Building and monitoring Zero Trust (TIC 3.0) workloads for federal information systems with Microsoft Sentinel
This blog is co-authored by Lili Davoudian, Program Manager II; and TJ Banasik, CISSP-ISSEP, ISSAP, ISSMP, Senior Program Manager of Microsoft Cloud & AI Security.
In this video, we discuss the new Microsoft Sentinel: Zero Trust (TIC3.0) solution which provides additional functionality to empower US government customers as they incorporate a Zero Trust perspective into their architecture.
In addition to design improvements, we’ve improved the better-together integration with Microsoft Defender for Cloud for assessments and alerting rules to actively monitor and alert on compliance posture deviations across each TIC 3.0 control family.
The solution includes the new Zero Trust (TIC 3.0) Workbook, (11) Analytics Rules, and (1) Playbook; enabling governance and compliance teams to design, build, monitor, and respond to Zero Trust (TIC 3.0) requirements.
We appreciate all the positive feedback and input from the government community which resulted in these updates to our workbook. Watch our demo to learn more.
Getting started
In addition to the video, we’re sharing content designed to provide the foundation for designing, building, and monitoring workload compliance within Zero Trust and TIC 3.0 requirements. Here are the steps to onboard required dependencies, enable connectors, review content, and provide feedback.
1. Onboard: Microsoft Sentinel and Microsoft Defender for Cloud
2. Add the Azure Security Benchmark and NIST SP 800-53 R5 Assessments to your dashboard
3. Continuously export Security Center Data to Log Analytics Workspace
4. Deploy the Microsoft Sentinel Zero Trust (TIC3.0) solution
- Microsoft Sentinel > Content Hub > Select Zero Trust (TIC3.0) Solution > Configure deployment options > Create
- Government: Access Solution on Microsoft Sentinel’s GitHub Repo. Select Deploy to Azure Government Button > Configure Options > Create
5. Review the Zero Trust (TIC 3.0) Workbook
- Microsoft Sentinel > Workbooks > Select Zero Trust (TIC 3.0)
6. Review/Enable Zero Trust (TIC 3.0) Analytics Rules
- Microsoft Sentinel > Analytics > Search Zero Trust (TIC 3.0)
7. Review Playbook Automation
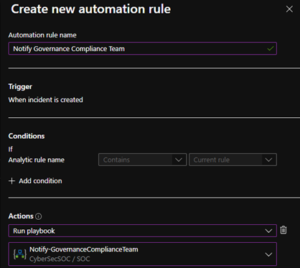
- Microsoft Sentinel > Automation > Active playbooks > Search Notify-GovernanceComplianceTeam > Enable
- Create Automation Rule
-
- Analytics > Search Zero Trust > Edit > Automated Response > Add new > Select Actions: Run Playbook > Select Notify-GovernanceComplianceTeam and configure automation options > Review > Save > Mirror configuration across all Zero Trust (TIC3.0) analytics rules.
8. Review the content and provide feedback through the survey
Learn more about Zero Trust (TIC 3.0) with Microsoft Security


 Light
Light Dark
Dark
0 comments