Authentication experiences are the gateway to consumer applications. Friction in sign-up or sign-in has a direct impact on user onboarding, retention, and ultimately company revenue. These processes should be smooth and align with your brand’s identity to instill consumer confidence and trust. With that, we’d like to share some work we’re doing to make this easier and invite you to get an early look.
Why Native Authentication matters
In the standard, browser-delegated mobile app login process, users often experience a disruptive jump during authentication. They are taken to a system browser for authentication only to be redirected back to the app when the login is complete. This leads to a diluted experience and branding can be compromised. Consumer mobile app developers often look for solutions that give them greater control over the user interface and experience.
Craft seamless, pixel-perfect authentication experiences
Native Authentication empowers you to take complete control over the design of the login experience. It allows you to craft stunning, pixel-perfect authentication screens that seamlessly integrated into your apps, rather than having to rely on browser-based solutions.
You can build rich, mobile-first sign-up and sign-in journeys using either our API or the Microsoft Authentication Library (MSAL), for Android and iOS. This API-centric approach offers extensive flexibility in design as well as the ability to create highly customized interactions and flows. All of which are essential for crafting stunning and delightful consumer mobile applications.
Authentication made simple, while you focus on building your app
We have designed our SDK with some key principles in mind. All with the goal of simplifying the process of adding authentication to your app:
No identity expertise required
Our SDK offers scenario-based, intuitive interfaces that eliminate the need for deep identity knowledge. The interfaces abstract away the details of the identity protocol and automatically take care of caching, session, and token management, offering a secure and reliable way of adding authentication.
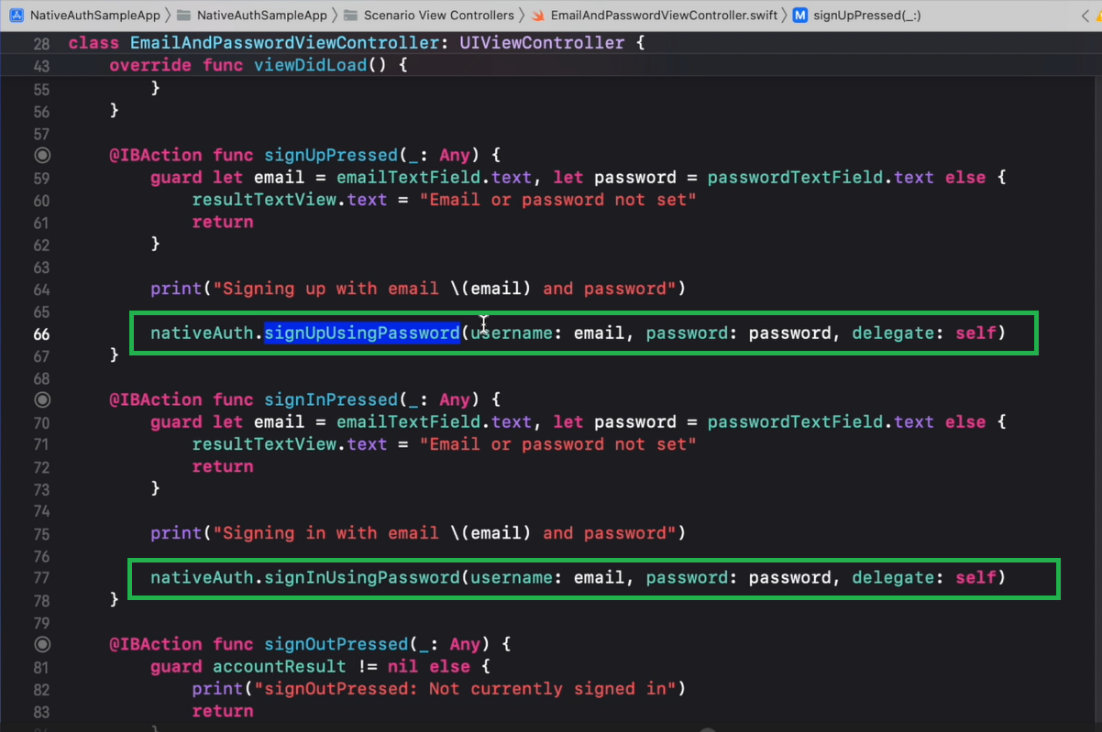
Discoverable via IDE
We appreciate that following long, step-by-step guides can be tedious. Which is why the native authentication SDK takes full advantage of IDE autocompletions, making integration a breeze with improved developer productivity.
State machines limit developer error
Coding errors are reduced by modelling SDK flows as a state machine. The states closely mimic actual user login flow. The design of the state machine limits what actions a developer can implement at each state. Let’s say, for example, a one-time passcode has been sent and the state machine is now in a state called CodeRequired. Developers can call only methods that make sense for that state—submitCode() and resendCode(). The IDE will automatically restrict any other methods at this state, effectively minimizing the potential for developer error and abstracting away the complexities of protocol orchestration.
Secure from the ground up
The Native Authentication SDK and the underlying API have been designed from the ground up with security in mind. The Microsoft Identity standards team and other industry players are working within the IETF to define a new standard that enables first-party clients to support native interaction patterns. Our API and SDK are based on this and enable native apps to authenticate securely, leveraging platform security capabilities like identity protection, and others, yet to be implemented, such as conditional access and MFA.
Participate in the private preview program
We are actively looking for developers to participate in a private preview of this new feature, ahead of the broader public preview release. If you are interested, or you believe this would be valuable for your organization, we would be happy to collaborate with you. Simply click the link below to register!
Join us at Microsoft Ignite
If you’re attending the Microsoft Ignite conference this week, you’ll have the opportunity to sit down with one of our experts in a one-on-one session to ask them questions about your own particular scenarios. Sessions will take place both virtually and in-person, at the Connection Zone at Ignite, and are available to book for free now.
Let’s stay connected
To learn more or test out features of the Microsoft Entra suite of solutions, visit our developer center. Sign up for email updates on the Identity blog to keep up with all things Identity. And, follow us on YouTube for video overviews, tutorials, and deep dives.


Any solution that involves passwords should be a massive red flag these days. The whole industry is moving towards Passkeys which are much more secure and resistant to phishing. Shouldn’t this be the primary focus now?
Passkeys are great because it brings in the right balance of user experience and security. We do see Passkeys playing a key role in the auth spectrum and it has been a big part of our focus. While the adoption of Passkeys is picking up in CIAM space, unfortunately it is still has limited familiarity among consumers who still find one-time pass-codes and passwords more familiar and is being used extensively by customers. With Native Authentication we aim to bring to our developers a wide range of auth methods so that they can choose what best suits their needs.
Is this available for B2C type scenarios?
This is available on Microsoft Entra ID for customers. It is not available for Azure AD B2C. This allows you to achieve the most common B2C scenarios on Microsoft Entra ID for customers.