Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables users to manage, control, and monitor access to important resources in an organization. Azure DevOps is a key resource for any organization as it stores Application Lifecycle Management artifacts (code, work item, pipelines, packages, test data etc.) of an Organization.
Hence, key roles like Project Collection Admin must not be available forever with anyone and access needs to be enabled on a need basis for certain period of time. This article details the steps to be performed to enable Project Collection Admin access for users in Azure DevOps. Other admin roles like Project Admin, Build Admin etc. can follow same steps.
Pre-requisite
- Azure DevOps must be integrated with Azure Active Directory which is the key to enable PIM.
Steps
1. Login to https://portal.azure.com. Search for Azure Active Directory and click on the same. Select the Groups from left pane and click on Add to create a security group.
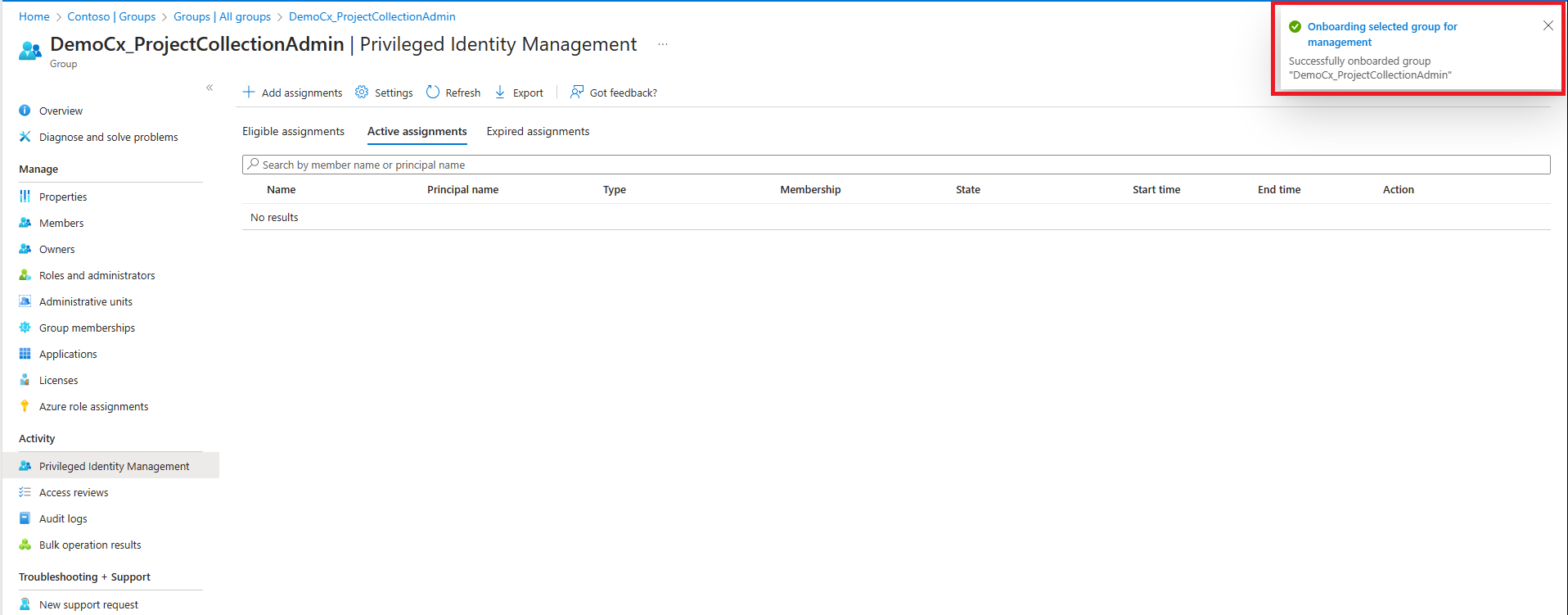
2. Once the group is created, click on the group and select Privileged Identity Management and click on Enable Azure AD PIM for this group button as shown below.
3. This will deploy PIM successfully for the group.
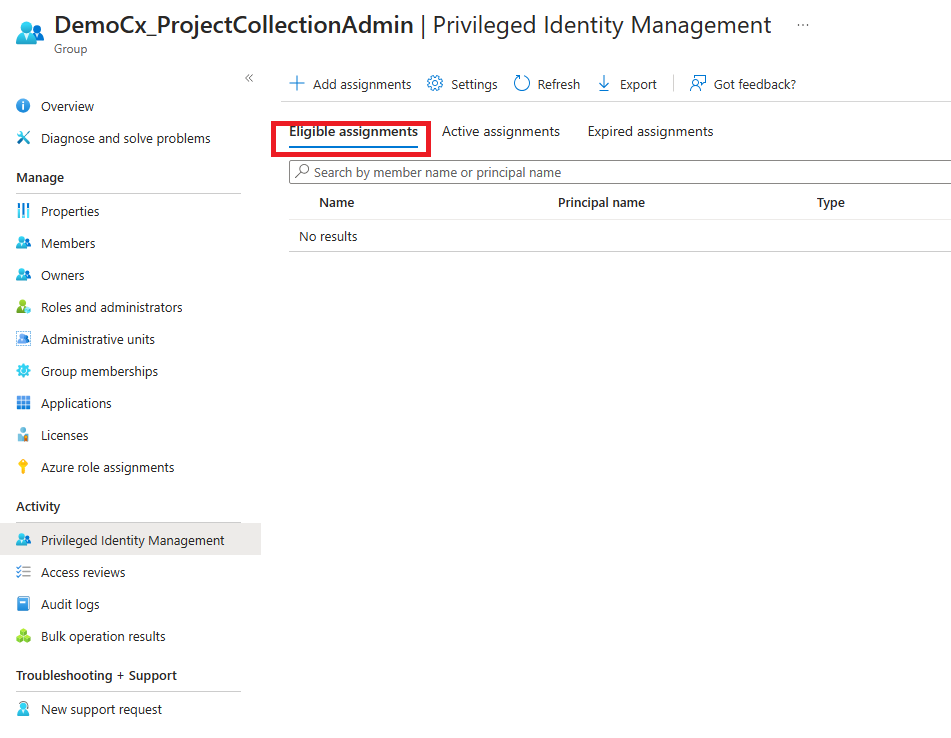
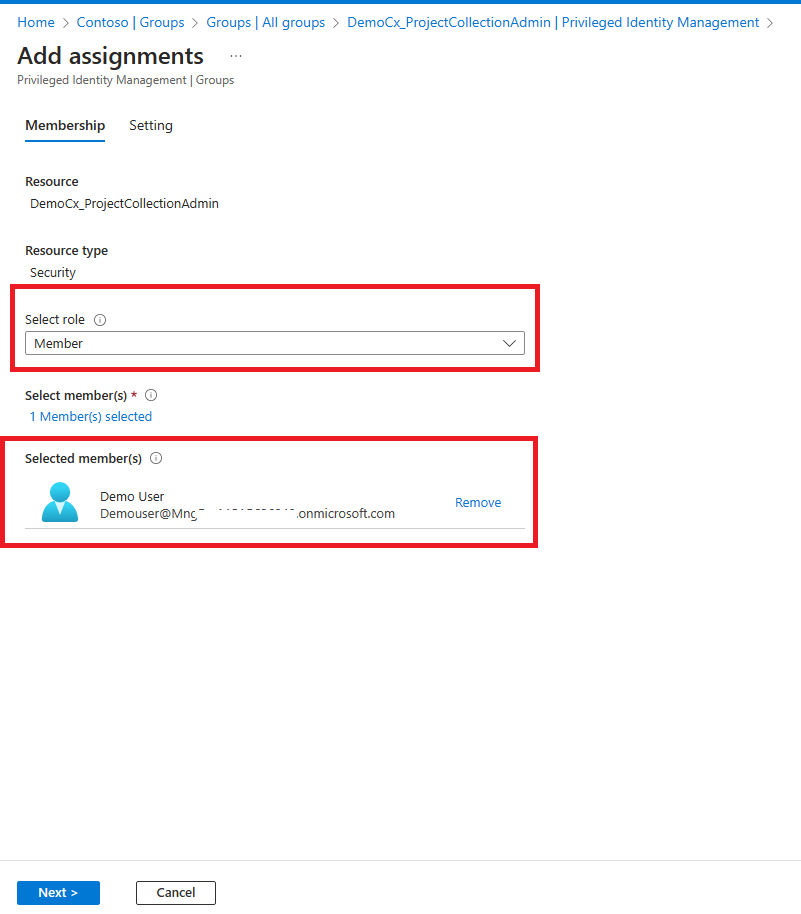
4. Now select Eligible assignments tab and click on Add assignments to assign user (Demo User) to the group who can activate the PIM.
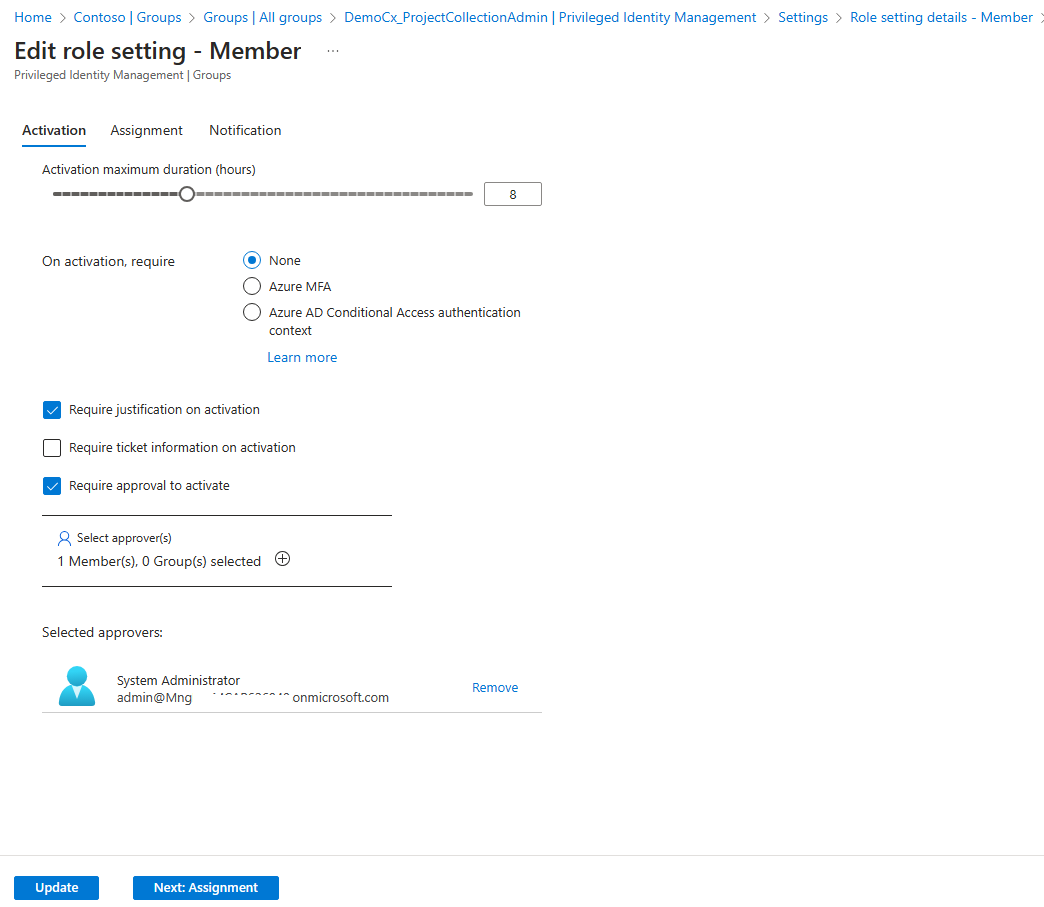
5. Once PIM is assigned, click on settings and click on Member -> Edit to add an Approver who would be eligible to approve the PIM request.
6. Now, the PIM set up is complete in Azure AD and we need to add the security group for which PIM is enabled to Project Collection Administrators role in Azure DevOps.
This completes the overall PIM set up process and next step is to validate the PIM.
Validate
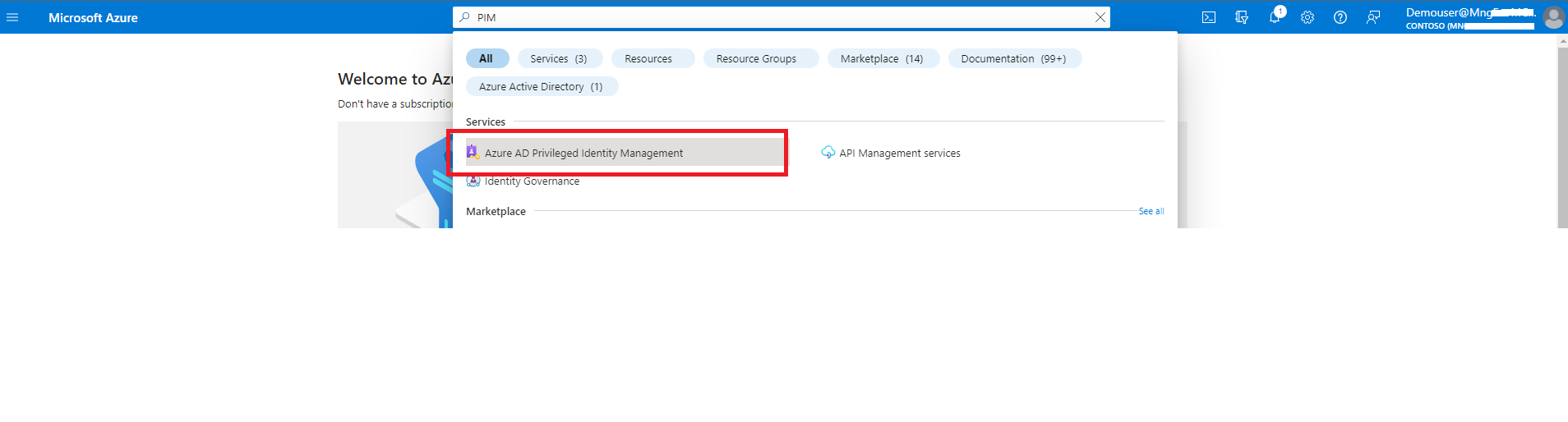
1. The Demo User who has the PIM enabled needs to login to Azure portal and search for Azure AD Privileged Identity Management and click on the same. Select Groups from left pane and then click on the security group for which PIM is enabled.
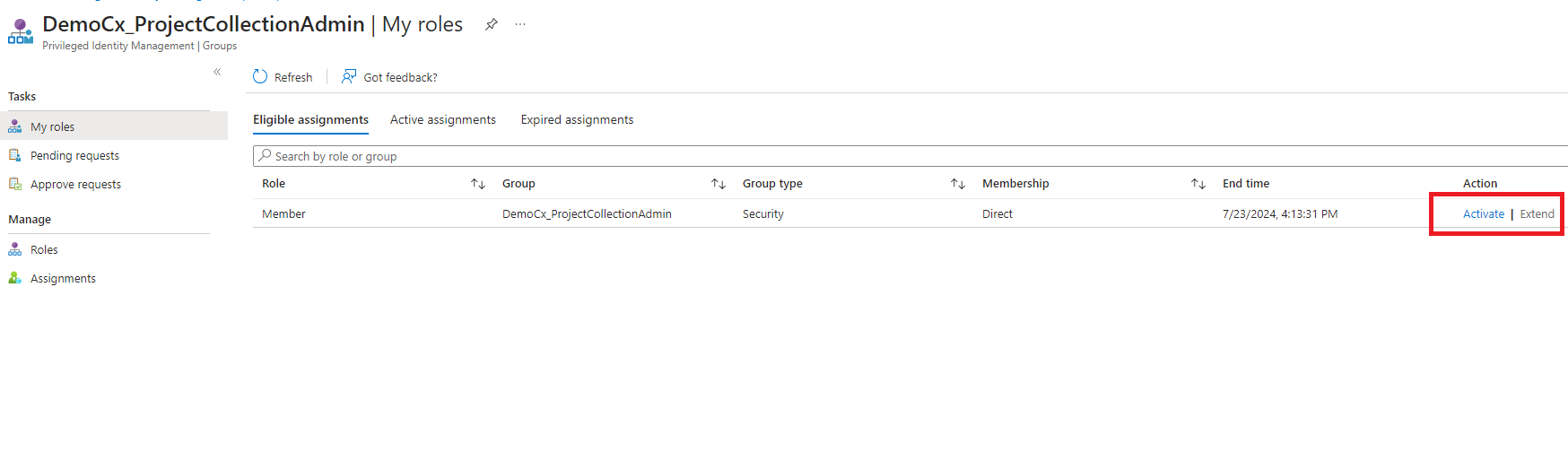
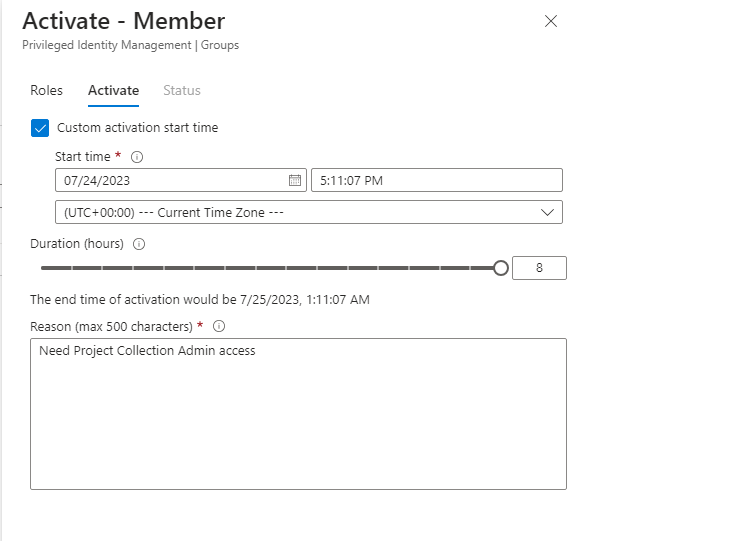
2. User needs to Activate PIM with appropriate reason.
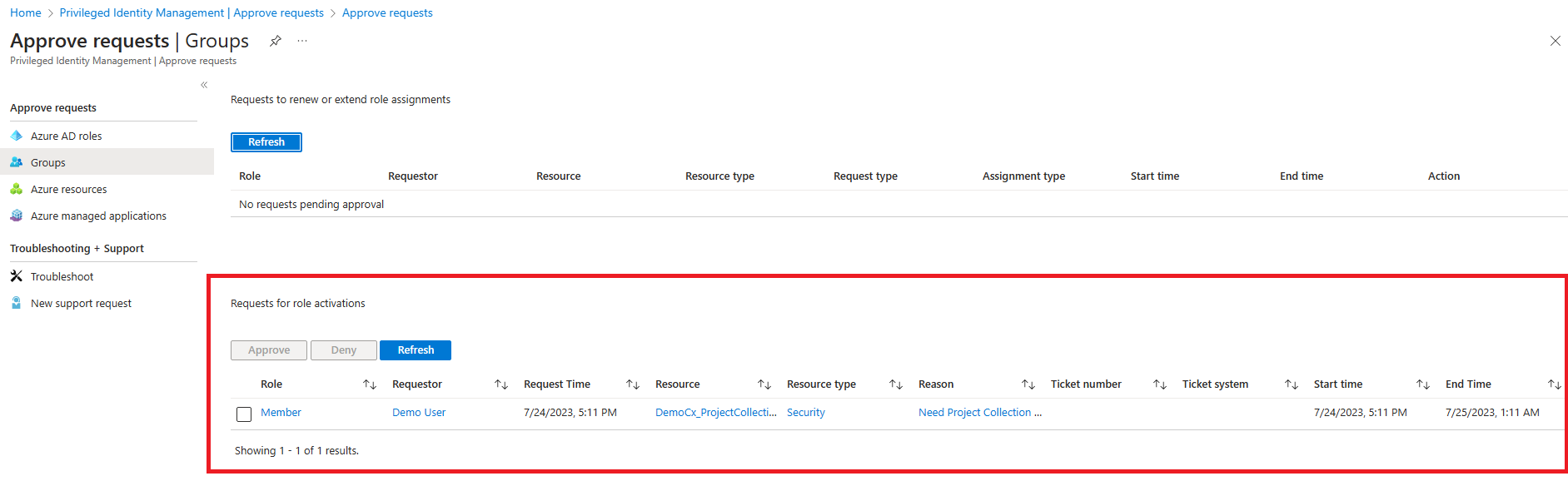
3. Once request is raised, a notification is sent to Approver. The approver can click on the link or login to Azure -> PIM -> Approve Requests -> Groups and select User to be approved.
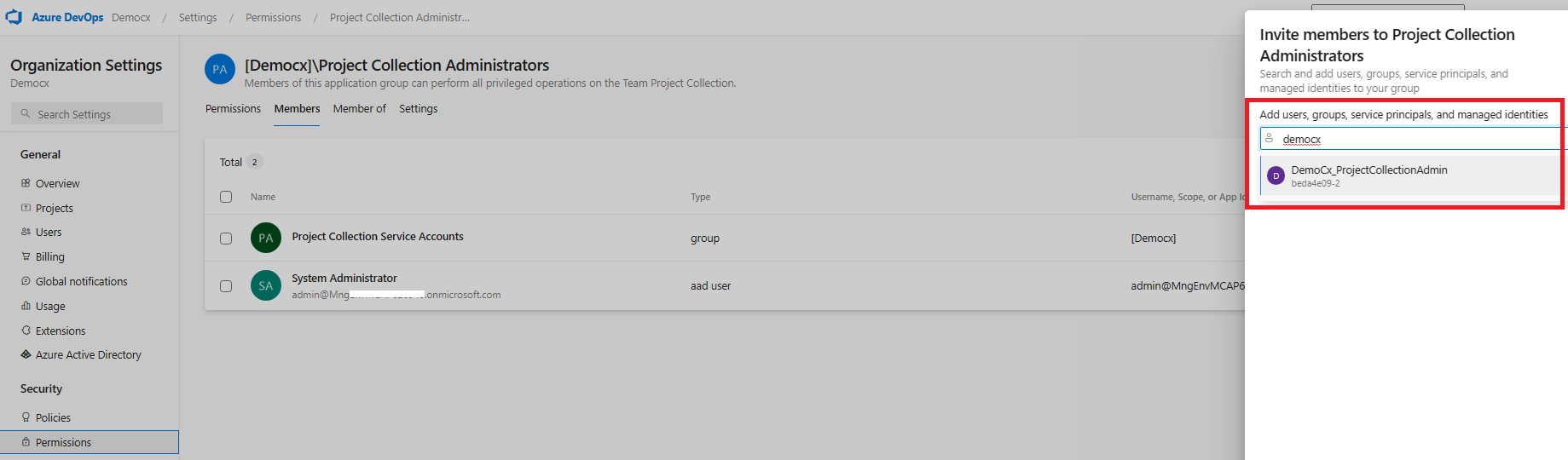
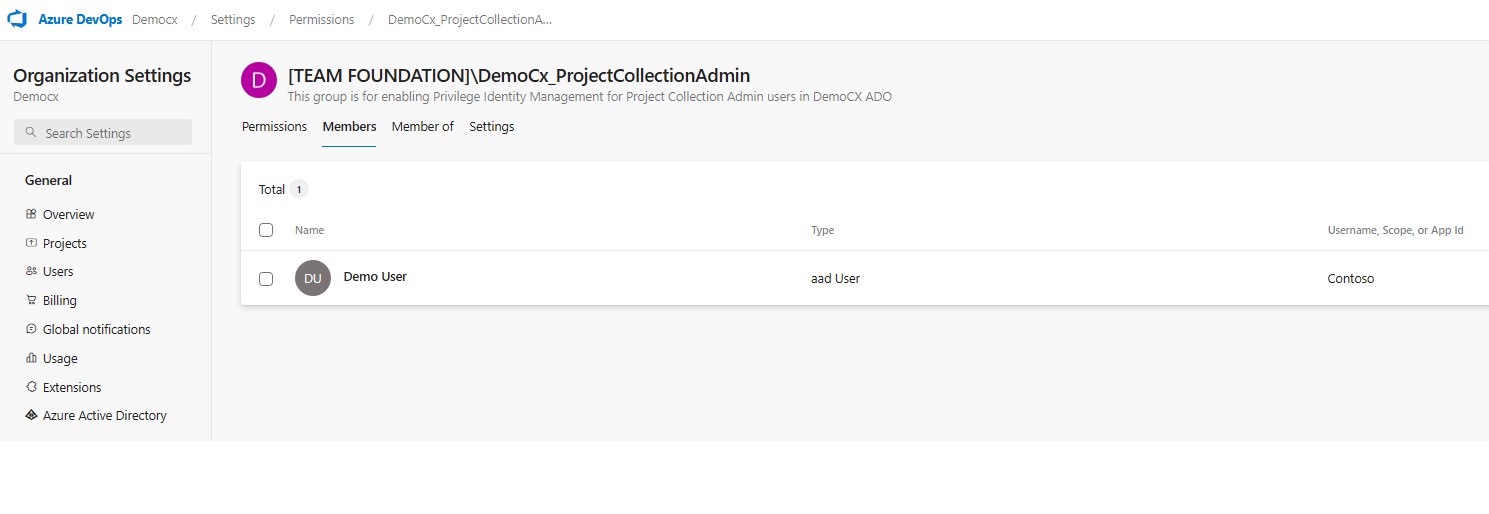
4. Now the approver (assuming that user is a Project Collection Admin) can login to Azure DevOps -> Organization Settings -> Permissions -> Project Collection Admin to check if the user (Demo User) is added to the security group and is reflecting ( just for the demo, here we show that user is available in the group. Generally user can login and check as in step 5)
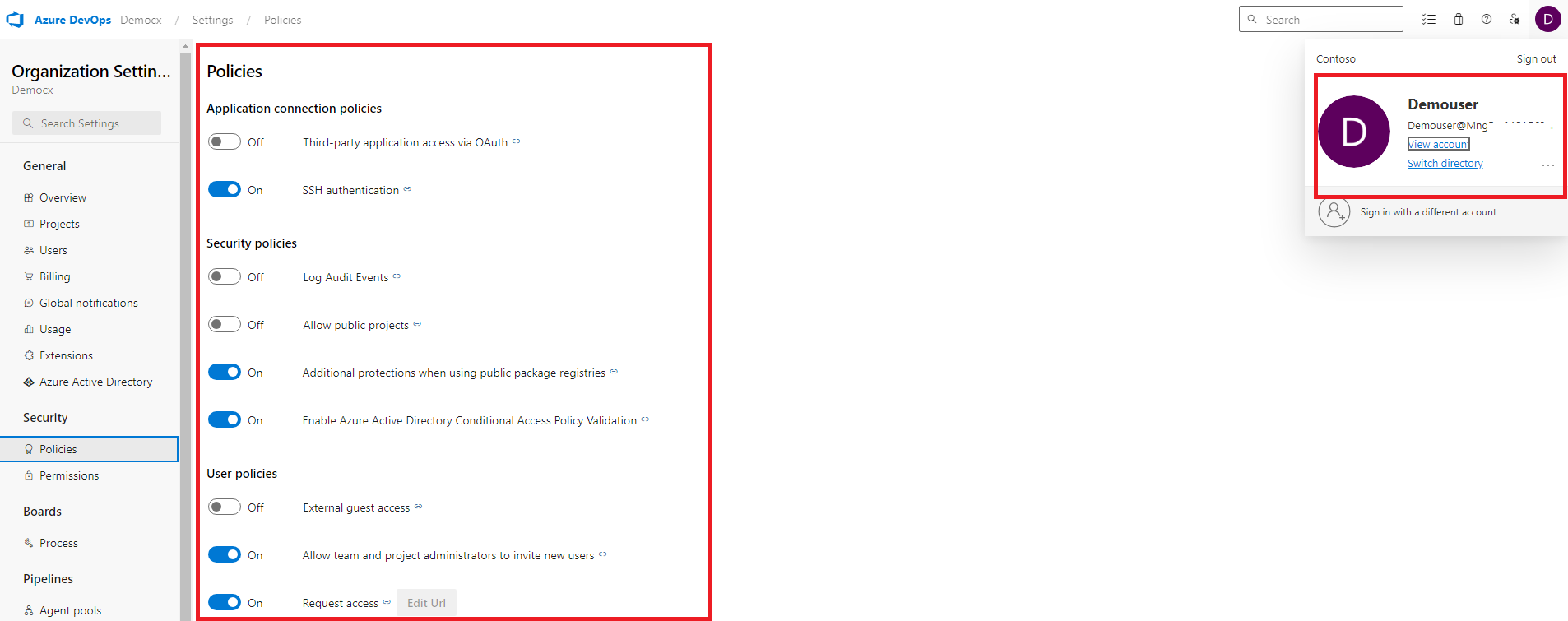
5. Now user can login to Azure DevOps and validate PCA permissions by going to Organization Settings -> Policies under security. Here user is allowed to enable and disable policies which is generally allowed for a Project Collection Admin role.
Note
1. This process of PIM enablement works for members of an organization and not for guest users.
Hope this helps users to secure Azure DevOps in their Organizations. Do leave your comments in case of any queries.



0 comments