Microsoft Entra External ID, our next-generation customer identity and access management (CIAM) solution, launched in May 2024 with a focus on flexibility and intuitive user experience. Based on customer feedback, one key request that emerged was support for federation with external identity providers like Amazon, Auth0, Okta, and our predecessor product, Azure Active Directory B2C, to enable our customers to enrich their new Microsoft Entra CIAM experiences by federating with their Azure AD B2C platform.
Today, we are excited to announce the Public Preview of OpenID Connect (OIDC) identity provider support in Microsoft Entra External ID. This new functionality allows you to federate sign-in and sign-up user flows with identity providers using the OAuth 2.0 authorization standard and OpenID Connect specifications.
Enabling users to access your applications with existing accounts from other identity providers offers two key benefits: it enables partner integrations through identity federation, and it allows users to sign in using their existing identities instead of creating new credentials associated with their accounts. This streamlined approach supports partnerships and improves conversion rates and user satisfaction.
The journey to Public Preview
During the development and testing stages of this feature, we worked with customers and partners to ensure that it met their needs and requirements. During Private Preview, we tested OIDC federation across hundreds of configurations, including various well-known endpoints, key secret combinations, authentication methods, response types, response modes, and more.
OIDC federation has been tested and validated with several popular identity providers, including Azure AD B2C, Amazon, Auth0, AWS Cognito, Discord, Itsme, Okta, OneLogin, OpenPass, PayPal, Ping Federate, and Salesforce.
Thank you to all our customers and partners that helped us validate the product.
Key scenarios for OIDC external identity providers
Microsoft Entra External ID’s OIDC external identity provider support enables several key scenarios:
- Integrate with cloud identity providers: Integrate your sign-in and sign-up flows with cloud identity providers.
- Federate with Azure AD B2C: Begin building new CIAM experiences with Entra External ID while federating with existing Azure AD B2C tenants.
- Implement partner identity providers: Enable federated authentication for partnership scenarios, such as partner employee discount programs.
- Federate with government and citizen identity providers: Establish secure authentication with government and citizen identity providers.
Getting started with OIDC federation
OIDC federation enables users to sign up and sign in to your applications using their existing accounts from external identity providers that support the OpenID Connect protocol. By adding an OpenID Connect identity provider to your user flow, users can authenticate to registered applications defined in that user flow, using their credentials from the OIDC identity provider.
For guidance on configuring your OpenID Connect identity provider, adding it to your user flow, and integrating sign-in and sign-up experiences into your application, you can refer to these resources:
- Add OpenID Connect as an external identity provider
- OpenID Connect claims mapping
- Add Azure AD B2C tenant as an OpenID Connect identity provider
Configuring an OIDC identity provider in your tenant involves four key steps:
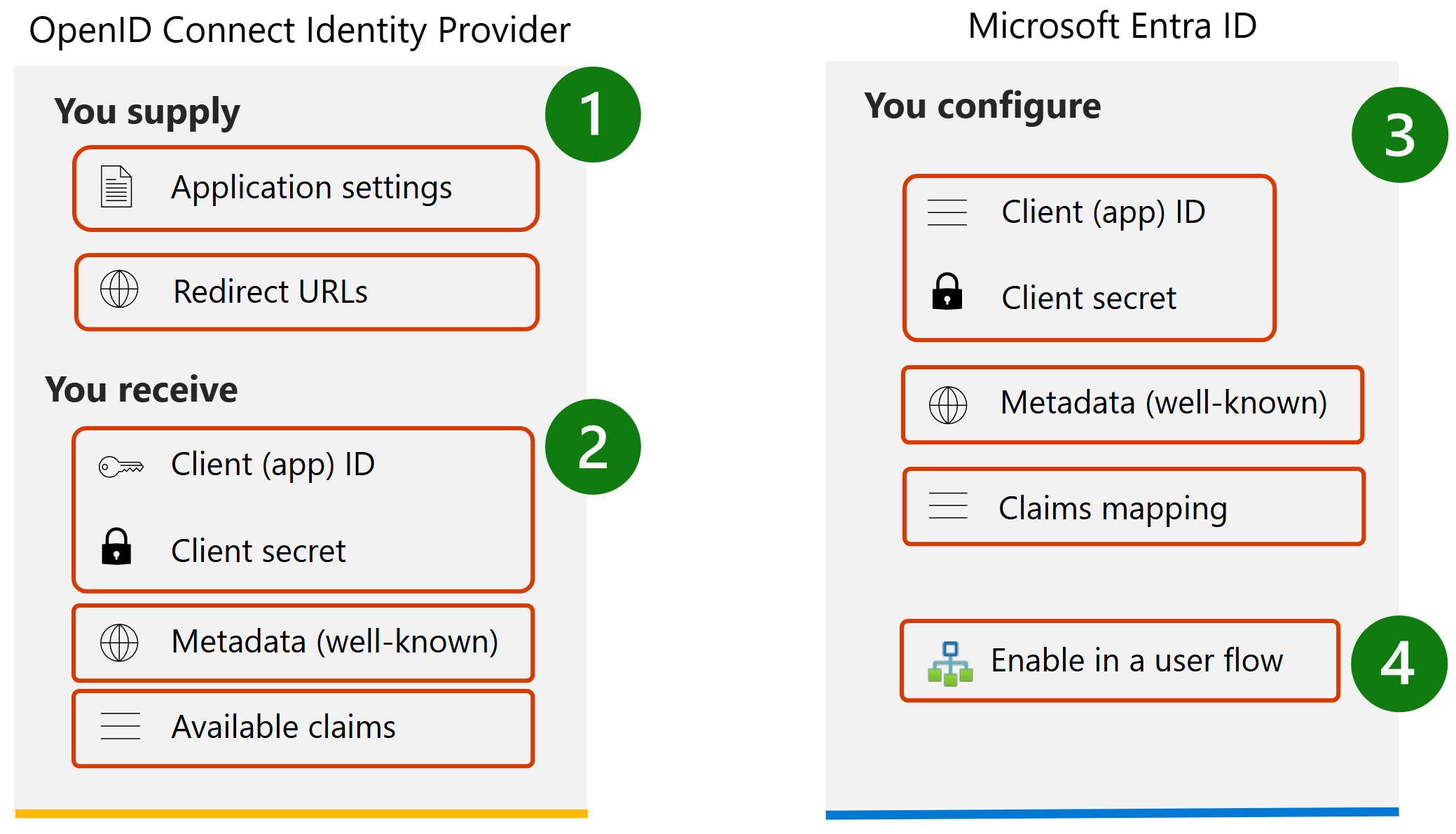
- Create and register an application with an external identity provider by supplying your Entra application settings and redirect URLs. These specify where users are sent to authenticate, and where to redirect them after successful login.
- The identity provider will generate a client ID and a credential, such as a client secret or a certificate, that will be used to configure your Custom OIDC Identity provider for your tenant. The identity provider will also provide the well-known configuration endpoint which contains key details, including the provider’s token and authorization endpoints, the public keys necessary for validating token signatures, and other pieces of information. Additionally, the identity provider will provide a catalog of supported ID token claims and the respective scopes necessary to obtain their values. Claims are pieces of information contained within the identity token, providing details about the user, like the display name and user’s unique identifier. This information is used to map with corresponding user flow attributes when creating a new user account.
- Add the new identity provider in your tenant using the information you received from the identity provider.
- Enable the identity provider in the user flow which is associated with your application.
What’s next?
Custom OIDC federation currently supports integration with Azure AD B2C and cloud identity providers that follow the OIDC protocol. Our next phase will enable federation with other Entra tenants as OIDC external identity providers. This enhancement will enable organizations to federate authentication with their business partners who use Entra tenants. Following that, we are also planning to support domain-based federation with OIDC and sign-in acceleration through domain hints.
Stay connected and informed
To learn more or test out features in the Microsoft Entra portfolio, visit our developer center. Make sure you subscribe to the Identity developer blog for more insights and to keep up with the latest on all things Identity. And, follow us on YouTube for video overviews, tutorials, and deep dives.
We encourage you share your feedback and tell us what you think, or suggest new features to make external identities federation features even better. Also, please join our research panel to receive occasional invites to participate in customer research.


This have been a missing feature for a while :). Looking forward for more features. I however cannot find any place to add my private key using client assertion for my external OIDC provider. See Q/A https://learn.microsoft.com/en-gb/answers/questions/2140109/add-external-idp-with-oidc-using-private-key-jwk
I would like to have more control of how the OIDC trust is setup. E.g. External OIDC providers can have their own custom extensions such as providing acr_values or having requirements to client authentication method (use certificates, client assertion etc.)
Thank you for the feedback, Jenny. For private_key_jwt implementation, you’ll need to use the jwks_uri token endpoint in the IdP metadata. Also, we already have alternative plans to support key pairs for private_key_jwt, as well as providing default acr_values for phishing-resistant MFA trust, in a future release.
Is this also coming to the Entra ID product SKU?
Hi Jeff. The feature is now supported with external tenants now, with Entra ID SKU. Workforce tenants will also be supported soon.