Combating fraud and impersonation with identity verification is essential in keeping any organization and its employee identities safe. A 2021 Microsoft survey of 3,000 US-based companies (with greater than 500 users), found that 92% of organizations today perform identity verification of some kind, but 82% of them wish there was a simpler, more secure way of verifying a remote user’s identity.
There aren’t many widely used methods that consistently and effectively verify who is using a company’s applications, which leaves the door open for impersonation. Most of the common methods of identity verification are ineffective or do not answer the right identification question.
-
Traditional passwords are supposed to verify who is attempting to gain access, but impersonators frequently exploit them. Microsoft detects over 4,000 password attacks per second, up from 1,287 in 2022.
-
Knowledge-based questions aren’t a reliable way of verifying identities either. The National Institute of Standards and Technology advises against using knowledge-based authentication because of how easily impersonators can discover or correctly guess the answers.
-
CAPTCHAs can identify that a human is attempting to log in rather than a bot, but they do not verify the identity of who is attempting to gain access.
-
Multi-factor authentication (MFA) can greatly reduce the risk of account compromise by identifying that the right device is attempting to gain entry, but a successful MFA does not guarantee the right person is using the device. Microsoft observed 6,000 MFA fatigue attacks per day in 2023, so the threat of impersonators exploiting the human element of MFA is a common danger.
Organizations also need to prepare for new types of impersonation attacks with the increase of AI-assisted tools.
At Microsoft Build 2024, we demonstrated how Face Check with Microsoft Entra Verified ID introduces a high level of identity protection, with an intuitive, simple user experience. Read on to check out snippets from our Build demo and learn more about how to implement Face Check into your apps with Microsoft Entra Verified ID.
Are apps serving the right users?
How do we know that our apps are serving the right users without a consistently effective means of verifying who is attempting to use them?
In February 2024, we launched the public preview of Face Check, a premium feature within Microsoft Entra Verified ID that uses privacy-respecting facial matching, along with Verified ID verifiable credentials for high assurance verification.
Verifiable credentials provide a secure method for digitally verifying an individual’s identity, qualifications, or other attributes. Users own their credentials and store them in a digital wallet. For example, users can store their Verified IDs in the Microsoft Authenticator app. When asked to prove their identity, users can present their verifiable credentials.
Face Check for identity verification
Using just a verifiable credential is a great way to verify someone’s identity, but completing a Face Check adds an even higher level of assurance that the rightful credential owner is trying to gain access. Even if someone stole the credential owner’s phone and attempted to use their Verified ID to impersonate them, they could not bypass the Face Check verification. The Azure AI technology behind Face Check compares a live selfie against a trusted photo from the credential, making sure that only the Verified ID owner can complete a Face Check. It can also detect a wide variety of spoofing techniques, including deepfakes, and leverages years of learnings from operating Microsoft’s Windows Hello.
Face Check demos at Build 2024
Secure and streamline your help desk with Face Check
Face Check with Microsoft Entra Verified ID can give your users an easy-to-follow identity verification experience that consistently protects their identity without sharing unnecessary personal data. At the 2024 Build conference, we shared a demo showing how Face Check can be used in a company’s help desk experience. Let’s walk through the scenario.
An employee wants to order a new laptop, change their password, or do something else through their company’s help desk. To do this, they must prove to the help desk that they are who they claim to be, and that they do actually work there. For many companies, this verification can potentially involve waiting for a long time to speak with someone at the help desk who can verify the employee’s identity in real time. Using the Face Check-powered help desk shown in the video below, an employee can quickly and conveniently verify their identity in real time:
Once the Face Check is completed, the verifier is given a confidence score which shows a percentage of how certain the person in the live selfie matches the person in the photo associated with the account. This value is the only data the verifier receives. Face Check does not store personal data and it does not give data to the verifier. A higher score means that the false-acceptance rate is lower.
Note: It is up to you as a developer to decide the acceptable threshold for the confidence score, depending on how sensitive the application is.
As a baseline, if the score is 90%, there is a one in a billion chance that the person in the live selfie is not the rightful credential owner. With statistics like that, you can be confident that only the right people will be able to access your company’s applications with Face Check.
Account recovery after total loss of credentials
What if an employee completely lost all employee credentials? In the case of a total loss, employees can still recover their account and regain access to their credentials. The Verified Help Desk can authenticate an employee’s identity with a Verified Government ID provided by leading identity verification providers, such as the ones listed in our partner gallery. Even without employee credentials, a user can quickly and securely recover their account.
Watch how employees can recover their account in the case of a total loss of credentials and perform the government ID verification in just a few clicks:
Add Face Check with Microsoft Entra Verified ID to your apps today
With identity threats growing more frequent and more complex every year, now is the time to enhance your identity protection with Face Check. Bring a critical layer of trust to your apps by introducing facial matching powered by Azure AI services.
Microsoft Entra Verified ID provides a seamless developer experience without compromising privacy or security.
To get started with Face Check, an admin must first set up Microsoft Entra Verified ID, which can be completed in a few minutes with this quick setup tutorial.
Once Verified ID is ready to use, you can easily add the requirement for a Face Check verification in the same request API. Start by having your application request that the user present a Verified ID for an application task, as it normally would without Face Check. In that presentation request, add three extra lines of code to the request to add the Face Check requirement.
// POST
https://verifiedid.did.msidentity.com/v1.0/verifiableCredentials/createPresentationRequest
...
"requestedCredentials": [
{
"type": "VerifiedEmployee",
"acceptedIssuers": [ "did:web:yourdomain.com" ],
"configuration": {
"validation": {
"allowRevoked": false,
"validateLinkedDomain": true,
"faceCheck": {
"sourcePhotoClaimName": "photo",
"matchConfidenceThreshold": 70
}
}
The JSON payload to the Request Service API for creating a presentation request needs to specify that a Face Check should be performed. The claim containing the photo must be named and you may optionally specify your confidence threshold as an integer between 50-100. The default is 70.
If you are unfamiliar with how to create regular user requests for Verified ID verification, follow this tutorial.
Successful Face Check presentation_verified callback event
The JSON payload for the presentation_verified has more data when a Face Check was successful during a Verified ID credential presentation. The faceCheck section is added which contains a matchConfidenceScore.
Note: It isn’t possible to request and receive the presentation receipt when the request includes
faceCheck. There is a separate Face Check success/fail receipt.
"verifiedCredentialsData": [
{
"issuer": "did:web:yourdomain.com",
"type": [ "VerifiableCredential", "VerifiedEmployee" ],
"claims": {
...
},
...
"faceCheck": {
"matchConfidenceScore": 86.314159,
"sourcePhotoQuality": "HIGH"
}
}
],
Failed Face Check callback event
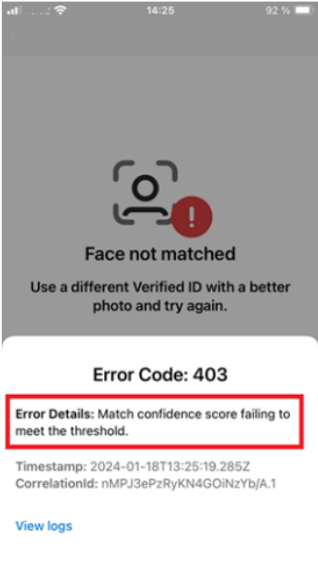
When the confidence score is lower than the threshold, the presentation request fails and a presentation_error is returned. The verifying application doesn’t get the score returned.
{
"requestId": "...",
"requestStatus": "presentation_error",
"state": "...",
"error": {
"code": "claimValidationError",
"message": "Match confidence score failing to meet the threshold."
}
}
The Authenticator displays an error message informing the user that the confidence score failed to meet the threshold.
Issuing a Verified ID credential with a photo
If a user already has their own Verified ID set up, it’s likely they already have a photo associated with the credential that their live selfie would be compared to in a Face Check verification.
If you want to learn how to set up a Verified ID with a photo, take a look at this tutorial. Below is the default Verified Employee data config for that credential.
The display definition for the photo claim should have the type set to image/jpg;base64u to let Microsoft Authenticator understand that it should be rendered as a photo correctly.
{
"claim": "vc.credentialSubject.photo",
"label": "User picture",
"type": "image/jpg;base64url"
}
When setting the actual claim value of the photo, it should be in the format UrlEncode(Base64Encode(JPEG image)).
{
"outputClaim": "photo",
"required": false,
"inputClaim": "photo",
"indexed": false
}
Custom credential types using the idTokenHint attestation flow can also issue a Verified ID credential containing a photo. The credential definition needs to have the display and rules definition for the photo claim.
Learn more
Securing your organization’s identities does not have to be complex. Microsoft Entra Verified ID allows you to quickly build unique user-owned identity scenarios that are designed for trustworthy, secure, and efficient interactions between people and organizations. Face Check provides an extra layer of certainty within those interactions that the right person is attempting to gain access to sensitive apps or resources.
Learn how to get started with Face Check with Microsoft Entra Verified ID and check out the latest Verified ID updates in the Microsoft Entra Verified ID developer center. Make sure you subscribe to the Identity blog for more insights and follow us on YouTube for video overviews, tutorials, and deep dives.
More resources
- Learn more about Face Check and read FAQ in Face Check documentation.
- Read about Face Check’s inclusive design in the Face API Fairness Report.
- Read about additional use cases for Verified ID in the eBook 11 ways verifiable credentials can transform your business.
- Quick admin tutorial to set up Verified ID.
- Explore the Microsoft Entra Verified ID Developer Documentation.
- Explore the Microsoft Entra Verified ID Product Page.
- Watch the Global Onboarding & Helpdesk tutorial to see step by step deployment.
- Check out the GitHub Sample Repository.


0 comments