Last year, GitHub released code scanning, which enables developers to incorporate security checks into their CI/CD environment and developer workflow. This post demonstrates the basics of using CodeQL, the analysis engine behind code scanning, with GitHub Actions.
What is CodeQL?
CodeQL is an analysis engine that automates security checks by running queries against a database generated from your codebase. This CodeQL database is created during the build process and represents the source code in relational form. By default, code scanning runs standard CodeQL queries written by GitHub researchers and the community, but you can also author your own custom queries.
The default set includes queries such as “Pointer overflow check”, “Potentially overflowing call to snprintf”, “Uncontrolled format string”, and more.
Setting up CodeQL with GitHub Actions
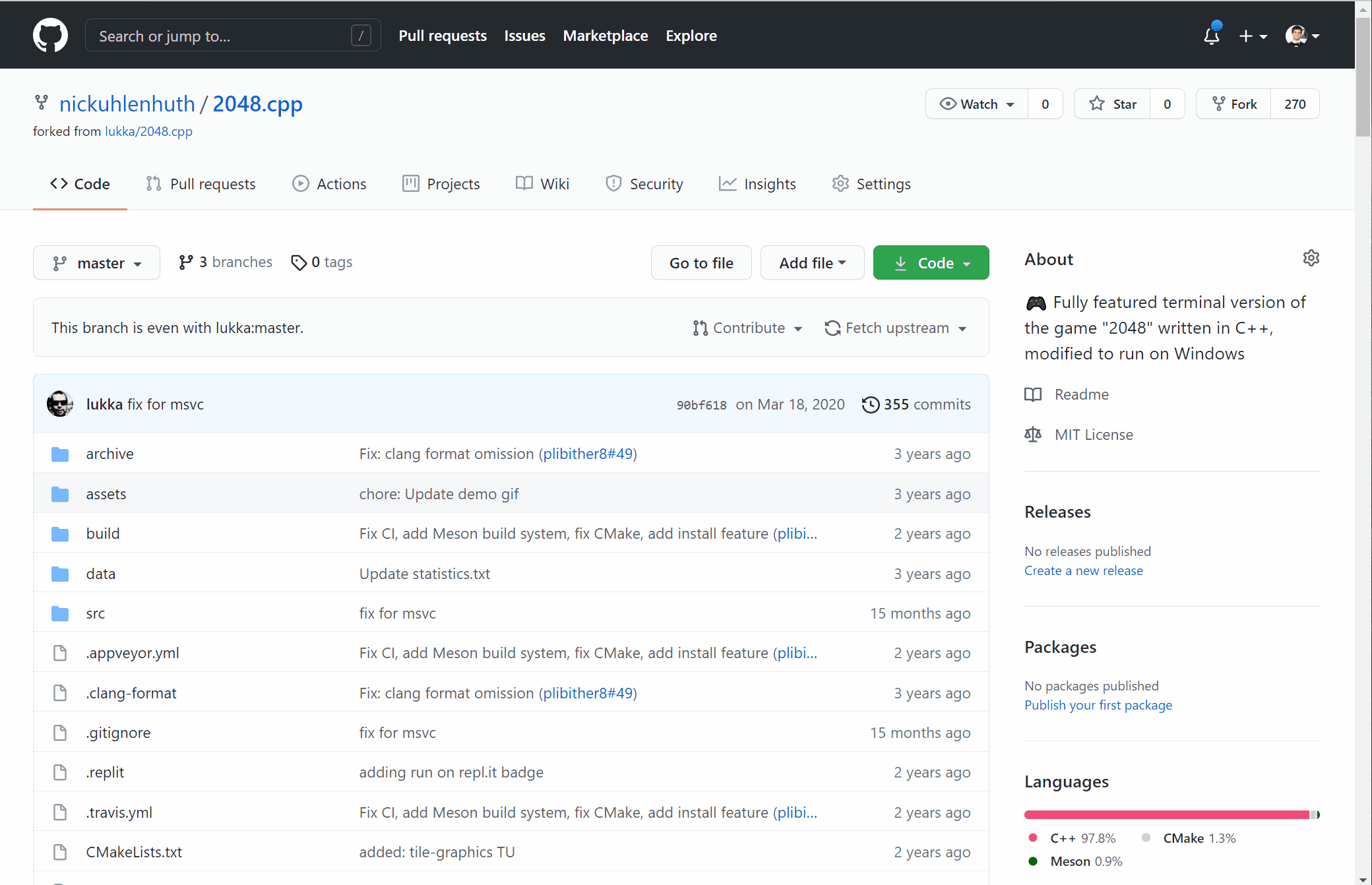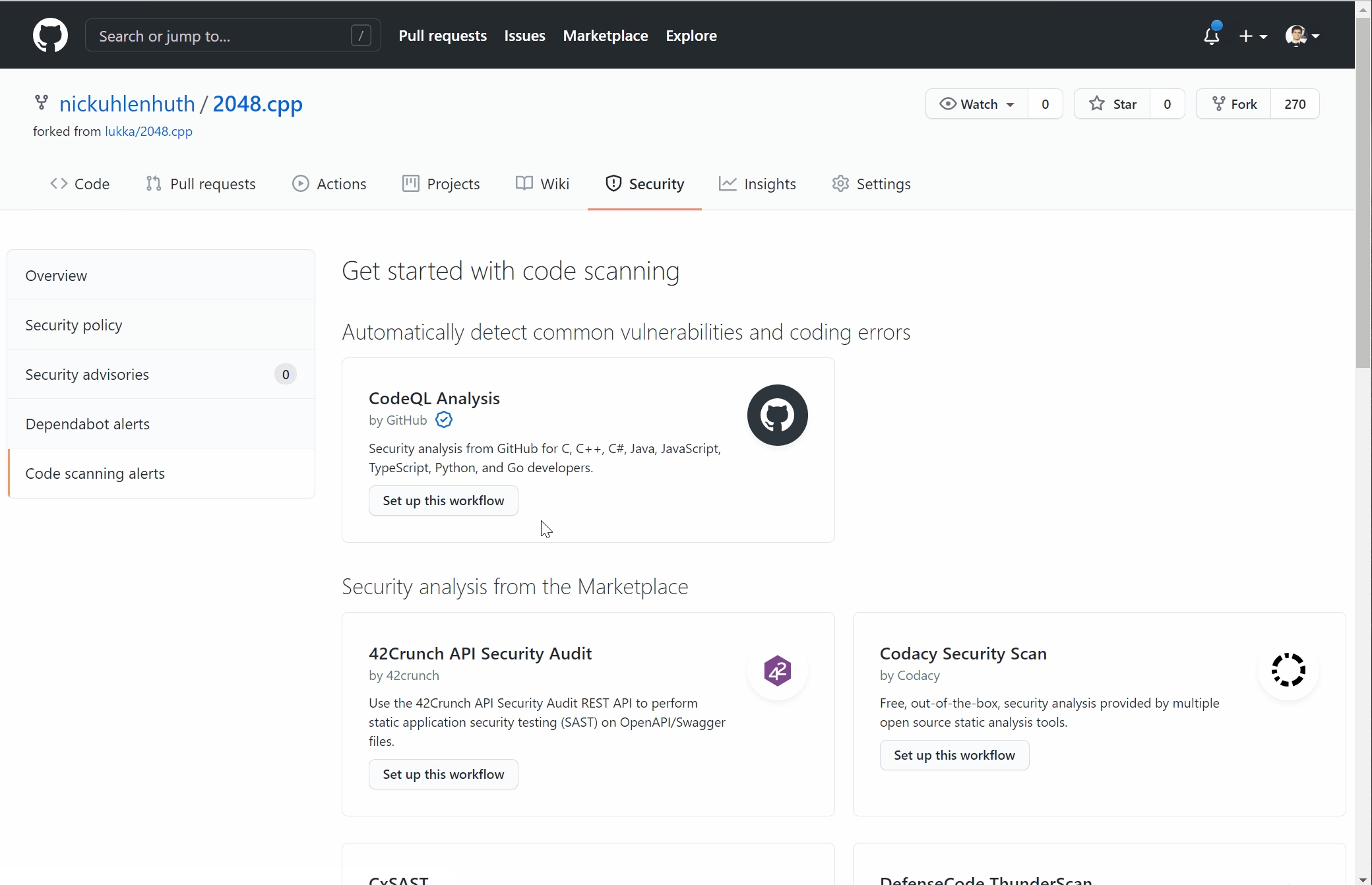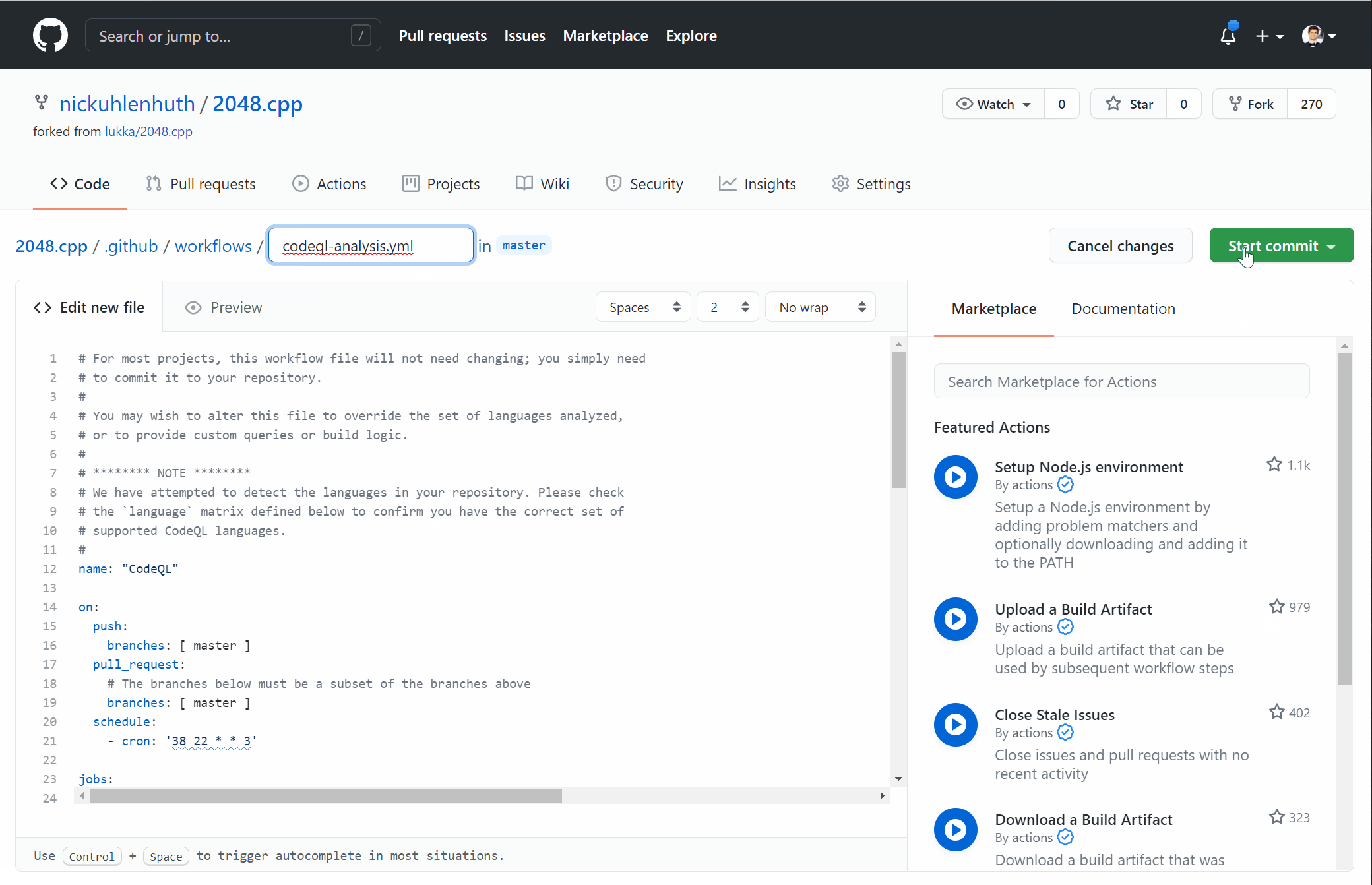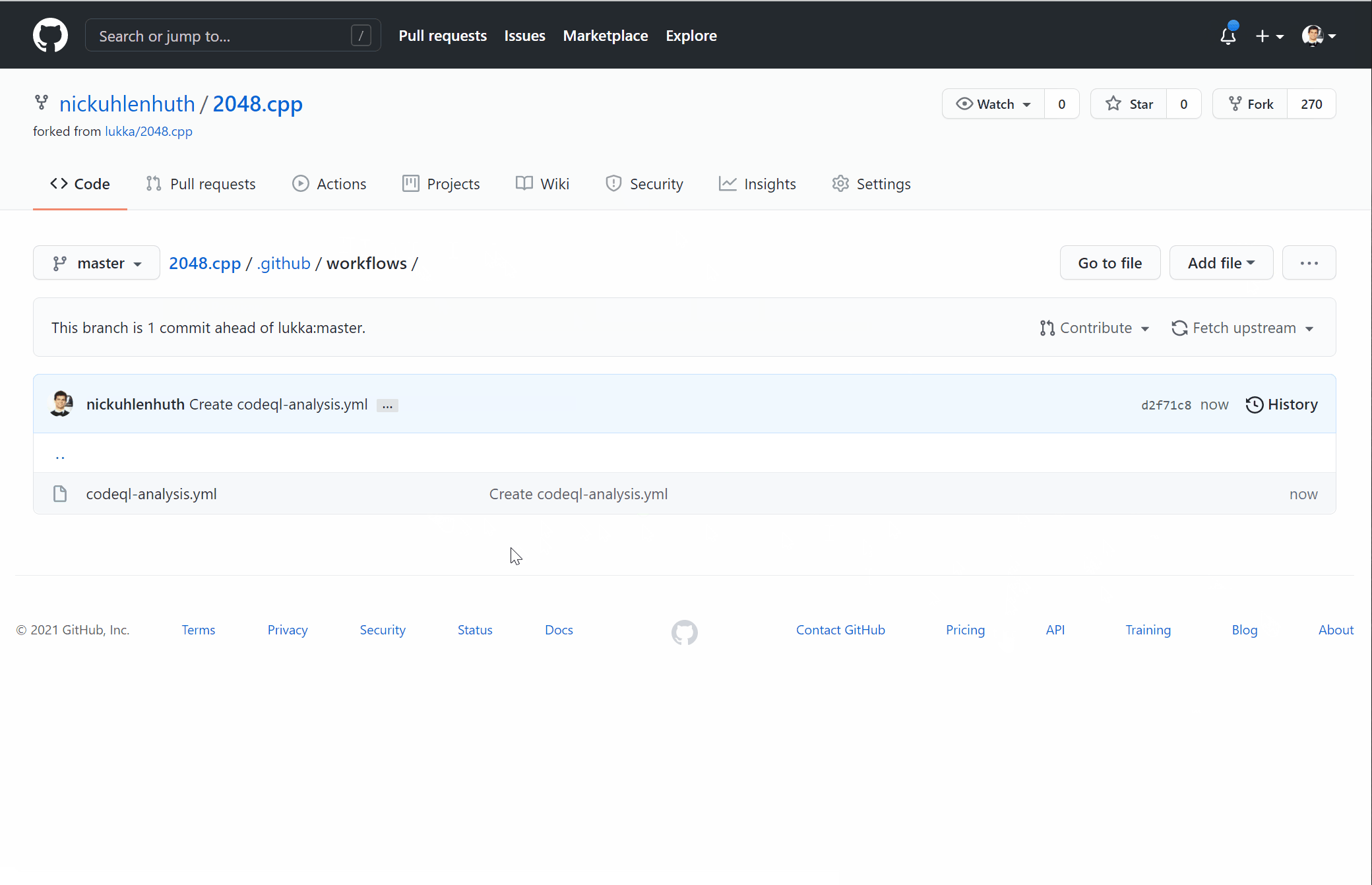
Code scanning with CodeQL is free for public repositories, and is part of GitHub Advanced Security for GitHub Enterprise. Here are instructions for the quick, 4-click setup process. Alternatively, I’ve included a gif of the steps below:
And just like that, you’re off to the races! The default CodeQL analysis workflow is configured to analyze your code each time you push a chance or raise a pull request against the default branch. This means code scanning automatically happened after I committed the new file directly to the main branch.
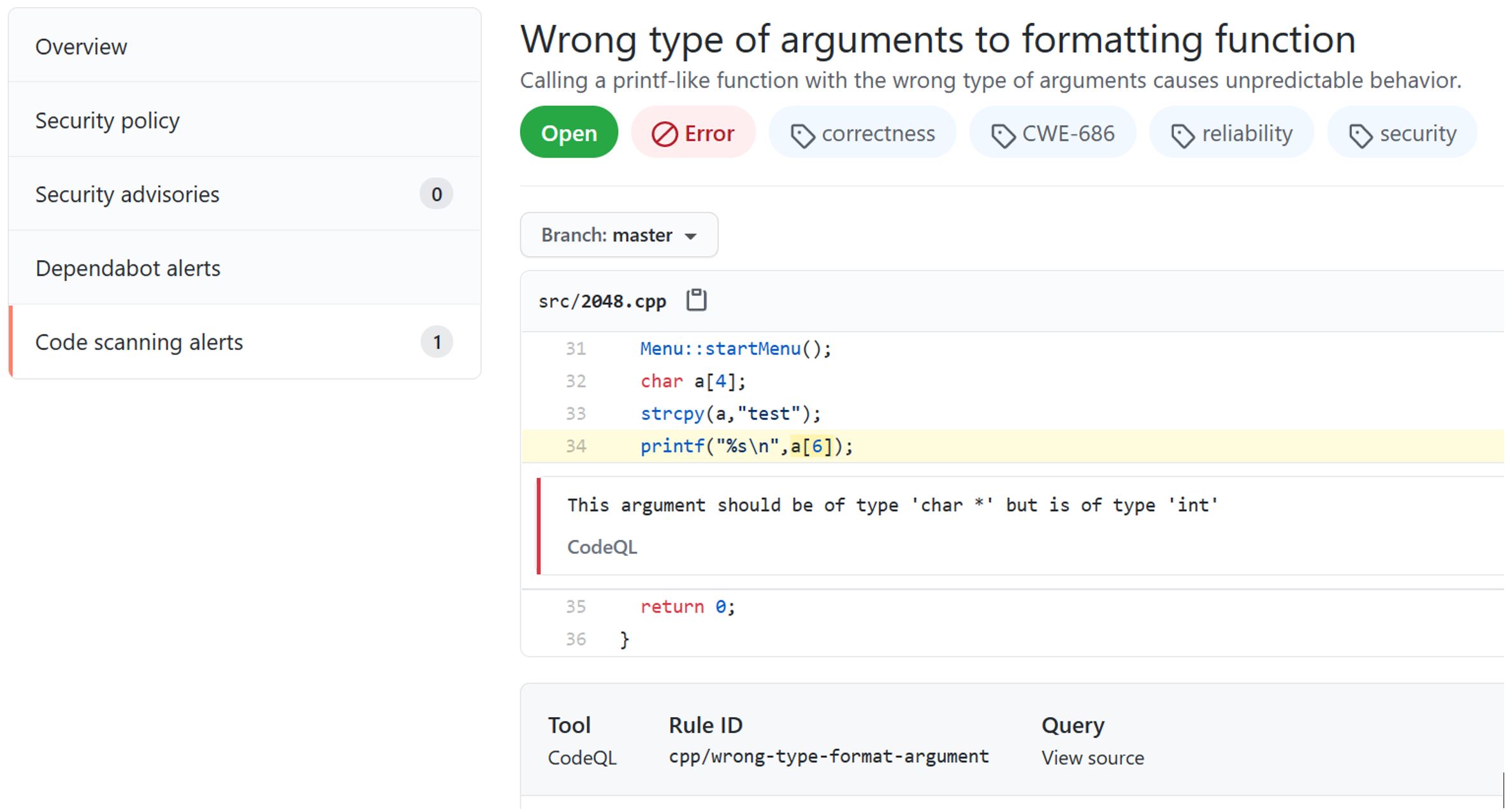
You can view the logging output of the scan under the Actions tab, and you can view/manage any code scanning alerts under the Security tab.
Baselining
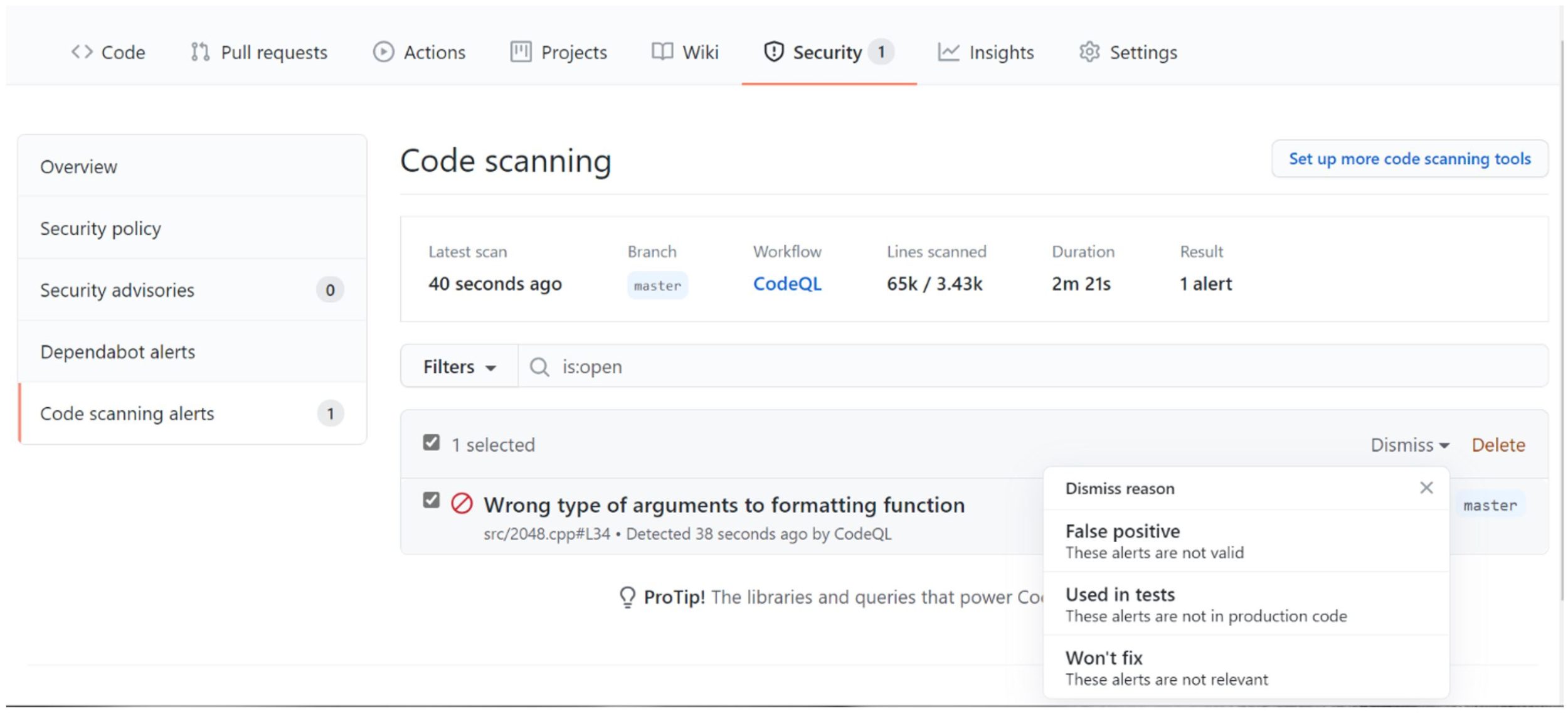
Sometimes, especially for large legacy codebases, the number of alerts can be overwhelming. For that reason, CodeQL only shows new/fixed alerts in pull requests. If you want to manage existing alerts, you can do so in the “Code scanning alerts” section under the “Security” tab.
It’s important to understand the distinction between Dismiss and Delete. One key distinction is that by Dismissing an alert, the same code won’t regenerate the alert. By Deleting an alert, the same code will generate the same alert the next time it is scanned. In the case that you want to bulk-dismiss alerts, you can do this from the summary of alerts (after filtering the list to whatever set of alerts you’d like to dismiss).
Feedback
This post just scratches the surface of code scanning in your CI/CD environment. Once you get the understand the basics, you may choose to author your own custom CodeQL queries or adjust the frequency of scanning. We hope you give code scanning with GitHub Actions a try, and we look forward to your feedback.

Thanks for the article!
Do you have an example repository with a C++ application?
Is it possible to run this check against MSVC project? or only CMake-based projects are supported?
Both are supported. Here is the full list: https://codeql.github.com/docs/codeql-overview/supported-languages-and-frameworks/