Earlier this year we announced the sunset of the Azure AD Authentication Library (ADAL). ADAL has been officially deprecated on June 30th of this year. As part of this announcement, we heard clearly from our customers that they need help in identifying applications that still use ADAL in their tenants. Using the ADAL workbook enabled that, but required a few extra steps that we now made easier by directly integrating the functionality in the Azure Portal as well as the Microsoft Graph API.
Today we’re introducing a new way for developers and administrators to identify ADAL applications running in their tenant within web-based and local experiences that they already use – the Azure Portal and the Microsoft Graph PowerShell SDK. It’s all powered by Microsoft Entra ID Recommendations.
To get started, in the Azure Portal navigate to the Azure Active Directory blade, and in the Overview section click on Recommendations. If your tenant has active applications that are using ADAL, you will see recommendations appear within 24 hours from the last time the application acquired a token. To get details about a recommendation, along with next steps that will help you migrate to the modern Microsoft Authentication Library (MSAL)-based stack, click directly on the recommendation.
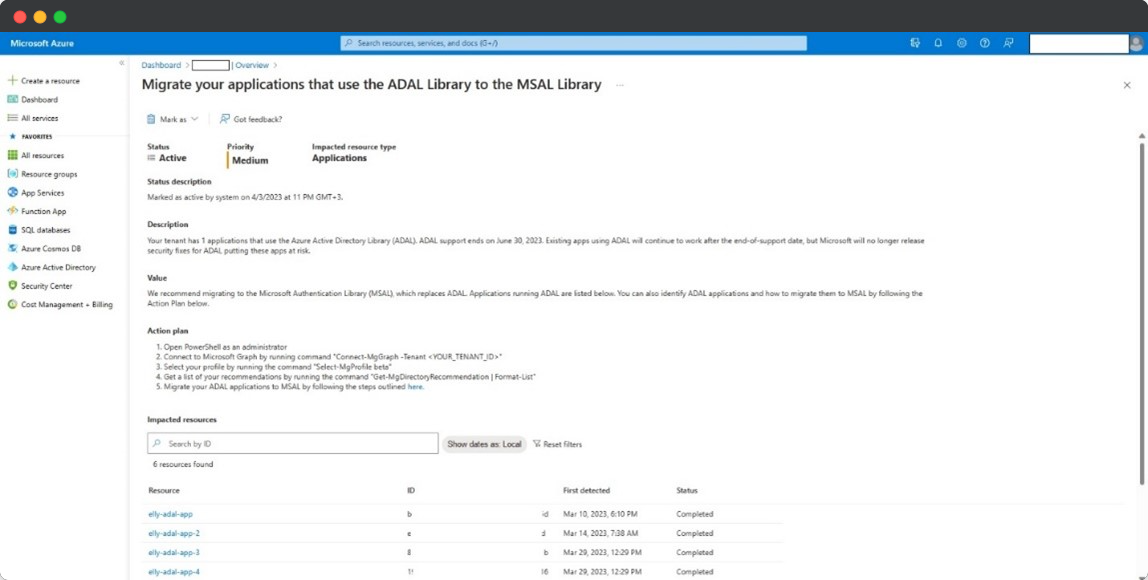
We also made sure that recommendations can be obtained programatically – whether you’re writing custom applications or monitoring scripts, you can use the Microsoft Graph PowerShell SDK to get the list of recommendations. If you want to customize your workflows even further, you can use the Microsoft Graph REST API directly by sending a GET request to:
https://graph.microsoft.com/beta/directory/recommendationsTo obtain the list of recommendations with Microsoft Graph PowerShell SDK, connect your account to the command-line interface (CLI):
Connect-MgGraph
-Scopes "DirectoryRecommendations.Read.All, DirectoryRecommendations.ReadWrite.All"
-Tenant MY_TENANT_IDNext, select the beta API profile:
Select-MgProfile betaAnd lastly, use Get-MgDirectoryRecommendation to get the list of recommendations associated with your tenant:
Get-MgDirectoryRecommendation -All | Format-ListRecommendations related to ADAL usage will contain detailed information about all ADAL applications, the first time those were detected, and instructions on how to migrate to MSAL.
We want your feedback
We’d love to hear your thoughts on the Microsoft Entra ID Recommendations experience for detecting ADAL applications! Let us know on by clicking the Got feedback? button in the Azure Portal.

With the Release of Microsoft.Graph 2.0.0 “Select-MgProfile beta” can not be used anymore
https://blog.icewolf.ch/archive/2023/07/06/microsoft-graph-powershell-module-2-0-0-GA-released/
This will work with Microsoft.Graph 2.0.0
Connect-MgGraph -Scopes “DirectoryRecommendations.Read.All, DirectoryRecommendations.ReadWrite.All”
Get-MgBetaDirectoryRecommendation -All | Format-List
Regards
Andres Bohren