In this post, Senior Application Development Manager, Anand Shukla shares some tips to harden your web server’s SSL/TLS ciphers.
I recently worked with a customer who had security requirements to disable the weak RC 4 ciphers from their Windows 2008 and Windows 2003 servers. The process is little different for Windows 2008 R2 servers and Windows 2003 servers, and there are multiple articles on internet on how to disable the RC 4 ciphers.
Below is a quick summary.
- Windows 2008 R2 – Check if security update 2868725 is installed, which allows disabling of RC4. If you have this update, you should have the registry setting which allows disabling of the RC4 and you can go ahead and apply the registry changes as mentioned in the article. If not, first apply the update and then change the registry settings.
- Windows 2003 SP2 – You need to make sure that the support for strong ciphers are added and then disable the weak ciphers.
One of the main challenges was testing for weak ciphers to make sure it is remediated. We could use SSL Labs for external facing application; but this was not feasible for internal applications. Nmap worked beautifully for this need.
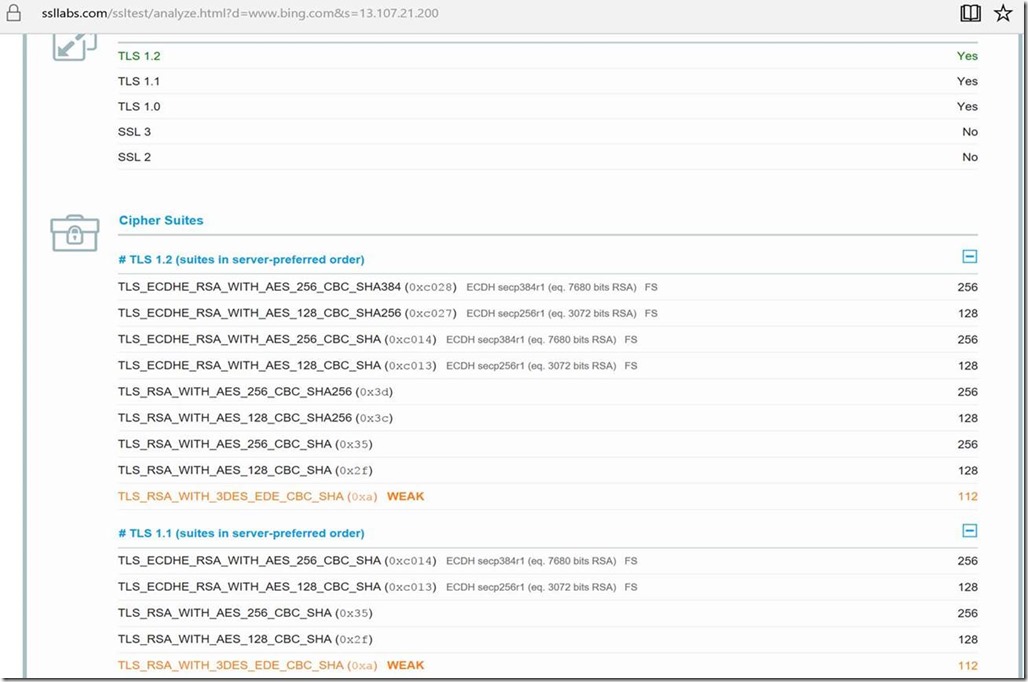
Here is the screenshot from https://ssllabs.com for testing SSL protocols and Cipher information for www.bing.com
You can download the nmap from https://nmap.org/download.html and run the following commands to check for ciphers. The first command finds out all the ports for SSL, and second one lists down the Ciphers available.
nmap -sV –reason -PN -n –top-ports 100 www.bing.com
nmap –script ssl-cert,ssl-enum-ciphers -p 443 www.bing.com
See the article for more details – https://www.owasp.org/index.php/Testing_for_Weak_SSL/TLS_Ciphers,_Insufficient_Transport_Layer_Protection_(OTG-CRYPST-001)
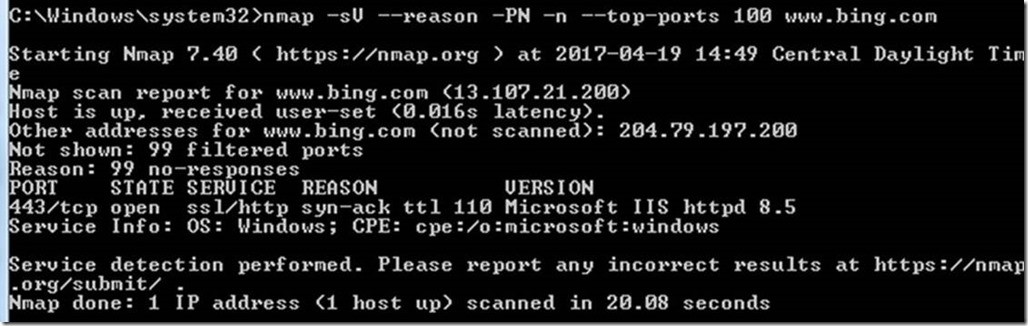
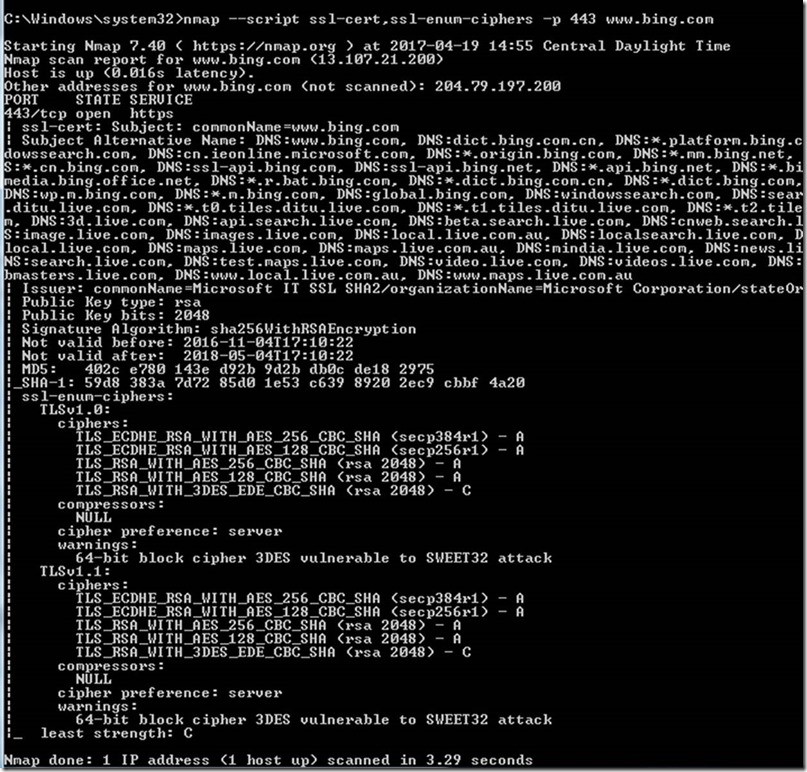
This approach helped us remediate the weak ciphers from servers and make sure they were removed.
Premier Support for Developers provides strategic technology guidance, critical support coverage, and a range of essential services to help teams optimize development lifecycles and improve software quality. Contact your Application Development Manager (ADM) or email us to learn more about what we can do for you.

nitpick: you use U+2013 : EN DASH instead of ascii minus in your nmap samples.