Security, governance and privacy built into Microsoft Graph Data Connect
Microsoft Graph Data Connect is a secure, scalable data service to quickly copy relevant Microsoft 365 datasets into your Azure Synapse Analytics for advanced analytics and insights. In this blog, we highlight the latest innovations enabling customers to build these analytics applications with data security, governance, and end user privacy in mind.
What’s New?
We are securing Microsoft 365 data by minimizing compliance management overhead for customers’ Microsoft 365 Administrators. Specify detailed compliance policies for applications to use Microsoft 365 data:
- Encrypted datasets for multi-tenant applications
- Muti geo access (available in public preview)
Ensure data governance so applications only use data essential to their analytics use case. Govern data by specifying what types of data an application can access:
- Streamlined approval and consent experience (available in private preview)
- Audit logs (available in public preview)
Upholding user privacy while enabling organizations to run analysis on deidentified data:
- Identity obfuscation (available in private preview)
Encrypted datasets for multi-tenant applications
By default, we transfer Microsoft 365 datasets in plain text in JSON format. With encrypted datasets by default, we will deliver datasets to multi-tenant applications encrypted by default with private key that is owned by the service. Multi-tenant application developers then request decryption of Microsoft 365 datasets for analysis.
Our customers may be concerned that Microsoft 365 datasets sitting in storage can be accessed and read by malicious actors. This update adds an additional level of security so that when the data is sitting in Azure, it is encrypted at rest by default. Even if a malicious actor tries to open the file, they will not see anything as the file will be fully encrypted.
Multi geo access updates
Currently, tenants who have the multi-geo capability enabled in Microsoft 365 can only access Microsoft 365 dataset through Microsoft Graph Data Connect in their respective geographic location. This means that data from different geographic regions need to be manually joined together to prepare the data for analysis. This can often be a slow, error-prone process. With this change, we are removing that limitation for companies with multi-geo tenants.
However, to maintain stringent content residency requirements, we are intentionally scoping this only for directory related datasets:
- Azure Active Directory (see here)
- Microsoft Groups (see here)
These datasets enable users to run system metadata analysis including our new SharePoint Information Oversharing use case. Learn more about that use case: Scale access to Microsoft 365 data with Microsoft Graph Data Connect – Microsoft 365 Developer Blog
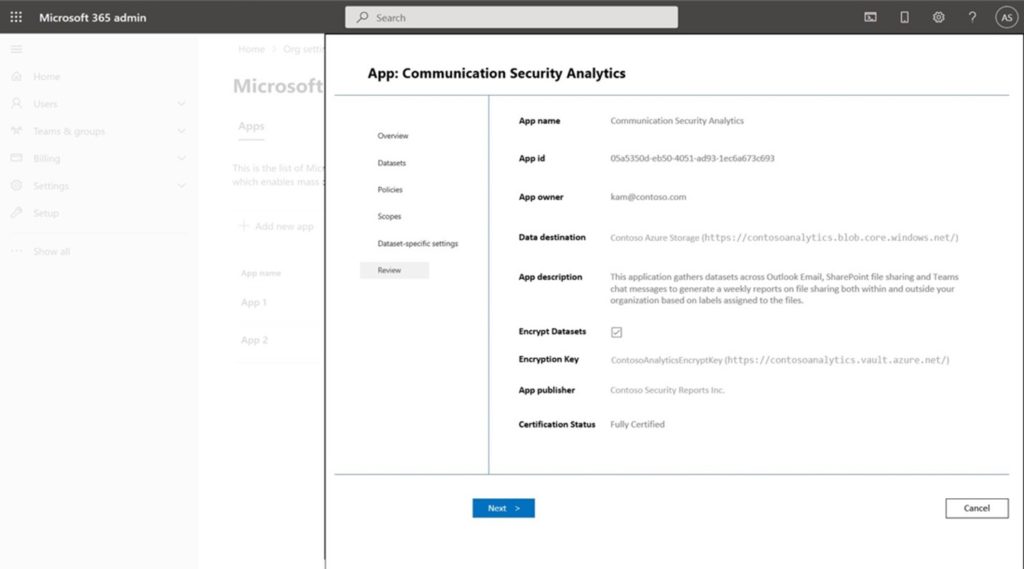
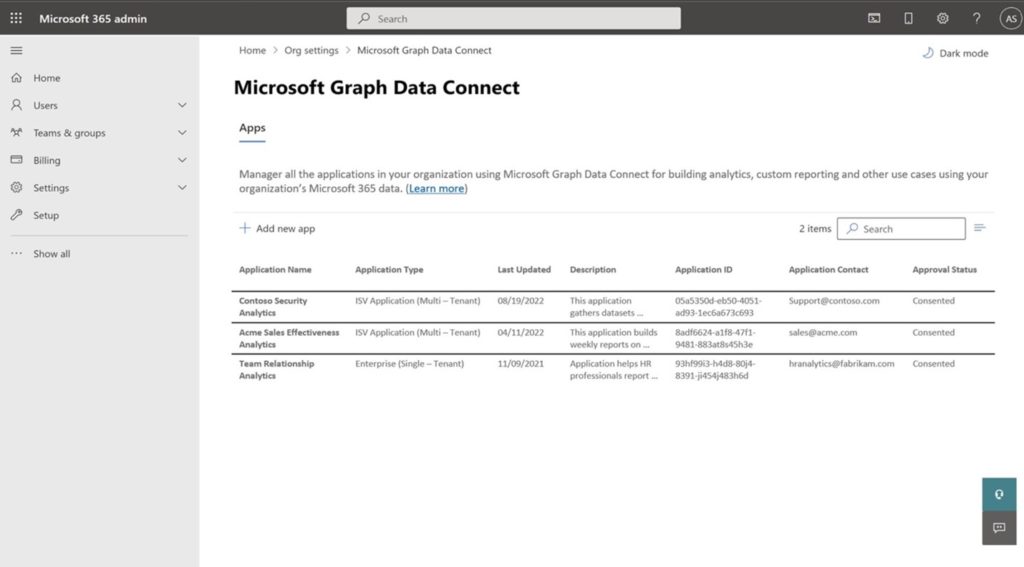
Streamlined approval and consent experience in Microsoft Compliance Center (MCC)
Microsoft 365 administrators can control (via granular controls) availability of the datasets to the tenants. In the past, Microsoft 365 administrators were only able to control approval and consent experiences. Now, administrators can define workload specific datasets made available to the approved applications resulting in an enhanced tenant level control and approval experience. As part of the same controls, you also have cross tenant data movement to control ISV access to Microsoft 365 datasets.
In our updates at Microsoft Ignite 2022, we announced private preview support of multi-tenant applications with Microsoft Graph Data Connect. With the new multi-tenant offering, ISV/SI developers would be able to build applications for their customers in their own tenancy and offer more robust solutions. With support for multi-tenant applications, we are also enabling tenant wide controls for these multi-tenant applications to enable/disable such access patterns with Microsoft Graph Data Connect.
Microsoft 365 administrators can now approve data access directly from the Microsoft 365 Admin Center (admin.microsoft.com). This means that Microsoft 365 administrators will be able to directly enable Microsoft Graph Data Connect without using Privileged Access Management (PAM) to consent to the application’s data usage. This also removes the additional E5 license requirements that our customers originally needed with PAM to approve Microsoft Graph Data Connect data access requests.
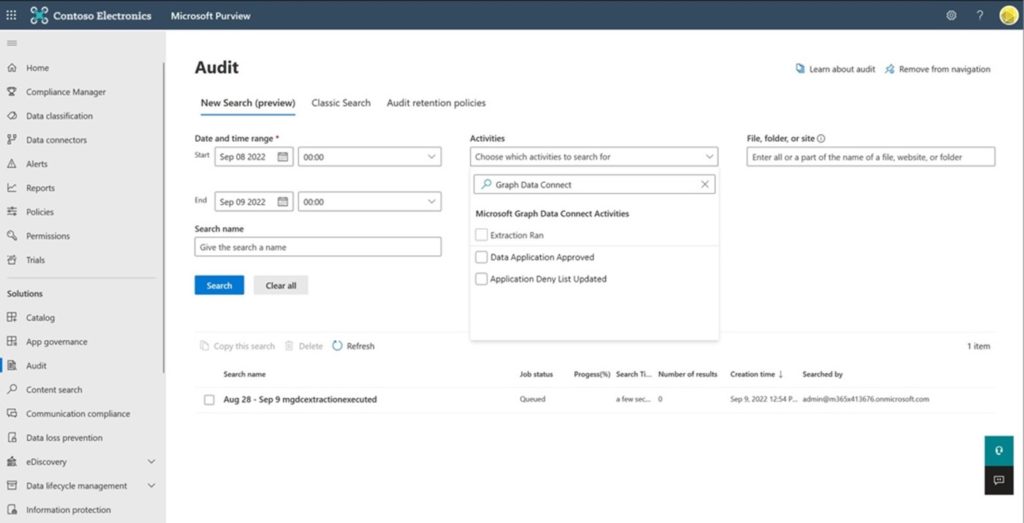
Audit logs for all Data Connect application access and approvals
We improve the overall audit experience with audit logs in the Microsoft Compliance Center. Previously, the only tracking that was available was when administrators approved or rejected an application to run in the organization.
This update provides a complete audit log view of all the events taking place across all applications using Microsoft Graph Data Connect running in your tenancy as a standardized report. This includes event level details covering application approvals, application run history (tracking dataset used, users accessed, volume of data transferred), application declined, and answer questions including:
- Validating Access: How often was the data accessed? Who accessed the data? Which regions are accessing the data? How often was the data accessed?
- Reporting Updates: How often did specific users request an update of the data? Was the data partially or fully refreshed? How much data was consumed in the update? Which users got this report? Were there failures in pulling the dataset that resulted in only partial dataset?
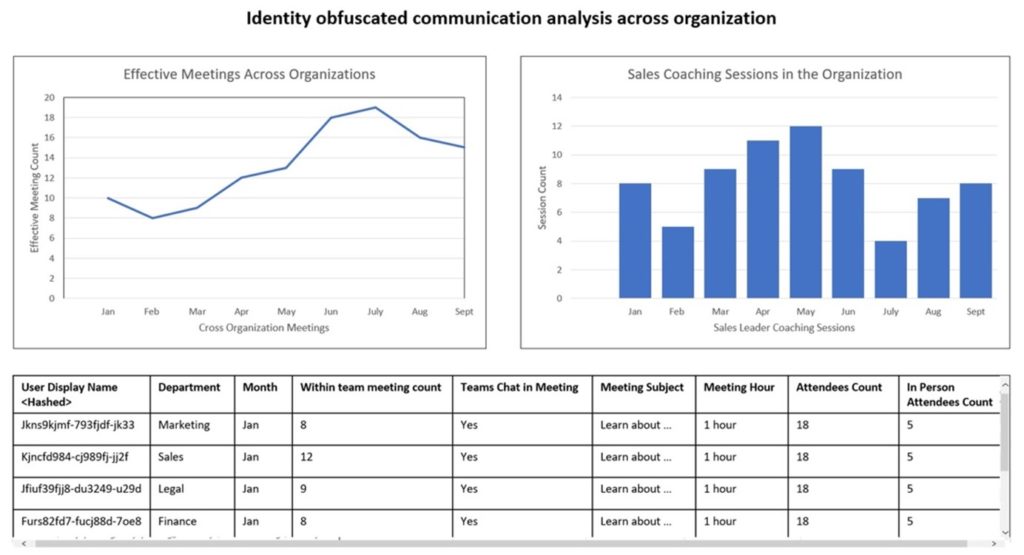
Identity obfuscation for select datasets
When accessing Microsoft 365 datasets for analytics, we provide user ID’s that can potentially be connected back to an individual. For example, an e-mail will have a sender’s object ID (which is a unique, random ID that is assigned to the sender of the e-mail). This is generally considered secure, but we want to take it a step further.
We are adding optional controls to obfuscate end user identity so that you will not be able to tie that ID back to an end user, but it will still be a unique user in that overall dataset. This enables a customer to build analytics and reporting to track overall usage and information sharing for business process analysis, but they will not be able to tie data to a specific individual in their own company or organization. Our solution preserves end user privacy, while still enabling organizations to run their analytics and reporting on top of obfuscated Microsoft 365 datasets.
Recap
We’ve seen:
- Security: Encrypted datasets for multi-tenant applications and Muti Geo Access
- Governance: Streamlined Approval & Consent Experience and Audit Logging
- Privacy: User identity obfuscation
Learn more
- Ignite blog: Scale access to Microsoft 365 data with Microsoft Graph Data Connect – Microsoft 365 Developer Blog
- Ignite breakout session: From low code to pro code: building and buying collaborative apps to power an evolving workplace (microsoft.com)
- Visit the Microsoft Graph Data Connect webpage

 Light
Light Dark
Dark
0 comments