As you may have read, Azure DevOps OAuth apps are due for deprecation in 2026. All developers are encouraged to migrate their applications to use Microsoft Entra ID OAuth, which can access all Azure DevOps APIs and has the added benefit of enhanced security features and long-term investment.
Although we are nearing Azure DevOps OAuth’s end-of-life, we remain committed to providing very critical security enhancements on Azure DevOps integration methods as they remain available. To this end, we’re introducing a new feature designed to improve security on existing apps and streamline the oft-disruptive secret rotation chore: overlapping secrets.
What are Overlapping Secrets?
Overlapping secrets allow you to add a new secret to your OAuth apps while the old secret remains valid. This ensures a seamless transition and continuous operation of your applications.
-
Programmatic Secret Rotation: Regularly rotating client secrets is crucial for minimizing the risk of secret exposure. The overlapping secrets APIs facilitate this by allowing you to programmatically manage secrets, encouraging more frequent rotation vs. relying on updating via UI alone.
-
Reduced Downtime: Use the new secret while the old one is still valid, eliminating any potential downtime during the transition.
-
Shortened Secret Duration: Given the improved tooling offered, we feel comfortable with reducing the default secret lifespan of new secrets to 60 days. If you have a long-lived secret, even if it’s recently rotated, we recommend you still explore building a secret rotation process into your code as it’s good practice.
How it Works
This new feature is available both via the ADO OAuth app pages in your Visual Studio profile and the new Rotate Registration Secret APIs. To authenticate to the Registration Secret APIs, you will need the vso.tokens scope. For more detail, visit our Azure DevOps OAuth docs.
-
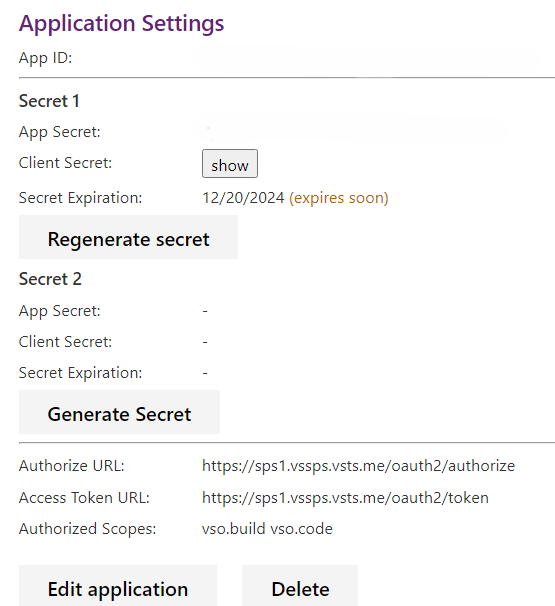
Generate a New Secret: Generate a new secret for your app by API or UI. This new secret is valid alongside the old one.
-
Use Both Secrets: Both secrets can be used to obtain access and refresh tokens, ensuring a seamless transition.
-
Old Secret Expires: Once the new secret is in place, you can let the old secret expire naturally. You may also regenerate the old secret to maintain security by ensuring that the old secret is no longer in use.

Test out this new feature today and rotate your existing long-lived secrets. Should your app secret ever be leaked, rectify this quickly with no downtime by rotating in a new secret as soon as possible.
Stay tuned for more updates on Azure DevOps OAuth and other exciting authentication features coming to Azure DevOps this year! Happy coding!


0 comments