Do you want to stop storing secrets and certificates in Azure service connections? Are you tired rotating these secrets whenever they expire? We are now announcing a public preview of workload identity federation for Azure service connections. Workload identity federation uses an industry-standard technology, Open ID Connect (OIDC), to simplify the authentication between Azure Pipelines and Azure. Instead of secrets, a federation subject is used to facilitate this authentication.
How it works
As part of this feature, the Azure (ARM) service connection has been updated with an additional scheme to support workload identity federation. This allows Pipeline tasks that use the Azure service connection to authenticate using a federation subject (sc://<org>/<project>/<service connection name>). The main benefits of using this scheme over existing authentication schemes are as follows:
- Simplified management: You do not need to generate, copy, and store secrets from service principals in Azure Entra ID to Azure DevOps anymore. Secrets that are used in other authentication schemes of Azure service connections (e.g., service principal) expire after a certain period (2 years currently). When they expire, pipelines fail. You have to generate a new secret and update the service connection. Switching to workload identity federation eliminates the need to manage these secrets and improves the overall experience of creating and managing service connections.
- Improved security: With workload identity federation, the federation subject (
sc://<org>/<project>/<service connection name>) uniquely identifies what the identity can be used for, which provides a better constraint than a (shared) secret. There is no persistent secret involved in the communication between Azure Pipelines and Azure. As a result, tasks running in pipeline jobs cannot leak or exfiltrate secrets that have access to your production environments. This has often been a concern for our customers.
How can I use it?
You can take advantage of workload identity federation in two ways:
- Convert your existing Azure service connections based on secrets to the new scheme. You can perform this conversion one connection at a time. Best of all, you do not have to modify any of the pipelines that use those service connections. They will automatically leverage the new scheme once you complete the conversion.
- Use the new workload identity federation scheme whenever you create a new Azure service connection. Moving forward, this will be the recommended method.
Converting an existing Azure service connection
To convert a previously created Azure service connection, select the “Convert” action after selecting the connection:
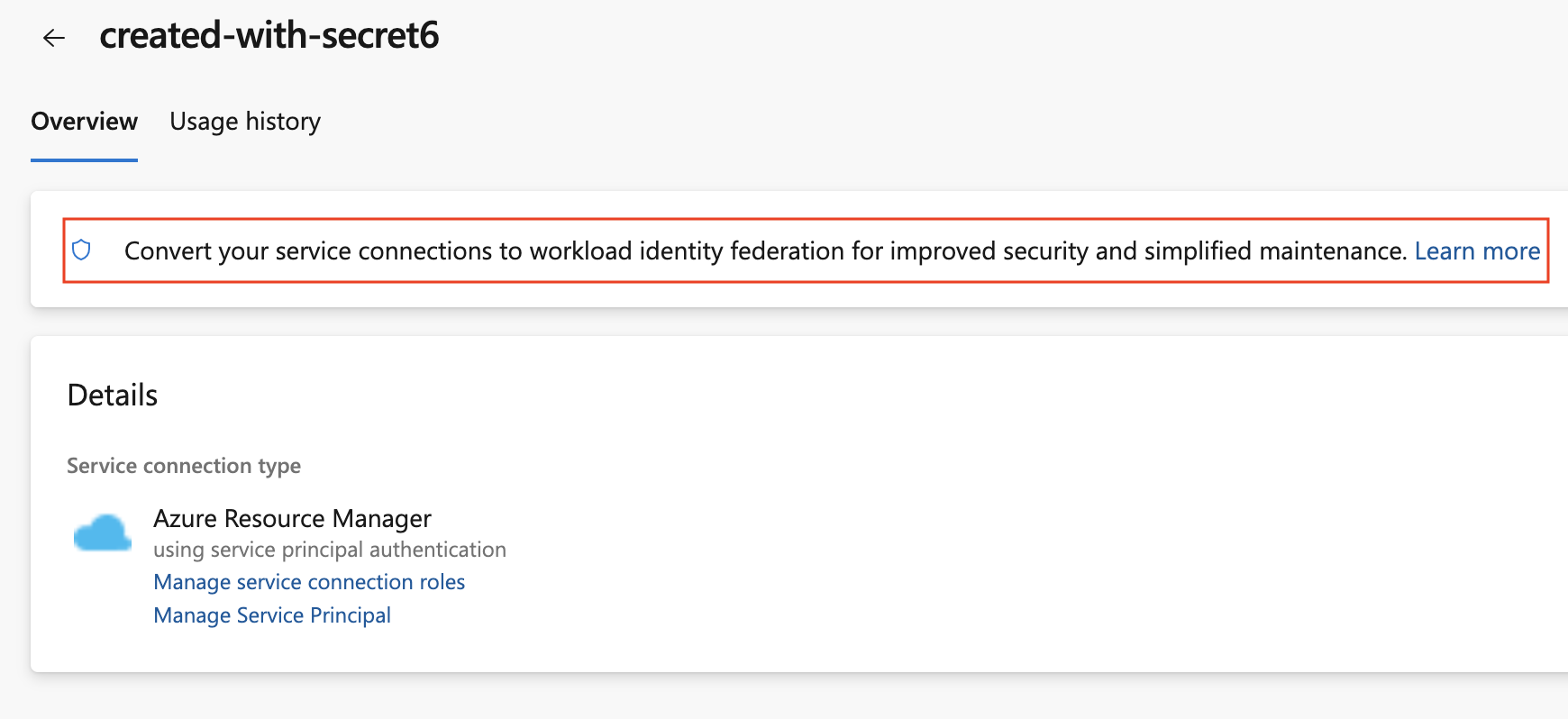
You can roll back from a conversion to use a secret by clicking the revert link on the service connection details page:
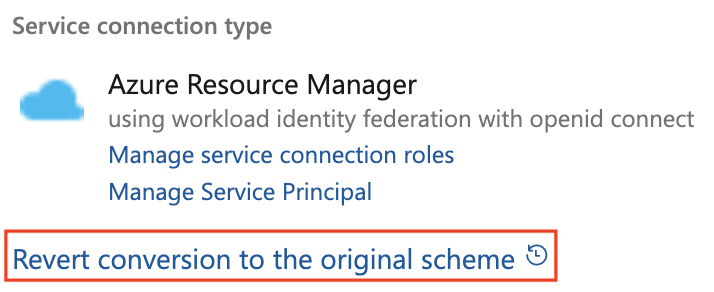
Create a new Azure service connection
To create a new Azure service connection using workload identity federation, simply select Workload identity federation (automatic) in the Azure service connection creation experience:


Create manually with a Managed Identity or Service Principal
You can also create an Azure service connection using workload identity federation manually with either a Service Principal or Managed Identity. Developers that do not have permission to create App Registrations in Azure Entra ID (AAD) can create Azure service connections with Workload identity federation by configuring the federation on a Managed Identity instead of a Service Principal. Using a Managed Identity in federation does not require assignment and works across all agent hosting models (Hosted, Self-hosted, Scale set agents). See manual configuration instructions for a step by step guide.
Built-in Pipeline tasks
Azure Pipelines built-in tasks that target Azure have been updated to take advantage of workload identity federation. This is the complete list: AzureAppServiceManage, AzureAppServiceSettings, AzureCLI, AzureCloudPowerShellDeployment, AzureContainerApps, AzureFunctionAppContainer, AzureFunctionApp, AzureKeyVault, AzureMonitor, AzureMysqlDeployment, AzurePolicy, AzurePowerShell, AzureResourceGroupDeployment, AzureResourceManagerTemplateDeployment, AzureRmWebAppDeployment, AzureSpringCloud, AzureVmssDeployment, AzureWebAppContainer, AzureWebApp, DockerCompose, Docker, HelmDeploy, InvokeRestApi, JavaToolInstaller, JenkinsDownloadArtifacts, Kubernetes.
Azure CLI task support for inline authentication
If a tool does not have a task or you prefer to use tools directly inside a script you provide, you can use the AzureCLI@2 task task to access the federated token used during authentication. Setting property addSpnToEnvironment: true will populate the idToken, servicePrincipalId and tenantId environment variables.
This example shows inline configuration of Terraform azuread/azurerm providers:
- task: AzureCLI@2
inputs:
addSpnToEnvironment: true
azureSubscription: 'my-azure-service-connection'
scriptType: bash
scriptLocation: inlineScript
inlineScript: |
# Inherit Azure CLI service connection
export ARM_CLIENT_ID=$servicePrincipalId
export ARM_OIDC_TOKEN=$idToken
export ARM_TENANT_ID=$tenantId
export ARM_SUBSCRIPTION_ID=$(az account show --query id -o tsv)
export ARM_USE_OIDC=true
terraform init
terraform apply -auto-approve
The idToken has a lifetime of 10 minutes.
Custom Azure tasks and extensions
If you are using a task from the Marketplace or a home-grown custom task to deploy to Azure, then it may not support workload identity federation yet. In these cases, we ask task developers to support workload identity federation to improve security.
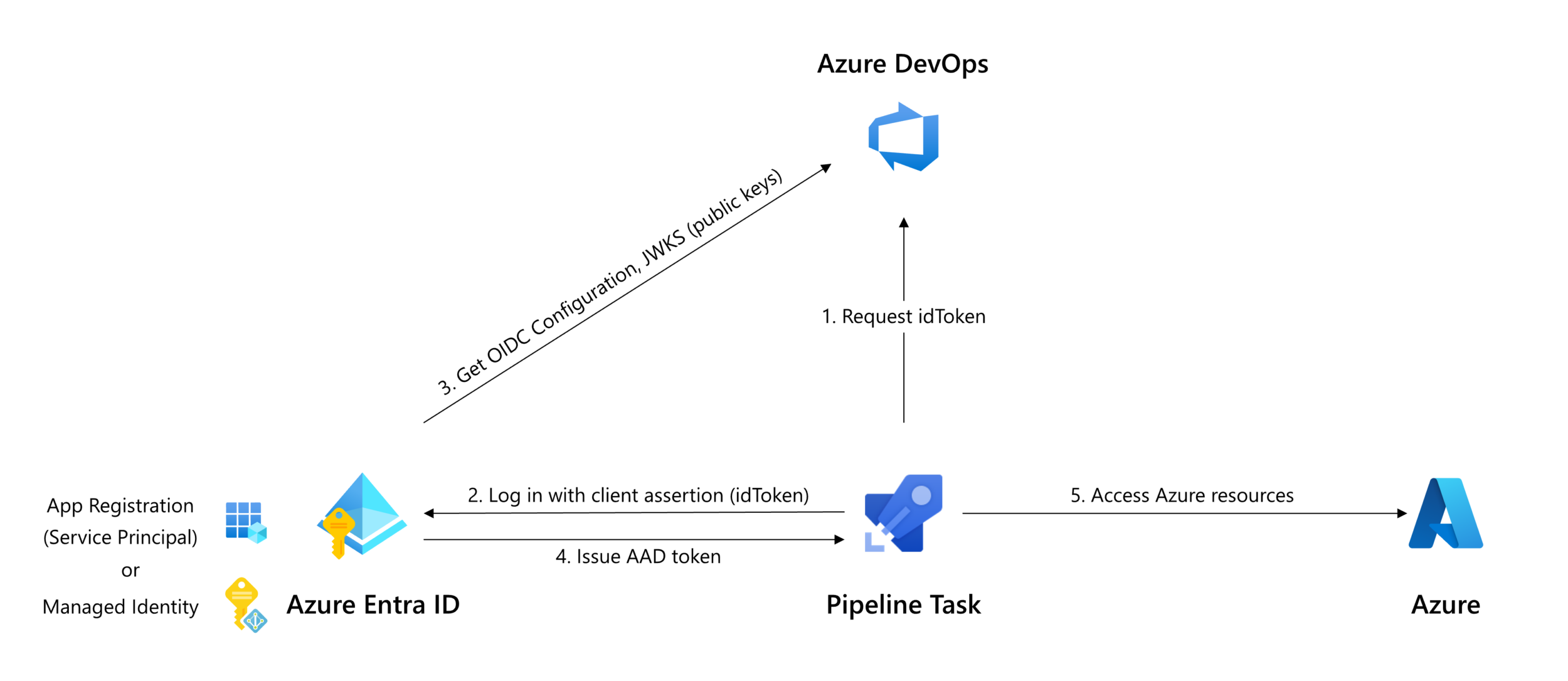
Tasks that take a connectedService:AzureRM input in task.json can be updated so support workload identity federation with the following steps:
- Request an idToken using the new Oidctoken REST API (arrow 1 in above diagram).
- Exchange the idToken for an access token using the federated credential flow of the OAuth API, specifying the idToken as
client_assertion(arrows 2 & 4 in above diagram);
or: - For tasks that act as a wrapper around a tool that performs authentication itself, use the tools’ authentication method to specify the federated token.
You can also publish extensions to the Marketplace with Workload identity federation. This blog post explains how.
Terraform tasks
The Terraform DevLabs and Azure Pipelines Terraform Tasks extensions have been updated to support workload identity federation. The Terraform DevLabs extension uses the azure-pipelines-tasks-artifacts-common npm package to get the idToken, see code example.
If you are a Terraform user, you should review this great walkthrough on the Tech Community that uses the Azure-Samples/azure-devops-terraform-oidc-ci-cd repository to create and use Azure service connections with Terraform.
Public preview
The feature will roll out over the next few weeks. For this preview, we support workload identity federation only for Azure service connections. This scheme does not work with any other types of service connections. See our docs for more details.


We have a pipeline that uses a service principal with access to multiple subscriptions. We’re trying to migrate this service principal to Workload Identity Federation (WIF) and have created a new WIF service connection for this purpose. However, when the pipeline is executed, it throws a subscription access issue. We’re looking for a solution to ensure that WIF has access to multiple subscriptions, similar to a service principal.
Do we have the Azure powershell task to support inline authentication for workload identity federation?
Hi Selva. No, the AzureCLI task supports inline authentication (through addSpnToEnvironment: true).
Hello Eric, thank you for the great post about this feature. Are there any plans to implement Workload Identity for Azure Devops Environment? It seems the Kubernetes environment there still only supports service connections via service accounts. We do use it for AKS deployments. Thanks! 🙂
This is a great feature. Can it be used to deploy to Service Fabric clusters, or are they not yet supported?
Above its mentioned that “Developers that do not have permission to create App Registrations in Azure Entra ID (AAD) can create Azure service connections with Workload identity federation by configuring the federation on a Managed Identity” . This requires some guardrail in production environent to control who can create a managed identity , is there any guardrail available on Azure to control this or a clarity of what roles and permissions is needed for creating a managed identity on Azure.
Hi Anil, this doc describes how to configure Managed Identity for federation. You will have to create the Managed Identity yourself, we will not create it for you. You can create an Azure policy that governs the creation of federations on Managed Identity, see doc.
Hi Eric,
Regarding the token expiry and the statement of the idToken having a lifetime of 10 minutes. Is the expiry period configurable or is it a fixed expiry period?
Alternatively, is the expiry period of the token used by the Azure Devops tasks greater than 10 minutes?
Our Azure DevOps pipelines execute terraform and some deployment of Azure resources can be in excess of an hour. Wondering if this is suitable for such deployments.
Thanks
Mark
Hi Mark, the idToken is valid for 10 minutes. Azure Pipelines tasks exchange the idToken for an AAD bearer token at the start of executing the task. In the case of Terraform, the tool the task is encapsulating will do so. Running Terraform apply for longer than 10 minutes is not an issue as the AAD bearer token has a longer lifetime.
Thanks, Eric
Hi. I’ve got some issue regarding this oidc token. When I use variable group linked to Key Vault and try to re-run failed job I see this error:
[error]Unhandled: Cannot read properties of null (reading ‘oidcToken’)
[error]TypeError: Cannot read properties of null (reading ‘oidcToken’)
Hi Ihar. In what type of job is this happening? e.g. agentless, deployment group, etc.
Deployment job (runOnce strategy). Key Vault secrets are embedded by using variable group in yaml file
Can you create an issue on the Developer Community and tag me?
https://developercommunity.visualstudio.com/t/Service-Connection-with-WI-federation-is/10516076
This does not work with task AzureFileCopy@5. Is there a timeline on when this will be available, or a workaround we can use in the mean time?
We will update AzureFileCopy@5 as soon as AzCopy supports Workload identity federation. This issue tracks that work.
UPDATE: The AzureFileCopy@6 task supports Workload identity federation.
This is great. I've used it to convert some of our existing Azure Resource Manager service connections that were using the Service Principal Authentication. Oddly though the "Convert" button does not show up on all of the Azure Resource Manager service connections. Even within the same team project, some service connections have the Convert button, while others don't. As far as I can tell there is nothing different about the service connections besides the Azure resource that they connect to. The
Hi Daniel. Convert works only for App registrations that can be modified by the user editing the Service Connection, typically the creator of the Service Connection.