This week at Microsoft Build, we introduced Microsoft Entra External ID, our next generation of customer identity and access management (CIAM) solution that evolves Azure AD External Identities to help developers efficiently build secure and compliant applications for customers, partners, and more.
As part of the launch, I want to tell you more about the important developer centric features we’ve created.
A new developer experience
To help you get started on your application development journey we’re thrilled to announce our new Identity Platform Developer Center. It’s a one-stop shop for everything you, as developers, need to understand about identity concepts, learn the features of Microsoft Entra External ID, and how best to use the new platform to build awesome consumer facing applications. You’ll find tons of new resources and learning materials including:
- Code Samples: How to integrate different application types with External ID.
- Tutorials: Step-by-step guides for your specific scenarios and use-cases.
- Blogs: Posts highlighting new features and releases, developer news and events as well as other interesting developer focused articles.
These new resources complement our existing content on our core technical documentation hub.
Getting started made easy
As part of the public preview there’s a new get started guide that gets you up and running with a configured application in three easy steps. This lets you configure your sign in experience, preview the end customer experience right away in your browser, and download a pre-configured sample for your preferred app type and language.

A single way to code for workforce and customer applications
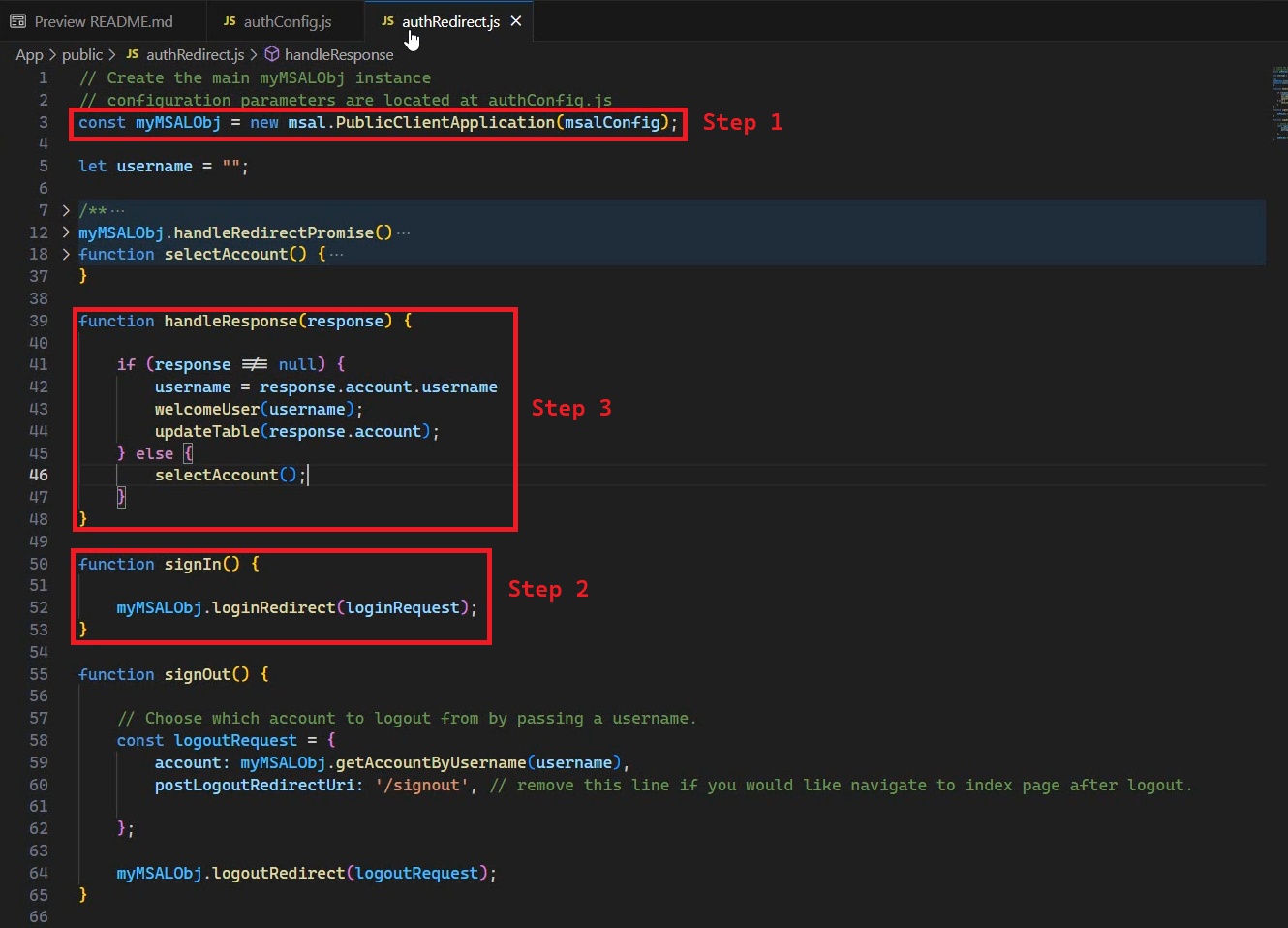
We now have a single, unified Microsoft Authentication Library (MSAL) where the same application code will work for workforce and customer scenarios. You can see how easy it is to use MSAL for consumer scenarios as seen in our updated samples, like the JavaScript sample we showed in our Build Keynote. As you can see below, you just need to do three simple steps to sign up or sign in a user:
- Configure MSAL to use to your tenant and application
- Create a sign-in function that calls MSAL to start the web based sign in flow
- Create a response handler which can extract customer information from the returned token
Signing up for Microsoft Entra External ID
To help you evaluate and adopt Microsoft Entra External ID for your applications, we’ve created two paths to join.
- Sign up for a free 30 day trial – You can try out most features for 30 days with a Microsoft account or an email address. There’s no need for a credit card or Azure subscription.
- Create an Azure free account – By creating a free Azure account, you gain access to all the Azure free account features. Azure free account requires a credit card at sign up, but you won’t be charged during public preview. Pre-existing Azure subscribers can try the preview with no change to their plan.
Ready to get started?
The Identity Platform Developer Center highlights specific solutions and answers to make troubleshooting easier for you, especially when you’re working on tight deadlines and across multiple workflows. By using these resources, you can build a high-quality customer-facing application, complete with strong authentication and identity management.
Join us at the Identity Platform Developer Center to access resources, find answers to your questions, and learn more to start building. Visit the Dev Center at aka.ms/ciam/dev to join the public preview. We love hearing feedback on how you’re using Microsoft Entra External ID or the Identity Platform Developer Center so we can make it better going forward. Give us feedback through Microsoft Entra External ID Support or by tagging @AzureAD on Twitter!

0 comments