In the digital age, identity and access management (IAM) is crucial for protecting data and ensuring that only authorized users, machines, and applications get access to the right resources, at the right time. It’s an essential part of ensuring secure and efficient system interactions.
This blog post explores some of the core elements of identity and access management, offering insights into its critical role in cybersecurity.
Basic concepts
Before we go any further, let’s make sure you’re familiar with a few basic concepts:
-
A resource is a digital asset that requires protection and controlled access. Essentially, anything that a user or digital entity, like a machine or application, might need to access or interact with in a digital environment. Examples include files, databases, web applications, APIs, devices, or services.
-
A user is someone represented by a digital identity (see below) who wants to access a resource or group of resources. For example, it could be a customer, partner, member, or an employee. A digital identity can also represent a non-human, digital entity such as a machine, application, or workload that wants to access a resource.
-
Authentication is the process of verifying the identity of a user or digital entity before granting access to resources. It involves validating credentials such as passwords, biometrics, or security tokens. It determines whether an entity is allowed to proceed to authorization.
-
Authorization follows authentication. It is the process of determining what level of access an authenticated user or digital entity has to specific resources and what actions they are allowed to perform.
What is digital identity?
At the heart of IAM lies the concept of digital identity—a collection of unique identifiers or attributes that represent users or digital entities in a computer system. These unique identifiers can include email addresses, sign-in credentials, and government-issued IDs, as well as more complex attributes, like MAC or IP addresses.
Identities are used to authenticate and authorize access to resources. The three types of identities are human, workload, and device identity, each playing a distinct role in the digital landscape:
Human identities
- Internal users (employees) and external users (customers, consultants, vendors, and partners).
Workload identities
- Software workloads such as applications, services, scripts, or containers.
Device identities
- Desktop computers, mobile phones, IoT sensors, and IoT managed devices.
Having a clear understanding of the different types of identities is critical for developers when creating systems that securely and efficiently manage identities. But it’s also empowering to understand these concepts when selecting an identity-as-a-service (IDaaS) solution to integrate with your application.
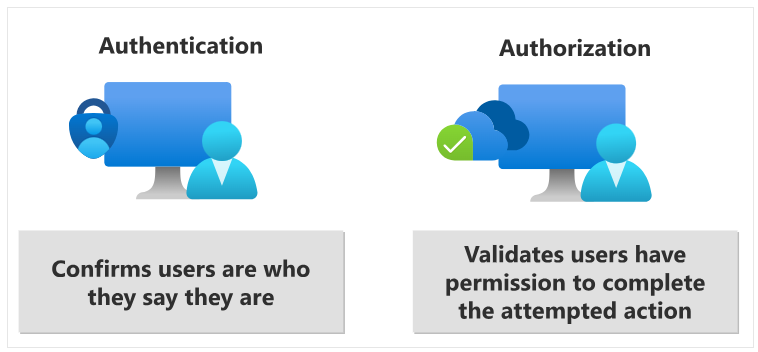
What’s the difference between authentication and authorization?
Authentication is verifying an identity—proving you are who you say you are. Authorization is granting an authenticated party with the permission to do something.
Understanding authentication
Authentication is the process of verifying an identity. It typically requires the use of credentials such as passwords, biometric data, or one-time passcodes. Although the industry is increasingly moving towards passwordless authentication technology.
Implementing robust authentication mechanisms, such as multi-factor authentication (MFA) and single sign-on (SSO), is essential for protecting user data and streamlining access across multiple platforms.
MFA is a security measure that requires you to provide more than one piece of evidence to verify your identity, such as a security token or fingerprint.
SSO allows you to authenticate your identity once, and then access other resources available to you, without the need for signing on to multiple systems.
Understanding authorization
The terms authentication and authorization and are often confused. It’s understandable. To the end user, they are generally experienced as a single flow or journey. They do, however, serve distinct functions.
Authentication is the act of verifying identity, ensuring that users or digital entities are indeed who (or what) they claim to be.
Authorization, on the other hand, validates and determines the level of access that an authenticated user, machine, or software component has been granted for a specific resource. Essentially, it defines what a verified user or digital entity is permitted to do within a system.
Together, they form a layered security approach, safeguarding against unauthorized access and ensuring that users and digital entities can only perform actions within their granted permissions.
Picture yourself spending a night at a hotel. Authentication and authorization is the process of checking-in and accessing certain areas of the hotel. You are the user, and your assigned room and other hotel facilities are the resources.
When you check-in, you start the authentication process. Your identification is verified at reception. Once verified, you will be granted permission to access your room and other certain areas in the hotel.
Access is usually provided in the form of a keycard and swiping your keycard is like performing the authorization process. The keycard gives you access to your room and other spaces you are allowed to enter, like the gym or the pool. If you swipe your keycard at another guest’s room or a staff-only area, access is denied.
Core functions of identity and access management
Identity and access management is a framework of policies and technologies that gives verified users or digital entities the appropriate level of secure access to resources, such as emails, databases, and applications. It involves the identification, authentication, and authorization of entities to have access to resources by associating permissions and restrictions with digital identities.
Naturally, the scope of IAM extends beyond employees working on company devices. It also includes customers, contractors, vendors, business partners, and individuals using personal devices.
Note that there is a specific type of identity and access management for customers called customer identity and access management (CIAM) which we look at in more detail in future blog posts.
Identity and access management systems are multifaceted, providing comprehensive features and functionality essential for secure digital environments. They typically provide the following core functionality:
-
Identity management: Creating, storing, and managing users’ digital identities, including monitoring their permissions and access levels.
-
Identity federation: Enabling access across systems, allowing users to use existing credentials for new services, such as getting access to your system.
-
Provisioning and deprovisioning: Managing the user account lifecycle, assigning or revoking access to resources and permission levels.
-
Authentication and authorization: Validating identities and granting appropriate access rights.
-
Access control: Defining and enforcing who or what has access to which resources. Regulating access to systems and data.
-
Reporting and monitoring: Generating reports and activity logs and monitoring for compliance and security purposes and usage patterns.
How does identity and access management work?
When we talk about identity and access management, we’re talking about the creation, storing, and management of identity information and the regulating of access through the processes of authentication and authorization.
IAM encompasses a broad range of systems and approaches—a framework, that orchestrates a series of processes to ensure the secure and efficient management of digital identities and access to resources. Let’s look at a typical flow:
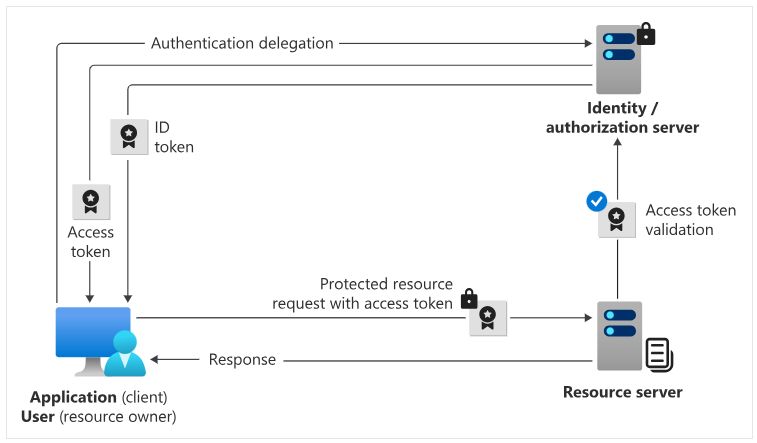
Request authentication
- The user initiates an authentication request with the identity provider from the client application.
Verify credentials
- If the user’s credentials are successfully verified, the identity provider sends an ID token containing user information to the client application.
Grant authorization
- The user consents, and the identity provider sends an access token to the client application, providing access to resources.
Access resources
- The access token is attached to subsequent requests to the resource server from the client application.
Validate and respond
- The identity provider validates the access token and, if valid, grants access to the requested resources and sends back a response to the client application.
The role of identity providers
As you can see from the above, identity providers play a pivotal role in identity and access management. They create, maintain, store, and manage identity information and offer authentication, authorization, and auditing services. Identity providers centralize authentication and authorization policies and processes that monitor user behaviour, identify suspicious activities, and reduce malicious attacks—allowing you, the developer, to implement consistent and robust security across applications and services.
By offering a unified approach to identity management, identity providers like Microsoft Entra ID, Google, Amazon, and Auth0 simplify the user experience while reducing development time and maintenance load. They enhance security with standardized protocols and provide you with the necessary tools to monitor and respond to potential security threats.
Authentication and authorization standards in IAM
Authentication and authorization standards are guidelines and protocols used in identity and access management. They ensure the secure and consistent handling of identity verification and access rights across systems. Commonly used authentication and authorization standards include:
-
OAuth 2.0
- An open-standards authorization protocol that allows applications to access resources on behalf of a user, using tokens instead of sharing user credentials. It has been widely adopted by major social media platforms for secure login and access control.
-
OpenID Connect (OIDC)
- An authentication layer on top of OAuth 2.0 using public-key encryption to verify user identity and obtain profile information. Widely used for single sign-on (SSO), using REST/JSON, making it compatible with a wide range of applications including web-based, native, and mobile apps.
-
JSON web tokens (JWTs)
- A compact, self-contained means of securely transmitting information as a JSON object. Digitally signed for verification and trust, JWTs facilitate the transmission of authenticated user identities between identity providers and services.
-
Security Assertion Markup Language (SAML)
- An open-standard, XML-based markup language for exchanging authentication and authorization data between parties. Enables users to access multiple applications with one set of login credentials. Widely used in enterprise environments for single sign-on (SSO) to (primarily web-based) integrated applications.
-
System for cross-domain identity management (SCIM)
- A standard designed to simplify user identity management across cloud-based applications and services. It streamlines the process of adding or removing users, improving efficiency, and reducing risk.
-
Web Services Federation (WS-FED)
- A Microsoft-developed standard, widely used in our applications, for the secure exchange of identity, authentication, and authorization information between different trust domains using security tokens.
Let’s stay connected
In this blog post, we’ve broken down the basics of identity and access management (IAM). We covered fundamental concepts like resources, users, and digital identities and discussed the differences between authentication and authorization. We delved into the different types of digital identities and their role in secure and efficient systems. We also looked at what IAM is and how it works, the important part that identity providers play, and explored commonly used standards such as OAuth 2.0 and OpenID Connect.
In the blog posts that follow, we’ll be diving deeper into identity-related topics as well as expanding on concepts discussed here. We’ll be focusing on customer identity and access management (CIAM), exploring how it intersects with and differs from broader IAM strategies.
Our aim is to provide informative, useful content for developers looking to implement robust security in customer-facing applications while enhancing the user experience.
To learn more or test out features in the Microsoft Entra suite of product offerings, visit our developer center. Sign up for email updates on the Identity blog for more insights and to keep up with the latest on all things Identity. And, follow us on YouTube for video overviews, tutorials, and deep dives.


This is a great article Adam, very clear and complete. I am going to make it required reading for the juniors on my identity team. My only suggestion would be to add numbers or letters to the identity flow diagram to make it easier to follow the sequence.