 In my day-to-day work, I help government agencies implement initiatives to protect, detect and respond to breaches. You’ve likely heard statistics – on average globally, it takes 191 days to identify a data breach and that the median number of days an attacker stays dormant within a network before detection is over 200. To put that in context: on average, an attacker exists within a company’s or agencies infrastructure, free to gather information or worse, for over six months before they’re found. It’s not that agencies aren’t employing security best practices but the reality is all the protection in the world can’t stop a determined hacker. Given these stats and the current security climate it’s not surprising that the top three cyberthreat concerns for 2016 were social engineering, insider threats and advanced persistent threats (APTs).
In my day-to-day work, I help government agencies implement initiatives to protect, detect and respond to breaches. You’ve likely heard statistics – on average globally, it takes 191 days to identify a data breach and that the median number of days an attacker stays dormant within a network before detection is over 200. To put that in context: on average, an attacker exists within a company’s or agencies infrastructure, free to gather information or worse, for over six months before they’re found. It’s not that agencies aren’t employing security best practices but the reality is all the protection in the world can’t stop a determined hacker. Given these stats and the current security climate it’s not surprising that the top three cyberthreat concerns for 2016 were social engineering, insider threats and advanced persistent threats (APTs).
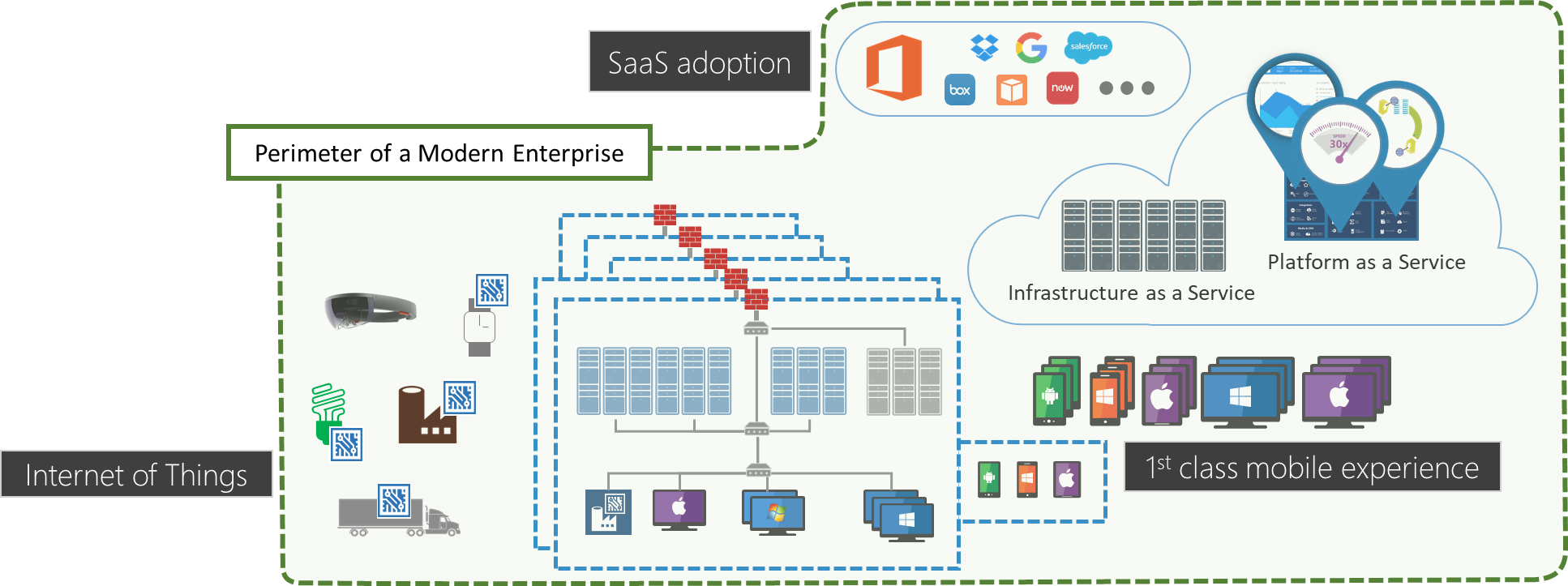
Citizens expect always-on secure, mobile digital services connected to massive hyperscale clouds with virtually unlimited bandwidth. Securely delivering these capabilities to agency information workers and citizens can be challenging given the new hybrid computing world we live in. Today’s modern perimeter is boundless and touches multiple cloud providers and endpoint devices. To protect this new hybrid environment, we need to change our security mindset to one where identity is the firewall, devices are the perimeter, and “assume breach” is the security model.
Assume Breach
To directly address this immense lag time from infiltration to detection, we encourage our customers to adopt an “assume breach”mindset. When you approach security as if your environment has already been compromised, you start thinking about how to detect compromises early and recover quickly. Shifting from passive-defense to active-defense changes your security posture – you’re aware, you’re prepared, you’re ready to act.
At Microsoft, we’re using machine learning to identify and detect issues early and accurately using an ‘assume breach’ approach. Our built-in approach to security now enables you to be vigilant from a high level on all fronts. For example, when a new SaaS app is being used by your employees, you can detect it immediately and get data about what risks and threats it may pose to your agency.
Identity is the new Firewall
With hybrid environments and an increasing demand for cloud services, how do you think about what needs to be kept out, and what needs to stay in, and how to manage that moving boundary? Instead of protecting a datacenter, we focus on protecting the data.
When protecting the data, permissions can be more granular and specific, which also enhances compliance with data protection regulations. For example, how sensitive is the data? Low, medium, or high business impact? What login credentials have the user supplied, such as multifactor authentication and biometrics? The new Azure AD Connect will integrate your on-premises directories with Azure Active Directory, enabling a common identity for your users for Office 365, Azure, and SaaS applications.
Devices are the new Perimeter
Most agencies still require employees to connect via VPN, which limits the ability to have granular control over the data. When agencies update to policy based access, you can look at the security state of the device the user is authenticating from, along with location data and credentials to determine what information should be accessible to that user.
And, this is not just for mobile workers in the field – this is shifting to a model where devices are your new perimeter. We’ve had more than one customer adopt Azure Security Center who decided to use it for their on-premises infrastructure, and discovered unpatched machines and machines with easy-to-guess passwords.
At Microsoft, we receive anonymized telemetry from billions of logins, devices, and services, both private and public cloud. Combining that with machine learning, behavioral inspection, and expert human analysis, we can detect and respond to what looks like anomalous behaviors and respond to potential threats. This intelligence is built into our products like Office 365 for U.S. Government and solutions such as Microsoft Enterprise Mobility + Security to give you visibility and insights and help you respond more quickly.
Learn more
With many agencies upgrading to a modern hybrid environment, we’re seeing the benefit of a new security mindset where identity is the firewall, devices are the perimeter, and ‘assume breach’ is the security model. Agencies using our cloud technologies to secure their data are not only discovering machines that weren’t patched, weak administrator passwords, and other hygiene issues, they’re to see anomalies in user activity they couldn’t see before. In addition, features like Azure Information Protection help them gain better insight into where data is moving across endpoints.
To learn more on these best practices, read 7 steps to a holistic security strategy. To experience the power of Azure Government for your organization, sign up for an Azure Government Trial. And for all things related security, privacy, transparency, and compliance, check out the Microsoft Trust Center.
You can also read more on harnessing the cloud for complex government regulations such as ITAR and new Azure Government capabilities for classified mission-critical workloads.

0 comments