Our vision for the Microsoft identity platform is to create a thriving developer and app ecosystem that makes securing identities easy. In fact, over one million applications use our platform, performing over eight billion authentications per day. We combine this with the 65 trillion signals that Microsoft Security processes each day to help us identify risky users, risky sign ins and risky workload identities – and we use this data to make your applications more secure.
In this blog I share how our platform enables developers to protect their users and apps without being identity or security experts. I will also share how developers can take advantage of our identity protection APIs to enhance their own product.
An overview of identity risk in your applications
A strong identity platform should help developers minimize identity and access management related vulnerabilities and respond to suspicious user account activity, for example, by alerting you if a user account is likely compromised. Identity related attacks are common – Microsoft sees 1,287 password attacks every second.
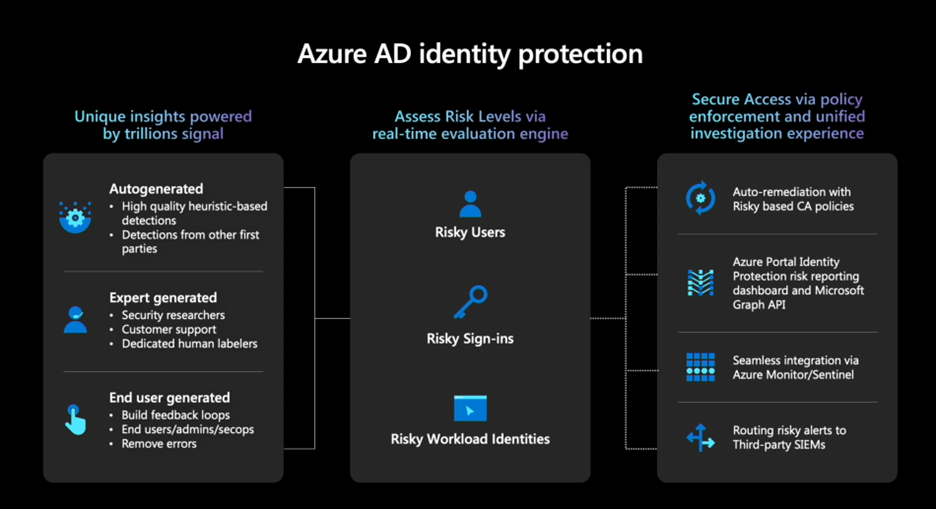
On our Identity platform, one way we deal with identity risk is through Azure AD Identity Protection, which draws upon the wealth of signals and intelligence we collect to detect and remediate risk. As depicted in the infographic below, the heart of identity protection is the aggregation of signals that power our risk engine. Our data science team creates heuristic-based detections that integrate into our machine learning models for best-in-class risk detection. We also integrate signals from security researchers within Microsoft, our customers, partners, and law enforcement.
For example, if a user logs in from a new IP address we can check if that IP address is associated with any known attackers, or if the location is suspiciously far away from previous login locations (atypical travel), the account will be flagged. These are just a couple examples of the many types of risk detections.
The Microsoft authentication library (MSAL) makes identity protection easy
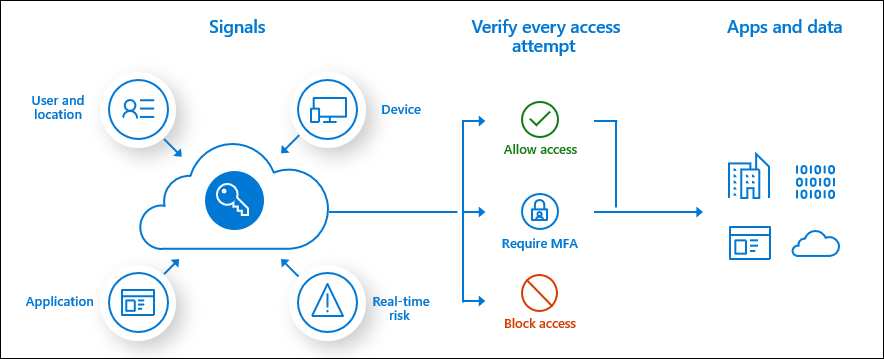
The core of our developer platform is the Microsoft Authentication Library (MSAL). The Microsoft Authentication Library (MSAL) enables developers to implement user sign-in and protect sensitive resources. To sign a user in, your application will ask Azure AD for a security token which it will then use to access resources. As part of this process, Azure AD will check to see if there is any risk related to this user and can require extra steps or block authentication if necessary.
That means that our platform’s Identity risk protections are built in to our developer tooling. To minimize your Identity risk, you can use our latest MSAL libraries to implement authentication and authorization. That’s it. We have made using identity protection as simple as possible.
Using Microsoft Graph for deeper integrations
In addition to the built in capabilities that you get automatically, we have made it easy to programmatically interface with Azure AD via Microsoft Graph for more in-depth integration with risk. The Microsoft Graph Identity Protection APIs can be used to analyze user risk, identify risk anomalies, and contribute to creating a secure ecosystem by sharing risk intelligence between Microsoft and your own application. You can try out the APIs for yourself using the Graph Explorer tool.
Independent security vendors are already making use of these APIs to enhance the value of their products by consuming and sharing risk signals from our Identity platform. For example, some of the vendors that have integrated with our Identity Protection APIs are shown below:
Conclusion
We know cybersecurity is a tricky business. Typically, developers are not trained as security experts, and yet they are responsible for building secure, resilient and robust applications and services that protect their company and their users. By developing with our SDKs and using Azure AD Identity Protection, you will be able to leverage our learnings and increase the ability of your application to detect and remediate compromised identities. Together we can reduce the impact of bad actors on all of our businesses.









0 comments