In support of National Cyber Security Awareness Month, sponsored by the Department of Homeland Security, we’re kicking off a blog series to share best practices from our experiences with our customers as part of our commitment to enabling U.S. government with a complete, trusted, and secure cloud platform.
In today’s guest blog, Ann Johnson, Microsoft Vice President, Strategic, Enterprise, & Cybersecurity (SEC), shares some historical context into the challenges of security management, providing insights into how the capabilities of the cloud changes the game for security management.
We also invite you to join us for some of the great events coming to Washington, DC in October:
- Oct. 17 – Microsoft Government Cloud Forum: spend a day diving into how government agencies are using technology to transform and improve their operations, solving such challenges as IT modernization, Cybersecurity, Mobility, Shared services, Citizen engagement, and more.
- Oct. 18 – CyberScoop CyberTalks: a full-day event featuring top government and industry cybersecurity experts including Microsoft Azure CTO Mark Russinovich.
- Oct. 18 – Microsoft Azure Government DC Meetup: an evening special-edition Azure Gov Meetup on “The Intersection of Cybersecurity & Digital Transformation for Gov” featuring Mark Russinovich and a panel of security experts moderated by Federal News Radio’s Jason Miller.
Security Management: From Holy Grail to Holy Mess and Back Again
Ann Johnson, Microsoft Vice President, Strategic, Enterprise, & Cybersecurity (SEC)
Security Management is a term I hear frequently from customers as an area of concern. They own multiple tools, and each tool comes with a new management interface or dashboard. Organizations are unable to hire the quantity and quality of security professionals they need to manage their increasingly complex environments, and with each new highly visible breach or compromise, the pressure on security organizations grows exponentially. The need for unified security management, automation and orchestration has never been greater. Yet, it remains one of the most challenging problems in security due to technical debt and legacy solutions.
This leaves most enterprises a disquieting paradox. The more security products they purchase the less secure they become. With each new product there is yet another control point-making security administration more error prone and less effective.
Aggregation and the Advent of a Single Pane of Glass
For a while, it seemed the problem would be solved by aggregating security functions into single product instances or appliances. You might remember universal threat management (UTM), which brought together network access control, intrusion prevention, anti-virus etc. The theory was that by daisy-chaining core security functions in a single product, management could be unified under one policy framework. As organizations became global and mobile devices ubiquitous, we layered more complex security functions on these instances and single line rules became thousands of lines of do-not-touch-lest-something-stop-working security policy.
This ushered in the ‘single pane of glass’ era. You may be groaning at the hackneyed phrase but at first introduction it had instant resonance. The security manager, like a 911 emergency call operator, was at last in control using a correlated view of the security environment with graphs that warned of possible attacker paths and heat maps that glowed red with guidance on high priority items. It was an administrative scheme driven by use cases rather than by policy editor.
This was the holy grail of security management, and it would be delivered by solutions that aggregated information from different types of products through connectors or plug-ins. Administrators where thrilled at the prospect and more than a few vendors delivered solid offerings. Over time, though, these solutions became encumbered by the need to support a highly-fragmented security vendor ecosystem that was adding new categories every year.
Made Workable by the Cloud
Now we are again talking about single panes of glass and security administration as the first and best way to reduce security risk. This time, however, the approach is built on the cloud. By leveraging some of the unique capabilities of our cloud architecture, which offers a flexible, extensible platform with built-in intelligence, we have the potential to make a truly significant step change in security management.
Previous approaches failed largely due to trying to unify best of breed products with little meaningful integration into a single management construct. In modern security architecture, the cloud provides a unifying framework which enables integration into a single management construct.
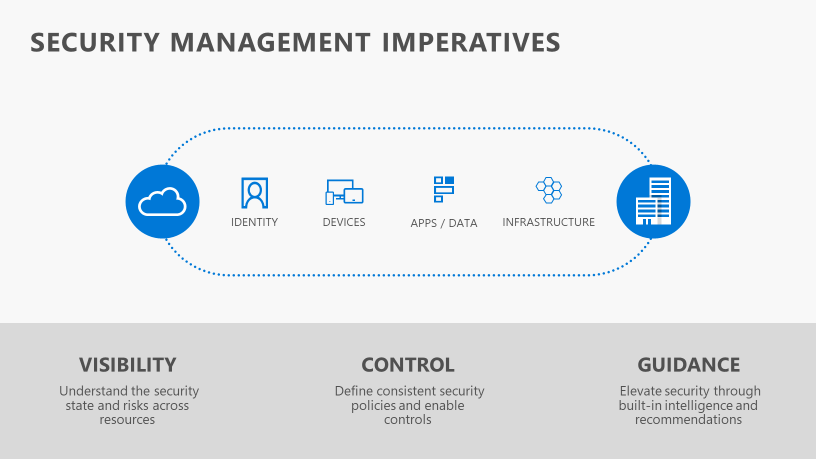
This is the key to success in managing security-integration wherever it makes sense. When comprehensive in coverage, the single pane of glass can provide the visibility, control, and guidance necessary for effective security management.
Example: Azure Security Center
Consider for instance what Microsoft has delivered with Azure Security Center (ASC). Harnessing the power of machine learning, ASC provides guidance and prioritized recommendations helping to strengthen the security posture of infrastructure. ASC monitors networks, machines, and cloud services for incoming attacks and post-breach activity, and streamlines investigation with interactive tools and contextual threat intelligence.
To help administrators assess their current state, ASC provides visibility into machines with missing security updates, insecure OS configurations, or insufficient malware protection, as well as vulnerable Azure virtual network, storage, database, and application configurations.
In addition, recommended security baselines for different roles help administrators ensure servers and VMs are secure and fully hardened. These baselines include sets of registry keys, audit policy settings, and security policy settings along with Microsoft’s recommended values for these settings, which help administrators quickly assess and improve compliance.
Simplified & Intelligent Security Management
In fact, Microsoft takes a similar approach in administering the security of identity, devices, applications, and data as it does with infrastructure. Each management “center” gives holistic views, security posture scoring (or guidance) and discrete actions that can reduce risk and help maintain a desired security baseline and compliance state.

Underpinning each management component is the intelligent security graph, a vast framework of threat and network intelligence providing contextualized insight not only to the location of threats, but also to the fastest way to mitigate them.
Taken together, Azure Active Directory, Windows Defender Security Center, Office 365 Security and Compliance Center and Azure Security Center are the modern implementation of single pane of glass for security management. They are at once commonly threaded by Azure and shared intelligence while providing the specialized views that each type of security and security operations administrator requires.
Most importantly this is a modular and scalable approach; an imperative given the certainty security functionality and administrative roles will evolve. As they do, security management should not become the weakest link but rather the lever by which incremental security investment pays off.
Additional Azure Government resources:
- To experience the power of Azure Government for your organization, sign up for an Azure Government Trial.
- For all things related security, privacy, transparency, and compliance, check out the Microsoft Trust Center.
- We welcome your comments and suggestions to help us improve your Azure Government experience. To stay up to date on all things Azure Government, be sure to subscribe to our RSS feed and to receive emails by clicking “Subscribe by Email!” on the Azure Government Blog.

0 comments