We’re excited to announce that GitHub Advanced Security for Azure DevOps is now generally available and is ready for you to use in your own Azure DevOps repos! You can now enable code, secret, and dependency scanning within Azure Repos and take advantage of the new product updates.
Learn how to enable Advanced Security in your Azure Repos >
Thanks to your great feedback, we were able to identify issues and deliver updates that address key improvements since our public preview. You wanted:
- Faster onboarding after registering for Advanced Security
- The ability to enable multiple repos simultaneously
- More upfront clarity in billing
- Better visibility into all enabled repo alerts through a single pane of glass
and we delivered.
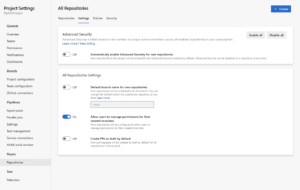
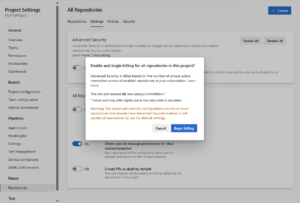
Instead of registering to get your organization onboarded to Advanced Security, we’ve done away with the registration process entirely. Any Azure DevOps Project Collection Administrator (PCA) can now enable Advanced Security protections for their orgs/projects/repos through the Azure DevOps configuration settings.
Speaking of enablement experiences, we also addressed that you’d really like an easy way to enable all the repos in a given project or org. During public preview, we provided some PowerShell scripts to help automate bulk-enablement as a workaround, but we acknowledged that you wanted the ability to enable Advanced Security on newly created repos by default. To make this process easier for you, you can now choose to enable Advanced Security at the org or project level as well as the individual repo level, and you can also choose for Advanced Security to be automatically enabled for any future repos you and your teams create.
Because Advanced Security is billed per active committer, we also now show the number of new active committers you would be billed for by enabling Advanced Security for a repo/project/org.
I’ve saved our biggest news for last: another virtually universal feature request we get is for a way for you to view all your Advanced Security alerts across all your repos in a single pane of glass. However, we’ve actually done better than that! Advanced Security is now integrating with Microsoft Defender for Cloud (MDC) to enable you to view all the alerts for all your repos across all your orgs – both Azure DevOps and GitHub – all in a single pane of glass in MDC. This all comes in the free tier of MDC, so it’s no extra cost to you, but you do get some awesome code-to-cloud contextualization capabilities in the paid tier, so please do check that out.
Again, whether you’ve ever signed up for an Advanced Security preview or not, all these new features and all the existing features of Advanced Security (such as code scanning, dependency scanning, and secret scanning) are now ready for you to enable in your own Azure DevOps orgs. We’d love to hear any feedback you have for us by using the Developer Community site. For more information, we’re also hosting a webinar demo and Q&A on October 6, and we’d love to see you there to answer any questions you may have in real time!
Learn more about the GitHub Advanced Security for Azure DevOps Webinar >
To learn more about other upcoming Azure DevOps investments in security and beyond, see https://aka.ms/AzureDevOpsRoadmap.


Are there any plans to support other languages like typescript during code scanning. Seems to only be a few supported at the moment according to the documentation.
Hi Gary, we do currently support TypeScript! Here’s the full list of languages:
– C/C++
– C#
– Go
– Java
– Kotlin
– JavaScript
– Python
– Ruby
– Swift
– TypeScript
– and more are on the way that we’re not ready to name quite yet 🙂 If you have requests for CodeQL language/framework support, please let us know at https://developercommunity.visualstudio.com. Thanks!
https://codeql.github.com/docs/codeql-overview/supported-languages-and-frameworks/
Hi Bryan. Been playing around with GHAS at work. Have added it to a few pipelines and it's looking good! I was wondering though if there are plans to introduce true shift left on the code scanning and dependency scanning by incorporating scan results into PRs?
I'd love it if I could set up a policy that blocks any PRs with code scan violations from being able to merge into main. Or at least set up some PR annotations, so the developer and reviewer can see if the code being merged caused any problems. I've done a fair bit of reading...
Hi Jonathan, great to hear you're liking it! Definitely we have plans to shift further left to raise alerts as PR annotations - this is something that GHAS-for-GitHub already does (https://docs.github.com/en/code-security/code-scanning/managing-code-scanning-alerts/triaging-code-scanning-alerts-in-pull-requests#viewing-an-alert-on-your-pull-request) and we're looking to deliver the same capabilities in GHAzDO by mid-calendar year 2024.
One thing that might help in the meantime is our Powershell script that you can customize for gating builds, including PR validation builds: https://github.com/microsoft/GHAzDO-Resources/tree/main/src/gating. You can set SLAs for different severities; for example, break the build if there are any criticals more than two days old, any highs more than seven days old, etc. You...
Ah that’s interesting, thanks Bryan. I was thinking about whether it was possible to download the SARIF file from the API, copy it to the artifacts and then maybe use the SARIF SAST Scans Tab devops extension to add something to the PR output.
That Powershell script looks like it will be cleaner though and do the job nicely. If I get a bit of time, I’ll give it a go.
Ever since this was deployed I’ve been getting permissions errors with VS2012 clients. I’m receiving TF31003, TF30063, and TF205020 errors. Anyone else receiving this?
I do not have Advanced Security enabled on either my Organization or my Project.
Hi Ben, thanks for reaching out. We don’t think Advanced Security is causing this but we are pulling in more colleagues from Azure DevOps engineering to help investigate. We are working from the info in your Developer Community post, and we’ll keep that thread updated. Thanks again!
Hi Bryan, Thanks for the response. Unfortunately MS has chimed in indicating they will not address this issue. They mentioned this on my community post as well as a much more active one regarding AX 2012 also loosing the ability to connect to Azure DevOps Services.
Do you think you can try to get some more assistance or information? It's very disturbing that we lost this crucial component in our development stack without any advance notice or testing windows.
https://developercommunity.visualstudio.com/t/Login-from-AX2012-R3-Version-Control-not/10461669
https://developercommunity.visualstudio.com/t/TF30063-and-associated-errors-since-920/10473760
Does this overlap with Defender for DevOps ?
Hi Ramu, no, we see Advanced Security and DfD as complementary. We had a small amount of overlap around secret scanning while Advanced Security was in preview, but secret scanning in DfD has now been deprecated in favor of Advanced Security. So they each have unique solution sets: Advanced Security is a developer-focused product that offers secret scanning, secret blocking, dependency scanning (SCA) and code scanning (SAST); while DfD is a Security Manager/CSO-focused product that offers code-to-cloud contextualization, a single pane of glass to see a broad overview of risk across your enterprise, and more. You'll definitely see more integration...
That seems reasonable. I heard from some of your colleagues that part of the longer preview was the problem around secret scanning and the overlap. We are still in the pilot for GHAS and AzDO and started in the preview.
And we recvently also had a workshop how the overlap works and what the differences are. Defender for DevOps really can be used to get an Enterprise overview of compliance and security. I like the approach in this!
Even if it is not the scope here but maybe you can give an insight @bryan. Will defender for DevOps also scan infrastructure code...
Hi Sebastian, yes Infrastructure as Code based policies are on Defender for DevOps roadmap. The exact policies that we provide at launch and what follows later is still TBD.
Are there any plans to bring this On Premise?
If so, how about the Dependabot feature?
No plans at this time to bring Advanced Security to ADO Server (on prem) but do let us know if this is something you’d take advantage of – we’re not saying “zero chance, never”, just no plans right now.
As for Dependabot, Advanced Security already does raise alerts when it detects that you’re using vulnerable OSS, and our dev team is working right now to bring the GH Dependabot automatic PR generation feature to Advanced Security.
This would also be of interest for us. As for now we don’t have any plans to move from ADO Server to ADO Services. So this would be a really interesting feature for us to improve security in our software development without integrating other tools or prodcts that fulfill the same features as Advanced Security.
Brian, this is really cool!
Is there any guidance on how we can get these alerts surfaced into an incident platform like Jira or Ops Genie or even webhook alerts to teams, email integration?
How can we create awareness and response for these these alerts in a structured manner?
Thanks! We do have a REST API you can use to pull alert data, and as soon as we get the documentation up on learn.microsoft.com I’ll reply back here with the link. No webhook yet but it’s something we’re thinking about. If you want to get really strict about awareness/enforcement, we have a Powershell script we put up on GH (https://github.com/microsoft/GHAzDO-Resources/tree/main/src/gating) that will break a build if there are any open alerts older than whatever SLA you configure.
Sorry but $49 per month per contributor is just too expensive. With just 2 devs it is almost $100 extra a month. There are free scanning tools available that take more setup to get working but once it is working then you're done. Without doing a cost analysis I'm going to assume that after 1 year the free scanning tools are saving money over the yearly cost of this new service.
It seems to me that more and more DevOps features are going behind paywalls. I personally don't like where this is going but I do understand that DevOps needs to...
That is not correct. Azure DevOps itself with 6$ costs per license is already heavily sponsored. Tools like GitHub or Gitlab cost twice as much per user already.
Additionally, if you look at the costs for Mend (WhiteSource) + Fortify or Blackduck and additionally to have secret scanning with push blocks in it then you already have the same upfront costs per user. Additionally, we tried secret scanning alone with gitleaks. Gitleaks is just a regex engine that you need to maintain yourself.
Saas tools are always less expensive than PaaS or any self-managed tool. We in our company can maintain...
I’d like to share a true story from Microsoft Build earlier this year. After my session on Advanced Security, one of the audience members took off their badge so I couldn’t see who they worked for, then came up to tell me that they were currently recovering from a breach caused by an exposed credential. They asked how much Advanced Security costs, I told them, and they said that’s a lot less expensive than the cleanup from their breach was costing them.
Hi Bryan,
How different is this from using the Microsoft Security DevOps Azure DevOps extension?: https://learn.microsoft.com/en-us/azure/defender-for-cloud/azure-devops-extension
Using Azure DevOps repositories and not GitHub repositories, I would like to better understand the differences between both solutions and to know if this is something complementary or if, on the contrary, it is better to use one over the other (in case one is more complete than the other one).
Regards.
Hi Ivan, great question - Advanced Security and the Microsoft Defender for Cloud (MDC) MSDO extension are definitely "better together", not overlapping. While we were in preview mode we did have some overlap in the secret scanning feature area, but secret scanning (CredScan) has now been deprecated from MSDO in favor of Advanced Security. So if you want secret scanning and secret blocking - and this is something important that everyone should use! - then you want Advanced Security. However, MDC also has important capabilities like code-to-cloud contextualization, and a single "pane of glass" to view all your Advanced Security...
Hi Bryan, thanks for clarifying. I didn't know about the CredScan tool being deprecated.
May I ask something else? What does that deprecation exactly mean? Are you planning on removing the tool from the MSDO extension set, or will it just get out of date (unattended) because of not having any more updates from the Microsoft side?
I also noticed that in “Microsoft Defender for Cloud | DevOps security (preview)” I no longer see the option in the “Pull Request Annotations” to enable the secrets scan but only the IaC scan. I guess this is one of these changes caused by the...
The CredScan tool no longer detects secrets. My understanding from the Defender team is that they didn't remove it from MSDO entirely because that would cause users' builds to break, but if you use it you'll get a warning in your build log that it's no longer trying to detect secrets. And yes, this is why MDC PR annotations aren't applicable for secret scanning - given that Advanced Security scans and blocks secrets at push time, which is more left-shifted, there really wasn't a need to repeat that analysis at PR time. Secret exposures are unique in that you're not...
Hi Bryan,
Thanks a lot for clarifying, it is really appreciated. I do think it is worth checking out all the things you mention.
Regards.
this comment has been deleted.
If we have the “Visual Studio Enterprise with GitHub Enterprise” subscription in our Azure DevOps, does that mean access to “GitHub Advanced Security for Azure DevOps” is available to us as part of that subscription with no extra charges? I can’t find anywhere in the documentation that specifically answers that question, nor does any of the screens in Azure DevOps settings that I can find indicate the answer to this in the same way that “Parallel jobs” for Azure Pipelines does where it lists the count of Visual Studio Subscribers as part of the limits.
No, Advanced Security is an extra charge beyond your VS Enterprise subscription. Please see https://learn.microsoft.com/en-us/azure/devops/repos/security/github-advanced-security-billing?view=azure-devops for more details on the billing model. The Billing screen in the ADO configuration settings now includes an “Advanced Security” section that shows the number of unique active committers in your Advanced Security-enabled repos (ie how many users you’re paying for Advanced Security for).