This is a guest post by Brian C. Reed, NowSecure Chief Mobility Officer
In the race to get innovative new mobile apps or cool new features added to existing mobile apps out the door faster, secure coding practices in mobile app development aren’t always at the top of every developer’s list. In fact, our NowSecure benchmarks show that some 85 percent of iOS and Android apps in the Apple App Store and Google Play have 1 or more security issues and bugs (i.e. security vulnerabilities). Wow, that’s pretty rough security stat to say the least!
Our team at Now Secure has experience testing over a million apps over the last decade, which gives us a unique perspective on the good, the bad and the ugly when it comes to secure mobile app development and security testing. In this post we discuss the most frequent mobile app coding mistakes on iOS and Android that lead to security issues so you can build more secure apps faster with fewer security bug showstoppers.
Inside The Mobile Attack Surface
So we can better understand how to build secure code that will stop an attacker, let’s start with a quick view into the mobile attack surface from the point of view of an attacker. The mobile attack surface can be broken down into four areas: data at rest on the device, data in motion transmitted between the mobile app on device and backend, functionality within the mobile app code itself, and the backend APIs and endpoints the mobile app communicates with. As shown in the figure below, many of the same exploitable security issues or vulnerabilities exist in both web and mobile apps such as buffer overflows, cross-site scripting (XSS), and SQL injection (SQLi). But iOS and Android present a number of new vectors like dynamic runtime injection, intent hijacking, and a plethora of gaps that can lead to man-in-the-middle attacks.
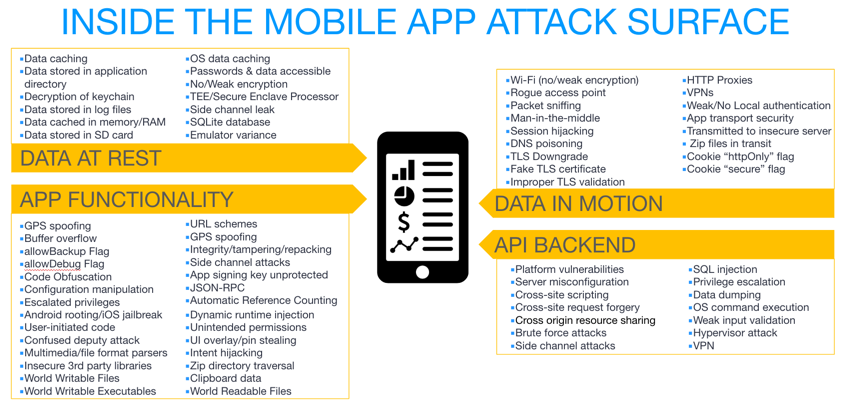
While developers are not expected to be advanced security gurus with deep understanding of all these attacks, these four areas provide a framework for developers and security pro’s to align and focus their efforts on delivering secure mobile apps.
Let’s look at the top 5 mobile app security failures based on years of mobile app security testing and what to do about them. As the chart shows below, the top 5 security failures span:
- data at rest with insecure data storage
- data in motion with insecure communication
- app and backend functionality with insecure extraneous functionality
- app functionality with insecure client code quality
- lack of obfuscation which exposes mobile apps to reverse engineering and attacks
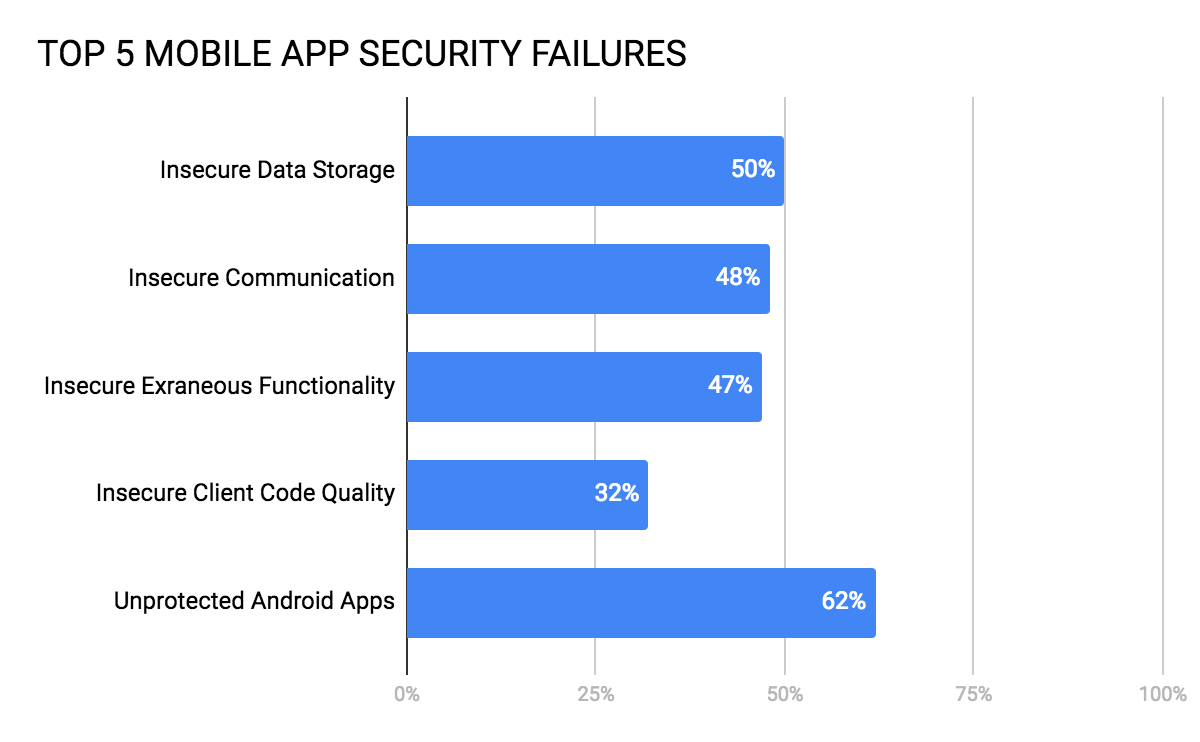 Source: NowSecure Mobile App Security Benchmarks Q1, 2018
Source: NowSecure Mobile App Security Benchmarks Q1, 2018
The Top 5 Mobile App Security Failures
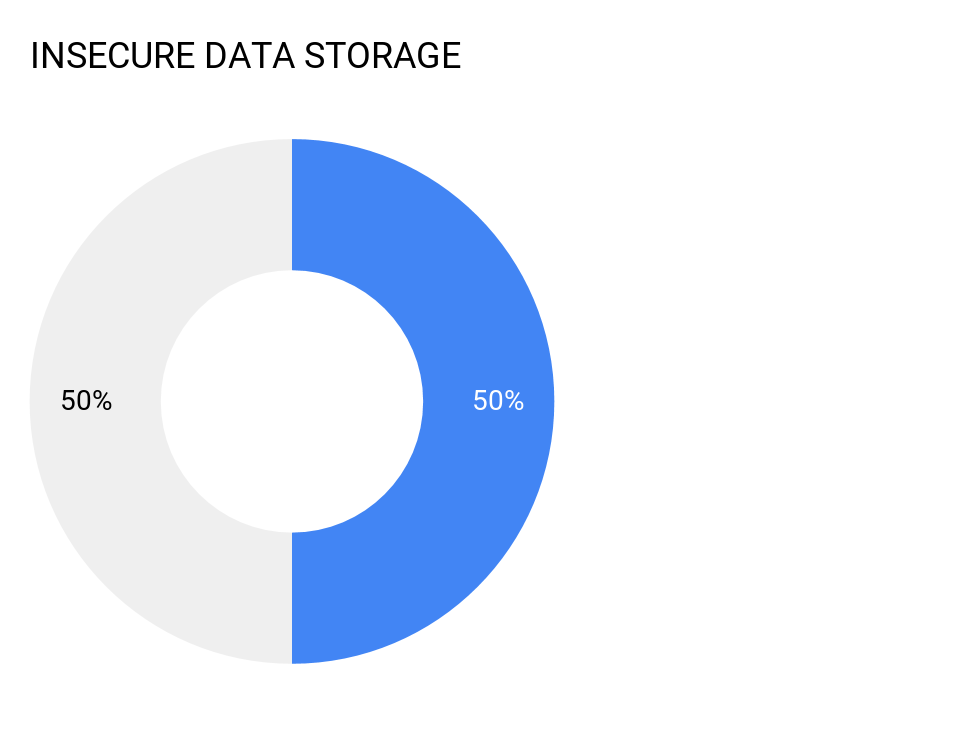
1. Insecure Data Storage
50 percent of all mobile apps tested exhibit “Insecure Data Storage” issues leaving data exposed that could be exploited by an attacker and/or violate industry compliance regulations.
|
 |
PREVENTION: Developers need to ensure all data is securely stored at all times on the device and ensure they do not write any sensitive data to local files and system logs. Security pro’s or outsourced security pen testing services need to test thoroughly for any unencrypted data leakage on device.
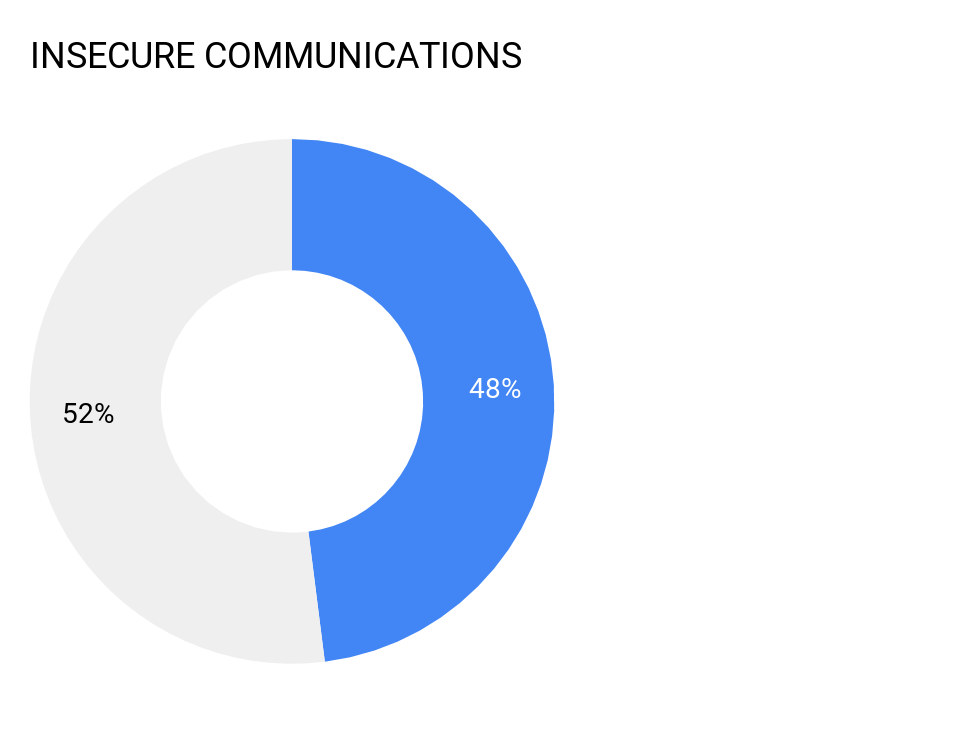
2. Insecure Communications
48 percent of all mobile apps tested exhibit “Insecure Communication” issues which leaves those mobile apps susceptible to man-in-the-middle (MITM) attacks that do not require hands on device to exploit.
|
 |
PREVENTION: Developers need to ensure all data is properly encrypted in transit at all times including proper use of certificates, and this includes 3rd party and OSS libraries that must encrypt all traffic as well. Security pro’s or outsourced security pen testing services need to test for any unencrypted data leakage on device via tests for proper use of SSL, cert pinning and look for sensitive data in transit.
3. Insecure Extraneous Functionality
47 percent of all mobile apps tested reveal “Extraneous Functionality” issues. In many instances these issues can be difficult to identify without deep security testing.
|
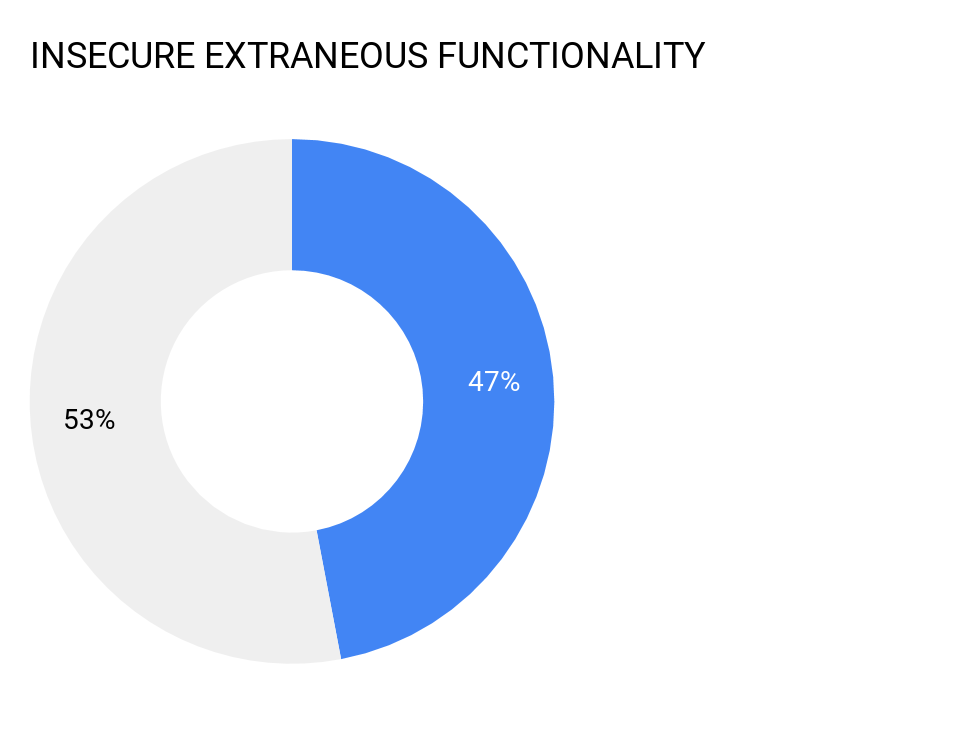 |
PREVENTION: Developers need to ensure proper secure coding hygiene and add code review process to ensure extraneous information is not left in code or comments. Security pro’s or outsourced security pen testing services need to probe and try to exploit extraneous functionality to identify and address any issues.
4. Insecure Client Code Quality
32 percent of all mobile apps tested exhibit “Client Code Quality” issues specifically the code running on the device side (not backend code). In many instances these issues can be difficult to identify without deep security testing.
|
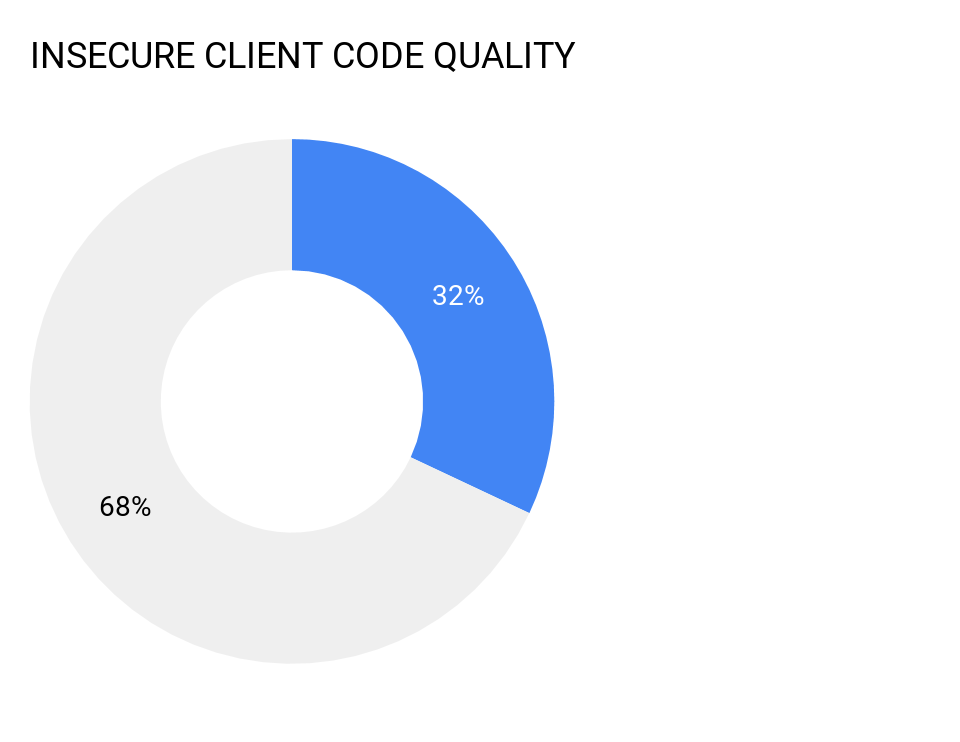 |
PREVENTION: Developers need to ensure proper use of mobile APIs and secure coding practices, especially on Android. Security pro’s or outsourced security pen testing services need to ensure mobile apps are security tested on real devices in the real world to ensure full client-side mobile app security.
5. Unprotected Android Apps
62 percent of Android apps are not properly obfuscated leaving them exposed to reverse engineering from attackers. While this is not a security bug per-se, if the responsibility of the team is to deliver secure mobile apps then obfuscation should be included.
|
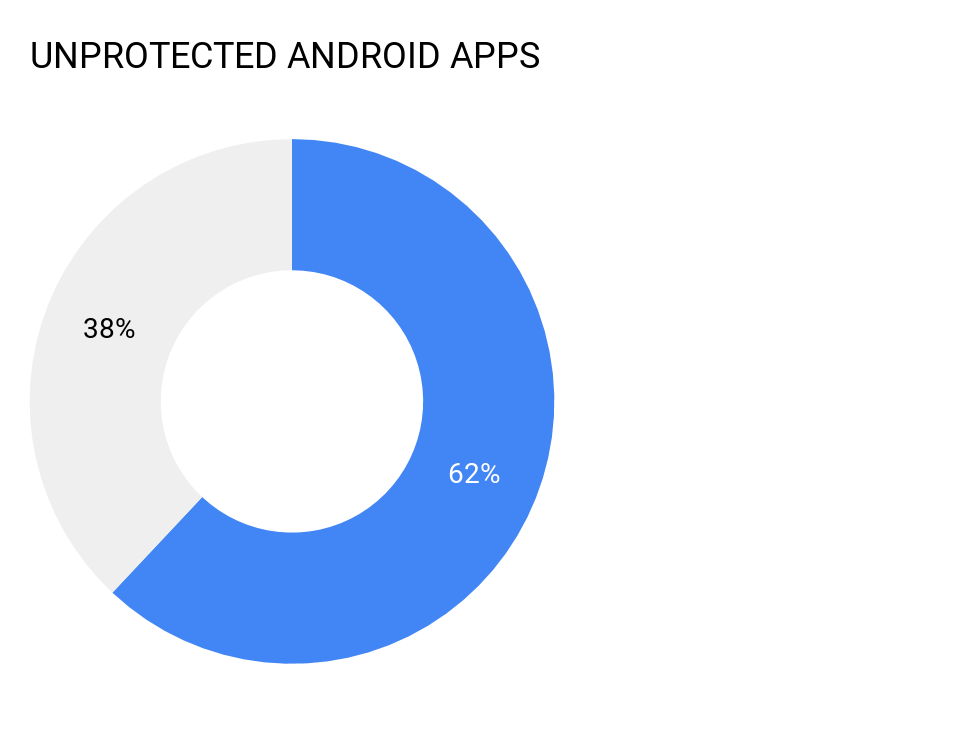 |
PREVENTION: Android developers should leverage 3rd party obfuscation tools such as the free ProGuard and even with built-in DRM process for AppStore publishing, iOS developers might consider additional protections as well. Security pro’s or outsourced pen testing services need to test for reversing to ensure proper obfuscation is in place such as using free reversing tool like APKTool or more advanced integrated testing tools.
Conclusion
All developers must take into consideration functionality, user experience and security when they build and update their mobile apps. These issues are not insurmountable and can be addressed by increasing a focus on secure mobile development best practices with developer training resources, improved security hygiene and the addition of automated security testing approach into the dev pipeline to establish a strong security baseline.
For a deeper guide with over 100 pages of API and code examples in 50+ best practices, see the free download Secure Mobile Development Best Practices Handbook from NowSecure.
Create an account on App Center today to get started.

0 comments