This blog is authored by members of Microsoft’s Government Cybersecurity, Azure Global Critical Infrastructure team: Michele Myauo, Principal Engineering Manager; Adam Dimopoulos, Senior Program Manager; and Shawn Gibbs, Senior Program Manager.
At Microsoft, our security and compliance story is one of our greatest differentiators. Microsoft recognizes the criticality of security compliance accreditations for Defense Industrial Base (DIB) and Department of Defense (DoD) customers. Maintaining Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) compliance is critical and often time consuming. STIGs are secure configuration standards for installation and maintenance of DoD Information Assurance (IA) and IA-enabled devices and systems. Azure provides automation and compliance dashboarding capabilities at cloud speed and scale, allowing customers to reduce the heavy costs of compliance when they choose Azure.
The Azure Team has created sample solutions using first-party Azure tooling to deliver STIG automation and compliance reporting. The STIG Automation GitHub Repository, enables customers to: Automate STIG implementation and baseline updates with Azure Image Builder Visualize compliance with Azure Monitor Log Analytics or Sentinel
Available for use with Azure commercial today and coming soon to Azure Government, here’s a summary of current resources to help get you started:
STIG automation architecture
With our STIG Automation GitHub Repository, customers can build STIG images and automate baseline updates as new versions of STIGs are released quarterly. The overall architecture uses a set of resources deployed via nested Azure Resource Manager (ARM) templates from this repository. The result is an automated virtual machine image creation via Azure Image Builder and final STIG’d images stored in the resource groups shared Azure Image Gallery for use in that Azure subscription.
Currently supported operating systems:
- Windows 10 RS5 Enterprise/Enterprise multi-session/Professional
- Windows 2019
- Windows 2016
STIG Automation Architecture
More specifically, automation creates a resource group that plays host to the required components to create, store and audit images as they are used. During deployment, several image templates will be uploaded representing how to make a STIG’d image. Once images are created, they can then be used in other automation templates or scripts. In addition to images in the shared Azure Image Gallery the Windows 10, 2019 and 2016 templates create Azure Virtual Hard Disk (VHDs) that can then be used or downloaded as needed. Azure Image Builder will also create resource groups that house the components used for creating images and this is where the Azure VHD files are stored until you move them.
The PowerSTIG Desired State Configuration (DSC) audit information for each image is automatically logged and reported to an Azure Log Analytics Workspace, and an Azure Sentinel Workbook is included with the deployment to visualize the data. If desired, this workbook can be removed or replaced with any other Log Analytics or Sentinel Workbook, by simply pointing new or existing queries to the Log Analytics Workspace included in the STIG automation deployment. PowerSTIG is an open-source GitHub project being actively supported.
Azure Image Builder
Azure Image Builder let’s you start with a Windows or Linux-based Azure Marketplace image and begin to add your own customizations. Because the Image Builder is built on HashiCorp Packer, you can also import your existing Packer shell provisioner scripts. Additionally, you can specify where you would like your images to be hosted; in the Azure Shared Image Gallery as a managed image or VHD.
Standardized virtual machine (VM) images allow organizations to migrate to the cloud and ensure consistency in the deployments. Images typically include predefined security and configuration settings, as well as necessary software. Setting up your own imaging pipeline requires time, infrastructure, and configuration. But with Azure VM Image Builder, just provide a simple configuration describing your image, submit it to the service, and the image is subsequently built and distributed. Note: Azure Image Builder is available in Public Preview in Azure commercial.
Azure Monitor Log Analytics
Azure Monitor collects monitoring telemetry from a variety of on-premises and Azure sources. Management tools, such as those in Azure Security Center and Azure Automation, also push log data to Azure Monitor. The service aggregates and stores this telemetry in a log data store that’s optimized for cost and performance. Analyze data, set up alerts, get end-to-end views of your applications, and use machine learning–driven insights to quickly identify and resolve problems.
Log Analytics is a tool in the Azure portal used to edit and run log queries with data in Azure Monitor Logs. You may write a simple query that returns a set of records and then use features of Log Analytics to sort, filter, and analyze them. Or you may write a more advanced query to perform statistical analysis and visualize the results in a chart to identify a particular trend. Whether you work with the results of your queries interactively or use them with other Azure Monitor features such as log query alerts or workbooks, Log Analytics is the tool that you’re going to use write and test them.
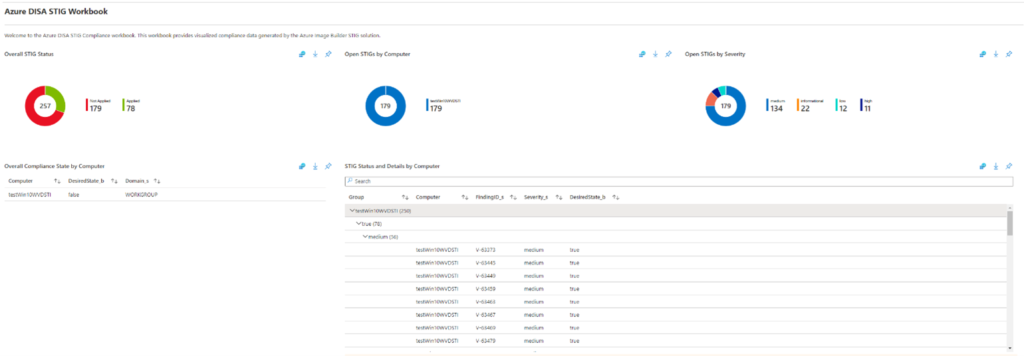
With the automation, your Azure Log Analytics Dashboard shows your current projected STIG compliance score, helps you see what needs attention, and guides you to key improvement actions. Below is an example of what your Azure Log Analytics dashboard will look like:
Note: The Azure Monitor Log Analytics dashboard is a projection of your organization’s STIG compliance profile based on all available information to date—Microsoft is not an accrediting body for STIGs, and thus cannot guarantee any outcome under the formal STIG review process.
Azure Sentinel
Azure Sentinel is a cloud-native security information and event manager (SIEM) platform that uses built-in artificial intelligence (AI) to help analyze large volumes of data across an enterprise—fast. Azure Sentinel aggregates data from all sources, including users, applications, servers, and devices running on-premises or in any cloud, letting you reason over millions of records in a few seconds. It includes built-in connectors for easy onboarding of popular security solutions. Collect data from any source with support for open standard formats like CEF and Syslog.
See and stop threats before they cause harm, with SIEM reinvented for the modern world. Azure Sentinel is your birds-eye view across the enterprise. Put the cloud and large-scale intelligence from decades of Microsoft security experience to work. Make your threat detection and response smarter and faster with artificial intelligence (AI). Eliminate security infrastructure setup and maintenance, and elastically scale to meet your security needs—while reducing IT costs.
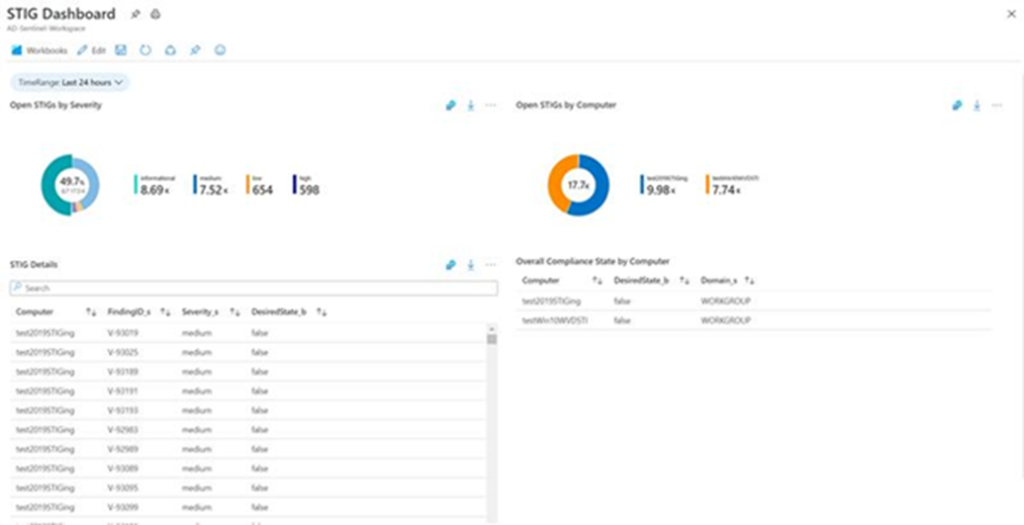
With the automation, your Azure Sentinel STIG Dashboard shows your current projected STIG compliance score, helps you see what needs attention, and guides you to key improvement actions. Below is an example of what your Azure Sentinel dashboard will look like:
Note: The Azure Sentinel dashboard is a projection of your organization’s STIG compliance profile based on all available information to date—Microsoft is not an accrediting body for STIGs, and thus cannot guarantee any outcome under the formal STIG review process.
Microsoft is actively building out additional STIG resources for Defense Industrial Base (DIB) companies and the Department of Defense (DoD) to use in their STIG journey. These tools cannot guarantee a positive STIG adjudication, but they may assist organizations by improving their STIG posture going into a formal STIG review in accordance with accreditation body standards. Get started by visiting our STIG Automation GitHub Repository


0 comments