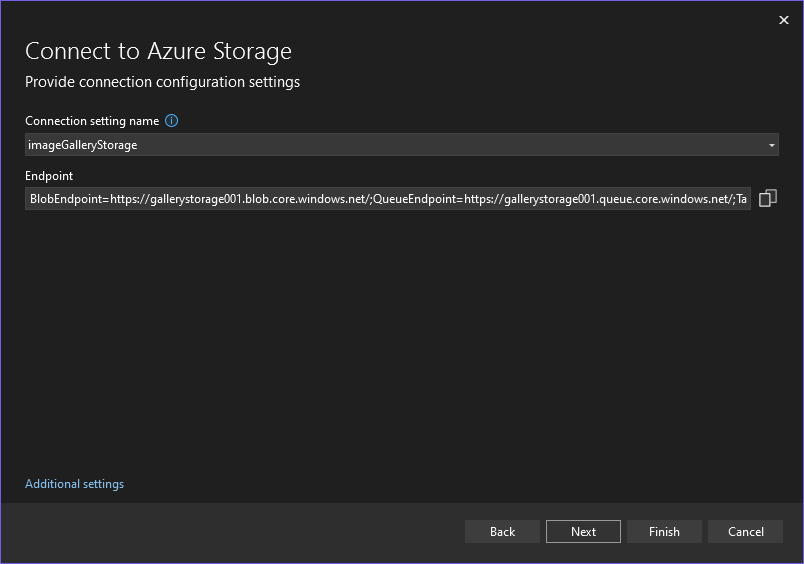
Visual Studio 2022’s Connected Services features are being updated to help you start secure. In the past, for example with Azure Storage, we’d inject the entire connection string into your configuration. With this update, we’ve removed the secrets from the UX – and from what we save to configuration – altogether. This means your code has fewer secrets in it, so you won’t push those into your source control repository inadvertently.
Integrated authentication, by default
Prior to this update, Connected Services would inject secret-inclusive connection strings for resources like Azure Storage into your secrets. If you were using secrets.json for local storage, this would result in your secrets being stored in files on disk.
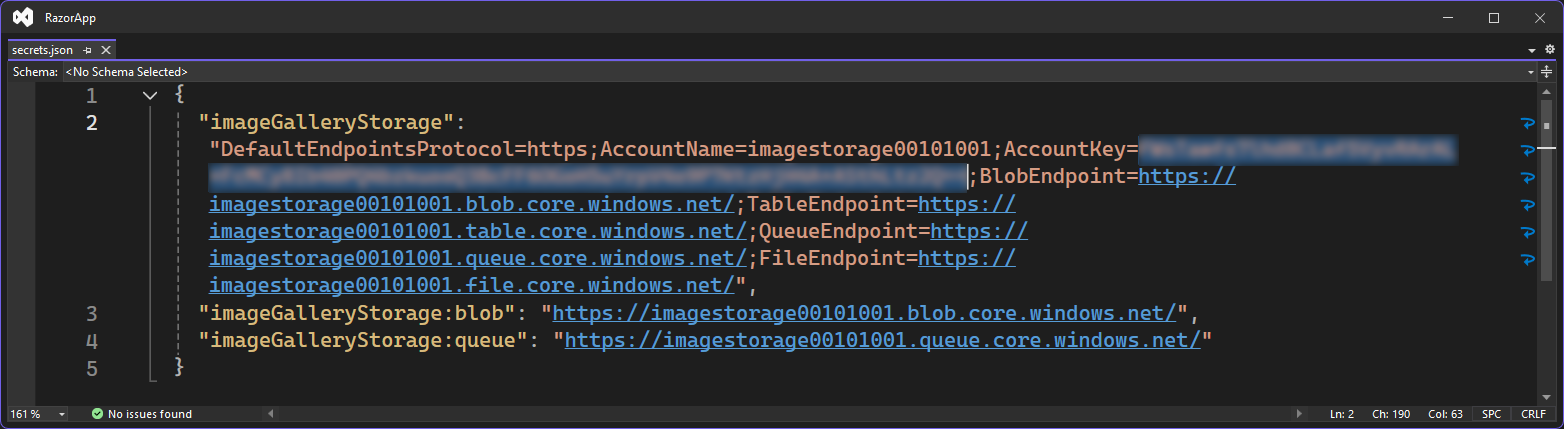
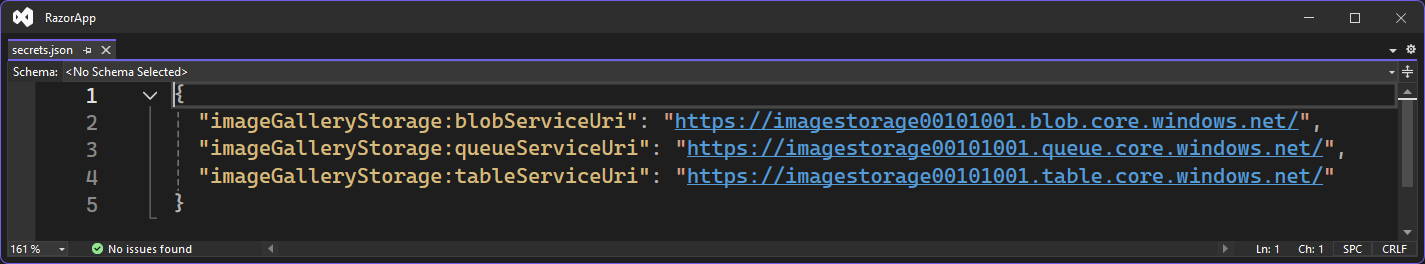
After this update, your secrets.json will contain no actual secrets, but rather the Azure Storage endpoints for your service instance. Using the latest Azure SDKs, your code connects to your Azure resources using your Visual Studio or Azure CLI login. Locally, your logged-in credential does the magic; in Azure, the app service’s managed identity takes over!
Benefits with this update
Enhanced security: Fewer secrets on disk means your development process is automatically more secure, since you mitigate the potential for these secrets to be inadvertently committed to source control.
Simplified development and deployment: Focus on what you do best – coding – while Connected Services handles the tedious parts, more securely than ever.
Automated configuration: During publishing, your app is seamlessly configured with the necessary identity and roles needed to access resources, making the process smoother than ever.
Thank You for Your Feedback
Your invaluable feedback drives our continuous improvement. We’re thrilled to bring you these enhancements and can’t wait to hear about your experiences with the new Connected Services feature. Happy coding!


0 comments