Summary: Microsoft Scripting Guy, Ed Wilson, talks about using Windows PowerShell to configure Windows Defender preferences.
Microsoft Scripting Guy, Ed Wilson, is here. Today is the day. It is time for PowerShell Saturday #005 in Atlanta. This fifth Windows PowerShell Saturday conference is a sell out like the four previous ones. It is really exciting to see IT pros give up a Saturday to learn about this exciting technology. In reality, they are not giving up much, because the sessions are exciting, useful, and practical. If you missed this one, don’t despair, because Windows PowerShell Saturday #007 is going to be in Charlotte, North Carolina, and the roster of speakers is stellar! If you did make it to Atlanta, make sure you thank Mark Schill for all the hard work he has put into making this event a reality. If not for him, there would be no Windows PowerShell Saturday event in Atlanta. It is so cool how the power of the community steps in and makes these things a reality. Of course, also come by and say hi to the Scripting Wife and me.
Note This is the fifth in a series of posts about the Windows Defender module in Windows 8.1. For more information, please see:
- Exploring the Windows Defender Catalog.
- Use PowerShell to Explore Windows Defender Preferences
- Use PowerShell to Update Windows Defender Signatures
- Use PowerShell to See What Windows Defender Detected
The other day, I wrote a post about exploring Windows Defender preferences. For my network, the defaults are just fine. But what if I needed to make changes? How would I do that? The cool thing is that with the Windows Defender module in Windows 8.1, I can use Windows PowerShell 4.0 to make the changes. The Windows Defender module is a CIM wrapper for new WMI classes, and so they remote by using the WinRM protocol that CIM utilizes. For information about using CIM against remote computers, see these Hey, Scripting Guy! Blog posts.
Configuring Windows Defender with Windows PowerShell is easy. You use the Set-MpPreference function. Everything you need to do is exposed as a parameter. This is good news, and also a bit of bad news, because the syntax is really, really long. Here is the syntax of the Set-MpPreference function.
PS C:\> get-help Set-MpPreference | select -expand syntax
Set-MpPreference [-AsJob] [-CheckForSignaturesBeforeRunningScan <Boolean>]
[-CimSession <CimSession[]>] [-DisableArchiveScanning <Boolean>]
[-DisableBehaviorMonitoring <Boolean>] [-DisableCatchupFullScan <Boolean>]
[-DisableCatchupQuickScan <Boolean>] [-DisableEmailScanning <Boolean>]
[-DisableIntrusionPreventionSystem <Boolean>] [-DisableIOAVProtection <Boolean>]
[-DisablePrivacyMode <Boolean>] [-DisableRealtimeMonitoring <Boolean>]
[-DisableRemovableDriveScanning <Boolean>] [-DisableRestorePoint <Boolean>]
[-DisableScanningMappedNetworkDrivesForFullScan <Boolean>]
[-DisableScanningNetworkFiles <Boolean>] [-DisableScriptScanning <Boolean>]
[-ExclusionExtension <String[]>] [-ExclusionPath <String[]>] [-ExclusionProcess
<String[]>] [-Force] [-HighThreatDefaultAction <ThreatAction>]
[-LowThreatDefaultAction <ThreatAction>] [-MAPSReporting <MAPSReportingType>]
[-ModerateThreatDefaultAction <ThreatAction>] [-QuarantinePurgeItemsAfterDelay
<UInt32>] [-RandomizeScheduleTaskTimes <Boolean>] [-RealTimeScanDirection
<ScanDirection>] [-RemediationScheduleDay <Day>] [-RemediationScheduleTime
<DateTime>] [-ReportingAdditionalActionTimeOut <UInt32>]
[-ReportingCriticalFailureTimeOut <UInt32>] [-ReportingNonCriticalTimeOut <UInt32>]
[-ScanAvgCPULoadFactor <Byte>] [-ScanOnlyIfIdleEnabled <Boolean>] [-ScanParameters
<ScanType>] [-ScanPurgeItemsAfterDelay <UInt32>] [-ScanScheduleDay <Day>]
[-ScanScheduleQuickScanTime <DateTime>] [-ScanScheduleTime <DateTime>]
[-SevereThreatDefaultAction <ThreatAction>] [-SignatureAuGracePeriod <UInt32>]
[-SignatureDefinitionUpdateFileSharesSources <String>]
[-SignatureDisableUpdateOnStartupWithoutEngine <Boolean>] [-SignatureFallbackOrder
<String>] [-SignatureFirstAuGracePeriod <UInt32>] [-SignatureScheduleDay <Day>]
[-SignatureScheduleTime <DateTime>] [-SignatureUpdateCatchupInterval <UInt32>]
[-SignatureUpdateInterval <UInt32>] [-ThreatIDDefaultAction_Actions
<ThreatAction[]>] [-ThreatIDDefaultAction_Ids <Int64[]>] [-ThrottleLimit <Int32>]
[-UILockdown <Boolean>] [-UnknownThreatDefaultAction <ThreatAction>]
[<CommonParameters>]
Making a simple change
So I see something I would like to change. By default, Windows Defender in Windows 8.1 does not check for a signature update prior to initiating a scan. I would like it to make sure that it has the latest signature before scanning. So how do I do that?
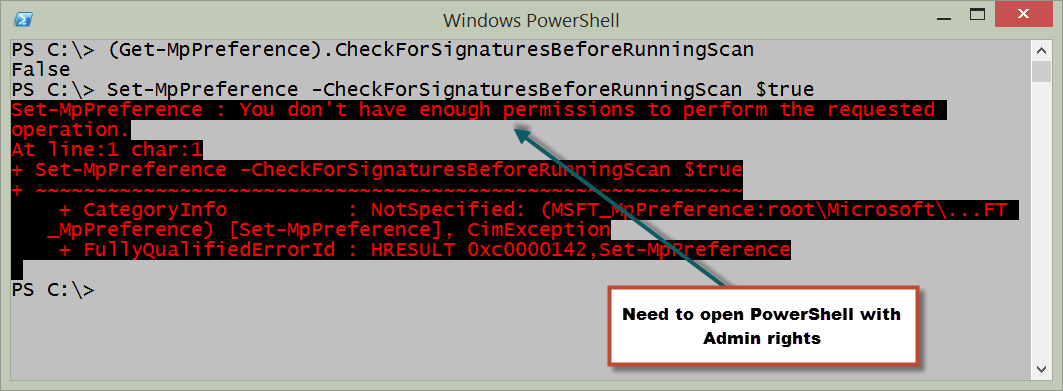
First I check to see what the current value is. I use the Get-MpPreference function to do this. Here is the command I use:
PS C:\> (Get-MpPreference).CheckForSignaturesBeforeRunningScan
False
Now, I use Set-MPPreference to set the value of the parameter to $true to cause it to check first. Unfortunately, an error occurs. Here is the command and the error message:
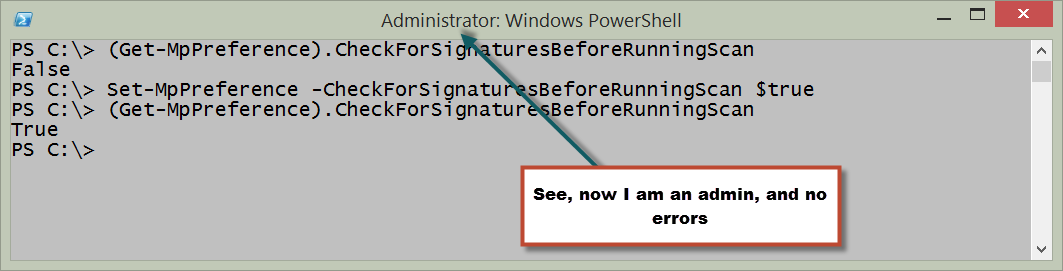
Oh, yeah. That makes sense. I need to have Admin rights to make a configuration change to Windows Defender. So I right-click the Windows PowerShell console icon, and select Run as administrator from the action menu. I say OK to the UAC prompt, and run the commands again. Here is the command I use to set the check before scan value:
Set-MpPreference -CheckForSignaturesBeforeRunningScan $true
Now, I click the Up arrow and re-run the Get-MPPreference command. Everything is groovy. Here is the output from the commands:
Interestingly enough, this particular setting is not one that is available via the graphical user interface.
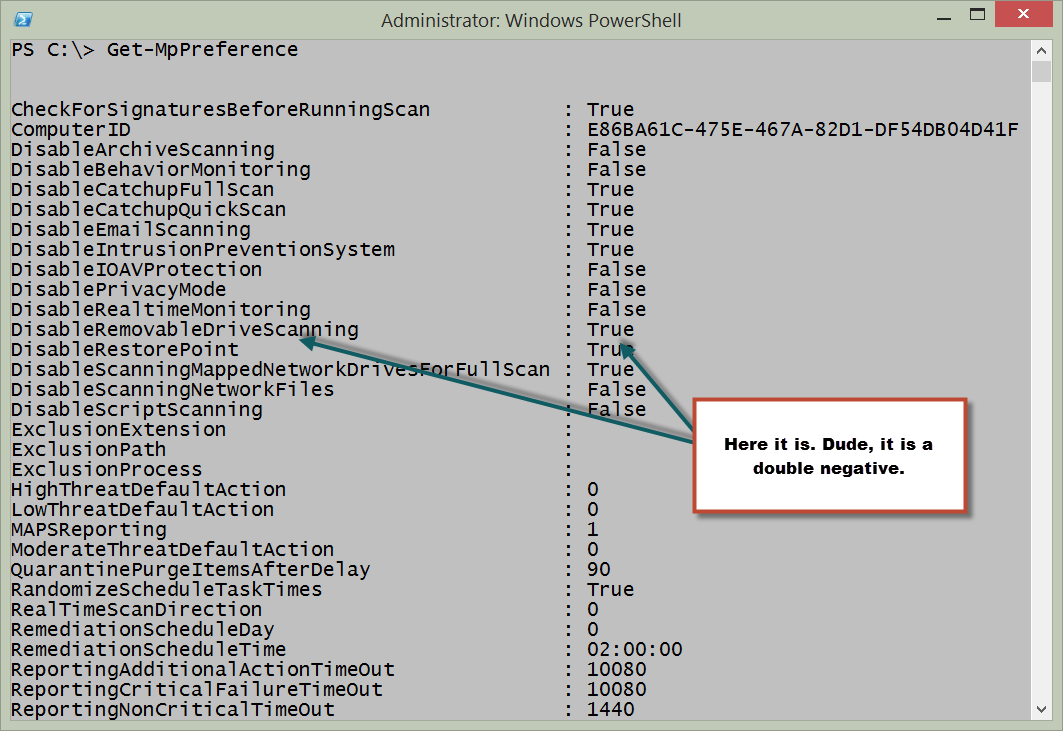
Another setting that I want to change is the one to scan any attached removable drives when Windows Defender does a full scan. It is also one that could be changed via the graphical user interface. How do I make that change? Easy. I need to find the parameter and modify the value.
So I use Get-MpPreference and look for something that makes sense.
I found it! It is called DisableRemovableDriveScanning. Cool. Here is the screen output I used to find this property:
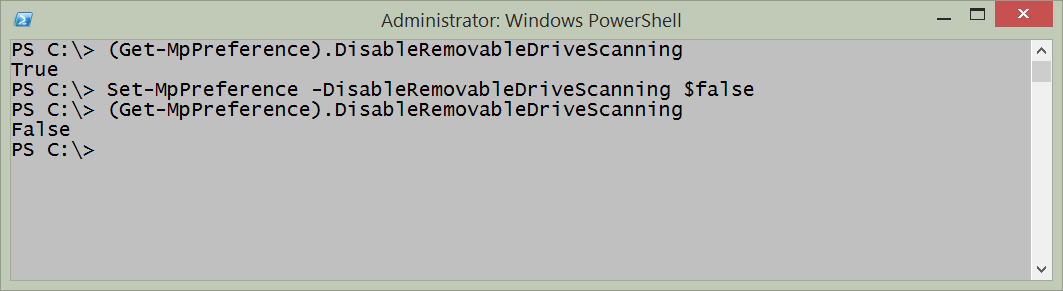
Now all I need to do is to use the Set-MpPreference function to modify the DisableRemovableDriveScanning parameter. Because of the way the function is designed, this is really easy. I press the Tab key to look through the parameters until I find it, and then I set it to $false. Here is the command:
Set-MpPreference -DisableRemovableDriveScanning $false
I use the Get-MpPreference function to ensure the command worked. The following image illustrates the command and the output.
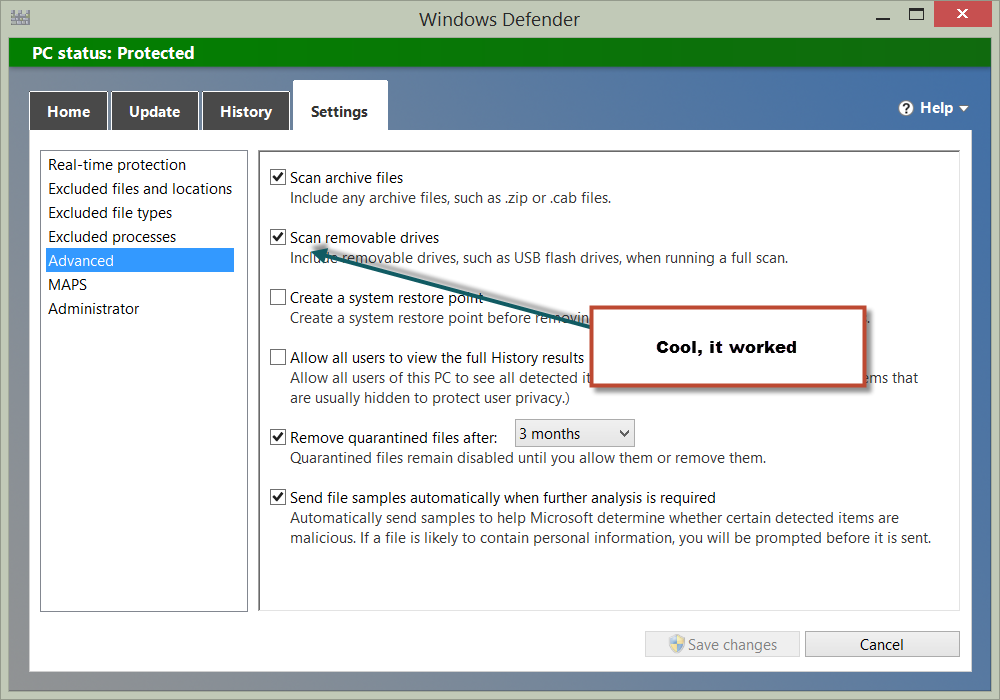
This time, I can use the Windows Defender GUI to check to ensure that my change actually worked. I type Defender on the Start page of my Windows 8.1 device, go to the Settings tab. Sure enough, it worked—as shown in the following image:
And that is all there is to using Windows PowerShell 4.0 in Windows 8.1 to make changes to Windows Defender. Remember, because these are CIM functions, I can do this to remote devices easily by creating a CIM session, and connecting there. Because these CIM functions wrap WMI classes that are not available on down-level systems, you need to upgrade your devices to Windows 8.1 before you can use Windows PowerShell to remotely manage Windows Defender.
Hope to see you in Atlanta today.
I invite you to follow me on Twitter and Facebook. If you have any questions, send email to me at scripter@microsoft.com, or post your questions on the Official Scripting Guys Forum. See you tomorrow. Until then, peace.
Ed Wilson, Microsoft Scripting Guy

0 comments