Today, we are thrilled to announce the public preview of data encryption at rest with customer managed keys for Azure Cosmos DB for PostgreSQL.
Data stored in your Azure Cosmos DB for PostgreSQL cluster is automatically and seamlessly encrypted with keys managed by Microsoft (service-managed keys). Optionally, you can now choose to add an additional layer of security by enabling encryption with customer-managed keys. Many organizations require full control of access to the data using a customer-managed key. Data encryption with customer-managed keys for Azure Cosmos DB for PostgreSQL enables you to bring your own key to protect data at rest. It also allows organizations to implement separation of duties in the management of keys and data. With customer-managed encryption, you’re responsible for, and in full control of, a key’s lifecycle, key usage permissions, and auditing of operations on keys. Data encryption with customer-managed keys for Azure Cosmos DB for PostgreSQL is set at the server level. Data, including backups, is encrypted on disk, including the temporary files created while running queries.
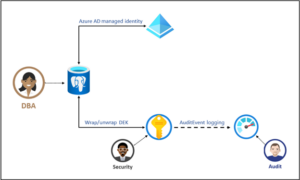
How does Microsoft Azure encrypt data at rest using Customer Managed Keys
At the most basic level, the data on disk is encrypted with an Azure internal key referred to as the Data Encryption Key (DEK). For a given cluster, a customer-managed key, called the Key Encryption Key (KEK), is used to encrypt the service’s DEK. The KEK is an asymmetric key stored in a customer-owned and customer-managed Azure Key Vault instance. A KEK that never leaves Key Vault allows the DEKs themselves to be encrypted and controlled. The entity that has access to the KEK might be different from the entity that requires the DEK. Since the KEK is required to decrypt the DEKs, the KEK is effectively a single point by which DEKs can be effectively deleted by deletion of the KEK.
Benefits:
- Full control of data access via the ability to remove the key and make the database inaccessible.
- Full control over the key lifecycle, including rotation of the key to align with corporate policies.
- Central management and organization of keys in Azure Key Vault
- The ability to implement separation of duties between security officers, DBA, and system administrators.
To enable and configure data encryption using CMK follow these steps:
*Note: Create all the following resources in the same region where your Azure Cosmos DB for PostgreSQL cluster will be deployed.
- Create a User-Assigned Managed Identity. Currently, Azure Cosmos DB for PostgreSQL only supports user-assigned managed identities.
- Create an Azure Key Vault and add an access policy to the created User-Assigned Managed Identity with the following key permissions: Get, Unwrap Key, and Wrap Key.
- Generate a Key in the Key Vault (supported key types: RSA 2048, 3071, 4096).
- Select the Customer-Managed Key encryption option during the creation of the Azure Cosmos DB for PostgreSQL cluster and select the appropriate User-Assigned Managed Identity, Key Vault, and Key created in Steps 1, 2, and 3.
Next Steps:
- Overview of Data encryption at rest using customer managed keys.
- Enable data encryption with customer managed keys.


0 comments