This is the first in a six-part blog series where we will demonstrate the application of Zero Trust concepts for securing federal information systems with Microsoft Azure. In this first blog of the series we will explore identity and access management with Azure Active Directory.
Additional blogs will include protecting cloud workloads, monitoring cloud security, policy enforcement, investigating insider attacks and monitoring supply chain risk management.
This blog series is coauthored by TJ Banasik, CISSP-ISSEP, ISSAP, ISSMP, Sr. Program Manager, Azure Global Customer Engineering, Mark McIntyre, CISSP, Senior Director, Enterprise Cybersecurity Group and Adam Dimopoulos, Azure Global Customer Engineering.
What is Zero Trust?
Zero Trust is a security architecture model which institutes a deny all until verified approach for access to resources from both inside and outside of the network. This approach addresses the challenges associated with a shifting security perimeter in a cloud-centric and mobile workforce era.
Taking a layered approach to secure corporate and customer data, Microsoft’s phased implementation of Zero Trust centers on strong user identity, device health verification, validation of application health, and secure, least-privilege access to corporate resources and services. The core principle of zero trust is maintaining strict access control. This concept is critical to prevent attackers from pivoting laterally and elevating access within an environment.
Defining Zero Trust governance based on federal frameworks
Governance definition is a critical precursor to any Zero Trust initiative. For federal agencies this means evaluating the available federal frameworks. There are several references for implementing Zero Trust in federal information systems which include NIST SP 800-207, TIC 3.0, and CDM:
- The National Institute of Standards and Technology (NIST) has recently released NIST SP 800-207 which is in draft for comment. This document provides a framework for designing a zero-trust architecture (ZTA) network strategy.
- Trusted Internet Connections (TIC) is a federal cybersecurity initiative to enhance network and perimeter security across the United States federal government. The TIC initiative is a collaborative effort between the Office of Management and Budget (OMB), the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA), and the General Services Administration (GSA). The TIC 3.0: Volume 3 Security Capabilities Handbook provides various security controls, applications and best practice for risk management in federal information systems.
- Continuous Diagnostics and Mitigation (CDM) Program is led by the Cybersecurity and Infrastructure Security Agency (CISA). The CDM program delivers cybersecurity capabilities across the federal government including providing cybersecurity tools, services, reporting and best practices. The Continuous Diagnostics and Mitigation Program Fact Sheet outlines five key program areas including dashboarding, asset management, identity and access management, network security management and data protection management.
In Azure, we crosswalk NIST SP 800-207, OMB TIC 3.0, and CISA CDM to align requirements for implementing Zero Trust architectures. Our first focus point is identity and access management (IAM), and these documents have a wealth of information aligned to IAM practices. The diagram below highlights the key takeaways and requirements from the frameworks:
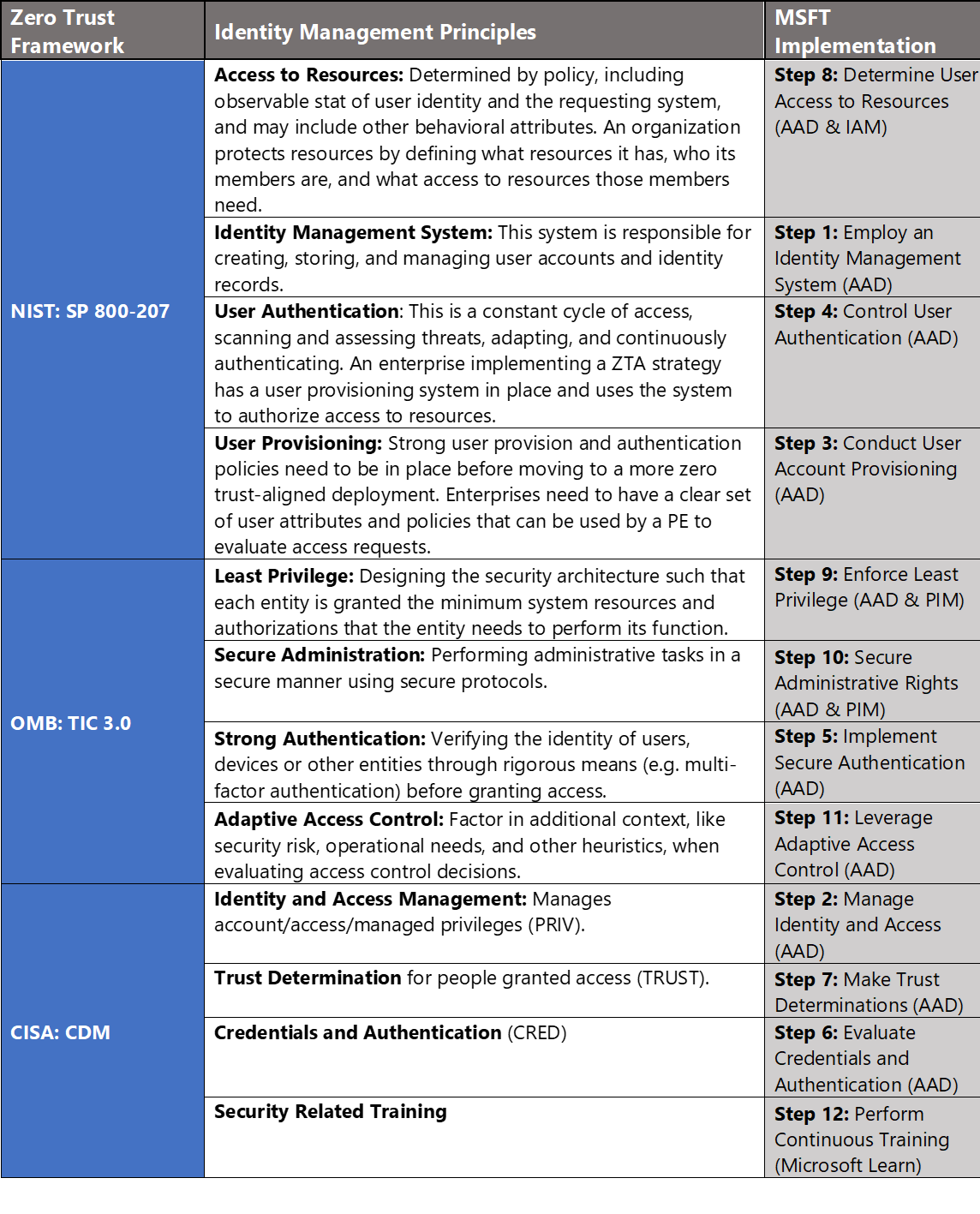
Conducting Identity Management with Microsoft Azure
Microsoft Azure Government has developed a 12-step process for securing identity and access management in federal information systems which is aligned with the identity management principles within the NIST, OMB, and CISA Zero Trust frameworks. Microsoft has several offerings to support identity management in Azure including Azure Active Directory (AAD), Azure Active Directory Identity Protection and Azure AD Privileged Identity Management (PIM).
- Azure Active Directory is an identity and access management-as-a-service (IDaaS) solution that combines single-on capabilities to any cloud and on-premises application with advanced protection. It gives your people, partners, and customers a single identity to access the applications they want and collaborate from any platform and device. And because it’s based on scalable management capabilities and risk-based access rules, Azure AD helps ensure security and streamline IT processes.
- Azure AD Identity Protection is a tool which allows organizations to automate detection/remediation of identity-based risks, investigate risk using data in the portal and export risk detection data to third-party utilities for further analysis.
- Azure AD Privileged Identity Management (PIM) manages policies for privileged access for users in Azure AD. PIM assigns users to one or more roles in Azure AD, and you can assign someone to be permanently in the role, or eligible for the role.
12 steps to implementing Zero Trust identity management principles in Azure

1) Employ an Identity Management System
Deploying Azure Active Directory (AAD) requires administrators to enable baseline security features to create a more secure and easy to use foundation in Azure AD before importing or creating user accounts. This process includes designating global administrators, using non global-admin roles where possible, enabling privileged identity management and designing identity polices. For more information, see the Azure Active Directory feature deployment guide.
2) Manage Identity and Access
In cloud-focused architecture, identity provides the basis of a large percentage of security assurances. While legacy IT infrastructure often heavily relied on firewalls and network security solutions at the internet egress points for protection against outside threats, these controls are less effective in cloud architectures with shared services being accessed across cloud provider networks or the internet.
It is challenging or impossible to write concise firewall rules when you don’t control the networks where these services are hosted, different cloud resources spin up and down dynamically, cloud customers may share common infrastructure, and employees and users expect to be able to access data and services from anywhere. To enable all these capabilities, you must manage access based on identity authentication and authorization controls in the cloud services to protect data and resources and to decide which requests should be permitted.
Additionally, using a cloud-based identity solution like Azure AD offers additional security features that legacy identity services cannot because they can apply threat intelligence from their visibility into a large volume of access requests and threats across many customers. For more information, see Identity and access management.
3) Conduct User Account Provisioning
Adding users to Azure Active Directory requires either User administrator or Global administrator rights. The process is accomplished via the steps below:
- Sign into the Azure Portal as a User administrator for the organization.
- Search for and select Azure Active Directory from any page.
- Select Users, and then select New user.
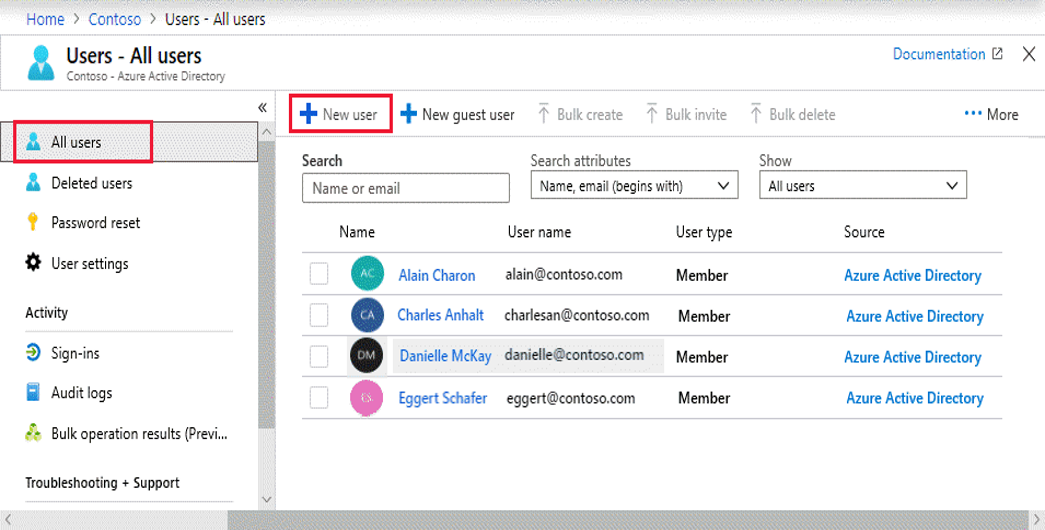
- On the User page, enter user information including name, username (within domain), groups, directory role, and job information.
- Copy the autogenerated password provided in the Password You’ll need to securely provide this password to the user for the first sign in.
- Select Create.
The user is created and added to your Azure AD organization. For more information, see Add or delete users using Azure Active Directory.
4) Control User Authentication
Azure Active Directory provides administrators the flexibility to apply granular user authentication per their requirements. As an administrator, choosing authentication methods for Azure Multi-Factor Authentication and self-service password reset (SSPR) it is recommended that you require users to register multiple authentication methods. When an authentication method is not available for a user, they can choose to authenticate with another method. Authentication methods include password, security questions, email address, Microsoft Authenticator app, OATH Hardware token, SMS, Voice call, and App passwords. For more information, see Authentication methods.
5) Implement Secure Authentication (MFA)
Implementing Multi-Factor Authentication is arguably one of the strongest controls to protect identity and access management in the cloud. This ensures the user making the authentication request is who they say they are, because the user must input an additional token which is generated on another device they own. The secondary factors used in MFA policies are much more difficult to spoof because they are time-sensitive and generally tied to hardware which an attacker is less likely to get their hands on. Configuring MFA requires either User administrator or Global administrator rights. The process is accomplished via the steps below:
- Browse to Azure Active Directory, Users, Multi-Factor Authentication.
- In the new tab that opens browse to service settings.
- Under verification options, check all boxes for methods available to users.
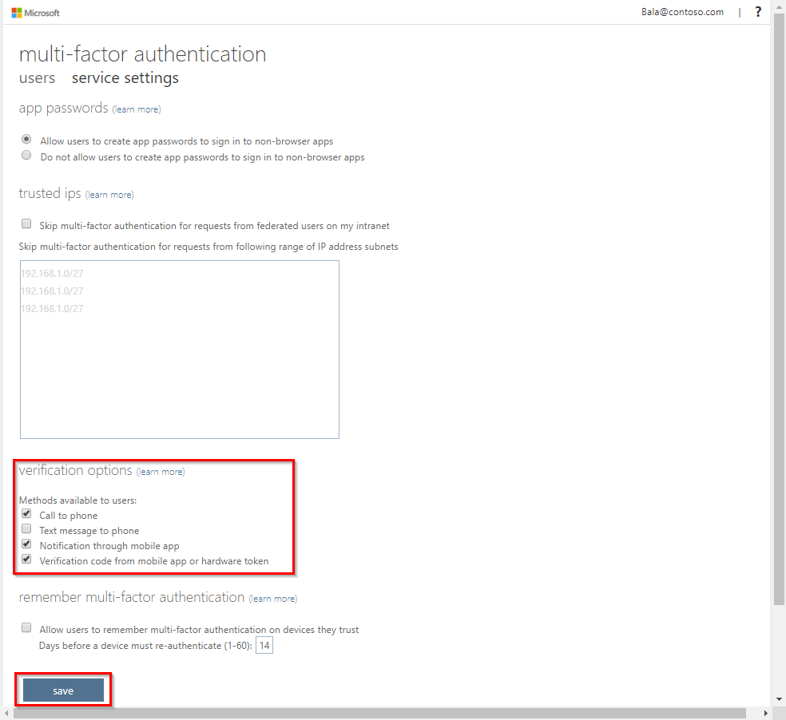
- Click on Save.
- Close the service settings tab.
The user authentication method has been changed to MFA. For more information, see Planning a cloud-based Azure Multi-Factor Authentication deployment.
6) Evaluate Credentials and Authentication
Evaluating user credentials is a challenging and continuous function requiring administrators to determine the appropriate user accounts, credentials and access methods. Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User’s access can be reviewed on a regular basis to make sure only the right people have continued access. Access reviews automate the process of controlling user and administrative rights and are accomplished via the steps below:
- Sign in to the Azure portal and open the Identity Governance
- In the left menu, click Access reviews.

- Click New access review to create a new access review.
- Name the access review and provide a description for the reviewers.
- Select the start date. The end date defaults to 30 days out.
- To make the access review recurring, change the Frequency setting from One time to Weekly, Monthly, Quarterly or Annually.
- In the Users section, specify the users that the access review applies to.
- In the Groups section, select one or more groups that you would like to review membership of.
- In the Reviewers section, select either one or multiple people to review all the users in scope.
- Set Upon completion settings to specify what happens (No change, Remove access, Approve access or Take recommendations) after a review completes then click Start.
This process initiates the access review. For more information, see Create an access review of groups and applications in Azure AD access reviews.
7) Make Trust Determinations
Evaluating and configuring trust relationships is a comprehensive process which requires adequate time and planning. Azure AD provides several options to support making trust determinations.
- Hybrid Identity: A hybrid deployment of Azure AD can be part of a strategy for an organization to migrate its IT assets to the cloud, or to continue to integrate existing on-premises infrastructure alongside new cloud services
- Azure AD Connect: Azure AD Connect is the Microsoft tool designed to meet and accomplish your hybrid identity goals. It provides password hash synchronization, pass-through authentication, federation integration, synchronization and health monitoring.
- Password hash synchronization: A sign-in method that synchronizes a hash, of the hash, of a user’s password from an on-premises Active Directory instance to a cloud-based Azure AD instance.
- Pass-through authentication: A sign-in method that allows users to use the same password on-premises and in the cloud but doesn’t require the additional infrastructure of a federated environment.
- Federation: Federation is a collection of domains that have established trust. The level of trust may vary, but typically includes authentication and almost always includes authorization. A typical federation might include several organizations that have established trust for shared access to a set of resources.
- Single sign-on: Azure Active Directory Seamless Single Sign-On (Azure AD Seamless SSO) automatically signs users in when they are on their corporate devices connected to your corporate network. When enabled, users don’t need to type in their passwords to sign in to Azure AD, and usually, even type in their usernames.
For more information, see Four steps to a strong identity foundation with Azure Active Directory.
8) Determine User Access to Resources
You can use the Access control (IAM) blade in role-based access control (RBAC) to view the access a user or another security principal has to Azure resources. However, sometimes you just need to quickly view the access for a single user or another security principal. The easiest way to do this is to use the Check access feature in the Azure portal. Determining user access to resources is accomplished via the steps below:
- In the Azure portal, click All services and then Subscriptions
- Click your subscription.
- Click Access control (IAM).
- Click the Check access tab.
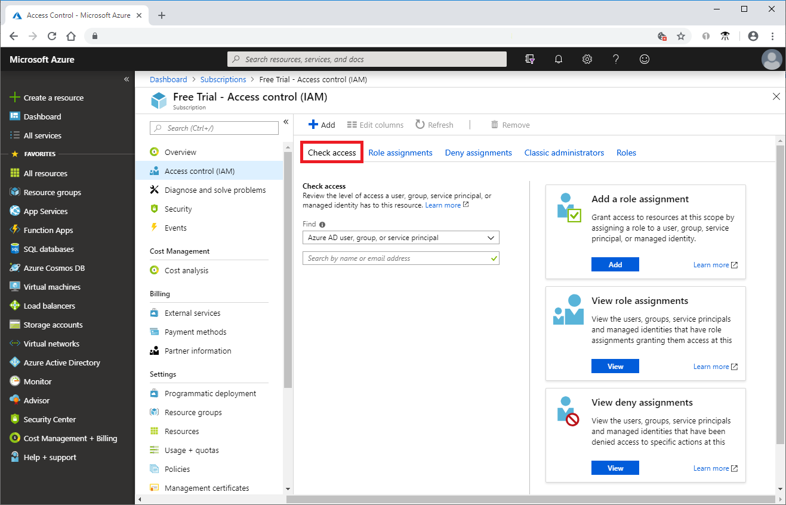
- In the Find list, select the type of security principal you want to check access for.
- In the search box, enter a string to search the directory for display names, email addresses, or object identifiers.
- Click the security principal to open the assignments
For more information, see Quickstart: View the access a user has to Azure resources.
9) Enforce Least Privilege
Access management for cloud resources is critical for any organization that uses the cloud. Role-based access control (RBAC)helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to. Designating groups or individual roles responsible for specific functions in Azure helps avoid confusion that can lead to human and automation errors that create security risks. Restricting access based on the need to know and least privilege security principles is imperative for organizations that want to enforce security policies for data access.
Your security team needs visibility into your Azure resources to assess and remediate risk. If the security team has operational responsibilities, they need additional permissions to do their jobs. You can use RBAC to assign permissions to users, groups, and applications at a certain scope. The scope of a role assignment can be a subscription, a resource group, or a single resource.
Best practice: Segregate duties within your team and grant only the amount of access to users that they need to perform their jobs. Instead of giving everybody unrestricted permissions in your Azure subscription or resources, allow only certain actions in scope. Use built-in RBAC roles in Azure to assign privileges to users. For more information, see Azure Identity Management and access control security best practices.
10) Secure Administrative Rights
Microsoft uses Azure Active Directory (AD) Privileged Identity Management (PIM) to manage elevated access for users who have privileged roles for Azure services. PIM manages privileged identities for on premises and Azure services to process requests for elevated access and help mitigate risks that elevated access can introduce. With Azure AD PIM, administrators can implement just-in-time access for privileged roles in Azure and view audit logs. Before Azure AD PIM, privileged roles in Azure were always elevated. The elevated access workflow provides a review, approval, just-in-time (JIT) time-bound access and detailed reporting for monitoring and the workflow is detailed in the diagram below.
11) Leverage Adaptive Access Control
Microsoft Azure leverages adaptive access control through Azure Active Directory (AAD) conditional access. The modern security perimeter now extends beyond an organization’s network to include user and device identity. Organizations can utilize these identity signals as part of their access control decisions. Conditional access policies incorporate Azure AD Identity Protection risk detections and include three default policies:
- Require all users to register for Azure Multi-Factor Authentication.
- Require a password change for users that are high risk.
- Require multi-factor authentication for users with medium or high sign-in risk.
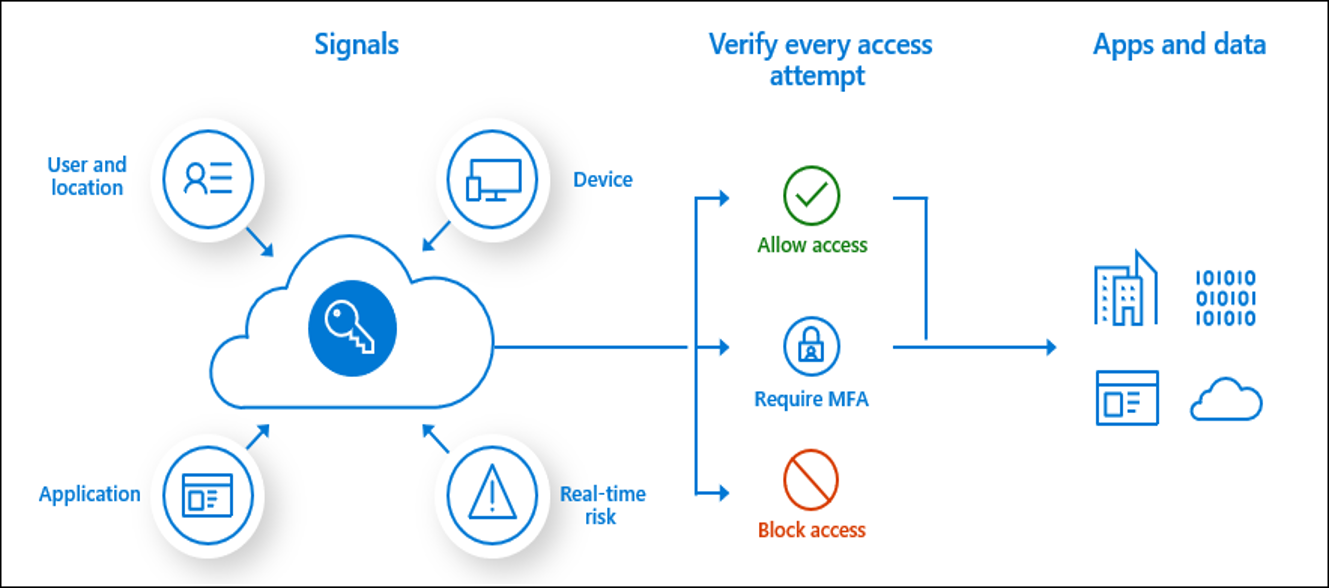
Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies. Conditional Access is at the heart of the new identity driven control plane. Conditional access policies are highly configurable and include several capabilities:
- Require MFA for admins
- End user protection
- Block legacy authentication
- Require MFA for Service Management
- Block access by location
- Require trusted location for MFA registration
- Require compliant devices
For more information, see What is Conditional Access?
12) Perform Continuous Training
Continuous training is often the hallmark of a successful security organization. Administrators and security engineers require constant training to keep ahead of the evolving threat. Training and personnel retention are often challenging and budget intensive for federal organizations. Microsoft Learn is a free resource which provides learning paths, hands-on learning and course modules at no cost. Microsoft Learn has hundreds of training modules and there are currently 12 courses for identity management in Azure which is a great resource for continuous security training for your teams.
Learn more about Zero Trust with Microsoft
Here are some of the best resources to learn more about Zero Trust in the cloud with Microsoft:
- Reach the Optimal State in your Zero Trust Journey
- The Zero Trust Maturity Model
- Zero Trust: A New Era of Security
- Implementing a Zero Trust Security Model at Microsoft
- Zero Trust Strategy: What Good Looks Like
- Securing Mobile: Designing SaaS Service Implementations to Meet Federal TIC Policy
Be sure to check out the other topics we have covered in this series:
- Protecting Cloud Workloads for Zero Trust with Azure Security Center
- Monitoring Cloud Security for Zero Trust with Azure Sentinel
- Enforcing Policy for Zero Trust with Azure Policy
- Insider Threat Monitoring for Zero Trust with Microsoft Azure
- Supply Chain Risk Management for Zero Trust with Microsoft Azure
Also, join us for the Microsoft Ignite Government Tour Feb. 6-7, 2020 in Washington, DC.
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.

Not all MFA is created equal. The federal government has made a large investment in and reaps great rewards from the use of PIV card. Not only does it provide the highest Authentication Assurance (AAL3) the consistent processes across the issuance community for secure identity verification (IAL3) is very important. Microsoft has long supported PIV authentication on the network and I would like to hear more about how assurance level fit into your view of...
Ross,
Thanks for your question and for following our blog on Zero Trust in Federal Information Systems. We understand your thoughts on MFA and Microsoft Azure has several configuration options for integrating PIV/CAC cards within Azure Active Directory. Planning identity for Azure Government applications provides details and configuration options aligned with Identity in Azure Government applications.