Adding flexibility to authentication with Microsoft Entra External ID custom extensions
As the much-anticipated, Microsoft Ignite conference edges (no pun intended) closer to the final (in-person only) day tomorrow, we hope you’ve been enjoying the interesting sessions and come away feeling energized!
Now, we’re excited to announce the public preview of a new set of extension points that enable you to add your own logic to Microsoft Entra External ID.
In this blog post, we explore the power of Custom Authentication Extensions and touch on how to use them.
Microsoft Entra External ID is designed with flexibility in mind and this new release allows you to further tailor your authentication journeys to your bespoke needs. Let’s dive in.
Building authentication your way
At Microsoft Build 2023, we introduced the concept of custom authentication extensions as an innovative feature of the newly launched Microsoft Entra External ID product offering. Microsoft Entra External ID is a unified platform that brings together the enterprise-grade controls of Microsoft Entra ID (formerly Azure AD) and the flexibility, customizability, and improved UX of Azure AD B2C.
ICYMI, here’s the recording of the Build 2023 session on Microsoft Entra External ID where we show you how to use custom extensions.
Custom authentication extensions allow you to build authentication experiences that are secure and adaptable to your specific business logic. In addition to the built-in authentication events within a sign-up and sign-in user flow, custom authentication extensions can be added at specific points within the authentication flow. They allow you to incorporate your own code and logic into how authentication flows work.
Custom extensions operate on an event-based model. During the authentication flow, there are certain points where we can add a hook. At these points, you have the ability to make a call out to an external API endpoint to modify the authentication flow.
In this release, we are adding new points to add hooks during sign-up, at the beginning of the attribute collection step, and after the user enters and submits attributes. See screenshot below.
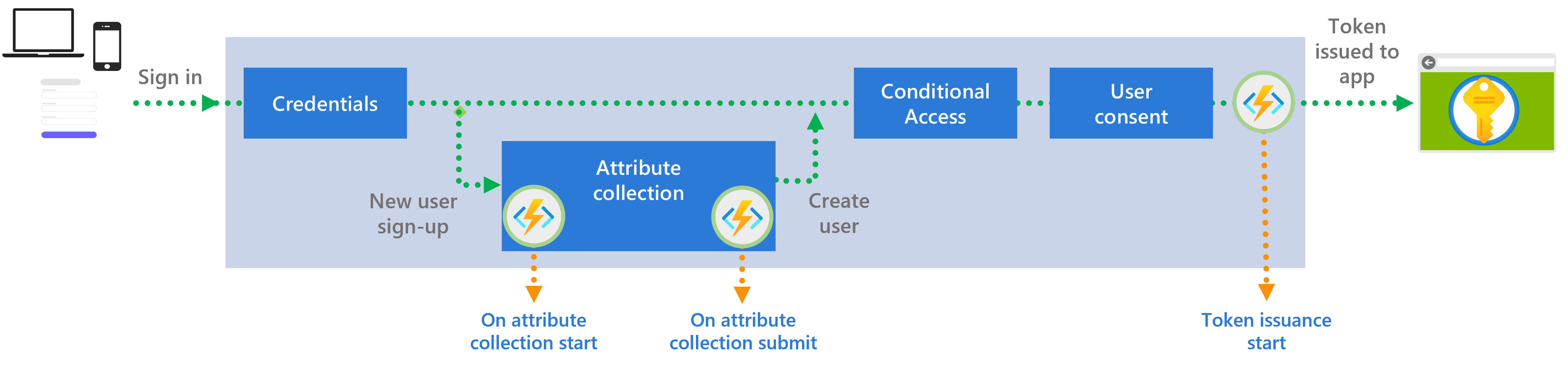
These new custom extension points are being added in addition to the token issuance custom extensions, announced at Build 2023—which trigger just before a token is issued to the application—and the existing pre-defined, built-in authentication configurations within a sign-up and sign-in user flow.
New extension events for enhanced customization
This latest update introduces an array of new extension events designed to provide you with an extensive level of control over user registration and authentication, ensuring a smooth and secure experience for end users. Here’s a closer look at what’s now possible:
- Prefilling attributes: Simplify your user’s sign-up experience by prefilling attributes based on existing information, reducing the time and effort needed to complete registration forms.
- Validating attributes in real-time: Enhance data accuracy with real-time validation of user inputs. This feature ensures that the information collected meets your specific criteria, right at the point of entry.
- Dynamic attribute updating: Adapt to changing user information seamlessly. Our new functionality allows for the immediate updating of user attributes during the sign-up process, ensuring that your records are always current.
- Selective sign-up blocking: Implement enhanced security measures by having the option to block sign-ups based on predetermined criteria. This is crucial for maintaining the integrity of your user base and preventing fraudulent activities.
To see how to implement these scenarios, check out this tutorial with code samples and implementation guidance.
The journey to General Availability (GA)
As we work towards the General Availability release of Microsoft Entra External ID, we continue our ongoing commitment to innovation and improvement. We are continuously working on expanding our offerings, with a focus on delivering solutions that meet and exceed your expectations.
Calling all developers and tech vendors
We are particularly excited about the potential of these updates and encourage developers and technology vendors to get familiar with them and try them out.
Visit our docs to learn how to configure custom authentication extensions for attribute collection and submit events. You can also learn more about custom claims providers and learn how to configure a custom claims provider token issuance event. This event is triggered right before the token is issued and allows you to call a REST API to add claims to the token.
Your feedback is invaluable to us—it helps in refining these extensions and identifying any additional functionalities that could be beneficial. We’re eager to hear about your experiences, the challenges you face, and the solutions you seek.
Let’s stay connected
To learn more or test out features of the Microsoft Entra suite of solutions, visit our developer center. Sign up for email updates on the Identity blog to keep up with all things Identity. And, follow us on YouTube for video overviews, tutorials, and deep dives.
Stay tuned for more updates on Microsoft Entra External ID and additional custom authentication extensions. The future of authentication is here, and it’s more flexible and tailored than ever before.

 Light
Light Dark
Dark
1 comment
First off this is awesome. Second, I was trying to implement and had a question on whether this is intended for internal (single tenant) implementation only or if you had plans for multi-tenant? I noticed the setup was on the Enterprise Application Level and not the Application registration. To ask clients to set this up every time they install the application might be a bit cumbersome. What would you suggest to SaaS software company who has a multi-tenant architecture that wants to take advantage of this? Or I may be misunderstanding something and I just need to read the right documentation 🙂 Let me know if you can help.