In this post, Premier Developer consultant Kurt Schenk walks us through setting up an SSH connection to Azure using a jumpbox.
Using SSH to access resources is becoming increasingly common for Windows users. Some typical scenarios are connecting to Linux VMs from Windows development computers; another common one is using SSH to connect to VMs in Azure through a jumpbox. These VMs behind the jumpbox could be any OS such as Linux or Windows, but the jumpbox is the secure entry point, deployed to a management subnet, requiring secure SSH (ideally with a private key vs. username and password) with ingress and egress strictly controlled. For example, see network DMZ reference architecture.
Below I am sharing a walkthrough of how I recently set up to use SSH tunneling through a jumpbox; as well as some helpful links.
- Download and install Git for Windows You will use Git BASH which provides a BASH emulation for Windows, where you can run ssh, openssl, ssh-keygen, and other commands
- Create the private key that you will use to connect to the SSH jumpbox
- SSH can use a username and password as well, but I strongly recommend a private key (and this may indeed be required)
- I used PuTTY to create a PuTTY private key (.ppk) but when I decided to use Git BASH instead, I converted it to an SSH key (.pem) using puttygen. I would recommend just going directly to create an SSH key with Git BASH (using openssl, or ssh-keygen). See this article for more information on using SSH with Windows on Azure.
openssl.exe req -x509 -nodes -days 365 -newkey rsa:2048 \ -keyout myPrivateKey.key -out myCert.pem
- Go to .ssh folder Located at C:\Users\{login}\.ssh (for me C:\Users\kurtsc\.ssh) and
- Create a subfolder authorized_keys and copy the .pem file there
- Create file called config in .ssh folder with the text below, replacing {sshUserName} with your user name, and {privateKey} with the name of your private key, formatted with tabs like below.
Host azure-jump HostName [FQDN or IP of jumpbox accessible on internet] Port 443 User {sshUserName} IdentityFile ~/.ssh/authorized_keys/{privateKey}.pem
- Share the SSH public key with SSH jumpbox administrator who will configure you as a user on the SSH server, using that public key. You will then connect with SSH using your private key.
- Configure proxy in FireFox to support SOCKS5, and Remote DNS[NOTE] Selecting Remote DNS resolves Domain Name System (DNS) requests by using the DNS server in your Azure VNET. Do not select this if that is not the case.
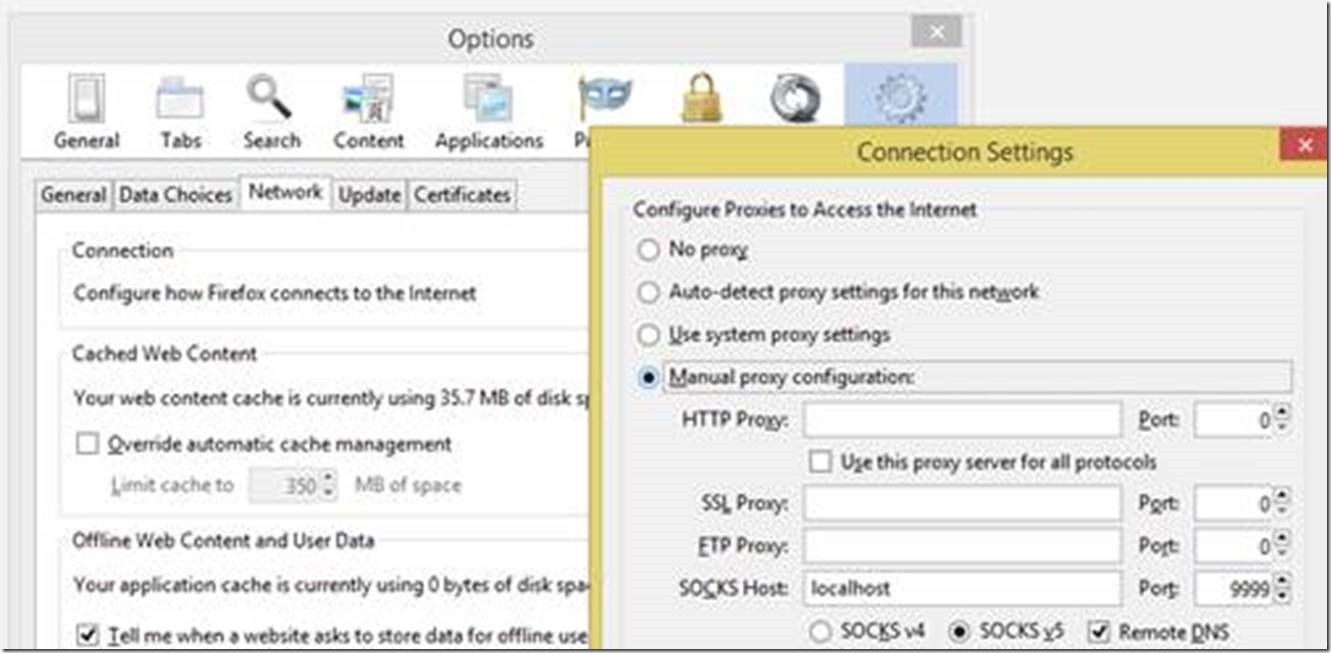
- Start Git BASH and type SSH -D 9999 azure-jump which will make a dynamic tunnel that can be used by SOCKS5 client, like FireFox as described above. You can then browse to web servers in you Azure Virtual Private Network, with https://[WebServerFQDNinYourVNET] if you have DNS set up in your Azure VNET; or https://[WebServerIpAddressInVNET].
![clip_image004[4] clip_image004[4]](data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAg8AAAFLAQMAAABryv0GAAAAA1BMVEXW1taWrGEgAAAACXBIWXMAAA7EAAAOxAGVKw4bAAAAK0lEQVR4nO3BAQEAAACCIP+vbkhAAQAAAAAAAAAAAAAAAAAAAAAAAAAAcGlWoQABHzJTBQAAAABJRU5ErkJggg==)
- Connecting to a database from SQL Server Management Studio
- Run the command below in Git BASH to create a local forward of port 8500 to the database server:
ssh -L 8500:10.0.10.4:1433 azure-jump
- in SSMS connect to 127.0.0.1,8500 and enter the proper SQL Server Login credentials
- Run the command below in Git BASH to create a local forward of port 8500 to the database server:
Links
Use SSH key authentication with VSTS: https://docs.microsoft.com/en-us/vsts/git/use-ssh-keys-to-authenticate
Example of SSH port forwarding to Jenkins: https://docs.microsoft.com/en-us/azure/jenkins/azure-container-agents-plugin-run-container-as-an-agent#connect-to-the-jenkins-server-running-on-azure
https://docs.microsoft.com/en-us/azure/virtual-machines/linux/create-ssh-keys-detailed
Discusses SOCKS5 support in browsers: https://docs.microsoft.com/en-us/azure/hdinsight/hdinsight-linux-ambari-ssh-tunnel

![clip_image004[4] clip_image004[4]](https://devblogs.microsoft.com/wp-content/uploads/sites/31/2019/04/clip_image0044_thumb.jpg)
![clip_image006[4] clip_image006[4]](https://devblogs.microsoft.com/wp-content/uploads/sites/31/2019/04/clip_image0064_thumb.jpg)
0 comments