This post is provided by App Dev Managers Latha Natarajan and Sujith Nair who explore the critical aspect of protecting personal information and the impact of data security failures. This post also discusses the rich set Azure services that Microsoft customers and organizations can use to protect personal data in compliance with GDPR and other regulations for various parts of the world.
Personal Data Protection and GDPR
Although the information economy has existed for some time, the real value of personal data has only become more recently evident. Cyber theft of personal data exposes citizens around the world to significant personal risks. Big data analysis techniques enable organizations to track and predict individual behavior and can be deployed in automated decision-making. The combination of all these issues, together with the continuing advance of technology and concerns about the misuse of personal data by governments and corporations, has resulted in a new law passed by the EU to clarify the data rights of EU citizens and to ensure an appropriate level of EU-wide protection for personal data.
Personal data in this context means any information relating to an identified or identifiable natural person. The EU General Data Protection Regulation (GDPR) will supersede the 1995 EU Data Protection Directive (DPD) and all EU member states’ national laws based on it in May 2018. All organizations – wherever they are in the world – that process the personal data of EU residents must comply with the Regulation. Failure to do so could result in fines of up to €20 million or 4% of annual global turnover.
Impact of Data Security Failures on Organizations
Data security failures and cyber breaches can be catastrophic events for any organization. Small organizations may well be wiped out simply by the nature of the breach and/or the immediate costs of dealing with it, and large corporations can be hit by enormous fines, class-action lawsuits and loss of reputation, all of which can have significant repercussions and inflict significant damage to both the organization’s reputation and its bottom line. As the overwhelming majority of data security failures result from a common set of vulnerabilities, organizations should be aware of these vulnerabilities and act to eliminate them. One of the more notable breaches in recent years was that of Target in the US. In late 2013, criminals gained access to around 70 million customers’ personal information, and data on 40 million credit cards and payment cards. These details were stolen from Target’s point-of-sale (POS) systems via malware. The attackers were able to gain access to Target’s systems because of a number of flaws: The attackers infiltrated the computer systems of Target’s HVAC supplier; Target had not established an effective supplier security vetting process and this supplier’s security processes were inadequate. As a result of the breach, Target was subjected to substantial fines and lawsuits, and both the CIO and CEO were forced to resign. The overall cost to Target was estimated to be in the hundreds of millions of dollars, not including the impact on revenues and profits that resulted from the loss in customer confidence.
What does GDPR mean for your data?
Leveraging Azure to be GDPR Compliant
When adopting Microsoft cloud services and products, it is important to remember that some security, privacy, and compliance needs are the responsibility of the customer, some are the responsibility of Microsoft, and some are shared. The white paper “Shared responsibility in cloud computing” (https://aka.ms/sharedresponsibility) can help you learn more about each party’s responsibilities in cloud-based solutions.
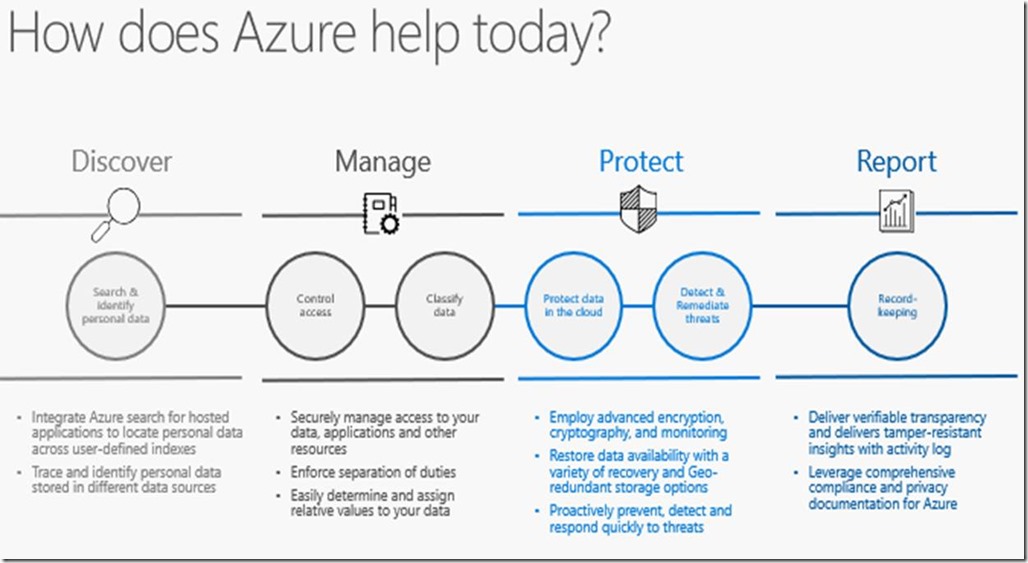
Microsoft has products and services available that can help you in your preparation for meeting GDPR requirements. Microsoft has developed a four-step process that can help you follow on your journey to GDPR compliance. The four steps are:
- Discover: Identify what personal data you have and where it resides. Azure Information Protection can help you automate the process of classifying categories of data as well as tagging of data assets. Azure Information Protection labels are available to apply classification to documents and email. The classification is identifiable always, regardless of where the data is stored or with whom it is shared. Also, Azure Data Catalog is an enterprise-wide metadata catalog that makes data asset discovery straightforward. It’s a fully-managed service that lets you—from analyst to data scientist to data developer—register, enrich, discover, understand, and consume data sources.
- Manage: The goal of the second step is to govern how personal data is used and accessed within your organization. There are several services available to provide mechanisms to grant and restrict access to personal data (such as Azure Active Directory and Azure Information Protection) as well as to use roles to enforce segregation of duties. For example, Azure Role-Based Access Control (RBAC) enables you to define fine-grained access permissions to grant only the amount of access that users need to perform their jobs. Instead of giving everybody unrestricted permissions for Azure resources, you can allow only certain actions for accessing personal data.
- Protect: The goal of this step is to establish security controls to prevent, detect, and respond to vulnerabilities and data breaches. The services in this category range from Azure Security Center (provides unified security management and advanced threat protection), Azure Key Vault (for managing cryptographic keys) to Azure Storage Services Encryption, Azure Disk Encryption, and the physical data center security at Microsoft data centers.
- Report: The goal of this fourth and last step is to retain the required documentation, manage data requests, and provide breach notifications. With Azure Monitor, you get detailed, up-to-date performance and utilization data, access to the activity log that tracks every API call. A good example of this service is Activity Log through which you can determine who initiated an operation, when it occurred, and the status of that operation. You can use the Activity Log to determine the what, who, and when for any write operations (PUT, POST, DELETE) made for the resources in your Azure subscription.
Resources to help you prepare for the GDPR
- Take our GDPR Assessment at www.gdprbenchmark.com to review your overall level of readiness.
- Explore our Service Trust Platform at servicetrust.microsoft.com to access: Audit reports, compliance guides, and trust documents
- The following figure shows Microsoft solutions to help you prepare for GDPR
Where can you get more information?
Hopefully, this blog provided the reader the importance of protecting personal information, imminent need to be GDPR compliant, and the basic approach and capabilities of Azure to be GDPR compliant and protect personal data. Please use the below links for more information.
Discover GDPR Compliance Solutions
Download Shared Responsibilities for Cloud Computing
Download the white paper, product-specific materials, and other resources at https://aka.ms/gdprpartners
The regulation itself is published on this EU official website:
https://ec.europa.eu/info/strategy/justice-and-fundamental-rights/data-protection_en
Premier Support for Developers provides strategic technology guidance, critical support coverage, and a range of essential services to help teams optimize development lifecycles and improve software quality. Contact your Application Development Manager (ADM) or email us to learn more about what we can do for you.


0 comments