By
Jason Henderson, Cloud Solutions Architect
Kyle Hoyer, Technical Solutions Professional
Derek Strausbaugh, Principal Program Manager, Azure Global
A rapidly increasing number of DoD customers deploying IaaS workloads to Azure have been asking for guidance setting up secure virtual networks and configuring the security tools and services stipulated by DoD standards and practice. DISA published the Secure Cloud Computing Architecture (SCCA) in 2017. SCCA describes the functional objectives for securing the Defense Information System Network’s (DISN) and Commercial Cloud Provider connection points and also how mission owners secure cloud applications at the connection boundary.
There are four components to the SCCA, the Boundary Cloud Access Point (BCAP), Virtual Datacenter Security Stack (VDSS), Virtual Datacenter Services (VDMS), and Trusted Cloud Credential Manager (TCCM).
Microsoft has developed a solution that runs on Azure and will meet the SCCA requirements. This Azure specific solution is called Secure Azure Computing Architecture (SACA). In developing the first iteration of SACA, we partnered with F5. F5 solutions are widely deployed throughout DoD and their virtual appliances for Azure provide a number of security capabilities required in the SCCA guidance. Our guiding principle in working with F5 was to develop an architecture that meets every function objective of SCCA for IaaS workloads on Azure. This blog explains the architecture, links to the F5 documentation that maps requirements to their services, and provides the Azure Resource Template that automates the deployment of the solution.
This architecture and automation template is not turnkey – every DoD customer will have requirements unique to their environment (i.e. log handling and configuration). However, we are willing to work with customers to work through their specific needs and evolve this architecture as necessary. For example, this first iteration of our solution uses F5 virtual appliances but it is not required that you use F5 to support the SCCA guidance.
Before diving into the architecture, let’s quickly describe the components of SCCA in more detail.
BCAP
The purpose of the BCAP is to protect the DISN from attacks originating in the cloud environment. BCAP will perform intrusion detection and prevention as well as filter out unauthorized traffic. This component can be co-located with other components of the SCCA.
VDSS
The purpose of the VDSS is to protect DoD Mission Owner applications that are hosted in Azure. VDSS performs the bulk of the security operations in the SCCA. It will conduct traffic inspection in order to secure the applications running in Azure. This component can be provided within your Azure environment.
VDMS
The purpose of VDMS is to provide host security as well as shared data center services. The functions of VDMS can either run in the hub of your SCCA or the mission owner can deploy pieces of it in their own specific Azure subscription. This component can be provided within your Azure environment.
TCCM
TCCM is a business role. This individual will be responsible for managing the SCCA. Their duties include establishing plans and policies for account access to the cloud environment, ensuring identity and access management is operating properly, and to maintain the Cloud Credential Management Plan. This individual is appointed by the Authorizing Official. The BCAP, VDSS, and VDMS will provide the capabilities needed for the TCCM to perform their job function.
Mapping SCCA to Azure and F5 Capabilities
The following tables illustrate the mapping of native Azure services and capabilities of F5’s virtual appliance to the SCCA guidance for BCAP, VDSS and VDMS.
| BCAP | ||||
| Requirement | Azure | F5 | Windows Service | 3rd Party |
| 2.1.1.1.1 | ASM | |||
| 2.1.1.1.2 | ASM and AFM | |||
| 2.1.1.1.3 | ASM | |||
| 2.1.1.1.4 | ASM | |||
| 2.1.1.1.5 | APM | |||
| 2.1.1.1.6 | AFM | |||
| 2.1.1.1.7 | Owner’s Choice | |||
| 2.1.1.1.8 | ASM | |||
| 2.1.1.1.9 | ASM | |||
| 2.1.1.1.10 | APM and AFM | |||
| 2.1.1.1.11 | TMOS and Core | |||
| 2.1.1.1.12 | TMOS and Core | |||
| 2.1.1.1.13 | ASM | |||
| VDSS | ||||
| Requirement | Azure | F5 | Windows Service | 3rd Party |
| 2.1.2.1 | Virtual Networks/Subnets | LTM | ||
| 2.1.2.2 | RDP w/TLS | LTM | ||
| 2.1.2.3 | LTM | |||
| 2.1.2.4 | ASM | |||
| 2.1.2.5 | ASM | |||
| 2.1.2.6 | ASM | |||
| 2.1.2.7 | ASM | |||
| 2.1.2.8 | LTM and ASM | |||
| 2.1.2.9 | LTM and APM | |||
| 2.1.2.10 | APM and AFM | |||
| 2.1.2.11 | LTM | |||
| 2.1.2.12 | TMOS and Core | |||
| 2.1.2.13 | Key Vault | LTM | ||
| 2.1.2.14 | ASM | |||
| 2.1.2.15 | LTM | |||
| 2.1.2.16 | LTM | |||
| 2.1.2.17 | LTM | |||
| 2.1.2.18 | LTM | |||
| VDMS | ||||
| Requirement | Azure | F5 | Windows Service | 3rd Party |
| 2.1.3.1 | ACAS/Owner’s Choice | |||
| 2.1.3.2 | HBSS/Owner’s Choice | |||
| 2.1.3.3 | Active Directory Federation Services | APM | Owner’s Choice | |
| 2.1.3.4 | Azure PowerShell | BIG-IQ | WSUS | |
| 2.1.3.5 | APM and BIP-IP DNS | Windows DNS and DHCP | ||
| 2.1.3.6 | Virtual Networks/Subnets | LTM and APM | ||
| 2.1.3.7 | TMOS and Core | Owner’s Choice | ||
| 2.1.3.8 | Azure AD/ADFS | APM | ||
| 2.1.3.9 | APM | |||
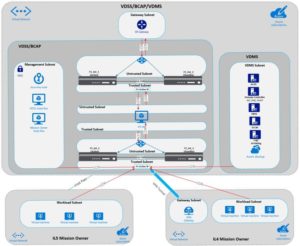
Architecture Overview
The following diagram illustrates the reference architecture for deploying the services and appliances outlined in the solution.
Solution Template
The template deployment below will only Deploy the VDSS, BCAP, and VDMS components seen in the top box of the diagram. The Mission Owner environments will not be deployed as part of this template. There are additional scripts for deploying and attaching a mission owner in IL5, IL4, and a different cloud vendor mission owner.
Full Azure Infrastructure and F5 Deployment Resources
The link below will take you to the F5 documentation explaining our SCCA on Azure solution from an F5 perspective.
http://f5-azure-scca.readthedocs.io/en/latest/index.html
After the deployment has finished, the system administrator will need to deploy HBSS, ACAS, and any other tools that are specific to your environment.
The last step is to attach Mission Owners to your Secure Azure Computing Architecture. Microsoft has developed scripts to automate the onboarding of Mission Owners. We are willing to work with your organization to tailor these scripts to your specific needs. Please reach out to Azure SCCA if you are a DoD customer interested in deploying our solution.
Learn More About Azure Government
Microsoft is committed to providing the most trusted, comprehensive cloud for mission-critical workloads so that our nearly 6 million government users across 7,000-plus federal, state, and local organizations can achieve more in carrying out their mission-critical workloads.
We welcome your comments and suggestions to help us continually improve your Azure Government experience. To stay up to date on all things Azure Government, click “Subscribe by Email!” on the Azure Government Blog. To explore Azure Government, request your free 90-day trial today. Or, check out purchasing options to get started now.

readthedocs.io link is broken