This is the fourth in a six-part blog series where we will demonstrate the application of Zero Trust concepts for securing federal information systems with Microsoft Azure. In this fourth blog of the series we will explore how to leverage Azure Policy for enforcing access control in Zero Trust models.
Additional blogs in the series will include investigating insider attacks and monitoring supply chain risk management.
This blog series is coauthored by TJ Banasik, CISSP-ISSEP, ISSAP, ISSMP, Sr. Program Manager, Azure Global Customer Engineering, Mark McIntyre, CISSP, Senior Director, Enterprise Cybersecurity Group and Adam Dimopoulos, Azure Global Customer Engineering.
How do we enforce policy for zero trust?
The Microsoft Zero Trust vision paper outlines three principles of Zero Trust- Verify Explicitly, Least Privilege Access and Assume Breach. The Zero Trust model requires strict access control to ensure every access request is authenticated, inspected and authorized within policy constraints. It’s important to evaluate the 5 W’s of each access request to determine who is requesting access, what resource is requested, when is the environment being accessed, where is the user located, why is access requested and how is the user authenticating. A central element to evaluating access is the policy enforcement point. The policy enforcement point evaluates each access request and applies respective control requirements such as Multi Factor Authentication for an access request from an unexpected location. Zero Trust requires capabilities that can make informed decisions using automated policy enforcement.
Defining Zero Trust governance based on federal frameworks
Governance definition is a critical precursor to any Zero Trust initiative. For this blog we’ve leveraged TIC 3.0 for Zero Trust access control policies and aligned with respective NIST CSF and NIST SP 800-53 controls.
- Trusted Internet Connections (TIC) is a federal cybersecurity initiative to enhance network and perimeter security across the United States federal government. The TIC initiative is a collaborative effort between the Office of Management and Budget (OMB), the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA), and the General Services Administration (GSA).[i] The TIC 3.0: Volume 3 Security Capabilities Handbook provides various security controls, applications and best practice for risk management in federal information systems.
- NIST Cybersecurity Framework. The National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework to address risks highlighted in the Cybersecurity Enhancement Act of 2014 with a goal to identify “a prioritized, flexible, repeatable, performance-based, and cost effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks.”[ii] The Framework for Improving Critical Infrastructure Cybersecurity outlines these principles.
- NIST SP 800-53 R4. This publication “provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the Nation from a diverse set of threats including hostile cyber-attacks, natural disasters, structural failures, and human errors (both intentional and unintentional).”[iii] NIST SP 800-53 Rev 4 outlines the security and privacy controls for federal information systems and organizations.
In Azure Government, we cross-reference TIC 3.0, NIST Cybersecurity Framework and NIST SP 800-53 Rev4 to align requirements for implementing Zero Trust models. Our fourth focus point is enforcing access control policy for zero trust and these documents have a wealth of information aligned to this principle. The diagram below highlights the key takeaways and requirements from the standards.
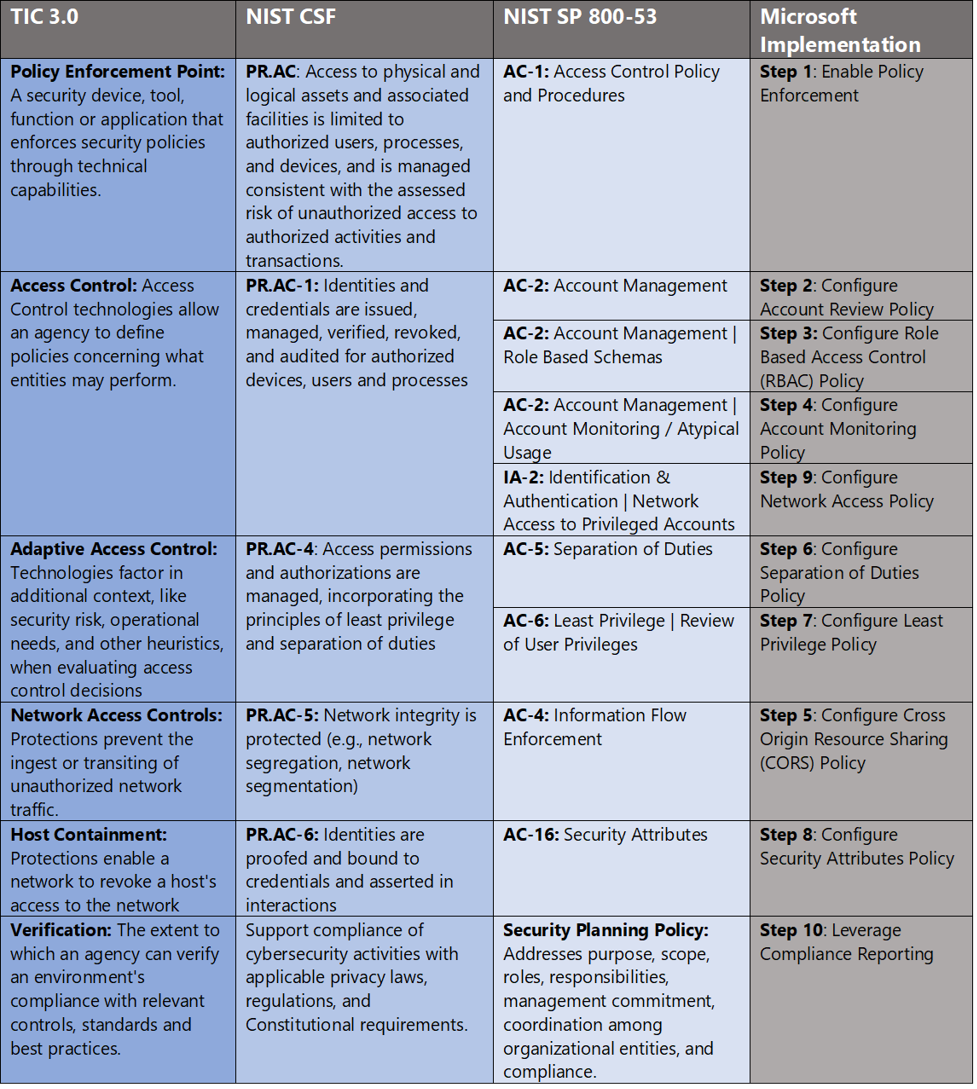
Access control policy enforcement for Zero Trust with Azure Policy
Microsoft Azure Government has developed a ten step process for enforcing access control policy in federal information systems which is aligned with the security monitoring principles within the TIC 3.0, NIST CSF, and NIST SP 800-53 standards. Azure has several offerings for policy enforcement including Azure Policy, Azure Security Center and Azure Blueprints.
- Azure Policy helps you manage and prevent IT issues with policy definitions that enforce rules and effects for your resources.
- Azure Security Center provides unified security management and advanced threat protection across hybrid cloud workloads. The Azure Security Center Compliance dashboard provides insights into your compliance posture based on continuous assessments of your Azure environment.
- Azure Blueprints simplifies deployments by packaging artifacts, such as Resource Manager templates, role-based access controls, and policies, in a single blueprint definition.
10 steps to access control policy enforcement for Zero Trust with Azure Policy
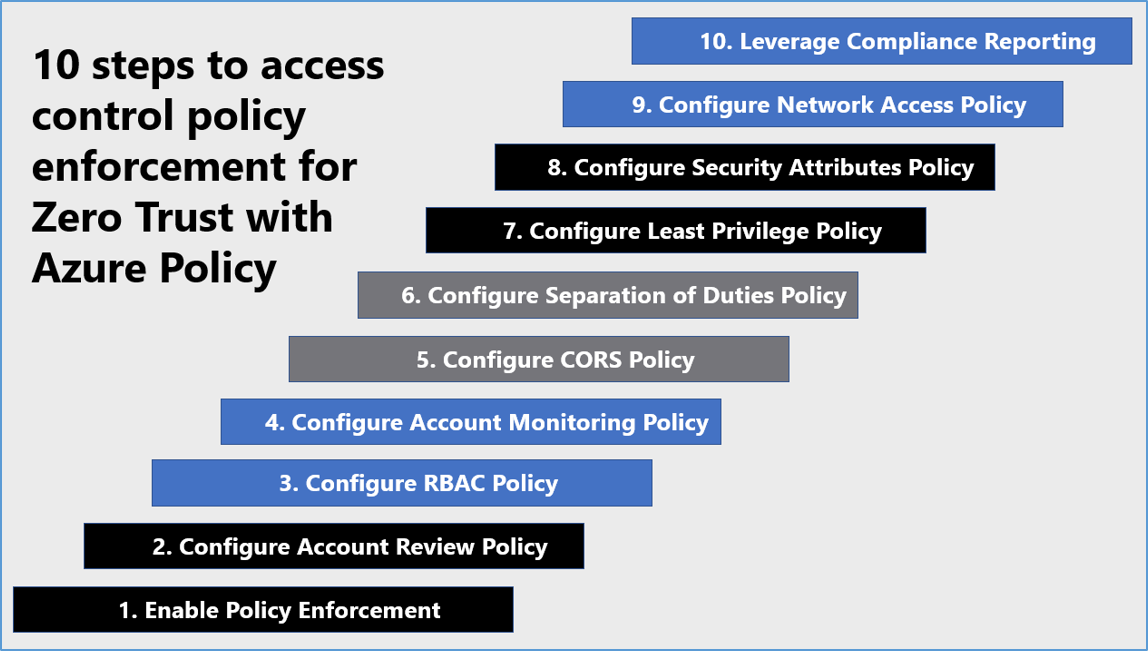
1) Enable Policy Enforcement
Azure Policy is a service in Azure used to create, assign and manage policies. These policies enforce different rules and effects over resources, so those resources remain compliant with organizational standards and service level agreements. Azure Policy meets this requirement by evaluating resources for non-compliance with assigned policies. Azure Policy focuses on resource properties during deployment and for already existing resources. Azure Policy controls properties such as the types or locations of resources. Unlike RBAC, Azure Policy is a default allow and explicit deny system. Azure Policy has several built-in policies enabled by default including allowed resource types, allowed locations and resource tagging. Azure Policy is configured with the following considerations:
- Policy Assignment: A policy definition that has been assigned to take place within a specific scope. The term scope refers to all the resource groups, subscriptions, or management groups that the policy definition is assigned to.
- Policy Parameters: Simplify your policy management by reducing the number of policy definitions you must create. This allows creation of a generic policy with an assigned value which can be retailored to different requirements.
- Initiative Definition: A collection of policy definitions that are tailored towards achieving a singular overarching goal.
- Initiative Assignment: Like a policy assignment, an initiative assignment is an initiative definition assigned to a specific scope.
- Initiative Parameters: Like policy parameters, initiative parameters help simplify initiative management by reducing redundancy.
Azure Policy is highly versatile and can be created with the Azure portal, Azure CLI, Powershell and Azure Resource Manager (ARM) templates. Creating an Azure Policy in the portal is accomplished via the following steps:
- In the Policy portal, select Assignments
- Select Assign Policy from the top of the Policy – Assignments page.
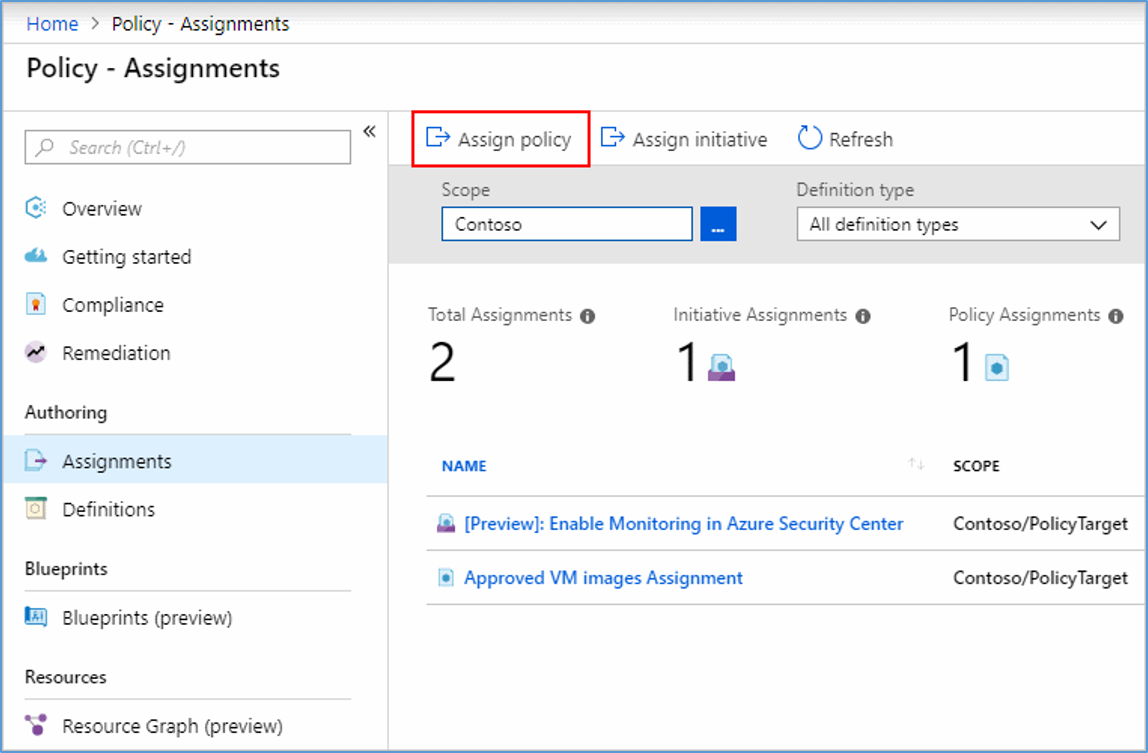
- On the Assign Policy page, select the Scope by clicking the ellipsis and selecting either a management group or subscription.
- Select the Policy definition ellipsis, search for the desired policy definition and click Select.
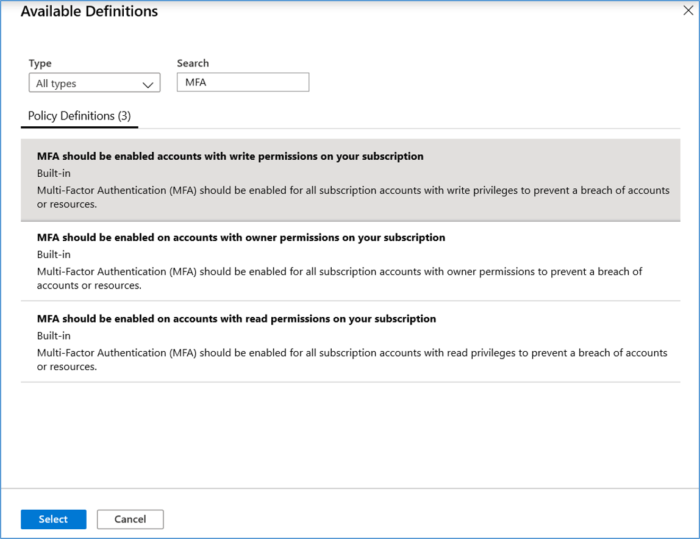
- Set an Assignment name, Description, and set Policy Enforcement to Enabled.
- Click Assign.
It’s important to note that Azure Policies can be active for automated enforcement or passive for auditing requirements. It is recommended to test all policies with the AuditIfNotExists effects prior to moving to automated policy enforcement with the DeployIfNotExists effect. For automated policy enforcement check Create a Managed Identity from the Assign Policy blade and set a DeployIfNotExists Effect in the policy parameters. For more information, see Quickstart: Create a policy assignment to identify non-compliant resources.
2) Configure Account Review Policy
The preceding sections are based in configuring policy for granular access controls within a Zero Trust model. An administrator is free to set each policy individually in Azure Policy, but there is a more effective method to combine and deploy policy initiatives aligned with compliance standards. Azure Blueprints enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization’s standards, patterns, and requirements. Create an Azure Blueprint for NIST SP 800-53 Rev4 via the steps below:
- Select All services in the left pane. Search for and select Blueprints.
- Select Create a blueprint.
- Select the NIST SP 800-53 R4 template
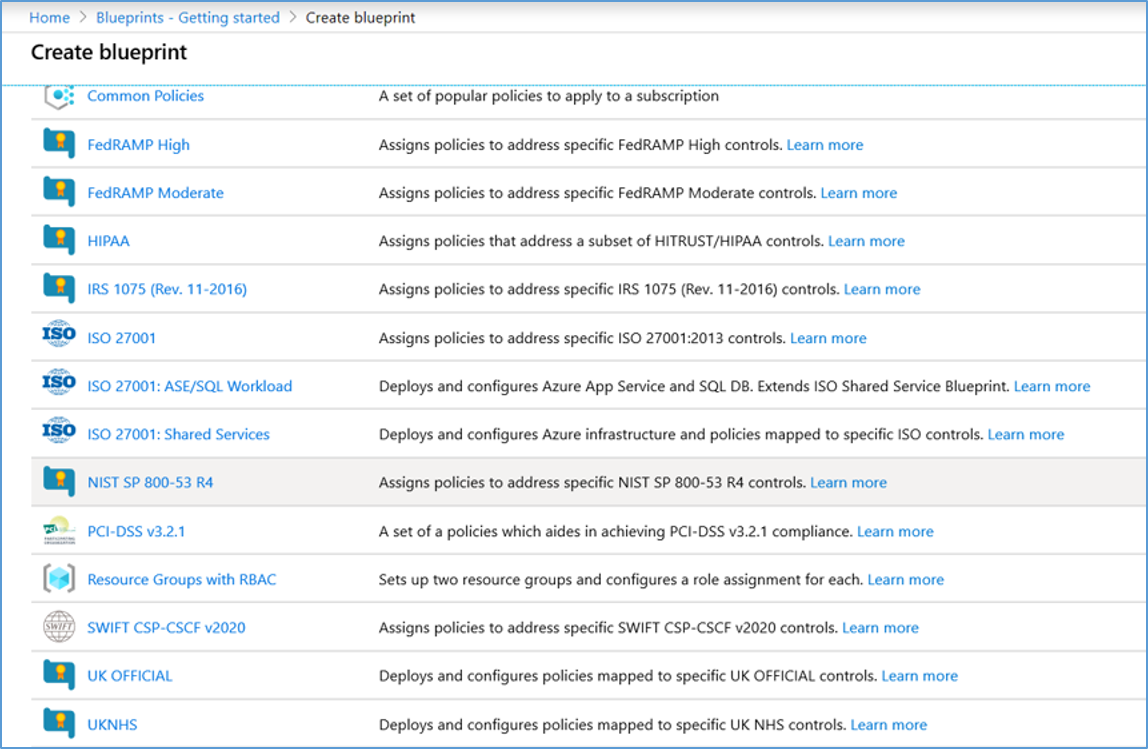
- Configure Blueprint name and select a target subscription for Definition location.
- Select Next: Artifacts>> and Save Draft.
- Select Blueprints definitions and select your blueprint draft.
- Click Publish blueprint and provide a Version such as 0.
- Select Assign blueprint.
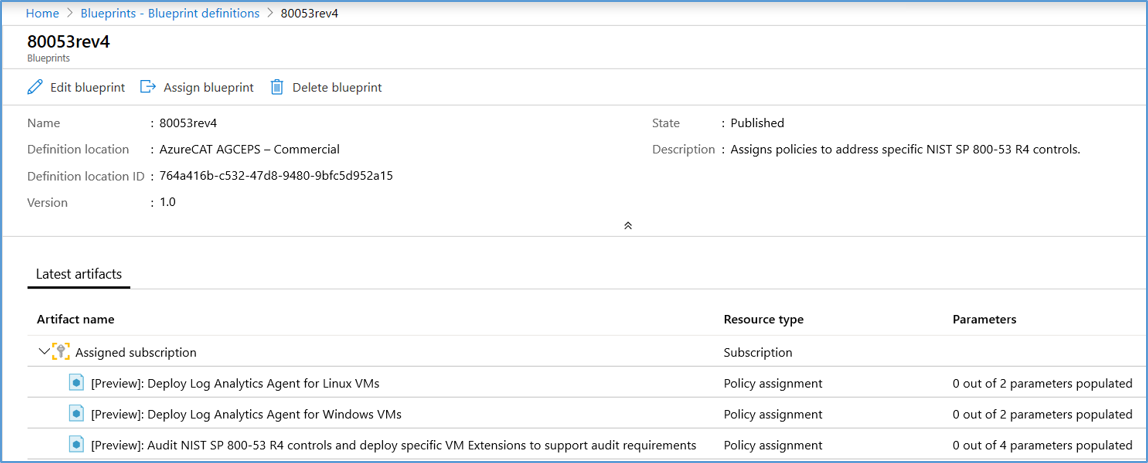
- Select Assign blueprint.
- The Assign blueprint blade will populate Assignment name, Location, Blueprint definition version, Lock Assignment and Managed Identity. Feel free to adjust per your requirements. Artifact Parameters require more granular settings, adjust per your requirements or input a semicolon and return for more detailed configuration at another time.
- Select Assign.
- Return to the Blueprints – Assigned blueprints blade and select your blueprint Assignment name for a detailed status of the blueprint application.
Configure account review policy via AC-2 Account Management in the NIST SP 800-53 R4 blueprint. This blueprint helps you review accounts that may not comply with your organization’s account management requirements. This blueprint assigns Azure Policy definitions that audit external accounts with read, write and owner permissions on a subscription and deprecated accounts. By reviewing the accounts audited by these policies, you can take appropriate action to ensure account management requirements are met. Below is a listing of respective policy assignments for account review:
- Deprecated accounts should be removed from your subscription
- Deprecated accounts with owner permissions should be removed from your subscription
- External accounts with owner permissions should be removed from your subscription
- External accounts with read permissions should be removed from your subscription
- External accounts with write permissions should be removed from your subscription
For more information, see Quickstart: Define and assign a blueprint in the portal and Control mapping of the NIST SP 800-53 R4 blueprint sample.
3) Configure Role-Based Access (RBAC) Policy
Configure role-based access control policy via AC-2 (7) Account Management | Role-Based Schemes in the NIST SP 800-53 R4 blueprint. Azure implements role-based access control (RBAC) to help you manage who has access to resources in Azure. Using the Azure portal, you can review who has access to Azure resources and their permissions. This blueprint also assigns Azure Policy definitions to audit use of Azure Active Directory authentication for SQL Servers and Service Fabric. Using Azure Active Directory authentication enables simplified permission management and centralized identity management of database users and other Microsoft services. Additionally, this blueprint assigns an Azure Policy definition to audit the use of custom RBAC rules. Understanding where custom RBAC rules are implemented can help you verify need and proper implementation, as custom RBAC rules are error prone. Below is a listing of respective policy assignments for RBAC:
- An Azure Active Directory administrator should be provisioned for SQL servers
- Audit usage of custom RBAC rules
- Service Fabric clusters should only use Azure Active Directory for client authentication
For more information, see Role-based access control.
4) Configure Account Monitoring Policy
Configure account monitoring policy via AC-2 (12) Account Management | Account Monitoring / Atypical Usage in the NIST SP 800-53 R4 blueprint. Just-in-time (JIT) virtual machine access locks down inbound traffic to Azure virtual machines, reducing exposure to attacks while providing easy access to connect to VMs when needed. All JIT requests to access virtual machines are logged in the Activity Log allowing you to monitor for atypical usage. This blueprint assigns an Azure Policy definition that helps you monitor virtual machines that can support just-in-time access but have not yet been configured. Below is a listing of respective policy assignments for account monitoring:
- Just-In-Time network access control should be applied on virtual machines
For more information, see Manage virtual machine access using just-in-time.
5) Configure Cross Origin Resource Sharing (CORS) Policy
Configure cross origin resource sharing policy via AC-4 Information Flow Enforcement in the NIST SP 800-53 R4 blueprint. Cross origin resource sharing (CORS) can allow App Services resources to be requested from an outside domain. Microsoft recommends that you allow only required domains to interact with your API, function, and web applications. This blueprint assigns an Azure Policy definition to help you monitor CORS resources access restrictions in Azure Security Center. Understanding CORS implementations can help you verify that information flow controls are implemented. Below is a listing of respective policy assignments for CORS:
- CORS should not allow every resource to access your Web Application
For more information, see Cross-Origin Resource Sharing (CORS) Support for the Azure Storage Services.
6) Configure Separation of Duties Policy
Configure separation of duties policy via AC-5 Separation of Duties in the NIST SP 800-53 R4 blueprint. Having only one Azure subscription owner doesn’t allow for administrative redundancy. Conversely, having too many Azure subscription owners can increase the potential for a breach via a compromised owner account. This blueprint helps you maintain an appropriate number of Azure subscription owners by assigning Azure Policy definitions that audit the number of owners for Azure subscriptions. This blueprint also assigns Azure Policy definitions that help you control membership of the Administrators group on Windows virtual machines. Managing subscription owner and virtual machine administrator permissions can help you implement appropriate separation of duties. Below is a listing of respective separation of duties policies:
- A maximum of 3 owners should be designated for your subscription
- Audit Windows VMs in which the Administrators group contains any of the specified members
- Audit Windows VMs in which the Administrators group does not contain all of the specified members
- Deploy requirements to audit Windows VMs in which the Administrators group contains any of the specified members
- Deploy requirements to audit Windows VMs in which the Administrators group does not contain all of the specified members
- There should be more than one owner assigned to your subscription
For more information, see Securing privileged access for hybrid and cloud deployments in Azure AD.
7) Configure Least Privilege Policy
Configure least privilege policy via AC-6 (7) Least Privilege | Review of User Privileges in the NIST SP 800-53 R4 blueprint. Azure implements role-based access control (RBAC) to help you manage who has access to resources in Azure. Using the Azure portal, you can review who has access to Azure resources and their permissions. This blueprint assigns Azure Policy definitions to audit accounts that should be prioritized for review. Reviewing these account indicators can help you ensure least privilege controls are implemented. Below is a listing of respective least privilege policies:
- A maximum of 3 owners should be designated for your subscription
- Audit Windows VMs in which the Administrators group contains any of the specified members
- Audit Windows VMs in which the Administrators group does not contain all of the specified members
- Deploy requirements to audit Windows VMs in which the Administrators group contains any of the specified members
- Deploy requirements to audit Windows VMs in which the Administrators group does not contain all of the specified members
- There should be more than one owner assigned to your subscription
For more information, see Azure Identity Management and access control security best practices.
8) Configure Security Attributes Policy
Configure security attributes policy via AC-16 Security Attributes in the NIST SP 800-53 R4 blueprint. The data discovery and classification capability of advanced data security for Azure SQL Database provides capabilities for discovering, classifying, labeling, and protecting the sensitive data in your databases. It can be used to provide visibility into your database classification state, and to track the access to sensitive data within the database and beyond its borders. Advanced data security can help you ensure information as associated with the appropriate security attributes for your organization. This blueprint assigns Azure Policy definitions to monitor and enforce use of advanced data security on SQL server. Below is a listing of respective security attributes policies:
- Advanced data security should be enabled on your managed instances
- Advanced data security should be enabled on your SQL servers
- Deploy Advanced Data Security on SQL servers
For more information, see Control mapping of the NIST SP 800-53 R4 blueprint sample.
9) Configure Network Access Policy
Configure network access policy via IA-2 (1) Identification and Authentication (Organizational Users) | Network Access to Privileged Accounts in the NIST SP 800-53 R4 blueprint. This blueprint helps you restrict and control privileged access by assigning Azure Policy definitions to audit accounts with owner and/or write permissions that don’t have multi-factor authentication enabled. Multi-factor authentication helps keep accounts secure even if one piece of authentication information is compromised. By monitoring accounts without multi-factor authentication enabled, you can identify accounts that may be more likely to be compromised. Below is a listing of respective network access policies:
- MFA should be enabled on accounts with owner permissions on your subscription
- MFA should be enabled on accounts with write permissions on your subscription
- MFA should be enabled on accounts with read permissions on your subscription
For more information, see How it works: Azure Multi-Factor Authentication.
10) Leverage Compliance Reporting
Evaluating compliance with organizational standards is a key requirement for enforcing access control policy for Zero Trust. Azure Security Center continuously assesses the configuration of your resources to identify security issues and vulnerabilities. These assessments are presented as recommendations, which focus on improving your security hygiene. In the regulatory compliance dashboard, you can view a set of compliance standards with all their requirements, where supported requirements are mapped to applicable security assessments. This enables you to view your compliance posture with respect to the standard, based on the status of these assessments. View the regulatory and compliance dashboard via the steps below:
- Search for and select Security Center from any page.
- Click Regulatory compliance to see your overall compliance score and number of passing vs. failing assessments for each standard.
- Select a tab for a compliance standard that is relevant to you. You will see the list of all controls for that standard.
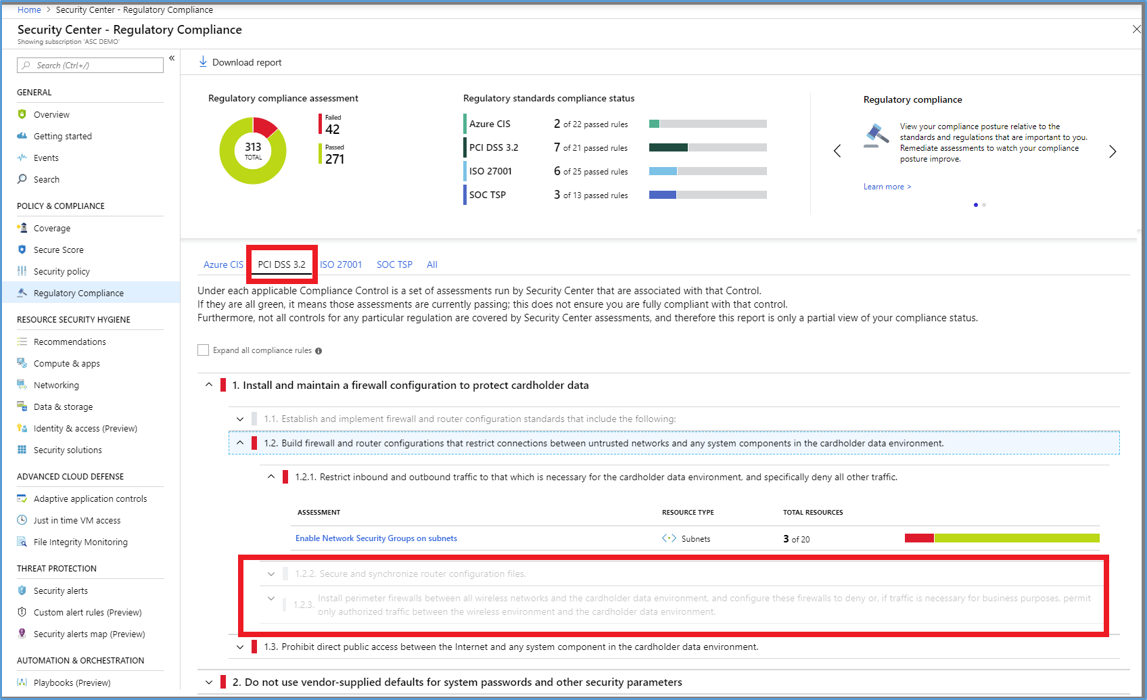
- Generate download a PDF report summarizing your current compliance status for a desired standard by clicking Download report. For more information, see Improve your regulatory compliance.
You can also add custom policy monitoring to the compliance dashboard. With this preview feature, you can add your own custom initiatives. You’ll then receive recommendations if your environment doesn’t follow the policies you create. Any custom initiatives you create will appear alongside the built-in initiatives in the regulatory compliance dashboard. Add a NIST SP 800-53 compliance monitoring initiative via the steps below:
- From Security Center’s sidebar, open the Security policy
- Select a subscription or Management Group to which you would like to add a custom initiative.
- In the Security policy page, under Your custom initiatives (Preview), click Add a custom initiative.
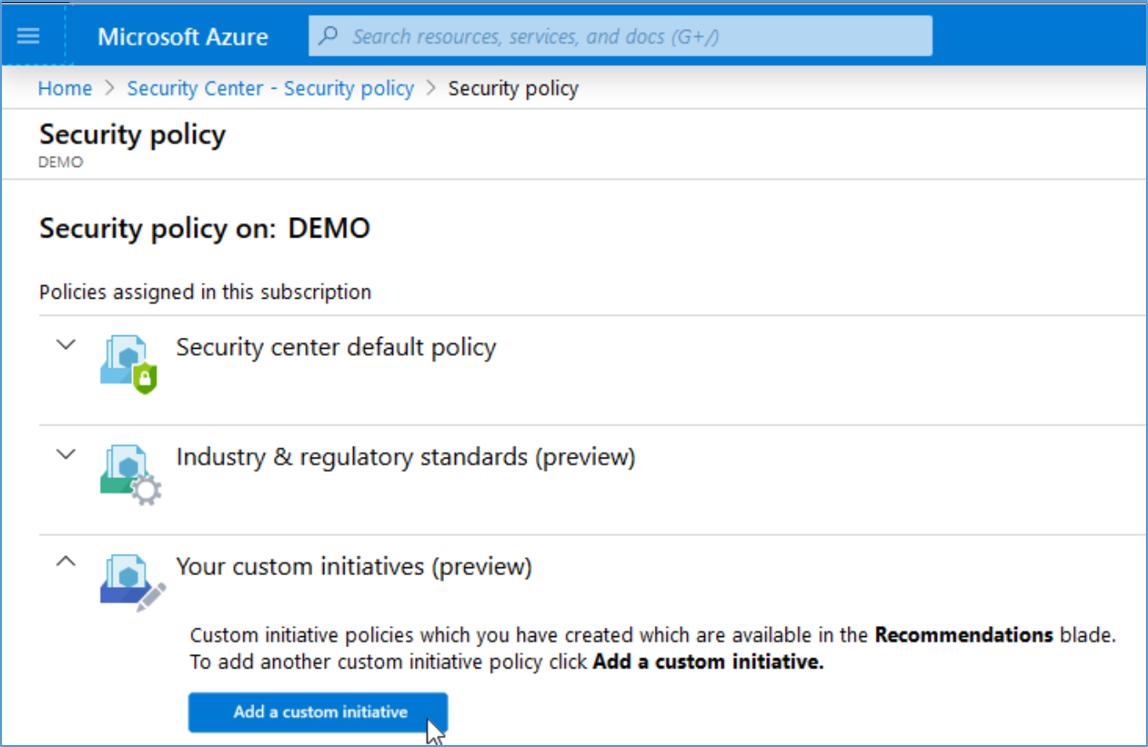
- In the Add custom initiatives page select NIST SP 800-53 R4 and click Add.
Upon completion the NIST SP 800-53 R4 standard will be included in the compliance dashboard and in the Recommendations blade. For more information, see Using custom security policies (Preview).
Learn more about Zero Trust with Microsoft
Here are some of the best resource to learn more about Zero Trust in the cloud with Microsoft:
- Reach the Optimal State in your Zero Trust Journey
- The Zero Trust Maturity Model
- Zero Trust: A New Era of Security
- Implementing a Zero Trust Security Model at Microsoft
- Zero Trust Strategy: What Good Looks Like
- Securing Mobile: Designing SaaS Service Implementations to Meet Federal TIC Policy
Be sure to check out the other topics we have covered in this series:
- Implementing Zero Trust with Microsoft Azure: Identity and Access Management
- Protecting Cloud Workloads for Zero Trust with Azure Security Center
- Monitoring Cloud Security for Zero Trust with Azure Sentinel
- Insider Threat Monitoring for Zero Trust with Microsoft Azure
- Supply Chain Risk Management for Zero Trust with Microsoft Azure
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.
[i] Cybersecurity and Infrastructure Security Agency. (2019, December 1). Trusted Internet Connections 3.0: Volume 3 Security Capabilities Handbook. Retrieved January 22, 2020, from https://www.cisa.gov/sites/default/files/publications/Draft%20TIC%203.0%20Vol.%203%20Security%20Capabilities%20Handbook.pdf
[ii] National Institute of Standards and Technology. (2018, April 16). Framework for Improving Critical Infrastructure Cybersecurity. Retrieved January 22, 2020, from https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
[iii] National Institute of Standards and Technology. (2013, April 1). NIST Special Publication 800-53: Security and Privacy Controls for Federal Information Systems and Organizations. Retrieved January 22, 2020, from https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf

0 comments