Summary: Guest Blogger, Jason Hofferle, continues his series about PowerShell Remoting.
Microsoft Scripting Guy, Ed Wilson, is here. This week I am in Seattle, Washington speaking at Microsoft TechReady 15. Therefore, we have a series written by guest blogger, Jason Hofferle, about PowerShell Remoting. Here is a little bit about Jason:
Jason Hofferle has been an IT professional since 1997. His experience includes enterprise desktop engineering for a Fortune 500 financial institution and Active Directory design for local governments and law enforcement. Jason currently works for the Defense Contract Management Agency, where he implements new technology such as virtual desktop infrastructure. He recently has been speaking about Windows PowerShell at SQL Saturday and IT Pro Camp events in Florida, and he frequently attends the Tampa PowerShell User Group.
Blog: Force Multiplication through IT Automation
Twitter: @jhofferle
In the first blog post of this series, An Introduction to PowerShell Remoting: Part One, I took a look at what PowerShell Remoting is and how it takes advantage of the Web Services for Management (WSMan) framework to provide a uniform way to manage remote computers. Maybe after seeing some of the possible performance benefits, you’ve decided to at least take a closer look at what’s required to get it up and running in your environment. In this post I’m going to discuss the requirements and configuration.
PowerShell Remoting requires that Windows PowerShell 2.0 is installed on all computers that are being remotely managed or being used to connect to those remote systems. Windows 7 and Windows Server 2008 R2 include Windows PowerShell 2.0 with the operating system. For older operating systems, the Windows Management Framework Core can be downloaded and installed on Windows Vista, Windows XP, Windows Server 2008, and Windows Server 2003. The framework includes WinRM 2.0 and Windows PowerShell 2.0, and it requires the Common Language Runtime (CLR) 2.0, which is included with the Microsoft .NET Framework 2.0 or later.
Even on operating systems that include the necessary components, PowerShell Remoting is disabled by default, so it needs some configuration before it can be utilized. The WinRM service needs to be running, and a listener has to be configured, which tells the computer to listen for incoming connections. Also, the Windows firewall needs to be configured with rules to allow incoming connections.
PowerShell Remoting is incredibly simple to configure in a domain environment by using Group Policy. On a server operating system, the Windows Remote Management service is set to start automatically, but on a client operating system, this needs to be configured. Setting services to start automatically can be done at Computer Configuration\Windows Settings\Security Settings\System Services.
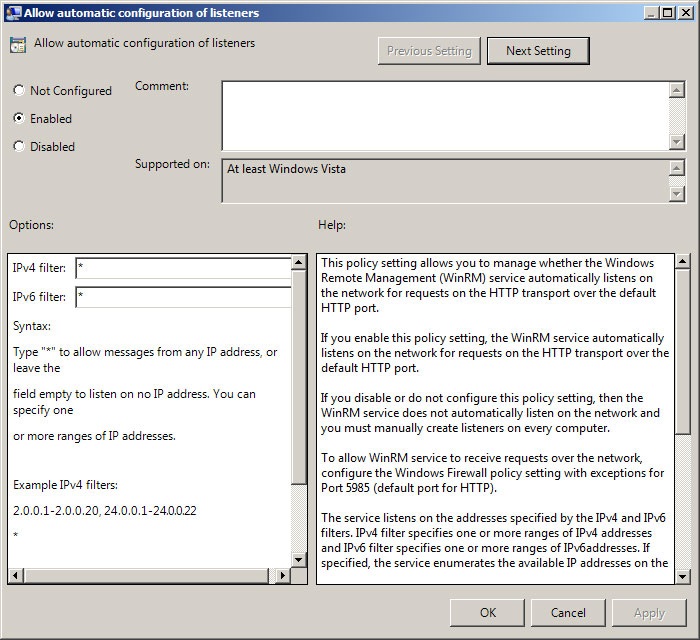
To setup the listener, the Enable Automatic Configuration of Listeners setting can be configured at Computer Configuration\Administrative Templates\Windows Components\Windows Remote Management (WinRM)\WinRM Service. An IP can be specified for systems that have multiple IP addresses assigned, or asterisks can be used to listen to all addresses.
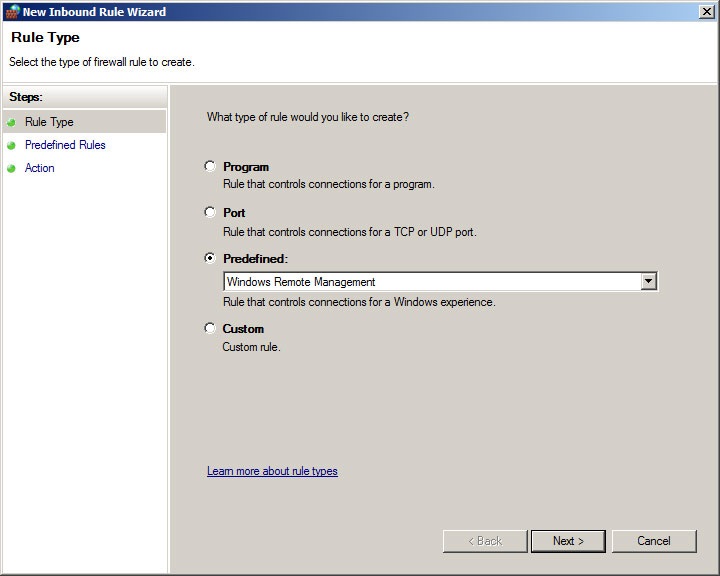
The firewall exception can be added at Computer Configuration\Administrative Templates\Network\Network Connections\Windows Firewall\Domain Profile. If there are no Windows XP or Windows Server 2003 systems that need to be configured, the firewall exceptions can also be configured through Computer Configuration\Windows Settings\Security Settings\Windows Firewall with Advanced Security\Inbound Rules by using a predefined rule for Windows Remote Management.
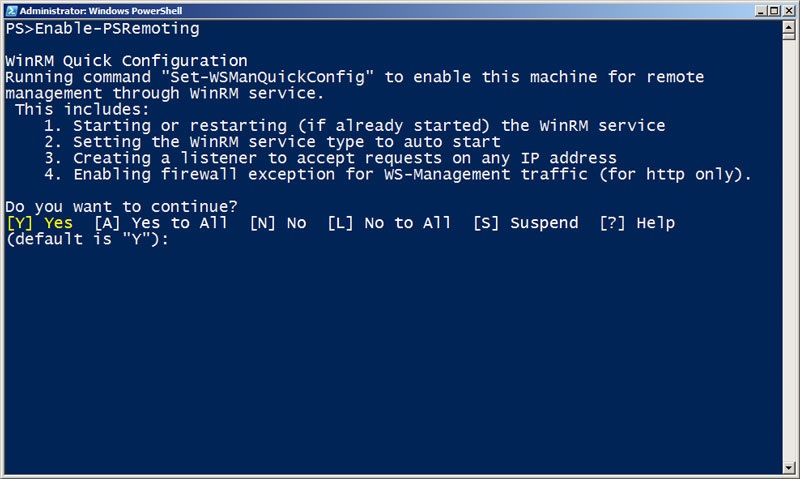
If Group Policy isn’t an option, or PowerShell Remoting needs to be configured on an individual basis, the Enable-PSRemoting cmdlet can be used to perform the tasks of enabling the WinRM service, configuring the listener, and putting firewall rules into place.
PowerShell Remoting is pretty straightforward to configure when all the computers are joined to the same Active Directory domain and running on the same network. Going beyond the internal corporate network scenario requires some additional configuration depending on the particular situation.
One of the first issues commonly experienced is the concept of trusted hosts. When I’m connecting to a remote computer, I want to verify that computer’s identity before passing it my user credentials. When using Kerberos authentication in a domain, Windows PowerShell knows that it can trust the other computer because the domain controller is capable of verifying that system’s identity. When not in a domain environment, Windows PowerShell has no way of knowing if the system you’re trying to connect to is a malicious system spoofing as a legitimate computer.
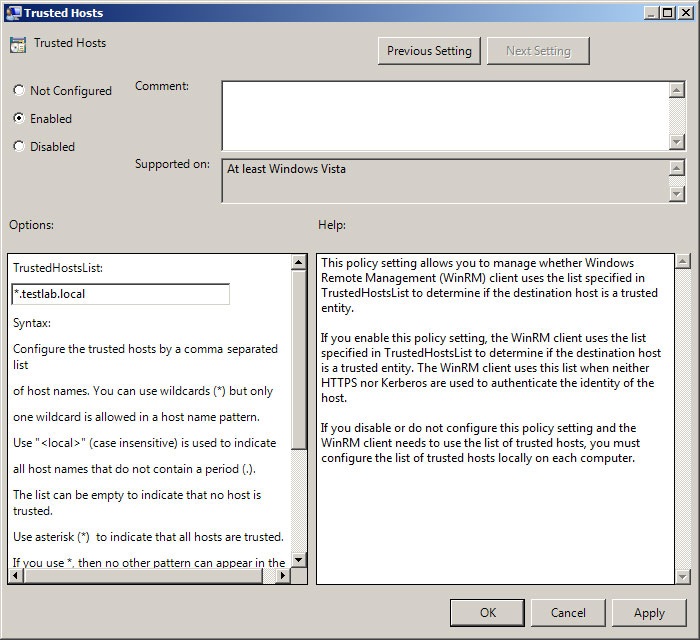
So I either need a way to verify that computer’s identity, or bypass the security precaution. By having a certificate installed on the computers from a trusted certification authority (CA), that certificate can be used to verify the system’s identity. The alternative is to modify the trusted hosts section of the WinRM configuration to say, “I know the identity of this system cannot be verified, but let me connect anyway.” Even in a domain environment, trusted hosts may need to be configured if using IP addresses to specify computers. Kerberos protocol will only work with computer names, so Windows PowerShell will default to NTLM authentication any time an IP address is used.
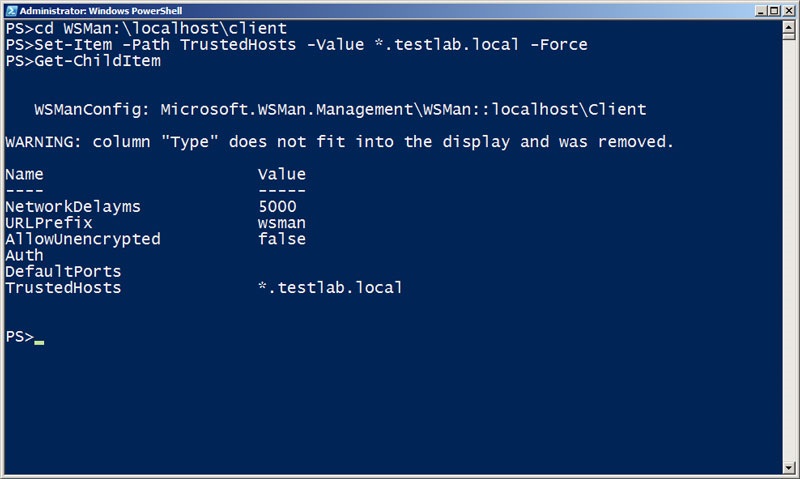
There are many WSMan configuration options, and not all of them can be managed with Group Policy. Windows PowerShell provides a WSMan: drive that can be used to view and modify the configuration.
Cd WSMan:\localhost\client
Set-Item –Path TrustedHosts –Value *.testlab.local –Force
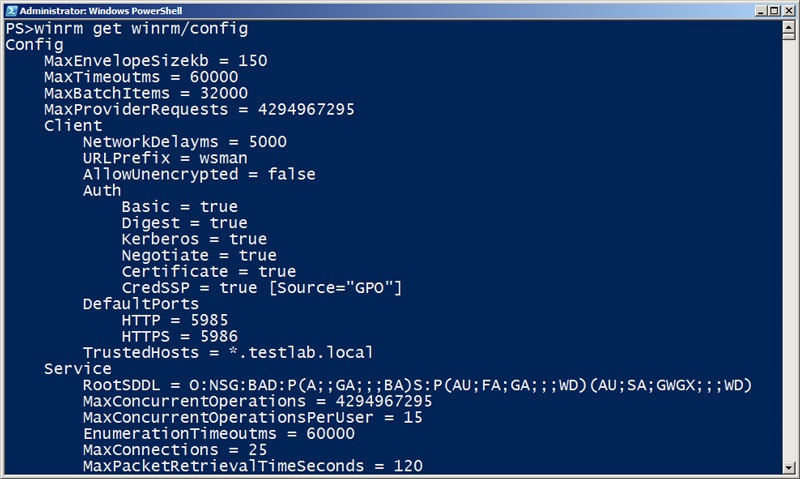
Another option for configuring WSMan is the winrm VBScript. I like using this to view my configuration because it tells me which settings are being configured with a Group Policy Object.
There are many different ways that PowerShell Remoting can be configured, and beyond the basics, it really depends on the specifics of the environment. Fortunately, there is a wealth of information about these scenarios and more in the about_remote_requirements and about_remote_troubleshooting Help files, which provide solutions for dealing with various issues when you are trying to get PowerShell Remoting working.
~Jason
Awesome job, Jason. Thank you for sharing your insights with us. We look forward to Part Three tomorrow.
I invite you to follow me on Twitter and Facebook. If you have any questions, send email to me at scripter@microsoft.com, or post your questions on the Official Scripting Guys Forum. See you tomorrow. Until then, peace.
Ed Wilson, Microsoft Scripting Guy



0 comments