Azure is a hyperscale public multi-tenant cloud services platform that provides customers with access to a feature-rich environment incorporating the latest cloud innovations. While a multi-tenant cloud platform implies that multiple customer applications and data are stored on the same physical hardware, Azure uses logical isolation to segregate each customer’s applications and data. This approach provides the scale and economic benefits of multi-tenant cloud services while rigorously helping prevent customers from accessing one another’s data or applications.
To provide customers with more detailed information about isolation in a multi-tenant cloud, Microsoft has published Azure guidance for secure isolation which provides technical guidance to addresses common security and isolation concerns pertinent to cloud adoption. It also explores design principles and technologies available in Azure to help customers achieve their secure isolation objectives using the following multi-layered approach:
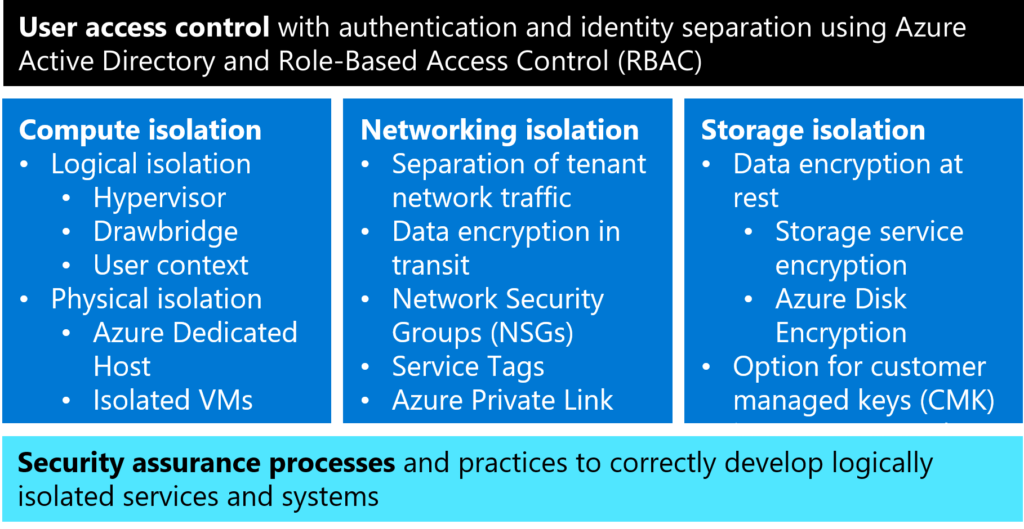
Here’s a summary of isolation approaches:
User access controls with authentication and identity separation
All data in Azure irrespective of the type or storage location is associated with a subscription. A cloud tenant can be viewed as a dedicated instance of Azure Active Directory (Azure AD) that customer organization receives and owns when they sign up for a Microsoft cloud service. The identity and access stack helps enforce isolation among subscriptions, including limiting access to resources within a subscription only to authorized users.
Compute isolation
Azure provides customers with both logical and physical compute isolation for processing. Logical isolation is implemented via:
- Hypervisor isolation for services that provide cryptographically certain isolation by using separate virtual machines and leveraging Azure Hypervisor isolation.
- Drawbridge isolation inside a Virtual Machine (VM) for services that provide cryptographically certain isolation for workloads running on the same virtual machine by leveraging isolation provided by Drawbridge. These services provide small units of processing using customer code.
- User context-based isolation for services that are comprised solely of Microsoft controlled code and customer code is not allowed to run.
In addition to robust logical compute isolation available by design to all Azure tenants, customers who desire physical compute isolation can utilize Azure Dedicated Host or Isolated Virtual Machines, which are deployed on server hardware dedicated to a single customer.
Networking isolation
Azure Virtual Network (VNet) helps ensure that each customer’s private network traffic is logically isolated from traffic belonging to other customers. Services can communicate using public IPs or private (VNet) IPs. Communication between customer VMs remains private within a VNet. Customers can connect their VNets via VNet peering or VPN gateways, depending on their connectivity options, including bandwidth, latency, and encryption requirements. Customers can use network security groups (NSGs) to achieve network isolation and protect their Azure resources from the Internet while accessing Azure services that have public endpoints.
Customers can use Virtual network service tags to define network access controls on network security groups or Azure Firewall. A service tag represents a group of IP address prefixes from a given Azure service. Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, thereby reducing the complexity of frequent updates to network security rules.
Moreover, customers can use Azure Private Link to access Azure PaaS services over a private endpoint in their VNet, ensuring that traffic between their VNet and the service travels across the Microsoft global backbone network, which eliminates the need to expose the service to the public Internet. Finally, Azure provides customers with options to encrypt data in transit, including Transport Layer Security (TLS) end-to-end encryption of network traffic with TLS termination using Azure Key Vault certificates, VPN encryption using IPsec, and ExpressRoute encryption using MACsec with customer-managed keys (CMK) support.
Storage isolation
To ensure cryptographic certainty of logical data isolation, Azure Storage relies on data encryption at rest using advanced algorithms with multiple ciphers. This process relies on multiple encryption keys, as well as services such as Azure Key Vault and Azure AD to ensure secure key access and centralized key management. Azure Storage Service Encryption (SSE) ensures that data is automatically encrypted before persisting it to Azure Storage and decrypted before retrieval. All data written to Azure Storage is encrypted through FIPS 140-2 validated 256-bit AES encryption and customers have the option to use Azure Key Vault for customer-managed keys (CMK). Azure SSE encrypts the page blobs that store Azure Virtual Machine disks. Additionally, Azure Disk Encryption (ADE) may optionally be used to encrypt Azure Windows and Linux IaaS Virtual Machine disks to increase storage isolation and assure cryptographic certainty of customer data stored in Azure. This encryption includes managed disks.
Security assurance processes and practices
Azure isolation assurance is further enforced by Microsoft’s internal use of the Security Development Lifecycle (SDL) and other strong security assurance processes to protect attack surfaces and mitigate threats. Microsoft has established industry leading processes and tooling that provide high confidence in the Azure isolation guarantee.
Additionally, in line with the shared responsibility model in cloud computing, the article provides customer guidance for activities that are part of customer’s responsibility. To learn more about how Azure helps customers meet secure isolation objectives, see Azure guidance for secure isolation.

Extremely helpful! THANKS