In April of this year, we completed a major project to archive older versions of our content.
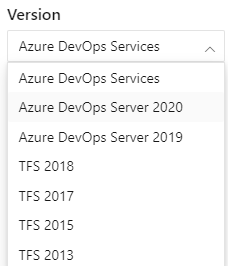
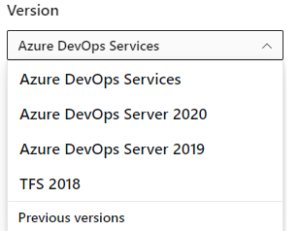
For several years now, we’ve supported content for all Azure DevOps versions. These versions included TFS 2013 through Azure DevOps Services. Users viewed the content for their versions through the content version selector. In April, the content version selector changed as shown.
| Content version selector prior to April 2022 | Content version selector post April 2022 |
|---|---|
 |
 |
Why do we archive content?
There are several reasons why we archive content.
- Improve search results for currently supported versions
- Cut down on the Reading time estimated for articles that maintain multiple versions
- Reduce potential confusion around article selection and the installed version.
What content is archived?
What happened to TFS 2013, TFS 2015, and TFS 2017?
We moved content for older versions to our archive site. You can access this site through the Previous versions link in the content selector. Or, through this link: Azure DevOps previous versions documentation.
The archive documentation site contains content for older versions, as well as content that addresses the following elements:
- Deprecated cloud content, content that is no longer relevant for use with Azure DevOps Services
- Legacy feature content, such as the SQL Server Reporting Services content that has been replaced by the Analytics service
- Deprecated feature content, content that addresses features that were deprecated with a previous version of Azure DevOps
- Release notes from 2012 through 2017.
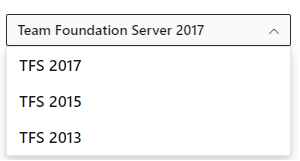
Archived content selector
When you go to the archive content site, the default view is set to TFS 2017. To access content for a previous version, use the content version selector to select the version of interest.
Additional resources

Azure uses kubernetes, which uses a secret file to get the password, that’s not secure. It should be redesigned and use our service to make the kubectl program to have the capabilities to combat software-based attacks, such as strace/pbftrace/dtrace/systemtap/uprobe/kprobe/TTY keylogger/memory snooper.