We make it easy for users to create new organizations and start collaborating within seconds in Azure DevOps. While our users loved this, some of our big enterprise customers have long been demanding that they need to control who can create new organizations within their company as a way to protect their IP. With the latest sprint deployment, I am happy to announce that we rolled out a new policy in Azure DevOps to restrict this to a configured list of people in your company. This policy is supported only for company owned (Azure Active Directory) organizations. Users creating organization using their personal account (MSA or GitHub) have no restrictions.
To administer this policy, users need to be assigned to a new role called ‘Azure DevOps Administrator’ in Azure AD. Talk to the Azure AD administrator of your company to get this role assigned to you. Please refer to the documentation about this new role here.
You can find this role in the Azure Portal under Azure Active Directory > Roles and administrators.
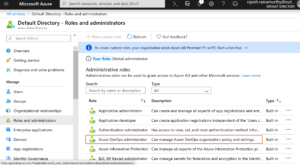
Once you are assigned to this role, sign into any Azure DevOps organization that is connected to your Azure AD tenant to start managing this policy. You can find this new policy under organization settings > Azure Active Directory.

You can find the documentation to configure this policy here.
Please try out this feature and let us know your feedback through via Twitter on @AzureDevOps, or using Developer Community.

How this will work with people creating organization based on their MSDN accounts?