tier 2 support when necessary. I have found this to be an effective way to streamline our help desk operation. The problem is that I do not want to make our Tier 1 support people Administrators on the remote machines.
— LB
![]() Hello LB, Microsoft Scripting Guy Ed Wilson here. When I was scuba diving in Little Cayman, I had the opportunity to take pictures of Nassau Groupers. These are beautiful and friendly fish as seen in the following figure, (although unfortunately endangered due to overfishing). Speaking of groupers, LB, the solution to your problem is to use groups.
Hello LB, Microsoft Scripting Guy Ed Wilson here. When I was scuba diving in Little Cayman, I had the opportunity to take pictures of Nassau Groupers. These are beautiful and friendly fish as seen in the following figure, (although unfortunately endangered due to overfishing). Speaking of groupers, LB, the solution to your problem is to use groups.

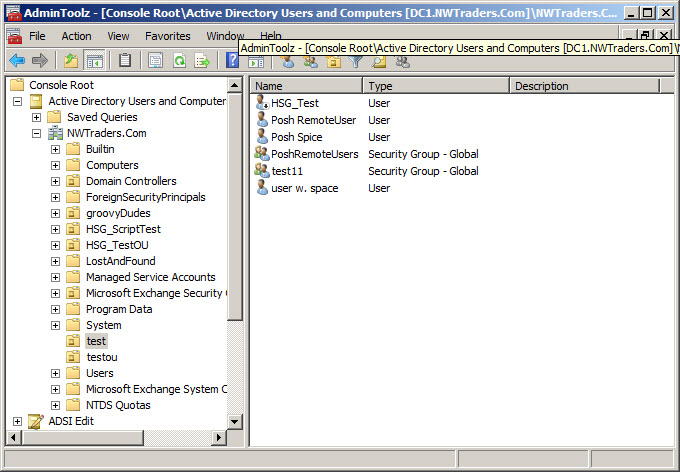
The first thing you need to do is to create a group, such as the one seen in the following figure.
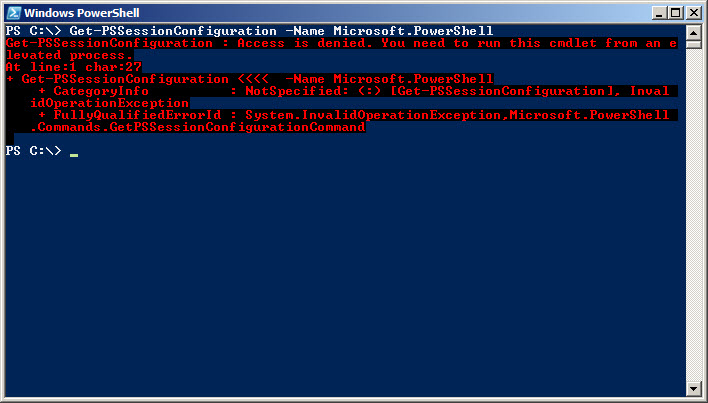
If you attempt to work with the Windows PowerShell session configuration information, and you do not start Windows PowerShell as an Administrator, an error will occur. Windows PowerShell will not allow you to retrieve session configuration information if you are not running as an Administrator. This error is seen here.
After you start the Windows PowerShell console with admin rights (right-click the Windows PowerShell icon and select Run as Administrator from the Action menu), you can use the Set-PSSessionConfiguration Windows PowerShell cmdlet to modify the security configuration for Windows PowerShell remoting. The easiest way to do this is to use the ShowSecurityDescriptorUI switched parameter to force the cmdlet to display a graphical interface that allows you to add a Security Group to the access control list for the session. In addition to using the ShowSecurityDescriptorUI switched parameter, you will also need to specify the name parameter to indicate the application to be configured. In this example, use Microsoft.PowerShell. I also like to use the force parameter to keep the cmdlet from prompting me. To me the prompt is annoying, and even a little misleading, as I have not changed or configured anything yet, and the prompt says that I am going to be “Performing operation “Set-PSSessionConfiguration” on Target “Name: Microsoft.PowerShell.” This is one of those “Well, duh” moments that arise when I say “Of course I am going to run the cmdlet, I just told you to do so.” The prompt is shown here.
PS C:\Windows\system32> Set-PSSessionConfiguration -ShowSecurityDescriptorUI -Name Mi
crosoft.PowerShell
Confirm
Are you sure you want to perform this action?
Performing operation “Set-PSSessionConfiguration” on Target “Name:
Microsoft.PowerShell”.
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help
(default is “Y”):
The command, (which is typed on a single line, but is wrapped here for publication on the blog) incorporating the force parameter is seen here.
PS C:\Windows\system32> Set-PSSessionConfiguration -ShowSecurityDescriptorUI -Name Mi
crosoft.PowerShell -Force
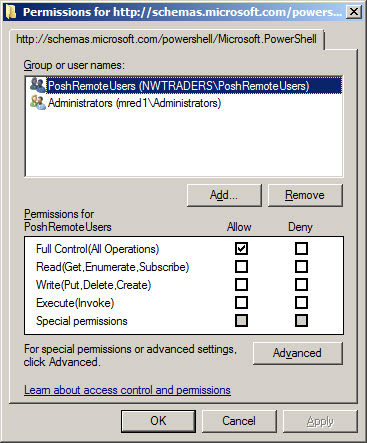
Once the command runs, the following permissions dialog box appears. As seen in the following figure, I have added the PoshRemoteUsers group and granted them full control.
I now pop over to a remote computer, and attempt to run a script block on my mred1 computer – the computer to which I just made the Windows PowerShell session configuration change. The user nwtraders\pshUser is not a member of the PoshRemoteUsers group, and therefore as a plain everyday user, does not have remote rights to my machine. When I run the following command an error arises.
Invoke-command -computername mred1 -scriptblock {hostname} -credential nwtraders\pshuser
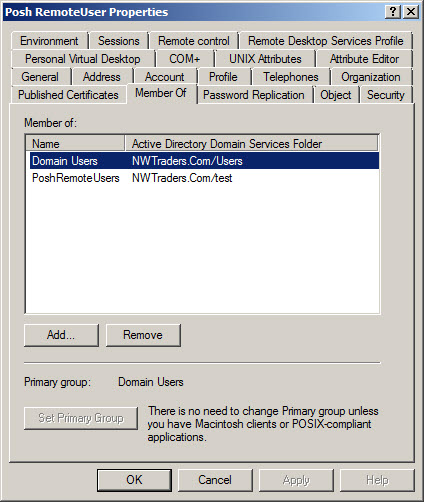
If I execute the command as the nwtraders\posh remoteuser the command succeeds because the posh remoteuser was added to the PoshRemoteUsers group. Keep in mind, that posh remoteuser is an ordinary user, and has no added group memberships other than membership in the PoshRemoteUsers group and the Domain Users group. This is seen in the following figure.
To test things out, I open a Remote Desktop session on a remote Windows 7 desktop, open Windows PowerShell and attempt to make a connection to the Mred1 computer. Because the posh remoteuser has a space in it, I thought there might be some confusion on using it from the Windows PowerShell console. Therefore I attempted different configurations of the name. The results are shown in this figure.

LB, that is all there is to configuring security for Windows PowerShell remoting. Remoting week will continue tomorrow when I will talk about working with remote sessions.
I invite you to follow me on Twitter or Facebook. If you have any questions, send email to me at scripter@microsoft.com or post them on the Official Scripting Guys Forum.. See you tomorrow. Until then, peace.
Ed Wilson, Microsoft Scripting Guy

0 comments