To help you understand and use the RWA pattern, we’ve created a comprehensive collection of materials that describe it in full. You can review the documentation and access the production-quality, ready-to-deploy web application – Reference Implementation.
The latest update to The Reliable Web App Pattern for Java builds on its initial promise to facilitate the migration of legacy Java applications to Azure, now with a sharper focus on enhancing the production infrastructure. This enhancement responds directly to user feedback, particularly around the value of Infrastructure as Code (IaC) with Terraform best practices and network security.
The update retains its core developer patterns but shifts its reference architecture from Proseware to Contoso Fiber, aiming to better reflect real line-of-business scenarios. This version introduces a reference application that embodies best practices for creating a Reliable Web App on Azure, demonstrating tangible improvements in cost efficiency, scalability, and workload separation based on customer feedback.
Hub and Spoke Deployment
As part of the network security recommendation, we have introduced the hub-spoke network design, where a main hub network connects to several spoke networks.
A hub and spoke network is a common cloud network topology designed around the best practices for application isolation and overall security. Shared services are homed into a dedicated “hub” network. This is also where connectivity to on-premise facilities and the Internet are located. A hub network allows the enterprise to control and monitor network traffic between applications and from applications and the Internet. Applications are homed into “spoke” networks that are peered to the hub network. All the resources within a spoke network can talk to one another and the isolation from other applications limits the “blast radius” when things go wrong with the application. In this way, enterprises can easily segment, monitor, and control each application individually while optimizing costs by utilizing shared services.
This approach enhances your network’s security through private endpoints adhering to stringent rules, without compromising system performance.
The design splits networks into public and private areas. Public services like Azure Front Door and App Service only have access to what they need to keep the system secure, and a special firewall checks them. Other services like PostgreSQL and Azure Cache for Redis, which don’t need to be publicly accessible, use private endpoints for more protection in their own subnets, and firewalls make sure only good traffic can pass. These services use private DNS to make connections safe and fast.
Azure Bastion Host lets you get to VMs from the Azure portal in a secure way, whether you’re in the same network or another one, keeping database access safe and VM management easy without being exposed online.
The setup assigns roles to the resource groups that they use. For developers, there’s a specific resource group that displays the app as they develop it, while other groups assist with networking and security tasks. This network design doesn’t make the development process more difficult as you can choose whether to set up network access restrictions e.g. in development, you can turn this off to let developers connect to the web app directly for extra debugging.
Pattern Recap
You can test and configure the three code-level design patterns with this implementation: retry, circuit-breaker, and cache-aside.
Cache-Aside Pattern
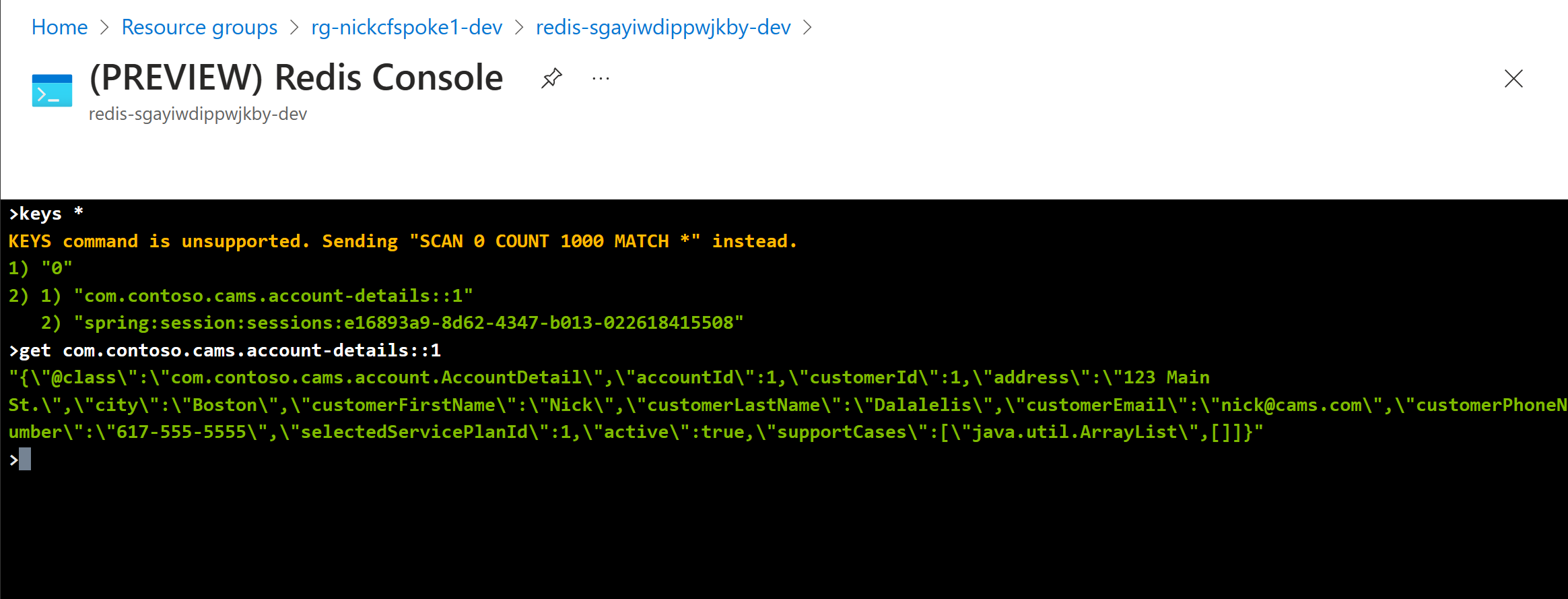
Azure Cache for Redis is a fully managed, open-source compatible in-memory data store that enables fast, high-performing applications, with caching and advanced data structures.
The cache-aside pattern helps us to reduce read queries to the Azure PostgreSQL Flexible Server. It also offers a layer of redundancy that can keep parts of our application operational in case of a problem with Azure PostgreSQL Database.
Using the Redis Console we can observe that we are caching objects and http sessions from Contoso Fiber in Redis.
Retry and Circuit Break Patterns
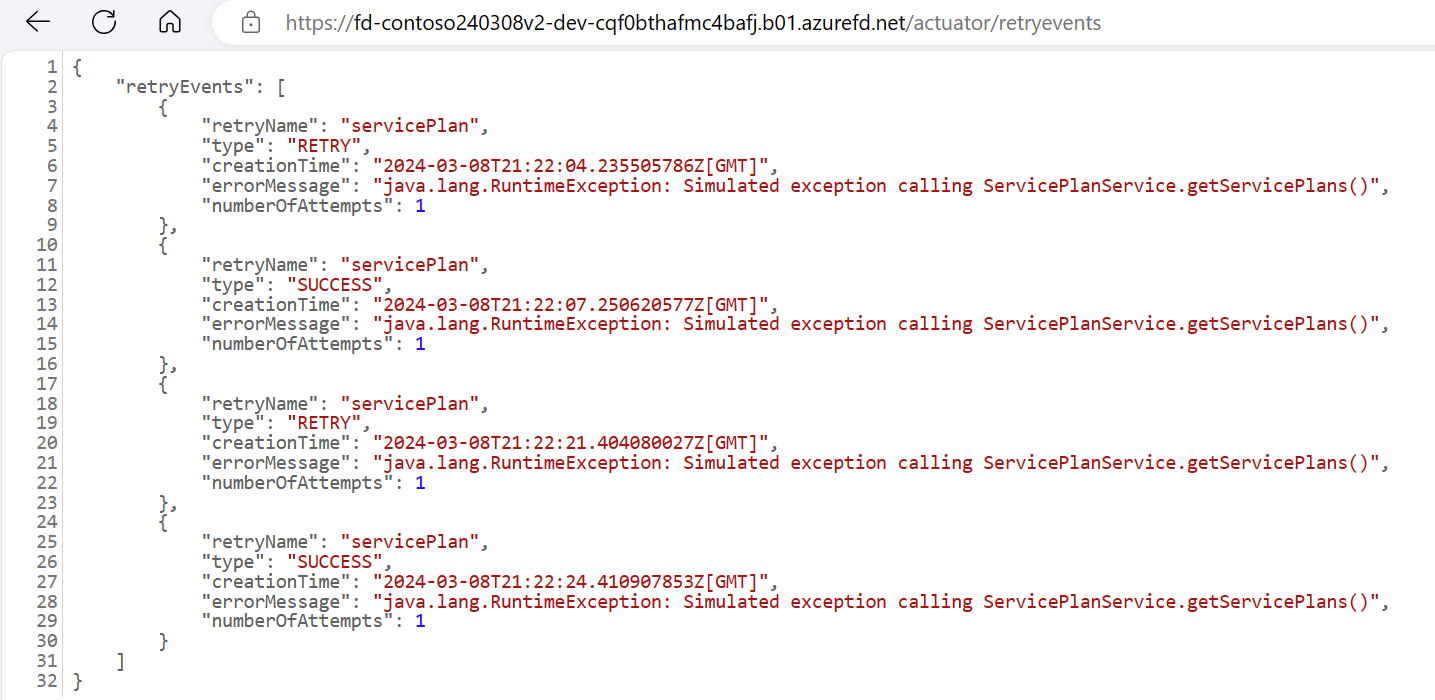
One of the most essential principles of the Reliable Web App pattern is the Retry Pattern. It helps your application deal with situations where a service might be temporarily down, a ‘transient fault’. The Retry pattern resends failed requests to the service until it’s working again.
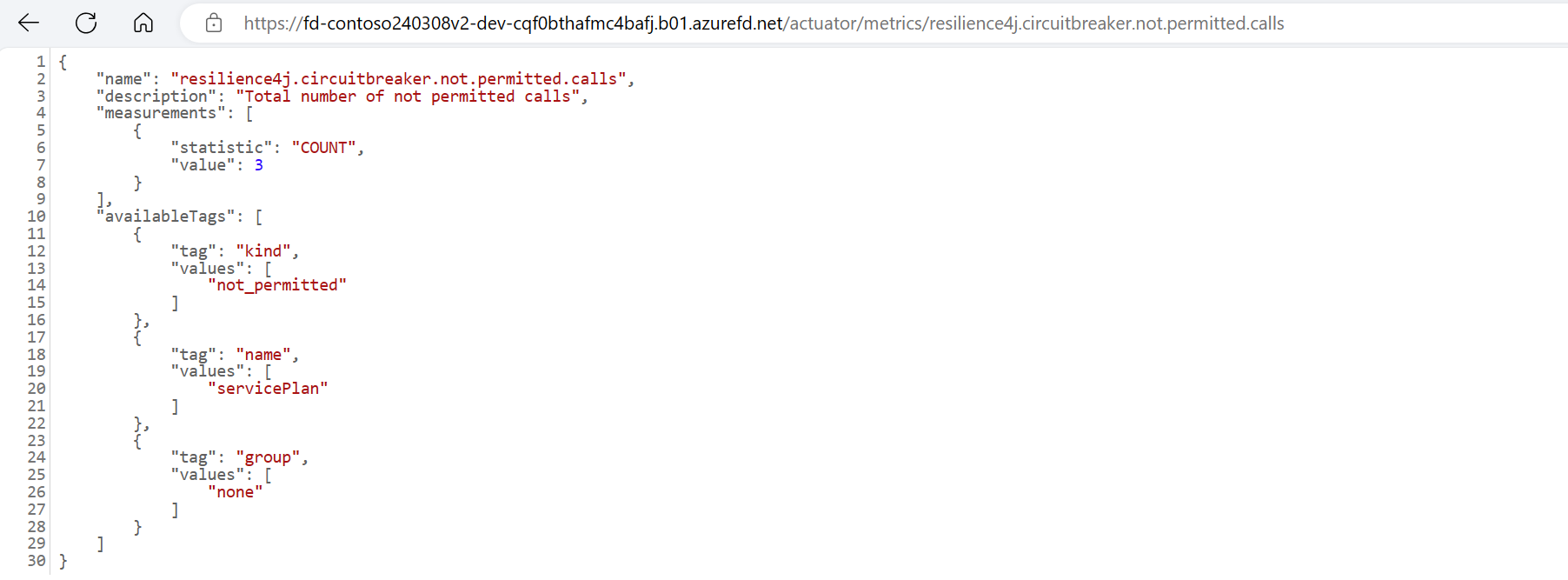
But the Retry Pattern alone is not enough. Sometimes, a service might be unavailable for a long time, or it might even be gone forever. It would be useless to keep trying to call such a service. That’s why we need the Circuit Breaker Pattern.
We added a feature to the reference application that lets you try out these patterns by making a transient failure happen. This way you can see when the circuit breaker opens or closes due to failure threshold!
New Reliability Features
In the latest update, we’ve rolled out Auto Scaling – now switched on by default, empowering your system to dynamically adjust from a baseline of two instances up to ten, based on CPU usage. Coupled with this, Application Insights offers an unparalleled depth of monitoring, from tracking anomalies to dissecting performance metrics, providing developers with the tools to pre-emptively tackle issues, ensuring a smooth and stable user experience.
By adopting a multi-region deployment approach, traffic is primarily directed to the active region, but should the unexpected happen, we’ve got a plan B: manual rerouting to a secondary region equipped with a read replica of the primary database. This means during unexpected downtimes, your application keeps running, making sure your users remain unaffected. This layered approach to resilience keeps your services online and operational, no matter what the circumstances. and delivers a minimum 99.9% service-level-objective – a key requirement of our reference implementation and its underlying business scenario.
Get Started
- Review the Documentation: Start by visiting the provided documentation link at https://learn.microsoft.com/azure/architecture/web-apps/guides/reliable-web-app/overview. This comprehensive guide will help you understand the pattern, its components, and how it improves your Java web applications’ security, scalability, and reliability.
- Explore the GIT Repository: Access the GIT repository at https://github.com/Azure/reliable-web-app-pattern-java. Here, you will find the production-quality, ready-to-deploy reference implementation of the pattern. Clone or download the repository to get started with the code.
- Experiment with the Demo: Check out Demo.md in the GIT repository to run a demo of the pattern. This practical experience will help you understand how the components work together and how to handle transient faults effectively.
Conclusion
The recent update to the Reliable Web App Pattern serves as a critical resource for developers looking to leverage Azure’s capabilities for building state-of-the-art Java web applications. The new reference release combines detailed architectural guidelines with practical implementation advice, so you can build resilient, scalable, and secure applications using Azure with Java.
We are excited for developers to dig in as this resource offers an invaluable opportunity for both learning and application, facilitating a seamless transition to cloud-based web development.

0 comments