There are scenarios where you may want to query your service from within the Kaizala card. While the APIs to be queried are public (without any authentication), you can query them directly. But, in case you want to secure your APIs to make sure the calls are made by the particular user from within the Kaizala card alone – you use the Integration Service token. This post explains how you generate this token and subsequently validate this on the service side.
Generating the Integration Service token
To generate the Integration Services token from within the card, you will need to call the method getIntegrationServiceToken exposed in the SDK (KASClient.js). Below is the screenshot of the API and the result printed from the developer tools console.
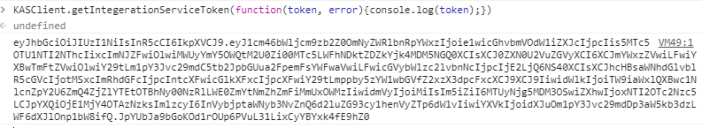
You can now pass this in your call to the API (as a header / in the body).
Validating the token
In order to identify if the API request is genuine, you will need to validate the token. This is done by calling into the v1/users/me endpoint with the token as the accessToken in the header. Integration Service token’s validity is 30 mins.
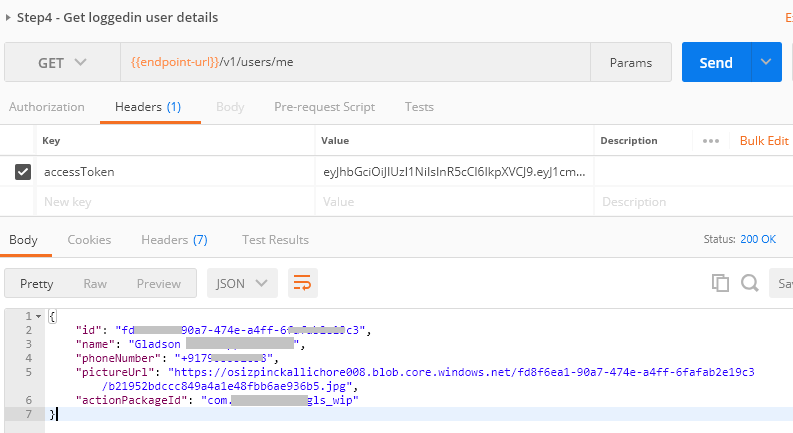
This gives you the following details:
- id – Kaizala user id, a guid to identify the user
- name – name set by the user in the profile
- phoneNumber – phone number of the user
- pictureUrl – link to the profile picture
- actionPackageId – Id of the Kaizala card / action package from which the token was generated
You can then use this on the service side to validate if the token to authenticate and authorize the request.
Hope that was helpful. Let me know if you have any questions through the comments section or you can email kaizaladev@microsoft.com. Thank you for reading!

0 comments