A DevSecOps best practice is root cause analysis, so that we can learn from live site incidents and prevent their recurrence. Equifax made news recently with the exfiltration of data from half the US population. This is a sobering opportunity to look at the root cause.
The Equifax attack used Apache Struts, a popular open source project for web apps. Unfortunately, the deployed version had a known vulnerability, Apache Struts CVE-2017-5638, that was known months before the attack. This was easy for bad actors to find. More importantly, Struts had a clear fix available. The fix could have been implemented to prevent the attack. Why wasn’t the current version in place?
Equifax is not an isolated case
Open Source Software (OSS) is simply a fact in organizations of every size, across all verticals. This is not a passing trend. Open source usage will continue to grow. OSS helps companies accelerate development by freeing developers to reuse common components and focus on competitive differentiation.
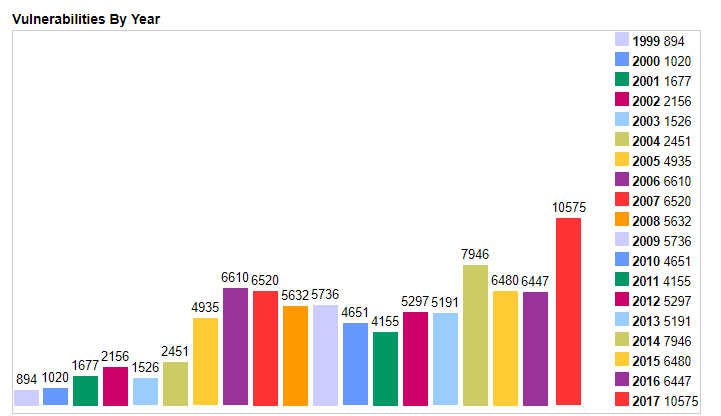 Source: https://www.cvedetails.com/browse-by-date.php
Source: https://www.cvedetails.com/browse-by-date.php
Every year, as more OSS is used, more vulnerabilities are found. The analysis from the National Vulnerability Database above makes the point, even though the NVD vastly underreports OSS projects. And worse still, the most vulnerabilities are in executable components. Exactly like the one that Equifax used.
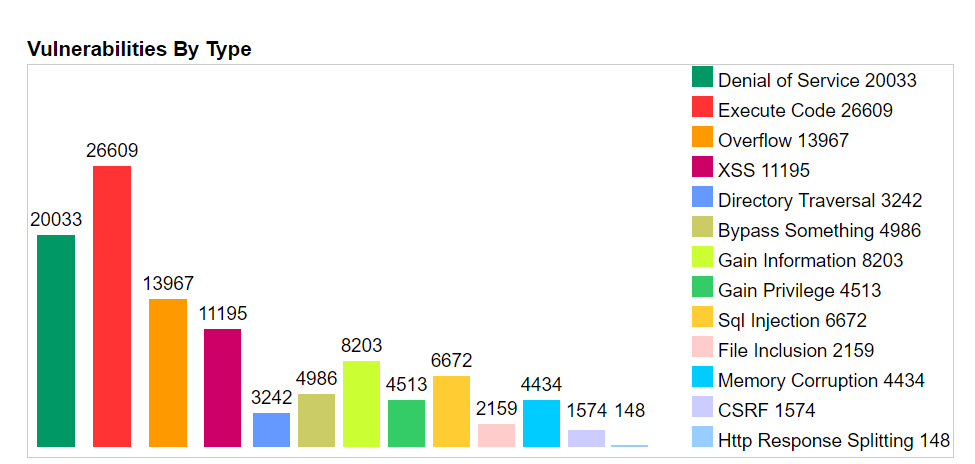 Source: https://www.cvedetails.com/vulnerabilities-by-types.php
Source: https://www.cvedetails.com/vulnerabilities-by-types.php
OSS vulnerabilities are the norm
Microsoft’s partner, WhiteSource Software, recently analyzed which popular open source projects are the most vulnerable, The WhiteSource database covers 3M OSS components with 70M source files across 20 programming languages. WhiteSource further analyzed 38,333 products that customers manage with its software. Unfortunately, 24,083 of them (62.8%) contain security vulnerabilities, for which most (87%) have known fixes.
Interestingly, Apache Struts2-Core was found to be the OSS component with the second highest level of vulnerability.
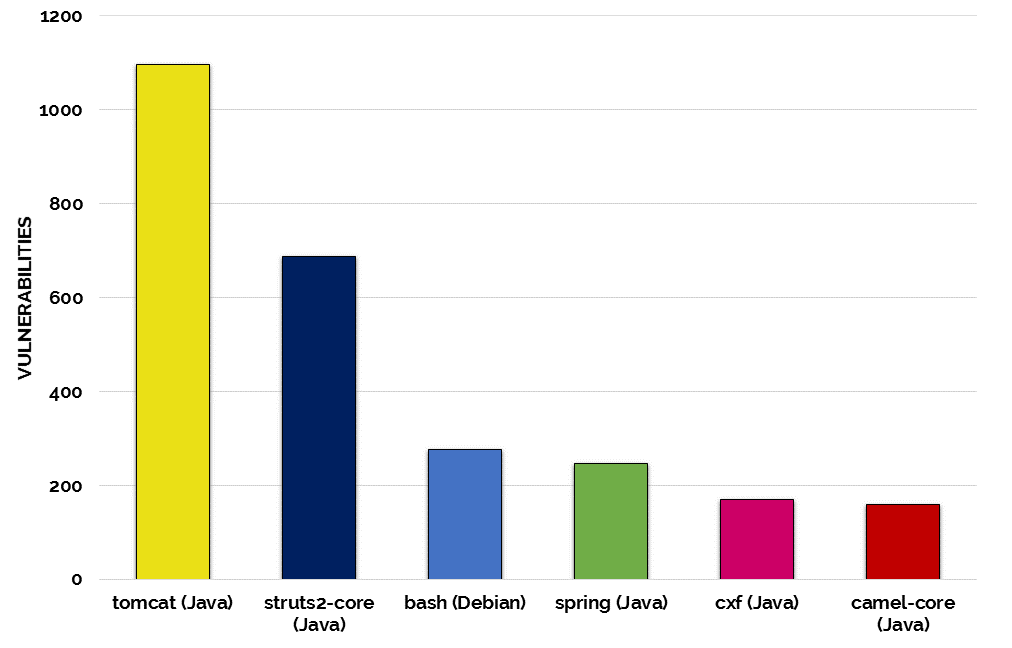 Source: WhiteSource Database
Source: WhiteSource Database
Don’t be the next victim
The DevSecOps best practice is to shift security left and continuously scan for vulnerabilities. WhiteSource has an extension for VSTS that allows you to see with every build what your vulnerabilities are. And if you are using WhiteSource, you will be notified when new vulnerabilities are discovered in the wild.
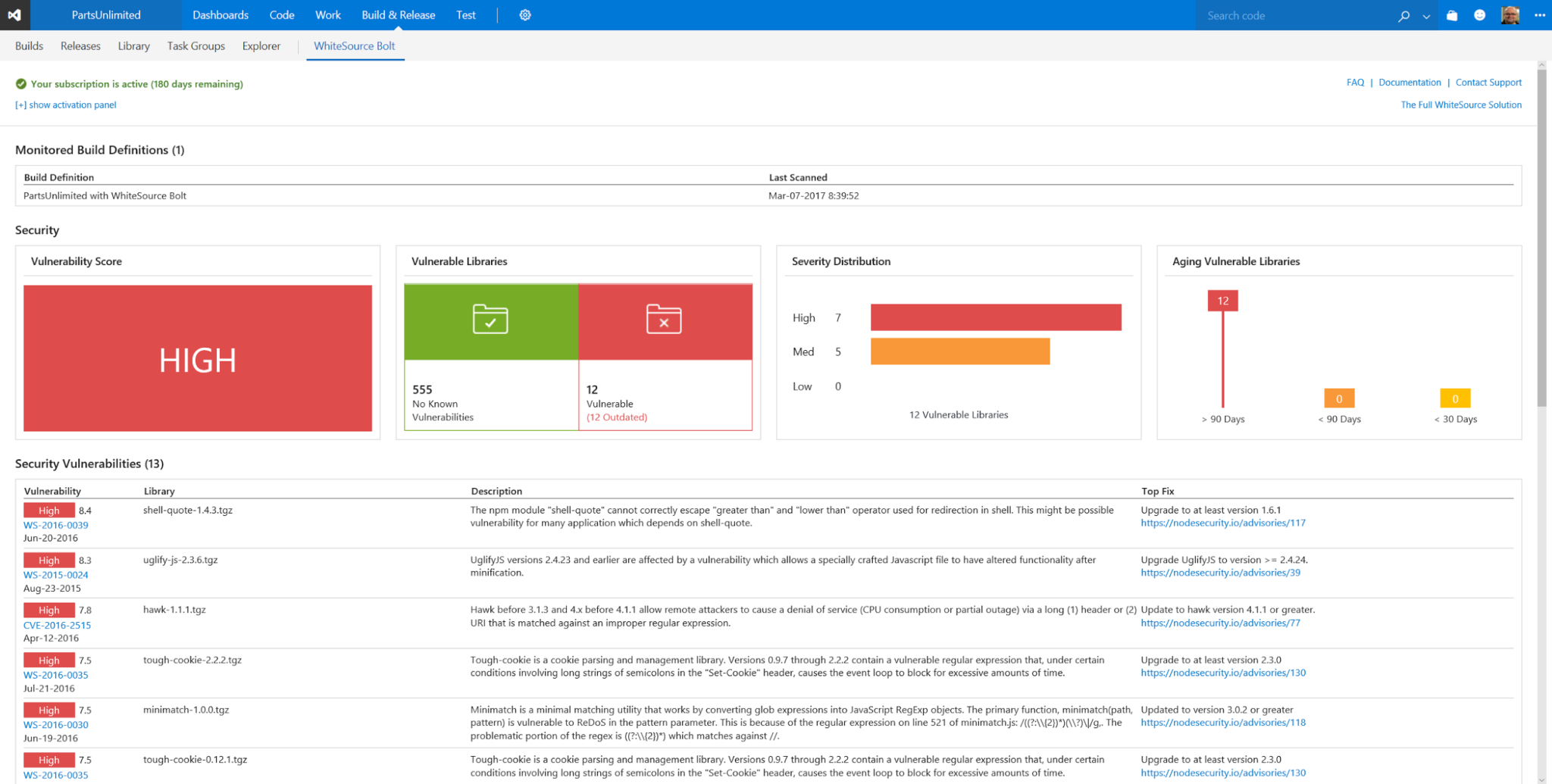 Example of WhiteSource Bolt scanning a build in the release pipeline
Example of WhiteSource Bolt scanning a build in the release pipeline
If you are using OSS and you don’t yet know where your vulnerabilities are, try WhiteSource in your pipeline.
- Click here to learn more on WhiteSource software.
- Click here to learn more about WhiteSource Bolt, the VSTS extension that helps you manage open source from within VSTS / TFS
- Click here to learn more about WhiteSource on Azure

0 comments