Personal access tokens (PATs) make it easy to authenticate against Azure Devops to integrate with your tools and services. However, leaked tokens could compromise your Azure DevOps account and data, putting your applications and services at significant risk.
Customers have told us that their administrators don’t have the necessary controls to limit the threat surface area posed by leaked PATs.
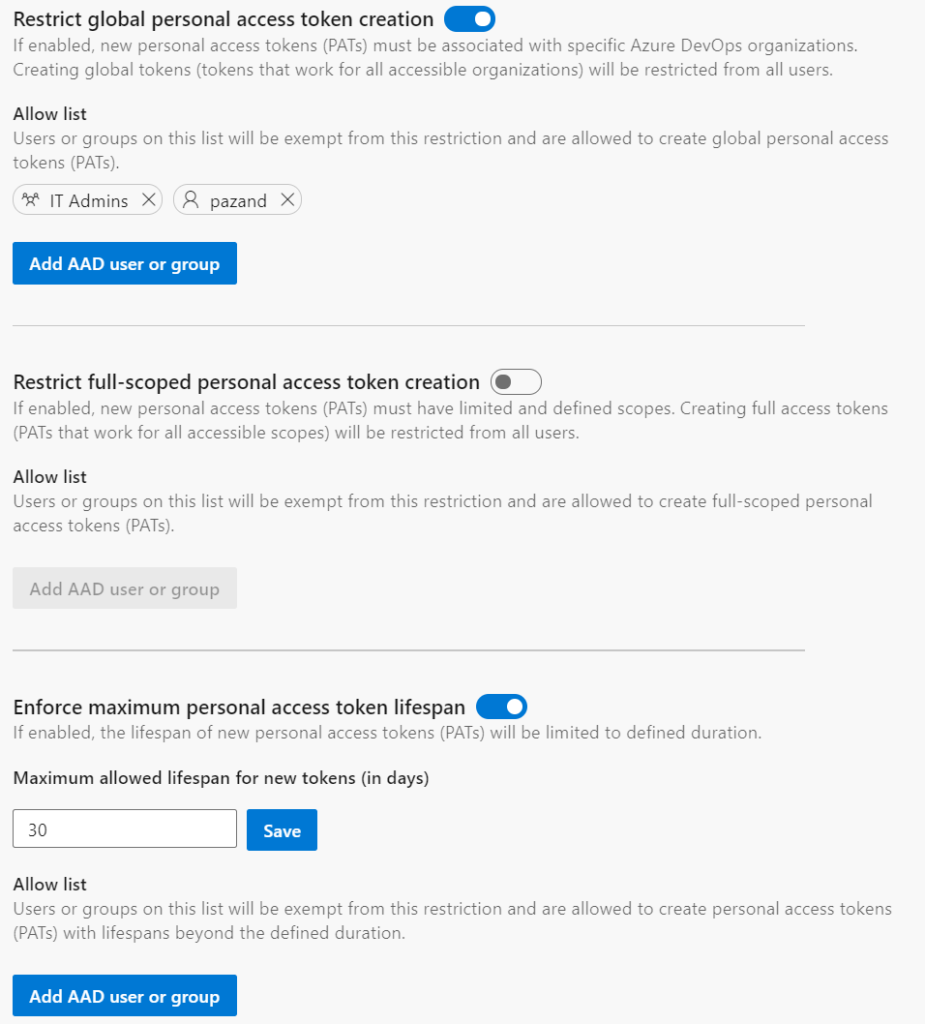
To protect our customers, we’ve added a new set of policies which can be used to restrict the scope and lifespan of your company’s Azure DevOps personal access tokens (PATs)! Here’s how they work:
Users assigned to the Azure DevOps Administrator role in Azure Active Directory can navigate to the “Azure Active Directory” tab in the organization settings of any Azure DevOps organization linked to their Azure AD.
There, administrators can
- restrict the creation of global personal access tokens (tokens that work for all Azure DevOps organizations accessible by the user)
- restrict the creation of full-scoped personal access tokens
- define a maximum lifespan for new personal access tokens
These policies will apply to all new PATs created by users for Azure DevOps organizations linked to the Azure AD tenant. Each of the policies has an allowlist for users and groups who should be exempt from the policy, but shouldn’t be allowed to manage policy configuration.
These policies only apply to new PATs, and will not affect existing PATs that have already been created and are in use. After the policies have been enabled however, any existing, now non-compliant PATs must be updated to be within the restrictions before they can be renewed.
Please comment below with any questions, comments or issues you may have. We take your input seriously and read every bit of feedback. We’re very excited for you all to try this out and let us know what you think!

Hello, some PAT must have a long life span because sometimes it’s the only one solution to authorize a service to Azure DevOps (for example SonarCloud requires PAT with a scope of read and write to repos to authorize quality gate to automatically contribute to PR). Renew the PAT every month (for example) is really painful (because you must renew the PAT and you must update its value in the connected service). Is there a solution to automatically renew the PAT and being notified by Azure DevOps for that?
Hi Micaël,
We recently released a new API for managing the lifecyle of Personal Access Tokens (PATs). One of the primary scenarios is setting up automated pipelines for rotating soon-to-be-expired PAT tokens being used within your apps. Check out the blog post here.
Thanks,
Parsa
Hello, we don’t see this options in the Azure Active Directory tab.
Is it enabled for everyone ?
Hi Laurent,
This feature is still being rolled out to all customers. You will see it in the next two weeks if you do not see it already.
Thanks,
Parsa
Hi Parsa, it is four weeks later, and we still do not see the feature in our Azure DevOps organisation.
Willy
Hi Willy,
The new policies are still being rolled out to all customers. If the policies are not yet available for your organization, you can expect them before August 9th, 2021. I apologize for the delay and sincerely thank you for your patience!
Thanks Parsa, we will wait then 🙂